各种加密逻辑
在进行js逆向的时候,总会遇见一些人类无法直接能理解的东西出现。此时你看到的大多数,是被加密过的密文。
一. 一切从MD5开始
MD5是一个非常常见的摘要(hash)逻辑。其特点就是小巧、速度快、极难被破解(王小云女士)
所以md5,依然是国内非常多的互联网公司,选择的密码摘要算法
请求对象: url, method, header, body(page=2)scrapy 调度器. 为什么不直接存储请求对象.
特点:
-
这玩意不可逆。 所以摘要算法,就不是一个加密逻辑.
-
相同的内容,计算出来的摘要应该是一样的
-
不同的内容(哪怕是一丢丢丢丢丢不一样) ,计算出来的结果差别非常大
在数学上. 摘要其实计算逻辑就是hash.
hash(数据) => 数字
1. 密码2. 一致性检测
md5的python实现:
from hashlib import md5obj = md5()
obj.update("alex".encode("utf-8"))
# obj.update("wusir".encode('utf-8')) # 可以添加多个被加密的内容bs = obj.hexdigest()
print(bs)
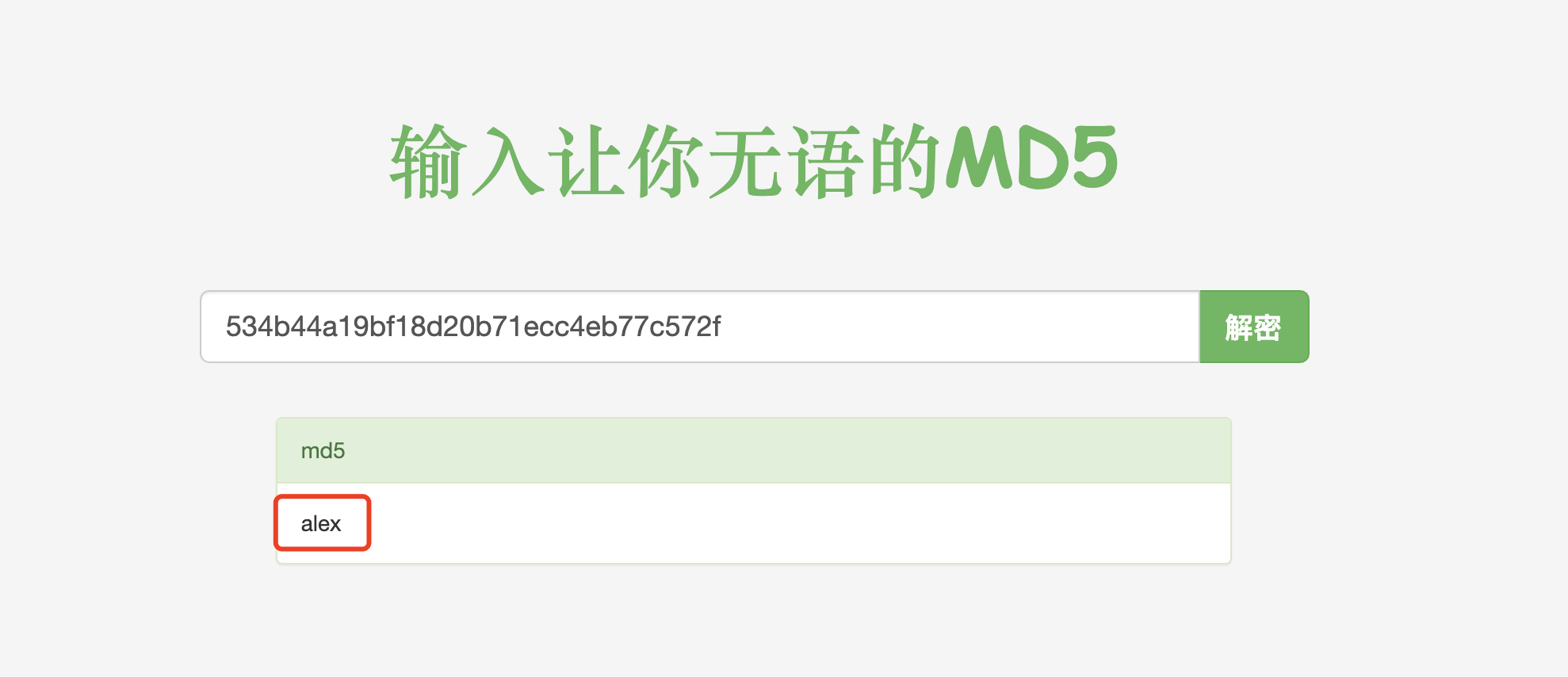
把密文丢到网页里,发现有些网站可以直接解密。但其实不然,这里并不是直接解密MD5,而是"撞库"
就是它网站里存储了大量的MD5的值. 就像这样:
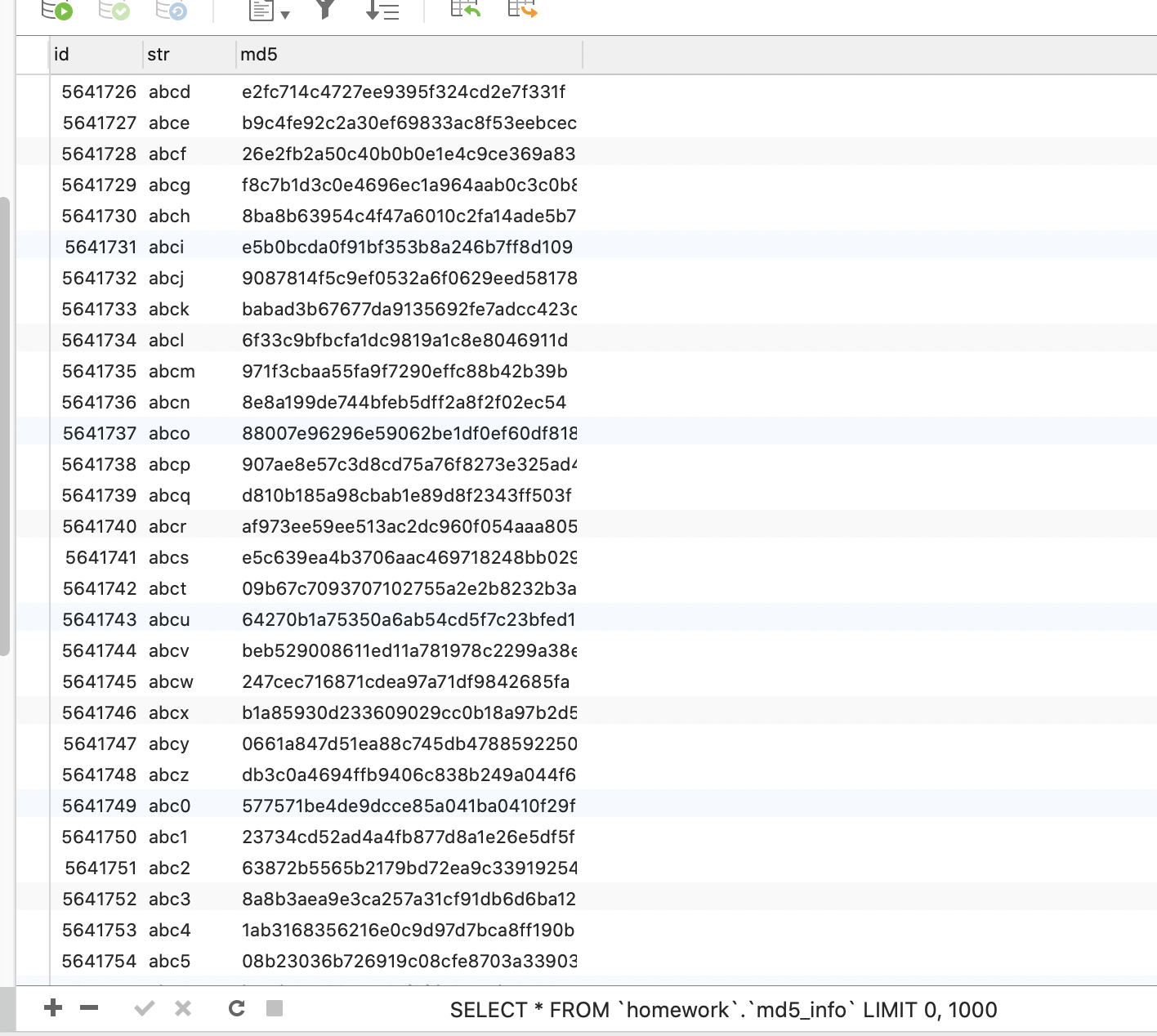
而需要进行查询的时候,只需要一条select语句就可以查询到了,这就是传说中的撞库。
如何避免撞库: md5在进行计算的时候可以加盐。加盐之后, 就很难撞库了
from hashlib import md5salt = "我是盐.把我加进去就没人能破解了"
obj = md5(salt.encode("utf-8")) # 加盐obj.update("alex".encode("utf-8"))bs = obj.hexdigest()
print(bs)
扩展:sha256
from hashlib import sha1, sha256
sha = sha256(b'salt')
sha.update(b'alex')
print(sha.hexdigest())
不论是sha1, sha256, md5都属于摘要算法. 都是在计算hash值. 只是散列的程度不同而已.
这种算法有一个特性:它们是散列,不是加密。而且由于hash算法是不可逆的,所以不存在解密的逻辑
二. URLEncode和Base64
在访问一个url的时候,总能看到这样的一种url
https://www.sogou.com/web?query=%E5%90%83%E9%A5%AD%E7%9D%A1%E8%A7%89%E6%89%93%E8%B1%86%E8%B1%86&_asf=www.sogou.com&_ast=&w=01019900&p=40040100&ie=utf8&from=index-nologin&s_from=index&sut=3119&sst0=1630994614300&lkt=0%2C0%2C0&sugsuv=1606978591882752&sugtime=1630994614300
此时会发现, 在浏览器上明明是能看到中文的. 但是一旦复制出来. 或者在抓包工具里看到的. 都是这种%. 那么这个%是什么鬼? 也是加密么?
