Clam AntiVirus(ClamAV)是免费而且开放源代码的防毒软件,软件与病毒码的更新皆由社群免费发布。ClamAV在命令行下运行,它不将杀毒作为主要功能,默认只能查出系统内的病毒,但是无法清除。需要用户自行对病毒文件进行处理。
在线安装
# ubuntu
sudo apt install clamav clamav-daemon -y# centos
sudo yum install clamav clamav-update -y
离线安装
1、官网下载对应的软件包
ClamAVNet![]() https://www.clamav.net/downloads
https://www.clamav.net/downloads 
2、将下载的软件包上传到服务器后使用rpm/dpkg命令进行安装,软件包里面已经将相关依赖这些打包好了,直接安装就行。
rpm -ivh --prefix=/usr/local/clamav clamav-1.3.0.linux.x86_64.rpmdpkg -i --instdir=/usr/local/clamav clamav-1.3.0.linux.x86_64.deb 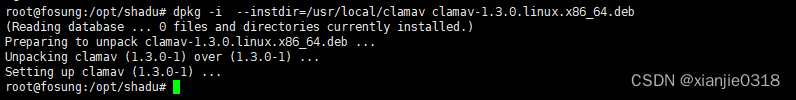
手动更新病毒库
病毒库位置:/var/lib/clamav/*
1、暂时停止服务:sudo systemctl stop clamav-freshclam
2、运行freshclam:sudo freshclam 或者直接: /usr/bin/freshclam
3、重新启动服务:sudo systemctl start clamav-freshclam
注:
复制/usr/local/etc/freshclam.conf并注释掉:
#Example
使用说明:
1、clamscan用法
clamscan [options] [file/directory/-]--help -h Show this help--version -V Print version number--verbose -v Be verbose--archive-verbose -a Show filenames inside scanned archives--debug Enable libclamav's debug messages--quiet Only output error messages--stdout Write to stdout instead of stderr. Does not affect 'debug' messages.--no-summary Disable summary at end of scanning--infected -i Only print infected files--suppress-ok-results -o Skip printing OK files--bell Sound bell on virus detection--tempdir=DIRECTORY Create temporary files in DIRECTORY--leave-temps[=yes/no(*)] Do not remove temporary files--gen-json[=yes/no(*)] Generate JSON metadata for the scanned file(s). For testing & development use ONLY.JSON will be printed if --debug is enabled.A JSON file will dropped to the temp directory if --leave-temps is enabled.--database=FILE/DIR -d FILE/DIR Load virus database from FILE or load all supported db files from DIR--official-db-only[=yes/no(*)] Only load official signatures--fail-if-cvd-older-than=days Return with a nonzero error code if virus database outdated.--log=FILE -l FILE Save scan report to FILE--recursive[=yes/no(*)] -r Scan subdirectories recursively--allmatch[=yes/no(*)] -z Continue scanning within file after finding a match--cross-fs[=yes(*)/no] Scan files and directories on other filesystems--follow-dir-symlinks[=0/1(*)/2] Follow directory symlinks (0 = never, 1 = direct, 2 = always)--follow-file-symlinks[=0/1(*)/2] Follow file symlinks (0 = never, 1 = direct, 2 = always)--file-list=FILE -f FILE Scan files from FILE--remove[=yes/no(*)] Remove infected files. Be careful!--move=DIRECTORY Move infected files into DIRECTORY--copy=DIRECTORY Copy infected files into DIRECTORY--exclude=REGEX Don't scan file names matching REGEX--exclude-dir=REGEX Don't scan directories matching REGEX--include=REGEX Only scan file names matching REGEX--include-dir=REGEX Only scan directories matching REGEX--bytecode[=yes(*)/no] Load bytecode from the database--bytecode-unsigned[=yes/no(*)] Load unsigned bytecode**Caution**: You should NEVER run bytecode signatures from untrusted sources.Doing so may result in arbitrary code execution.--bytecode-timeout=N Set bytecode timeout (in milliseconds)--statistics[=none(*)/bytecode/pcre] Collect and print execution statistics--detect-pua[=yes/no(*)] Detect Possibly Unwanted Applications--exclude-pua=CAT Skip PUA sigs of category CAT--include-pua=CAT Load PUA sigs of category CAT--detect-structured[=yes/no(*)] Detect structured data (SSN, Credit Card)--structured-ssn-format=X SSN format (0=normal,1=stripped,2=both)--structured-ssn-count=N Min SSN count to generate a detect--structured-cc-count=N Min CC count to generate a detect--structured-cc-mode=X CC mode (0=credit debit and private label, 1=credit cards only--scan-mail[=yes(*)/no] Scan mail files--phishing-sigs[=yes(*)/no] Enable email signature-based phishing detection--phishing-scan-urls[=yes(*)/no] Enable URL signature-based phishing