re
你的flag被加密啦!
可以直接改源码
点击查看代码
def custom_encrypt(plaintext):encrypted = ""key = [3, 5, 2]key_index = 0for char in plaintext:if 'a' <= char <= 'z':shift = key[key_index]new_char = chr((ord(char) - ord('a') - shift) % 26 + ord('a'))key_index = (key_index + 1) % len(key)elif 'A' <= char <= 'Z':shift = key[key_index]new_char = chr((ord(char) - ord('A') + shift) % 26 + ord('A'))key_index = (key_index + 1) % len(key)elif '0' <= char <= '9':num = int(char)new_num = (num - 7) % 10new_char = str(new_num)else:new_char = charencrypted += new_charreturn encryptedencrypted_flag = custom_encrypt("iqcj{qafmgh89991}")
print("加密后的flag是:", encrypted_flag)
crypto
CTF
运行附件得到
加密后的 flag: GzSkR/OLfsenxQd5Hh4t2RlEwL/3JG5dW/gYu7YI1Os=
密钥(Base64 编码): MTIzNDUAAAAAAAAAAAAAAA==
IV(Base64 编码): MTIzNDU2AAAAAAAAAAAAAA==
加密模式: AES - CBC
可以直接找合适的在线解密
注意都是base64
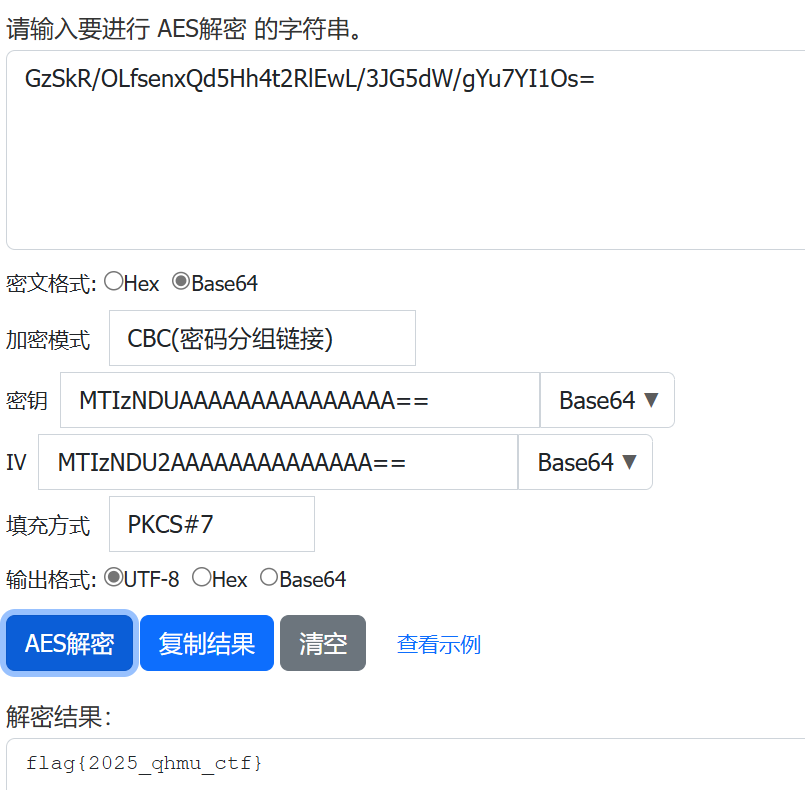
https://tool.hiofd.com/aes-decrypt-online/
新年快乐
点击查看代码
aa='Gsv_Bvzi_lu_gsv_Hmzpv_rh_zfhkrxrlfh'
flag=""
for i in aa:if 'a'<= i <= 'z':new = chr(ord('z')-ord(i)+ord('a'))flag += newelif 'A'<= i <='Z':new = chr(ord('Z')-ord(i)+ord('A'))flag += newelse:new=iflag += new
print(flag)
misc
come on
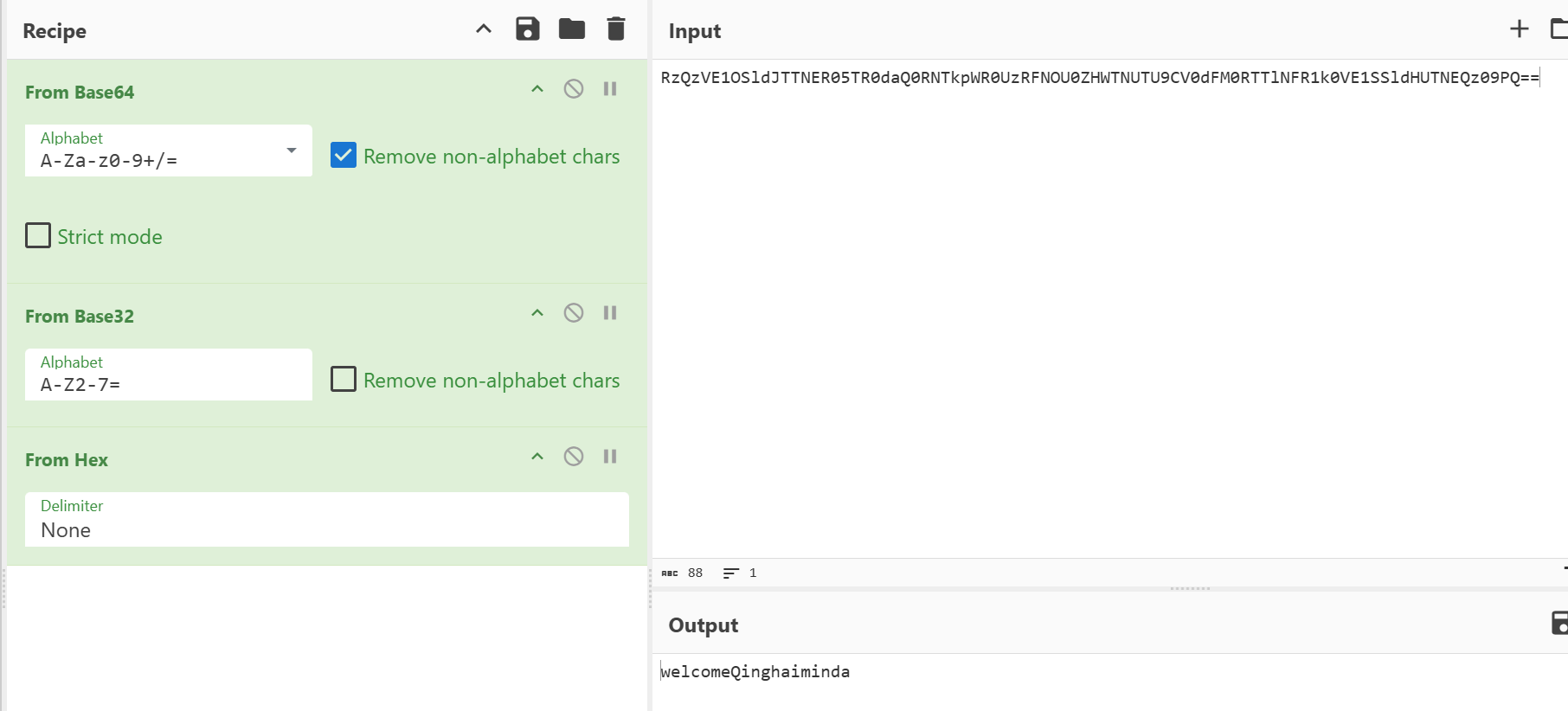
wenshilou
foremost分离文件,zip里面有flag.txt,base64解码
好看的照片
foremost分离文件,zip的密码根据txt的提示对照ASCII码表解决
密码为:7Fx.
分离出来是9张照片,拼接为一张二维码,扫码
失落遗迹的神秘预言
浏览器搜索维吉尼,发现是维吉尼密码,密钥为HERO,在线解码
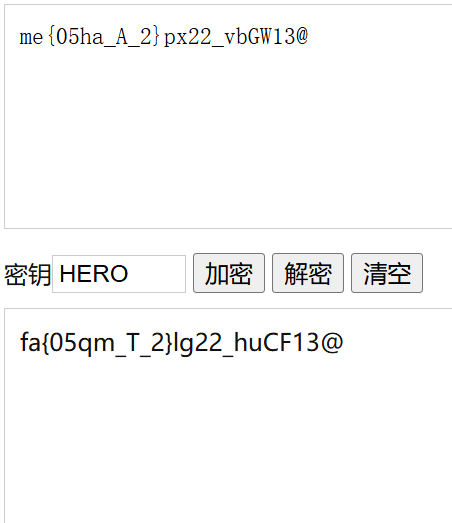
https://www.qqxiuzi.cn/bianma/weijiniyamima.php
然后还后栅栏密码
喔艾亭嘟歌
直接用Audacity打开,标签轨有内容,base4解密



![[羊城杯 2024]你这主函数保真么 _wp](https://img2024.cnblogs.com/blog/3599043/202502/3599043-20250208160818071-169768830.png)