非也,其实在访问一个url的时候,浏览器会自动的进行urlencode操作,会对请求的url进行编码
这种编码规则被称为百分号编码,是专门为url(统一资源定位符)准备的一套编码规则.
一个url的完整组成:
scheme://host:port/dir/file?p1=v1&p2=v2#anchorhttp ://www.baidu.com/tieba/index.html?name=alex&age=18参数: key=value 的形式 # 服务器可以通过key拿value此时,如果参数中出现一些特殊符号,比如'=' ,想给服务器传递 ‘a=b=c’ 这样的参数,必然会让整个URL产生歧义
所以,把url中的参数部分转化成字节,每字节的再转化成2个16进制的数字,前面补%.
看着很复杂,在python里,直接一步到位
from urllib.parse import urlencode, unquote, quote# 单独编码字符串 quote unqquote 解码
wq = "米饭怎么吃"
print(quote(wq)) # %E7%B1%B3%E9%A5%AD%E6%80%8E%E4%B9%88%E5%90%83
print(quote(wq, encoding="gbk")) # %C3%D7%B7%B9%D4%F5%C3%B4%B3%D4# 多个数据统一进行编码 urlencode
dic = {"wq": "米饭怎么吃","new_wq": "想怎么吃就怎么吃"
}print(urlencode(dic)) # wq=%E7%B1%B3%E9%A5%AD%E6%80%8E%E4%B9%88%E5%90%83&new_wq=%E6%83%B3%E6%80%8E%E4%B9%88%E5%90%83%E5%B0%B1%E6%80%8E%E4%B9%88%E5%90%83
print(urlencode(dic, encoding="utf-8")) # 也可以指定字符集# 一个完整的url编码过程
base_url = "http://www.baidu.com/s?"
params = {"wd": "大王"
}url = base_url + urlencode(params)
print(url) # http://www.baidu.com/s?wd=%E5%A4%A7%E7%8E%8B
解码
s = "http://www.baidu.com/s?wd=%E5%A4%A7%E7%8E%8B"print(unquote(s)) # http://www.baidu.com/s?wd=大王
base64
通常被加密后的内容是字节,而密文是用来传输的(不传输谁加密啊)
但在http协议里,想要传输字节是很麻烦的一个事儿。相对应的, 如果传递的是字符串就好控制的多,此时base64就应运而生了。
26个大写字母 + 26个小写字母 + 10个数字 + 2个特殊符号( + / ),组成了一组类似64进制的计算逻辑,这就是base64了。
import base64bs = "我要吃饭".encode("utf-8")
# 把字节转化成b64
print(base64.b64encode(bs).decode())# 把b64字符串转化成字节
s = "5oiR6KaB5ZCD6aWt"
print(base64.b64decode(s).decode("utf-8"))
注意:
b64处理后的字符串长度, 一定是4的倍数。如果在网页上,看到有些密文的b64长度,不是4的倍数,会报错
eg:
import base64s = "ztKwrsTj0b0"
bb = base64.b64decode(s)
print(bb)# 此时运行出现以下问题
Traceback (most recent call last):File "D:/PycharmProjects/rrrr.py", line 33, in <module>bb = base64.b64decode(s)File "D:\Python38\lib\base64.py", line 87, in b64decodereturn binascii.a2b_base64(s)