detection--heuristic-alerts[=yes(*)/no] Heuristic alerts--heuristic-scan-precedence[=yes/no(*)] Stop scanning as soon as a heuristic match is found--normalize[=yes(*)/no] Normalize html, script, and text files. Use normalize=no for yara compatibility--scan-pe[=yes(*)/no] Scan PE files--scan-elf[=yes(*)/no] Scan ELF files--scan-ole2[=yes(*)/no] Scan OLE2 containers--scan-pdf[=yes(*)/no] Scan PDF files--scan-swf[=yes(*)/no] Scan SWF files--scan-html[=yes(*)/no] Scan HTML files--scan-xmldocs[=yes(*)/no] Scan xml-based document files--scan-hwp3[=yes(*)/no] Scan HWP3 files--scan-onenote[=yes(*)/no] Scan OneNote files--scan-archive[=yes(*)/no] Scan archive files (supported by libclamav)--alert-broken[=yes/no(*)] Alert on broken executable files (PE & ELF)--alert-broken-media[=yes/no(*)] Alert on broken graphics files (JPEG, TIFF, PNG, GIF)--alert-encrypted[=yes/no(*)] Alert on encrypted archives and documents--alert-encrypted-archive[=yes/no(*)] Alert on encrypted archives--alert-encrypted-doc[=yes/no(*)] Alert on encrypted documents--alert-macros[=yes/no(*)] Alert on OLE2 files containing VBA macros--alert-exceeds-max[=yes/no(*)] Alert on files that exceed max file size, max scan size, or max recursion limit--alert-phishing-ssl[=yes/no(*)] Alert on emails containing SSL mismatches in URLs--alert-phishing-cloak[=yes/no(*)] Alert on emails containing cloaked URLs--alert-partition-intersection[=yes/no(*)] Alert on raw DMG image files containing partition intersections--nocerts Disable authenticode certificate chain verification in PE files--dumpcerts Dump authenticode certificate chain in PE files--max-scantime=#n Scan time longer than this will be skipped and assumed clean (milliseconds)--max-filesize=#n Files larger than this will be skipped and assumed clean--max-scansize=#n The maximum amount of data to scan for each container file (**)--max-files=#n The maximum number of files to scan for each container file (**)--max-recursion=#n Maximum archive recursion level for container file (**)--max-dir-recursion=#n Maximum directory recursion level--max-embeddedpe=#n Maximum size file to check for embedded PE--max-htmlnormalize=#n Maximum size of HTML file to normalize--max-htmlnotags=#n Maximum size of normalized HTML file to scan--max-scriptnormalize=#n Maximum size of script file to normalize--max-ziptypercg=#n Maximum size zip to type reanalyze--max-partitions=#n Maximum number of partitions in disk image to be scanned--max-iconspe=#n Maximum number of icons in PE file to be scanned--max-rechwp3=#n Maximum recursive calls to HWP3 parsing function--pcre-match-limit=#n Maximum calls to the PCRE match function.--pcre-recmatch-limit=#n Maximum recursive calls to the PCRE match function.--pcre-max-filesize=#n Maximum size file to perform PCRE subsig matching.--disable-cache Disable caching and cache checks for hash sums of scanned files.
--基本扫描
##扫描文件
[root@localhost ~]# clamscan targetfile ##递归扫描home目录,并且记录日志
[root@localhost ~]# clamscan -r -i /home -l /var/log/clamav.log ##递归扫描home目录,将病毒文件删除,并且记录日志
[root@localhost ~]# clamscan -r -i /home --remove -l /var/log/clamav.log ##扫描指定目录,然后将感染文件移动到指定目录,并记录日志 -----重点扫描目录
[root@localhost ~]# clamscan -r -i /home --move=/tmp/clamav -l /var/log/clamav.logclamscan -r -i /etc --max-dir-recursion=5 -l /var/log/clamav-etc.logclamscan -r -i /bin --max-dir-recursion=5 -l /var/log/clamav-bin.logclamscan -r -i /usr --max-dir-recursion=5 -l /var/log/clamav-usr.logclamscan -r -i /var --max-dir-recursion=5 -l /var/log/clamav-var.log重点扫描报告
---------- SCAN SUMMARY -----------
Known viruses: 9141451 #已知病毒
Engine version: 0.102.4 #软件版本
Scanned directories: 498 #扫描目录
Scanned files: 738 #扫描文件
Infected files: 4 #感染文件!!!
Data scanned: 530.25 MB #扫描数据
Data read: 14131.60 MB (ratio 0.04:1) #数据读取
Time: 203.805 sec (3 m 23 s) #扫描用时