binascii.Error: Incorrect padding
解决思路:base64长度要求,字符串长度必须是4的倍数, 用 = 填充一下即可
import base64s = "ztKwrsTj0b0"
s += ("=" * (4 - len(s) % 4))
print("填充后", s)bb = base64.b64decode(s).decode("gbk")
print(bb)
三. 对称加密
所谓对称加密,就是加密和解密用的是同一个秘钥
就好比:我要给你邮寄一个箱子,上面怼上锁,提前我把钥匙给了你一把、我一把。
那么我在邮寄之前,就可以把箱子锁上,然后快递到你那里,你用相同的钥匙,就可以打开这个箱子
条件: 加密和解密用的是同一个秘钥。那么两边就必须同时拥有钥匙,才可以
常见的对称加密: AES、DES、3DES。 这里讨论AES、DES
3.1 AES
# AES加密
from Crypto.Cipher import AES"""
长度16: *AES-128*24: *AES-192*32: *AES-256*参数:MODE 加密模式. 常见的ECB, CBC以下内容来自互联网~~ECB:是一种基础的加密方式,密文被分割成分组长度相等的块(不足补齐),然后单独一个个加密,一个个输出组成密文。CBC:是一种循环模式,前一个分组的密文和当前分组的明文异或或操作后再加密,这样做的目的是增强破解难度。CFB/OFB:实际上是一种反馈模式,目的也是增强破解的难度。FCB和CBC的加密结果是不一样的,两者的模式不同,而且CBC会在第一个密码块运算时加入一个初始化向量。
"""aes = AES.new(b"alexissbalexissb", mode=AES.MODE_CBC, IV=b"0102030405060708")
data = "我吃饭了"
data_bs = data.encode("utf-8")# 需要加密的数据必须是16的倍数
# 填充规则: 缺少数据量的个数 * chr(缺少数据量个数)
pad_len = 16 - len(data_bs) % 16
data_bs += (pad_len * chr(pad_len)).encode("utf-8")bs = aes.encrypt(data_bs)
print(bs)
AES解密
from Crypto.Cipher import AESaes = AES.new(b"alexissbalexissb", mode=AES.MODE_CBC, IV=b"0102030405060708")
# 密文
bs = b'\xf6z\x0f;G\xdcB,\xccl\xf9\x17qS\x93\x0e'
result = aes.decrypt(bs) # 解密
print(result.decode("utf-8"))
3.2 DES
# DES加密解密
from Crypto.Cipher import DES# key: 8个字节
des = DES.new(b"alexissb", mode=DES.MODE_CBC, IV=b"01020304")
data = "我要吃饭".encode("utf-8")# 需要加密的数据必须是16的倍数
# 填充规则: 缺少数据量的个数 * chr(缺少数据量个数)
pad_len = 8 - len(data) % 8
data += (pad_len * chr(pad_len)).encode("utf-8")bs = des.encrypt(data)
print(bs)
# 解密
des = DES.new(key=b'alexissb', mode=DES.MODE_CBC, IV=b"01020304")
data = b'6HX\xfa\xb2R\xa8\r\xa3\xed\xbd\x00\xdb}\xb0\xb9'result = des.decrypt(data)
print(result.decode("utf-8"))
四.非对称加密
非对称加密,加密和解密的秘钥不是同一个秘钥。
需要两把钥匙:一个公钥(公开的秘钥, 对数据进行加密)、一个私钥(私密的秘钥, 对数据进行解密)
公钥发送给客户端 (发送端),发送端用公钥对数据进行加密,再发送给接收端,接收端使用私钥来对数据解密。
由于私钥只存放在接受端这边,所以即使数据被截获了,也是无法进行解密的
# 非对称加密的逻辑:1. 先在服务器端. 生成一组秘钥, 公钥/私钥2. 把公钥放出去,发送给客户端. 3. 客户端在拿到公钥之后. 可以使用公钥对数据进行加密.4. 把数据传输给服务器5. 服务器使用私钥,对数据进行解密.
常见的非对称加密算法: RSA、DSA等等。介绍一个:RSA加密,也是最常见的一种加密方案
4.1 RSA加密解密
4.1.1 创建公钥和私钥
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_v1_5
from Crypto import Random
import base64# 随机
gen_random = Random.new# 生成秘钥
rsakey = RSA.generate(1024)
with open("rsa.public.pem", mode="wb") as f:f.write(rsakey.publickey().exportKey())with open("rsa.private.pem", mode="wb") as f:f.write(rsakey.exportKey())
4.1.2 加密
# 加密
data = "我要吃饭了"
with open("rsa.public.pem", mode="r") as f:pk = f.read()rsa_pk = RSA.importKey(pk)rsa = PKCS1_v1_5.new(rsa_pk)result = rsa.encrypt(data.encode("utf-8"))# 处理成b64方便传输b64_result = base64.b64encode(result).decode("utf-8")print(b64_result)
4.1.3 解密
data = "e/spTGg3roda+iqLK4e2bckNMSgXSNosOVLtWN+ArgaIDgYONPIU9i0rIeTj0ywwXnTIPU734EIoKRFQsLmPpJK4Htte+QlcgRFbuj/hCW1uWiB3mCbyU3ZHKo/Y9UjYMuMfk+H6m8OWHtr+tWjiinMNURQpxbsTiT/1cfifWo4="# 解密
with open("rsa.private.pem", mode="r") as f:prikey = f.read()rsa_pk = RSA.importKey(prikey)rsa = PKCS1_v1_5.new(rsa_pk)result = rsa.decrypt(base64.b64decode(data), gen_random)print(result.decode("utf-8"))
五. 案例
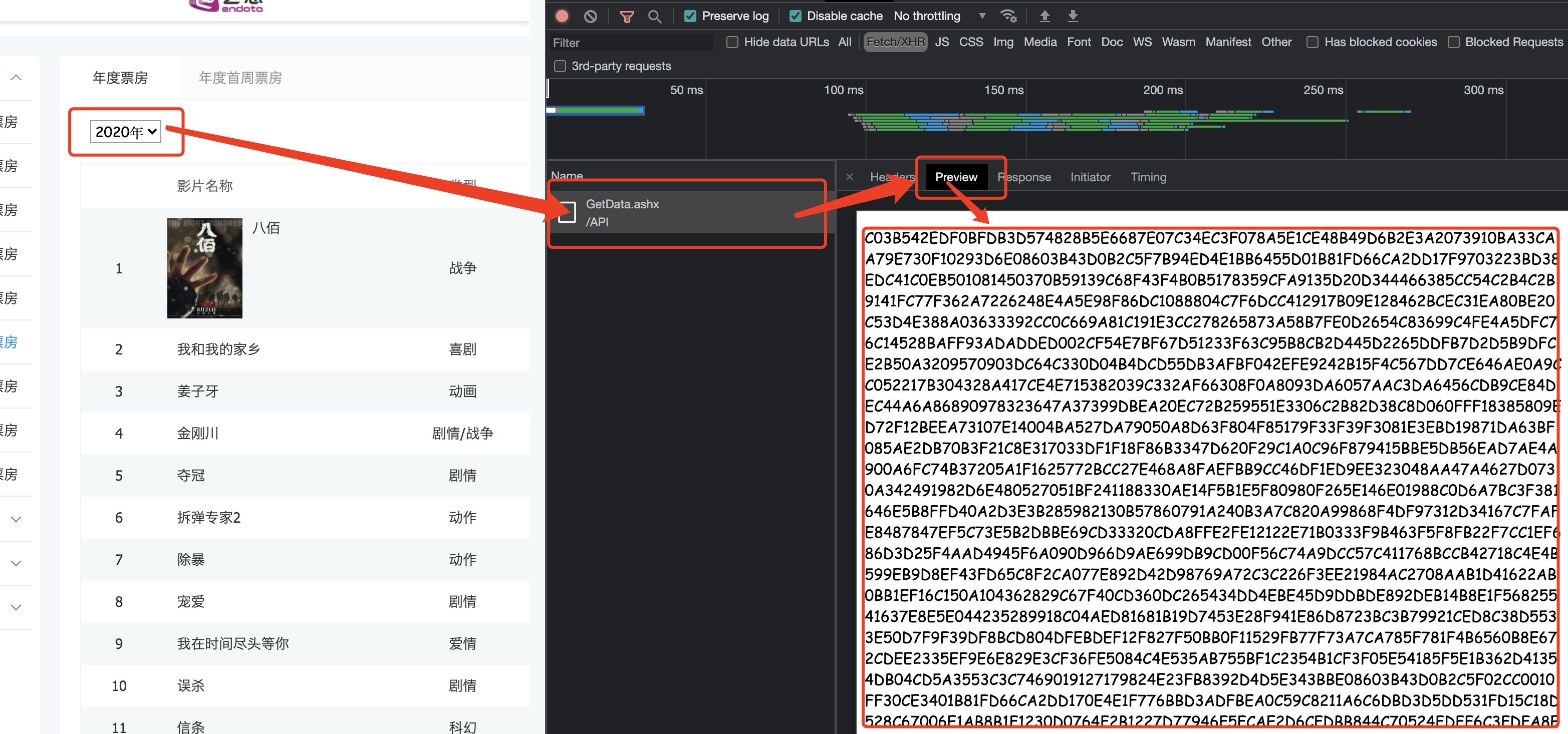
5.1 艺恩电影数据解密
以https://www.endata.com.cn/BoxOffice/BO/Year/index.html为案例. 来完成该网站数据解密
分析: 很明显,该网站的数据是经过加密的
接下来,到 Initiator (启动器,请求调用堆栈 看得到发送请求的 依次触发的文件) 里看看
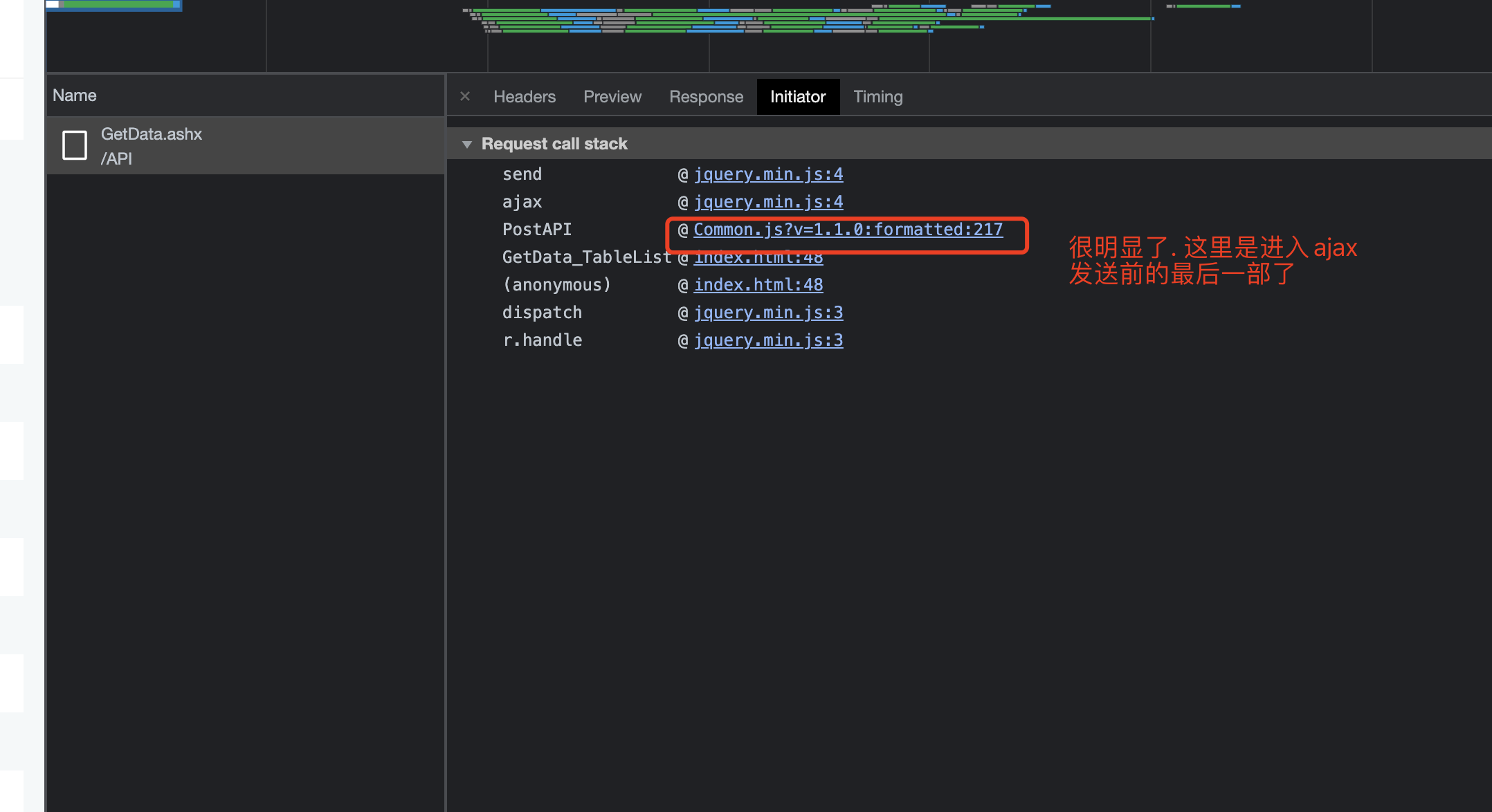
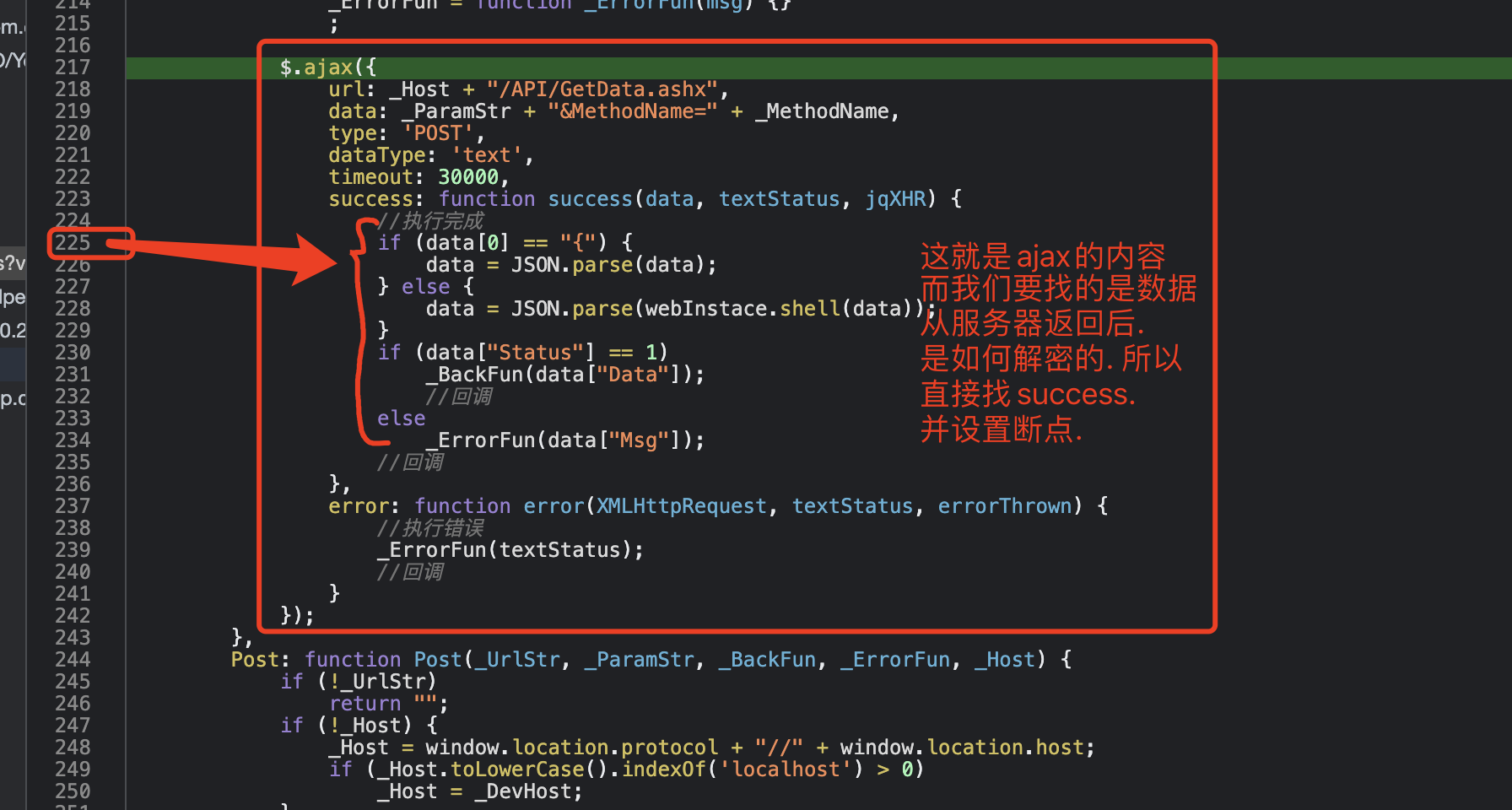
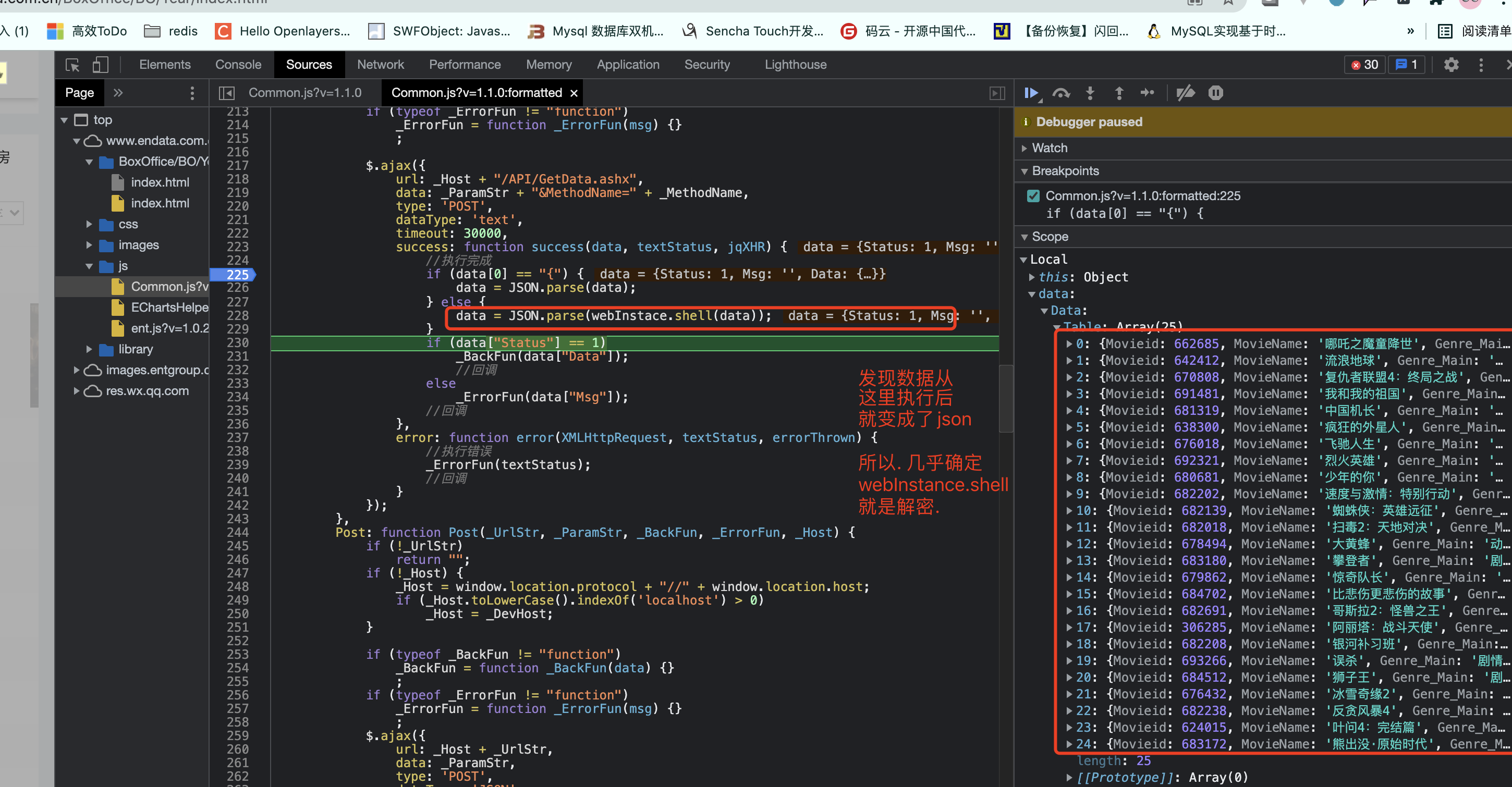
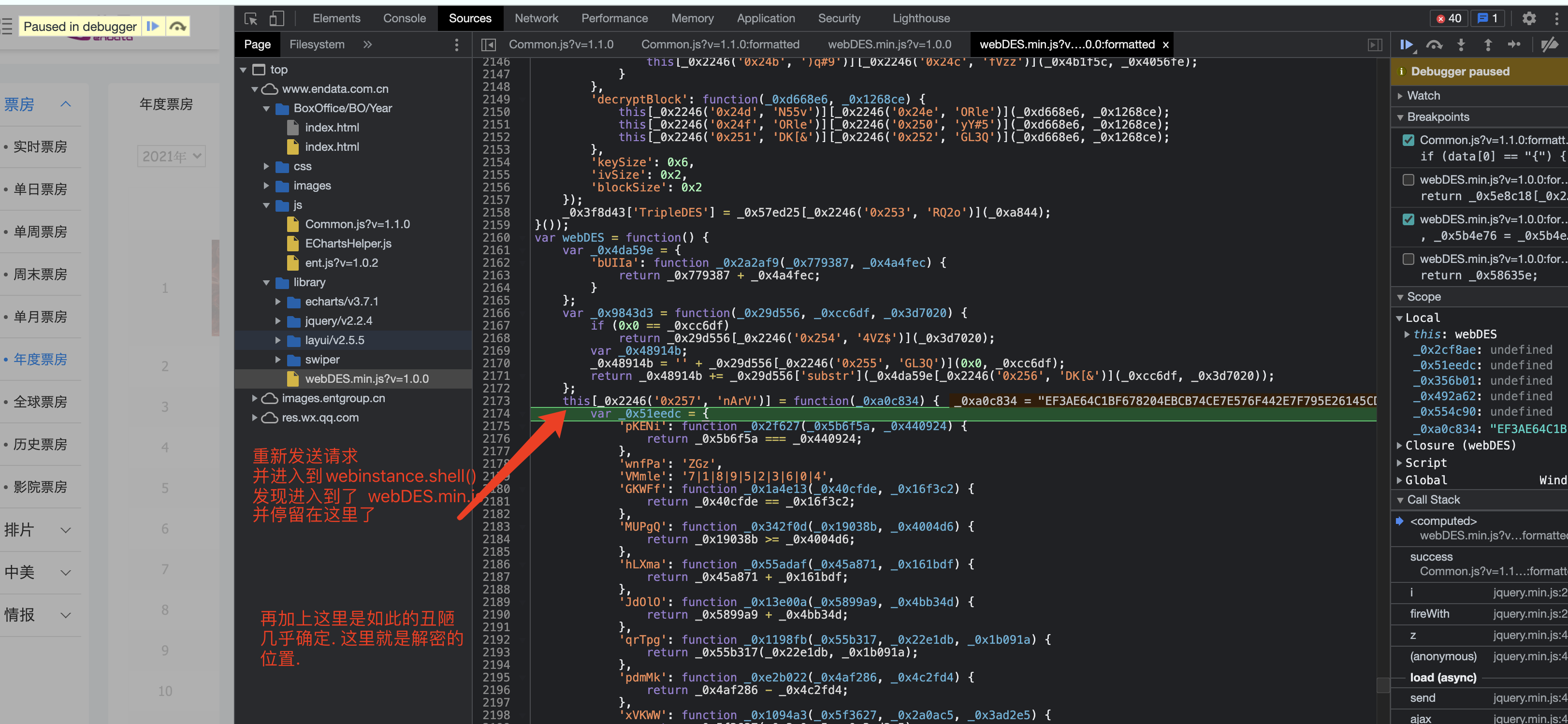
接下来就是逆向的过程了... 各位..还是看视频吧. 视频里有详细的分析过程.
给出完整破解代码
import binascii # 二进制和ascii之间转换
from Crypto.Cipher import DESdef func(a, b, c):if b == 0:return a[c:]d = a[:b] + a[b+c:]return ddef process(data):e = int(data[len(data)-1], base=16) + 9f = int(data[e], base=16)data = func(data, e, 1)e = data[f:f+8]data = func(data, f, 8)jiemi(data, str(e), str(e))def jiemi(data, key, iv):des = DES.new(key.encode("utf-8"), mode=DES.MODE_ECB)# de_text = base64.standard_b64decode(data)# 十六进制表示的二进制数据 -> 十六进制 -> 二进制print(binascii.a2b_hex(data))ee = des.decrypt(binascii.a2b_hex(data))print(ee.decode("utf-8"))if __name__ == '__main__':data = """BB95CA71E232FD88B71C758B19BDDDCB2BCF1E7ACCDC3B8777E875407841A1CE202F0F0028269913ADDA6050FED043DC8656C0F9FB3364603D5FB9C3B361B750AA36C06FC5500480DC8B3A1E0A994600FC0CEF28AF89450FC46C6E078FF9D3AA063D0303BE4A7CC74A3C70516ACE9F8944D7540071DF7DE33DB23B02B5A76D6AF455117F429EA2926F52C76F69CB9317F644A93A80D43FDB778C5E5B619578CBA12D958DE67163EFA55E1DB4C28D3D541FB7A4C426E2B592399B08BD67A3A4A23A953620B07EA643D69E6C1E93E8FB1971F9B95F4A71201149F60EBF38B3B86C042D786710415370A8514FC981E85B5D3C5198ACB740232AB600EF42623AA67703D9E43755F11E8B8DB2B3F5BCF8E833CA1DE7C1FC5DE615B949F421A16077DC964E4080795A37CE998736638753D181CD5D4B09FCB28F1671837114A55BCEC34F3905E9266B17B8C0B1C958F7BC245F5360937F4C3FA97DA9396A4B94E16CFCFA6C190B7527EC4E5DAD68C7C2641FCFAA93064487EE495A3BA567747EA8B1A504B45C2D186A661A66A287790959BB63321C3EFC500A3EEE7C0B5488149D960235C8A1751E2F3995DF11689353FFB4F92EE1B2A9ED66D12AE8DDC8AAE8CC120BBA64D93AA7C041BB6B5B1F752386E3B26ED20CC564C9BA498BE1FE0EEC80DA48DEA7CD92A52EA4764B55FB2FDAB5CF4D680B3E428C5C002AD0A12EBD3BE329F063E0FBBF9BBEB76CAD8C9CD10E2FE25AD1A9BC341BDC9F790616A1920AA9990D582E153393CCAAF65F8F5669C843D469B7EC692F41B3CCFD3A98D63153E7BF96A8268D338787E888F530285B52183523122230AD9F175667CD5E27E0A231A3BE5A9C24A28674FC768A9BA2338C890189E9C2CA8E608AA2470288E6FEEC64BDB6D06AA5E10681A5111D5E1FEDADBD16F12DED12EE99E8FCA112B8EC1C9E3EA5435315A7D2D14A7B9BBF5137010AB2A95E66B8FFA1695ACD708488A5620E1F147BFD985BC8EA097C836EC412B8B816E3F5936A23D82056212DA93DFDA7F7F6FE588338CF96CAD0AABB217C4F1C8646E1EB9A277874B7DE1C756362596B949B87AA00E23E301C6DCBCDBE1C9454E0A227F80F08EA86BA75B06FB7FD817DB9AE2729A0034DDDE18A213E4682C37A326A0FEF977DCC96A035E126AC71C754574A4D8FE0FF093BC14E34069AAC4C32DAF11CD687FE5766681C2181EE9C98514BD7AF44D79C97183F0E8CF60618F9B99FBAE66B139C8A0FEAD488E947D92092B5A80908F38B2DD73DC19C19550CF589661B1D8160C3568B8616025047318F889531F9CABB7AACAC62E5EA16C3804CD168C67F019A48CB0910F1EE3A2460B84251DB754038DEFE707463CB65C1666DFB25937A0C4BE17872A2DDE2090EB5687D09CD51AAF652FBE33A240A3B1F28617701E6EF6E733914BB32B05D1C0649C4ECA69D3075830DA732ED54DBC1F6A687EB13AE7505AD33F363A98241A0D30FAC9EB41D4FD53153B9403A14B3F71DDD6065FF7477EEED35A7E0F3E1CE0D545564AD812752817D32E52E5B08694252A69F25100CCD275D6C38F8AA3933D4F3FED4B2760CA0367A4E3FC7A4F15295050135F46F03C79914ACFE571527EC4E5DAD68C7CD1661A0FC37A62FC5FD275EBC1499F8EEA8B1A504B45C2D1233CF886DB4DC387959BB63321C3EFC5ABE261E2D0FF0E1E49D960235C8A1751451E687EAEBB700564D50B0C195DE84DAB29B668B737EC7E459AC26FBC734F5D7444C19860D9015D64AA91ED197D825957C2338ED354BE34AEABACDB4C32BF3A592838630E4FF8EF4A26611780CDC0F1AB0239DBAD1978A7BFA1587473E68FE2EF89B1144E3B6A99712C80A8BE7AE349695B250FDE76A54375C166A8767D41D838EFB9CB504C23563EA9E8EC3D1E94BDEE0791A86F1B31E9C81F872D38EB7F3AAC2593FF32DFCAECE1AC88882ED99F52F6466B2F437236C3241D0CACB5BBDC801AC086E0B2C0B87CE8158C0830A834ACF18EED58E6FA8B0E3DDA66031DFE0EC3C28A5F8D9CD9CD3A27EBE2F1F054A4EC9A108F283A0EC6698B66C2B05D1820D6ACCF5CB326100BDE4AD2D6221A818378DD1A18DAFCED301A9A39B85216D0370A047B1714A115A1E08A44217EE0A74AC18550D15370350F125734177A12B0BF26D079490D3A554232A1C738006CEBADCD6568A8D75801DD6D90BF6C2D8620033A98E1F9B93B9DFDA7BCE69DAB9AB241402929475CEAF6A8159CB1665965CE332E769D44CBEDF6C2902BE7755BBFEC2AD16669799D723493F8D4F8160E0507FBFABE103381917445735209BDEF1B373DBF5B9003947C952DC4150CE58CA6A08C112946C3A0684250C92F9727B92ED109394D4DB572F2324E01AE7D448A841D256D83360C70027E90F3EFF227D949E50B9F3C44141F66FDBE0413B43CF26912BEA8190633B2256927123E4E0CA56BADE27CF6A452AEBC574ED2CF00ADAC31534ECB8B8F7583E26126294025CFDA81D9B51453D2DEE57E0DAA501CE77328A5A3DE42966204659481C827CD0AD28EB502E0AF1DDC018155FD23CD6B34E395D1DC1492ED15DCCF4F2E9D5787B1A9CA775BA0AABFCAE959E9CE343BE15B3868761E6AC670E745C47A3CA77C8010CE5DF12FBA1FF47D1F3111502835E520BF1D4D07F7C589D6DBAEBBC5C3CA6BDE40A910A8FD98F1CDB7C1032DB93A4A4603950D9B2BC2EDB301F3B8A3733803B0363696805FA0C890189E9C2CA8E608AA2470288E6FEEC64BDB6D06AA5E10B9960959DB04E0FC6B4AE42919E6362D9E8FCA112B8EC1C9E3EA5435315A7D2D41F74C4DC73C4C32AB2A95E66B8FFA1677B8260867324907A601F44EB2F37C7BCF00ADAC31534ECB8B8F7583E26126294025CFDA81D9B514E24A4786C16FAE911CE77328A5A3DE42966204659481C827CD0AD28EB502E0AF1DDC018155FD23CD6B34E395D1DC1492ED15DCCF4F2E9D57017B8E2FD4ACA194414AC4306FFDDD0ECBAEEBD0DD9BEE40672653571AB681E1DD4BB5C3895A3AD65890B8F97FBF9C88E520BF1D4D07F7C589D6DBAEBBC5C3CA0AA59350F5B06A9CF1CDB7C1032DB93A600F905CAFDCC89426064368226E0398DA90A11148933932FBAE66B139C8A0FE40A1074779B3381A5A80908F38B2DD73A95E97608666FC205A5816B287D14A95616025047318F88974AB0F6F328BA18C2E5EA16C3804CD16649D903C38FF661E0F1EE3A2460B84251DB754038DEFE707463CB65C1666DFB25937A0C4BE17872A4D4793FB5D321EA59CD51AAF652FBE33A240A3B1F28617701E6EF6E733914BB32B05D1C0649C4ECA69D3075830DA732ED54DBC1F6A687EB113EF467AD942DE82433568E6C35F7F8E69C80EBCE3D0525690FE7F11E65866B52618E95AFC9AEAA6AC154CFAE9BAE61312752817D32E52E55B34B1FF2C048783FF73DCB5363871110B3326011985285A42FD2256723731435B9789386DF396F4B7E907756E3EB3BA14D41724B9938BE3E08E5416A728F2A1D9AD54738DA5F74F8CE3A2504A481D81616025047318F889FF5C244FEF7A458AAEC30C56BF88A048AB2A95E66B8FFA1677B8260867324907E1F147BFD985BC8EA097C836EC412B8B816E3F5936A23D825DB7BDA9B61D75577F6FE588338CF96CAD0AABB217C4F1C8646E1EB9A277874B7DE1C756362596B949B87AA00E23E3015D490874901DE069CC9E784D7C8167F87E9705A623E1DC9E4506DE4DE279B83475D14D9CD01A927321BFB61307DBAB51035E126AC71C754574A4D8FE0FF093BCDA0F829386AA0119AF11CD687FE576661F4C9E198A9BF44453B9BCD8DDF4F9DFAF4CD6FADF2A0EFDFBAE66B139C8A0FEB5298E04873FAF465A80908F38B2DD7346A3AB0F1D88AE6A3C7E4B72445DF2059E8FCA112B8EC1C991F981BCD6E9013914283CA7809B0D10AB2A95E66B8FFA1677B8260867324907E1F147BFD985BC8EA097C836EC412B8B816E3F5936A23D82242CAC4E1D58DFB67F6FE588338CF96CAD0AABB217C4F1C8646E1EB9A277874B7DE1C756362596B949B87AA00E23E3015D490874901DE0696DFA53B227EFCFEFDD39AE8E57EB577B9176ED83D6431466D9F3E9DB9C0C28549CBDCBF30D9D2825035E126AC71C754574A4D8FE0FF093BCCCEFCB727BA620B2AF11CD687FE57666F3633A86CF7124A5E782C0A0236A3B4AAE8E269FE0E302F8FBAE66B139C8A0FEAD488E947D92092B5A80908F38B2DD73633125B1DBA8CA0390DFF227F8D5F0D4270F87A346DD8D7777F104C4E22319AB41F74C4DC73C4C32AB2A95E66B8FFA1677B8260867324907E1F147BFD985BC8EA097C836EC412B8B816E3F5936A23D82ED937131BC18FCAF7F6FE588338CF96CAD0AABB217C4F1C8646E1EB9A277874B7DE1C756362596B949B87AA00E23E3015D490874901DE069AC018A4AF210397DEC31572E1772A5DE68760C413C81BC650E3A2546AAE47214A0723D94F61CDFB6035E126AC71C754574A4D8FE0FF093BC3CE90A942BC9A267AF11CD687FE57666F8AA317690E44ED5F1F5535D6515E747EE0A07D93CEB4AF2B7E907756E3EB3BA17664C4C9DEFDE32A7056D8B191D39B37EBDC765807597018950115302DD3A9B616025047318F889D00A2A799AA39A690A256C4D657A2CB7AB2A95E66B8FFA1677B8260867324907E1F147BFD985BC8EA097C836EC412B8BEDF7348D88FA841C4DBCF56EA2F0D9037F6FE588338CF96CAD0AABB217C4F1C8646E1EB9A277874B7DE1C756362596B949B87AA00E23E3015D490874901DE069925BBE4AABDDC6D5B1C4CE3F72F804EF9BF7363B37B6F6D8577AAFD3D9FB3D2786D6B026B51B877A035E126AC71C754574A4D8FE0FF093BCF07C1B608B727A0CAF11CD687FE57666E1E117A1853A9FB55DF08E0D036D7D917A70F27FFD1D2239E8158C0830A834AC70FA36D3655C5BBE9BF05D89E933E74BC28A5F8D9CD9CD3A65DE8659196B73AF959BB63321C3EFC5ABE261E2D0FF0E1E49D960235C8A1751451E687EAEBB7005730CE729EB0318CAAB29B668B737EC7E459AC26FBC734F5DBE252FF94BDA41E675192671BFA50C0857C2338ED354BE34AEABACDB4C32BF3A592838630E4FF8EF4A26611780CDC0F1AB0239DBAD1978A7BFA1587473E68FE234BC03311BE64FDD8D16CB98901ACA1CF18367A85B5C7EE32D4E08C530A378B48687343D377740591410021C7FECFB1EEE0791A86F1B31E920E6CE797374C688E4046D6659B5E7BBE1AC88882ED99F523390FB264826B70FFCECC22A8B51BEAAD5C7DB122168126B2F9727B92ED10939E1ED793B9BDCCCFB125285EA628230F583360C70027E90F3894262EC2FDBF79B9A108F283A0EC669E4418550BB47F7E5ACCF5CB326100BDE6B26049D936BE2CC3FFB4F92EE1B2A9ED66D12AE8DDC8AAE8CC120BBA64D93AA7C041BB6B5B1F75292BBAC28FEDD8FED4C9BA498BE1FE0EEC80DA48DEA7CD92A52EA4764B55FB2FDAB5CF4D680B3E428C5C002AD0A12EBD3BE329F063E0FBBF988D38205D195E158B41152D0A44EF17D2DD62B7E16212818EC0BAD6C5663DD1404D9C33BCB15712659E45B7EB74488D71B3CCFD3A98D6315A8816B73919ACD39100AC0519A6E42F22183523122230AD984CBBC8A33A398F0D4038C5799D60BB374E859046B362BA3EF84BB56F1426FB38A4BB1B673C1CD4A12A420C6EDFE64492A170AA4626ACA1490D5A3802BB6C5D8A64F836F68F8CECC2B072969E237DB1E0D43FDB778C5E5B639806A514B4665F667163EFA55E1DB4C28D3D541FB7A4C426E2B592399B08BD67A3A4A23A953620B07EA643D69E6C1E93E8FB1971F9B95F4A71201149F60EBF38B3B86C042D786710415370A8514FC981E85B5D3C5198ACB740232AB600EF42623AA67703D9E43753A2FEF37ADE3045C6C07652F260125EA7CD253EA717EE222E8A6AE60FF02A6A29C10AC9D0F134D52753D181CD5D4B09FCB28F1671837114AE8FD05DDB01347D966B17B8C0B1C958FCE712FF5C4F39582EF84BB56F1426FB38A4BB1B673C1CD4A5905CCDF47FB190C2A170AA4626ACA1459901C16526A7DB16DDC02368BA29D342629FE793C9285D30D43FDB778C5E5B6263F20252F7EAE10F6A452AEBC574ED2CF00ADAC31534ECB8B8F7583E26126294025CFDA81D9B514033E1DA16E0D6E2EDAD574660443C7B9966204659481C827CD0AD28EB502E0AF1DDC018155FD23CD6B34E395D1DC1492ED15DCCF4F2E9D5787B1A9CA775BA0AA301F074A41B09C10F499115961E8BCBA2E4C2BCD5E02C1AFB278FAAD8A5C1B8F378F43386163FFF6E520BF1D4D07F7C589D6DBAEBBC5C3CA58F4666BE22C60CBF1CDB7C1032DB93A68D5FD9E0242B2AAC4AE55BF4518A9094FA25D978F37D88698C3646292167449B7E907756E3EB3BAABAD6BCC780E4D722EF8636B8207C789BE65F9F20C180B36560EFDC6845569CA616025047318F889B5627A35D6ADA7552E5EA16C3804CD16FF3CBBE1641ED1060F1EE3A2460B84251DB754038DEFE707463CB65C1666DFB25937A0C4BE17872A4D4793FB5D321EA59CD51AAF652FBE33A240A3B1F28617701E6EF6E733914BB32B05D1C0649C4ECA69D3075830DA732ED54DBC1F6A687EB113EF467AD942DE82433568E6C35F7F8E34DB487999A43722A42612F9C87B74E86F4C225322A6B95F5FA8DBAFEC6A86FA12752817D32E52E526A256CAE0BDF92C489A3C26DF4611660B3326011985285AD85AEFD6FDFB3CF014BB6EACD809D727E8158C0830A834ACF18EED58E6FA8B0E3DDA66031DFE0EC3C28A5F8D9CD9CD3A8A6A2F55AC3BAC2B959BB63321C3EFC5D7DBBCEDAB91121F49D960235C8A1751451E687EAEBB7005730CE729EB0318CAAB29B668B737EC7E459AC26FBC734F5D7444C19860D9015DC9BE46BA8C7AA43757C2338ED354BE34AEABACDB4C32BF3A592838630E4FF8EF4A26611780CDC0F1AB0239DBAD1978A7BFA1587473E68FE29D9822CEEBA91EB0232F1980678945BEB80F1813FBCCC379C0575B46E785F9C887830B3F723381B9B30515FC666EB8DBEE0791A86F1B31E940EA8BBAA6A33A3C1B5DDC9FB5F858DFE1AC88882ED99F52732E823ABD0B99266196CF3C68AEB770527EC4E5DAD68C7C8A0DBC920C874289DE5AB4E2D55D4804EA8B1A504B45C2D1A4E0A78E4F53A9BBEBB7602D39E849606B948890C7374840DDAC9159048DF564649D903C38FF661E0F1EE3A2460B84251DB754038DEFE707463CB65C1666DFB25937A0C4BE17872A1812F285E1956F769CD51AAF652FBE33A240A3B1F28617701E6EF6E733914BB32B05D1C0649C4ECA69D3075830DA732ED54DBC1F6A687EB13AE7505AD33F363AF7F3C0B0F2BF265A576BA40BC1FF1F1C5E4031404E60275802625CFB9A91F08C3E1CE0D545564AD812752817D32E52E57890E43643956C90FF73DCB5363871117929489C3A49D2D69636606C0DE4CBE0EF84BB56F1426FB38A4BB1B673C1CD4A150A5AC4F5C91398F045BE8E4E7FF45C1DF7DE33DB23B02BDB684E633911D9143C44141F66FDBE0485325C6E1516D547190633B225692712EAAD58F14667BB31AB19346E5E7CB67A2C89DC7AF56F53B5047B1714A115A1E08A44217EE0A74AC1D4CC67E203D866CD5734177A12B0BF26D079490D3A554232A1C738006CEBADCD6568A8D75801DD6D90BF6C2D8620033A98E1F9B93B9DFDA7BCE69DAB9AB24140D712C263959F3D86F9C82368F6F563DFA4AA1A75046DEB07C93B9FC3258E0F733B1B0DDFD60DECBDD4F8160E0507FBFABE1033819174457387C72C91CC1FC9FB5B9003947C952DC4A97202EF1F394DC78B1913BB7F73668B9AF5A21903708BB0FF9D3AA063D0303B10DBACD99CE24DE49A795002212705C51DF7DE33DB23B02B95F0FE9899782C0C3C44141F66FDBE04E5FE403075DAF970190633B2256927120AD527349FD5BE3EDD1A18DAFCED301A9A39B85216D0370A047B1714A115A1E08A44217EE0A74AC176B2205F658155AA5734177A12B0BF26D079490D3A554232A1C738006CEBADCD6568A8D75801DD6D90BF6C2D8620033A98E1F9B93B9DFDA7BCE69DAB9AB241404FFFE180CA04A1CA1D5799E281A0D976F5F87CDC93940A3793CDD54147241E24A6ECD683DD48F6CED4F8160E0507FBFA59685C3E9FE5919931FB5C1F26DE2EF65B9003947C952DC42B4B52B1E1422177E6367AD9F82A5B842F9727B92ED10939E1ED793B9BDCCCFBA285FDAF205A97C883360C70027E90F3E0AD10D8E244C5859A108F283A0EC6692300CA78EFB1C810ACCF5CB326100BDE7B7572132E8DD6EA8588DBEB2A9915DBC2956D781AF560F28CC120BBA64D93AA7C041BB6B5B1F7526670F160CA7248AA4C9BA498BE1FE0EEC80DA48DEA7CD92A52EA4764B55FB2FDAB5CF4D680B3E428C5C002AD0A12EBD3BE329F063E0FBBF988D38205D195E158A51161601072E7BA6A7BF4BC01A6AB1599A59972BAA5DB345C7E6F624CC7A91F873188C48AFE02DE1B3CCFD3A98D6315F948D1D944E2EC7B5D3519A652388EC32183523122230AD93EAE96299EFE09E550E11D244658141DA4AE42E98DFAB55B0CE49AECE56C95AEB7E907756E3EB3BAABAD6BCC780E4D722EF8636B8207C789F5CF931C25657252CD0B80599D612B38616025047318F889EAF442FB833A0DE4D8FABE15A561310AAB2A95E66B8FFA162AD4D9A4CA339BC004D421F162767523A097C836EC412B8B816E3F5936A23D8235FE44809B75EFA57F6FE588338CF96CAD0AABB217C4F1C8646E1EB9A277874B7DE1C756362596B949B87AA00E23E3015D490874901DE06900B47779801159ED09DAA66235343ED7E62F9F2105AB5E75A53CBE5B02CC27A359B1B7273C79375A035E126AC71C754574A4D8FE0FF093BCC69CBC4ACA3FE291AF11CD687FE57666D2135483AAC3969BB68E075C73055510FF9D3AA063D0303BE4A7CC74A3C70516CB8FD925E00C28A21DF7DE33DB23B02BE430FEAEE9D5BE853C44141F66FDBE04826FA7F6BAA451BD190633B22569271216F372A5CAC4C59AF6A452AEBC574ED2CF00ADAC31534ECB8B8F7583E26126294025CFDA81D9B5141C691927E798BE3DE10CE475A92E59EF966204659481C827CD0AD28EB502E0AF1DDC018155FD23CD6B34E395D1DC1492ED15DCCF4F2E9D5787B1A9CA775BA0AA2796E63311615D51EB98E4DA5BDD38E1126CF3D39CA1C6D999110275DACABA9E8220DC566AE0AEF5773B9E0DE18A163ED833C30B73D5FE1FF3A78353E3239B7DD03434631610158B"""process(data)
5.2 中大网校登录
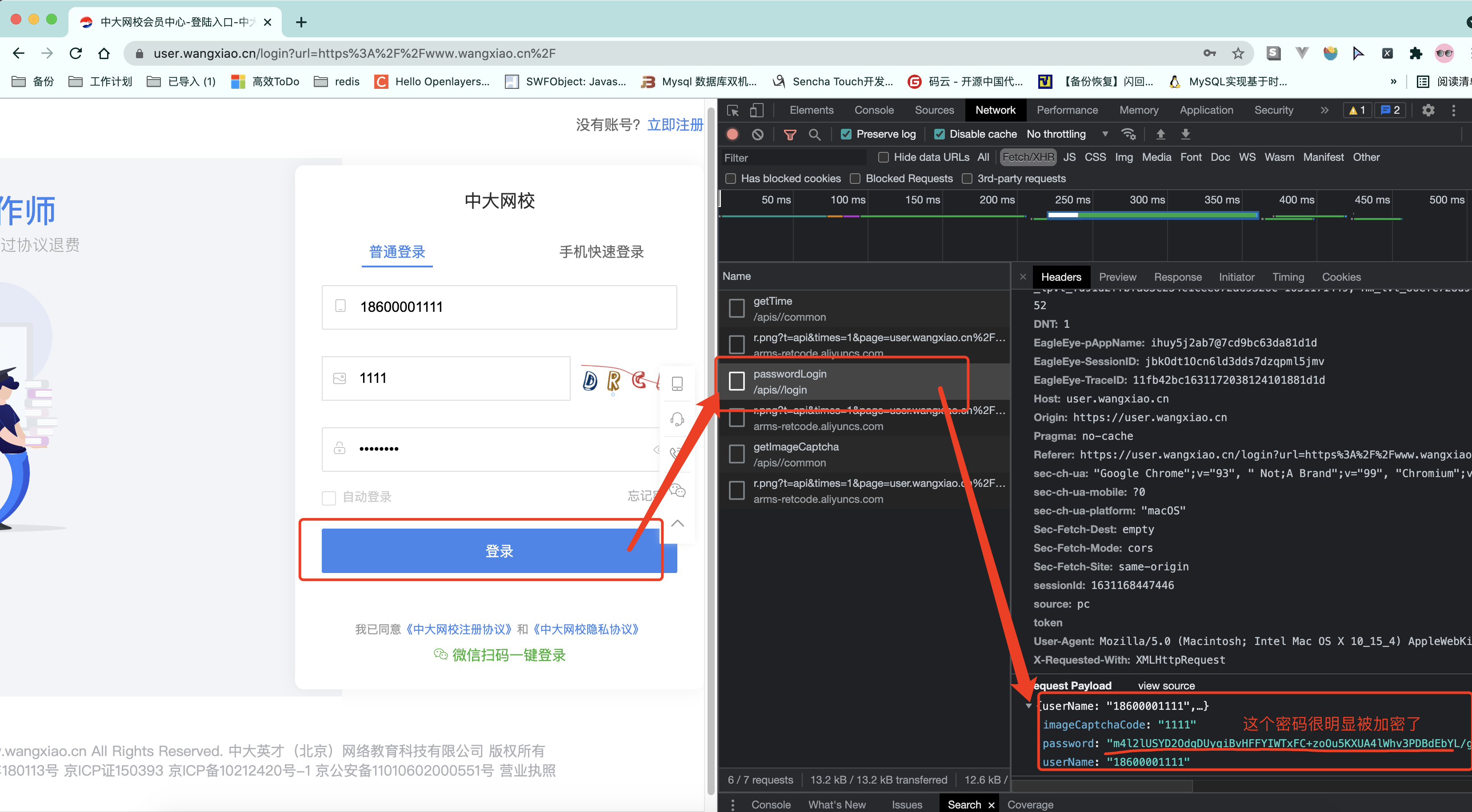

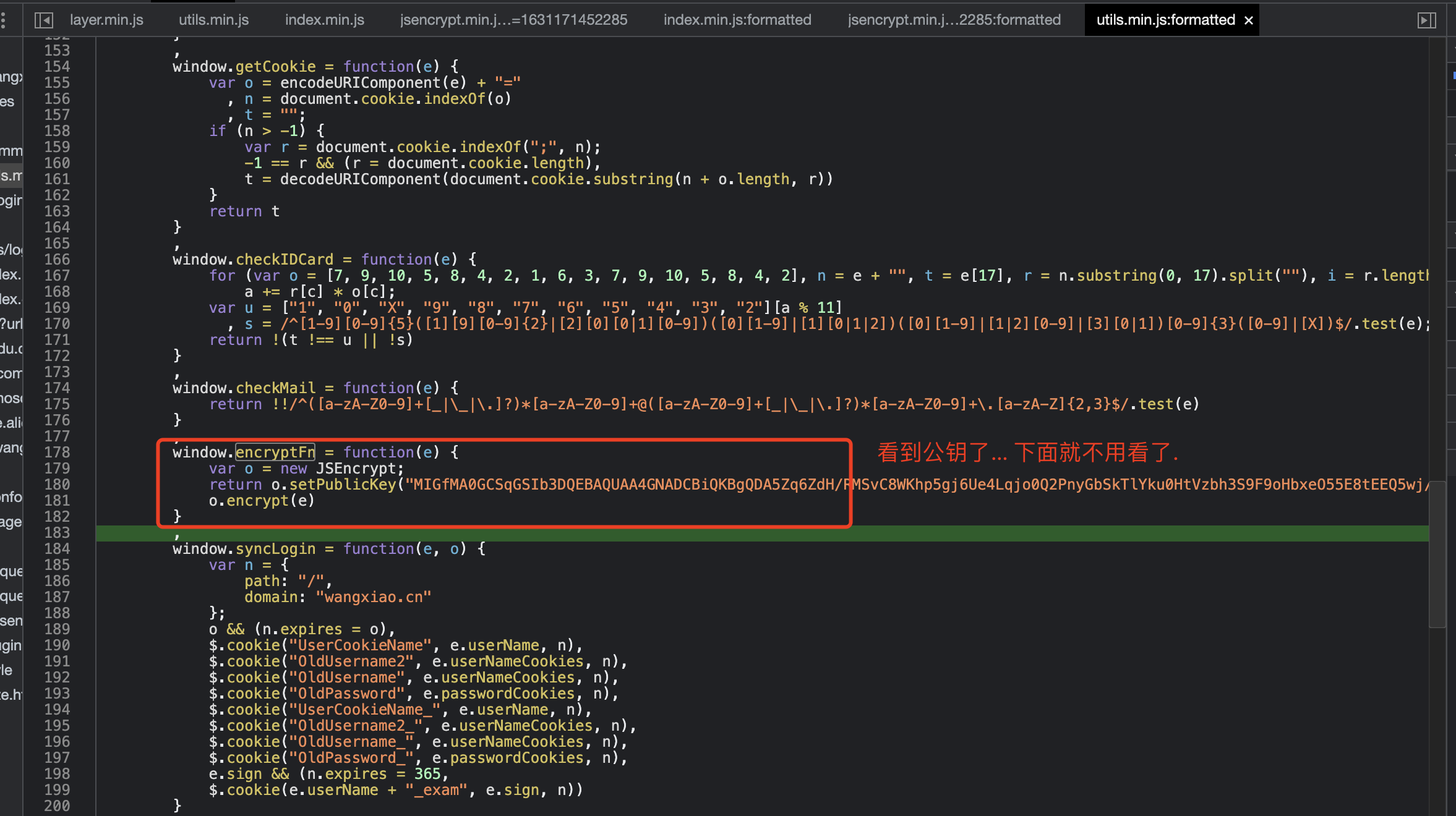
接下来开始逆向试试吧. 从登录位置开始,第一个事儿要搞定的,是那个烦人的验证码
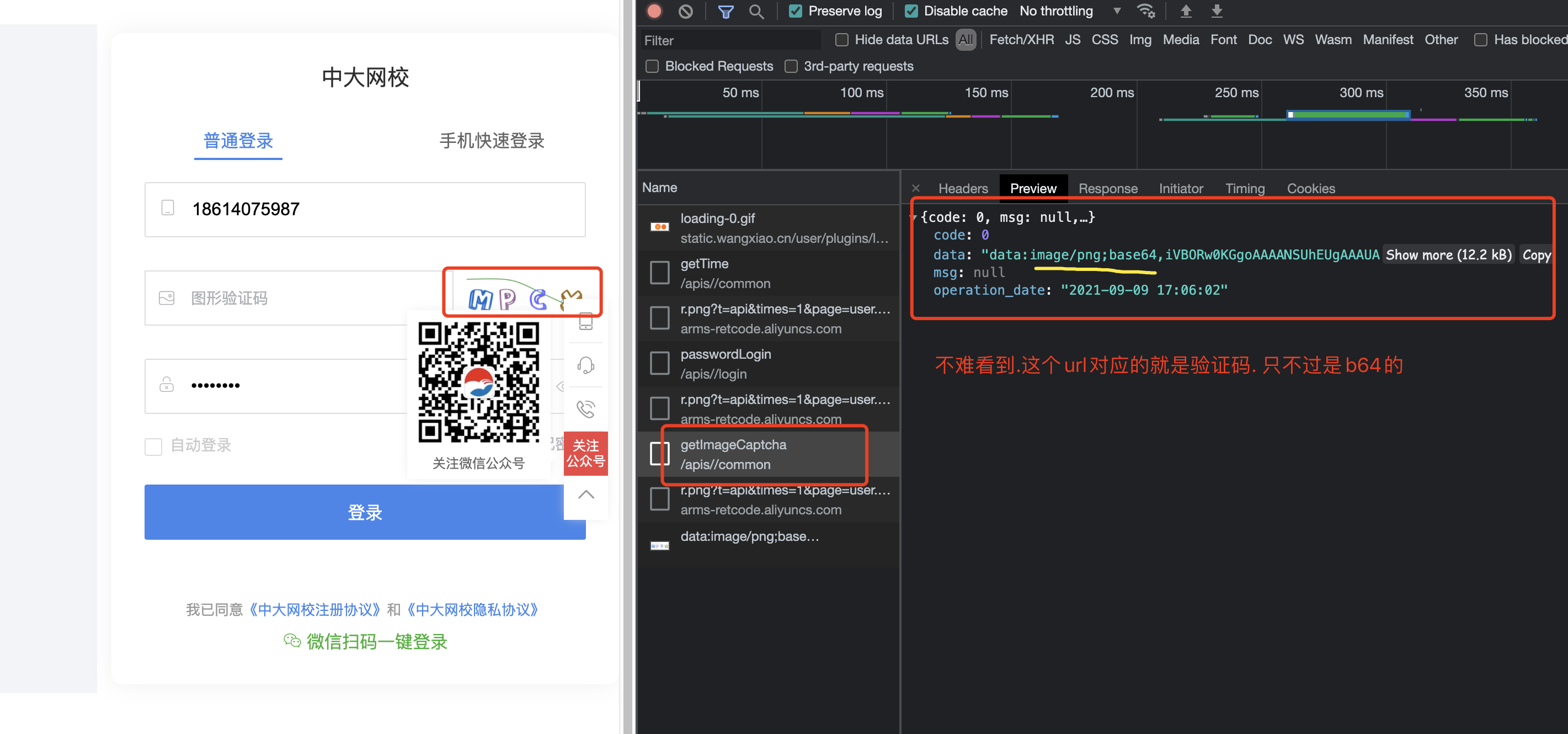
但是这个请求是需要cookie的,想想也应该如此。因为服务器要知道这张图片给哪个客户端使用了。就必须借助cookie,来判别不同的客户端.
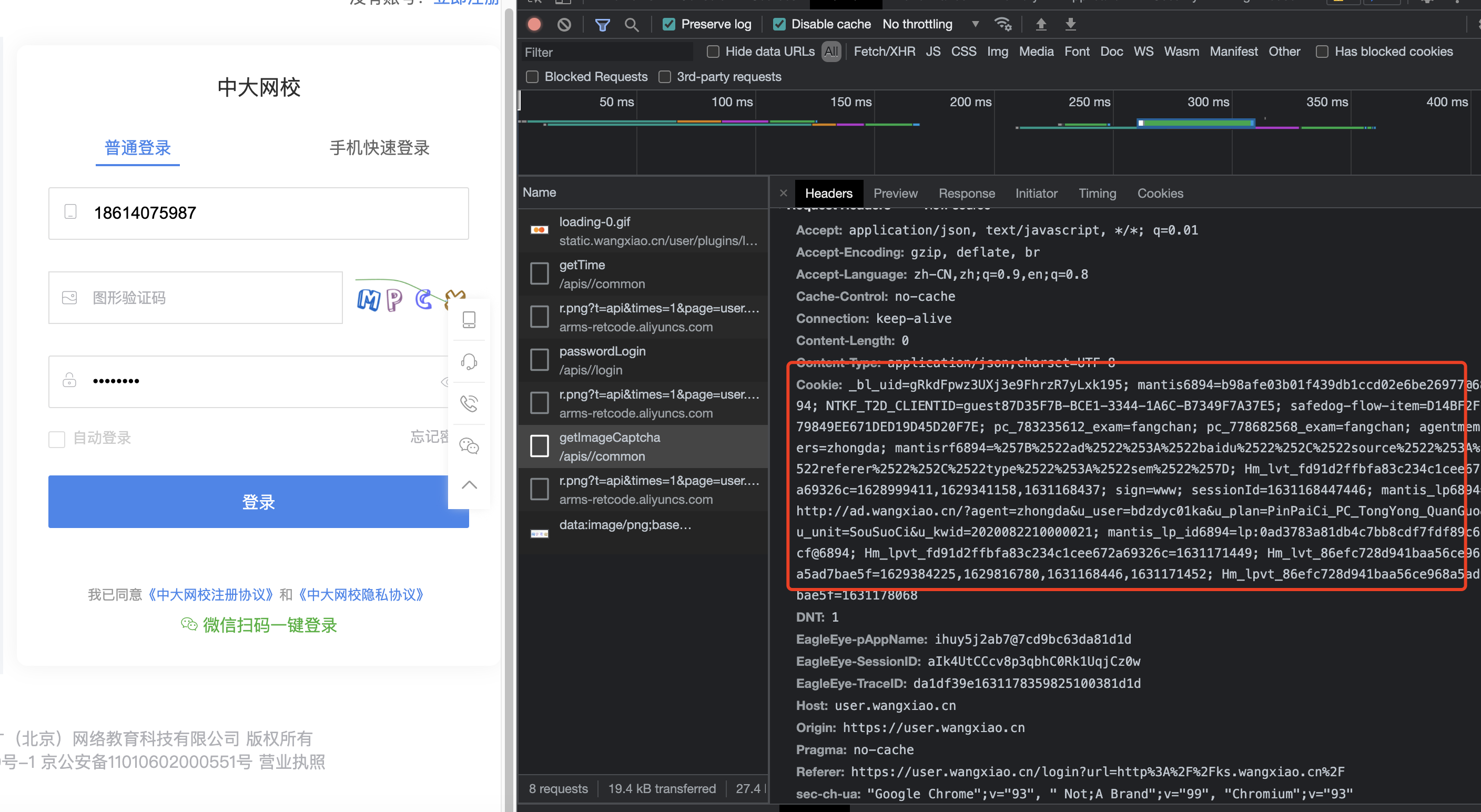
所以. 整个流程应该是:
- 进入登录页,加载到cookie
- 访问验证码ur,获取到验证码,并完成破解
- 访问getTime api,虽然不知道它用来做什么, 但是在后续的密码加密时,是需要这个api返回的data
- 准备好用户名和密码,对密码进行加密
- 发送登录请求
- 得到的结果处理(加入到cookie中)
代码:
import requests
import json
import time
from Crypto.Cipher import PKCS1_v1_5
from Crypto.PublicKey import RSA
import base64def base64_api(img, uname='q6035945', pwd='q6035945', typeid=3):data = {"username": uname, "password": pwd, "typeid": typeid, "image": img}result = json.loads(requests.post("http://api.ttshitu.com/predict", json=data).text)if result['success']:return result["data"]["result"]else:return result["message"]def enc(s):key = "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDA5Zq6ZdH/RMSvC8WKhp5gj6Ue4Lqjo0Q2PnyGbSkTlYku0HtVzbh3S9F9oHbxeO55E8tEEQ5wj/+52VMLavcuwkDypG66N6c1z0Fo2HgxV3e0tqt1wyNtmbwg7ruIYmFM+dErIpTiLRDvOy+0vgPcBVDfSUHwUSgUtIkyC47UNQIDAQAB"rsa_key = RSA.importKey(base64.b64decode(key))rsa_new = PKCS1_v1_5.new(rsa_key)mi = rsa_new.encrypt(s.encode("utf-8"))return base64.b64encode(mi).decode("utf-8")session = requests.session()
session.headers = {'Referer' : "https://user.wangxiao.cn/login?url=http%3A%2F%2Fks.wangxiao.cn%2F","Content-Type": "application/json;charset=UTF-8","User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36"
}login_url = "https://user.wangxiao.cn/login?url=http%3A%2F%2Fks.wangxiao.cn%2F"# 进入登录页面(目的: 加载到第一波cookie)
session.get(login_url)
time.sleep(1)resp = session.post("https://user.wangxiao.cn/apis//common/getImageCaptcha")dic = resp.json()
operation_date = dic['operation_date']
img_data = dic['data'].split(",")[1]
verify_code = base64_api(img_data)# 走登录流程
# 1.getTimeget_time_resp = session.post("https://user.wangxiao.cn/apis/common/getTime")
get_time_dic = get_time_resp.json()
get_time = get_time_dic['data']# 2. 登录
login_verify_url = "https://user.wangxiao.cn/apis/login/passwordLogin"username = "你的账号"
password = "你的密码"data = {"imageCaptchaCode": verify_code,"password": enc(password+get_time),"userName": username,
}resp = session.post(login_verify_url, data=json.dumps(data))dic = resp.json()['data']
"""window.syncLogin = function(e, o) {// util.jsvar n = {path: "/",domain: "wangxiao.cn"};o && (n.expires = o),$.cookie("UserCookieName", e.userName, n),$.cookie("OldUsername2", e.userNameCookies, n),$.cookie("OldUsername", e.userNameCookies, n),$.cookie("OldPassword", e.passwordCookies, n),$.cookie("UserCookieName_", e.userName, n),$.cookie("OldUsername2_", e.userNameCookies, n),$.cookie("OldUsername_", e.userNameCookies, n),$.cookie("OldPassword_", e.passwordCookies, n),e.sign && (n.expires = 365,$.cookie(e.userName + "_exam", e.sign, n))//index.jskeepOurCookie12("autoLogin",null) ;keepOurCookie12("userInfo",JSON.stringify(res.data)) ;keepOurCookie12("token",res.data.token) ;}
"""session.cookies['UserCookieName'] = dic['userName']
session.cookies['OldUsername2'] = dic['userNameCookies']
session.cookies['OldUsername'] = dic['userNameCookies']
session.cookies['OldPassword'] = dic['passwordCookies']
session.cookies['UserCookieName_'] = dic['userName']
session.cookies['OldUsername2_'] = dic['userNameCookies']
session.cookies['OldUsername_'] = dic['userNameCookies']
session.cookies['OldPassword_'] = dic['passwordCookies']
session.cookies['autoLogin'] = "null"
session.cookies['userInfo'] = json.dumps(dic)
session.cookies['token'] = dic['token']data = {"examPointType": "","practiceType": "2","questionType": "7","sign": "jz1","subsign": "8cc80ffb9a4a5c114953","top": "30"
}
resp = session.post('http://ks.wangxiao.cn/practice/listQuestions', data=json.dumps(data))
print(resp.text)