0x01 关于rc4
rc4简介
rc4的维基
具体实现
step1 rc4_init()
void rc4_init(unsigned char* s_box,unsigned char* key)
{int i=0,j=0;char k[256];int len=strlen(key);for(i=0;i<256;i++){//以256填充s盒s[i]=i;//使用key循环填充kk[i]=key[i%len];}//打乱s盒for(i=0;i<len;i++){j=(j+s_box[i]+k[i]);swap(s_box[i],s_box[j]);}
}
step3 rc4_crypt()
void rc4_crypt(unsigned char* s_box,char* data)
{int i=0,j=0;int result=0;int len=strlen(data);for(int k=0;k<len;k++){i=(i+1)%256;j=(j+s_box[i])%256;swap(s_box[i],s_box[j]);result=(s_box[i]+s_box[j])%256;data[k]^=s_box[i];}
}
0x02 rc4解密
rc4解密关键在于key的选取,只要有正确的key和密文,编写脚本再跑一遍密文即可
0x03 关于题目
关于密文

IDA的问题,没有识别出v8和v9,buf1数组共四个数据
关于key
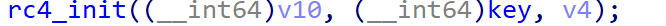
追踪key

检查交叉,发现是假key
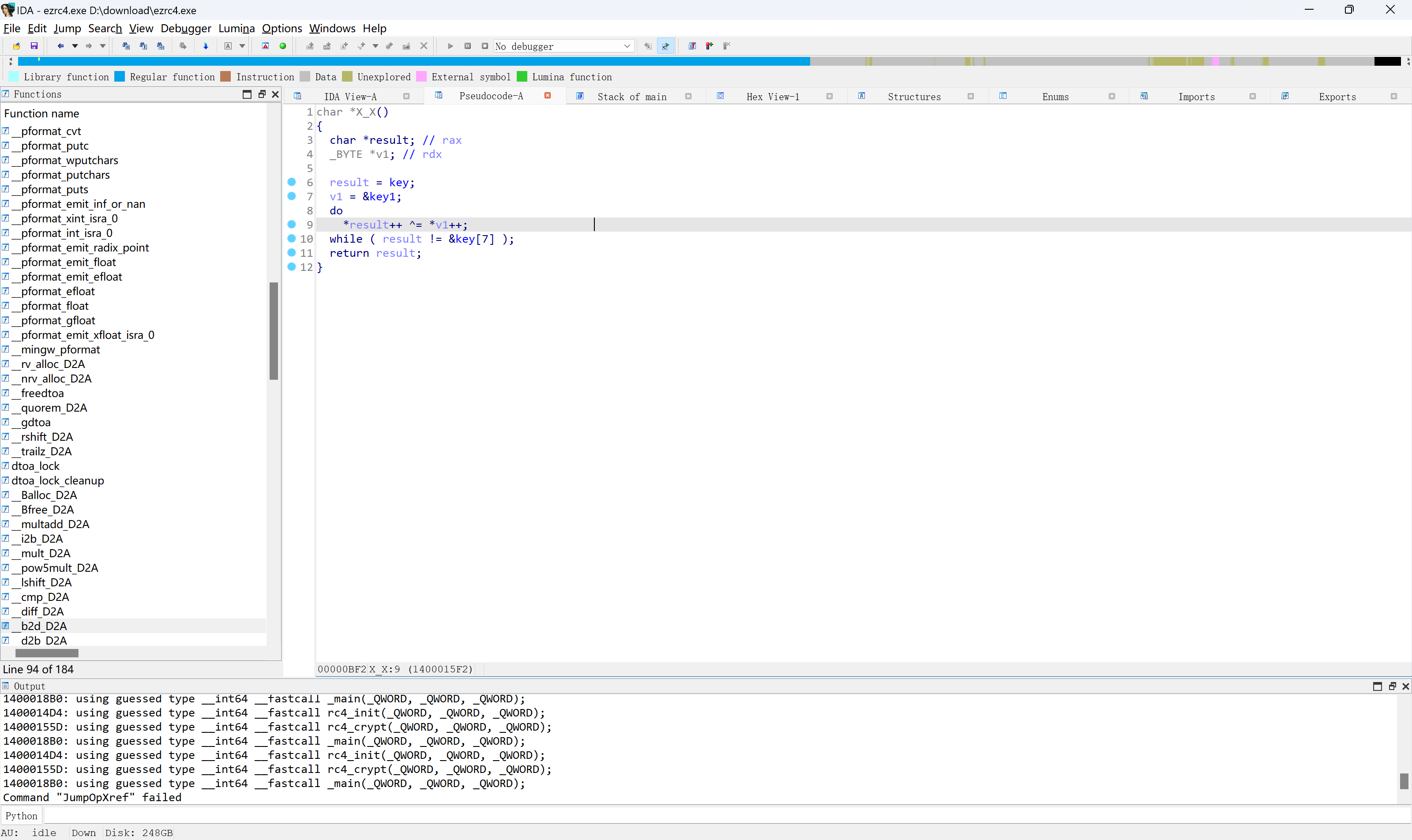
xor解密
key="fenkey?"
key=list(key)
key1=[10, 12, 26, 8, 17, 31, 30]
for i in range(len(key)):key[i]=chr(ord(key[i])^key1[i])
for i in range(0,len(key)):print(key[i],end="")
//litctf!
0x03 EXP
#include "string"
#include <cstring>
using namespace std;
long long buf[4];
unsigned char v10[256];
unsigned char v11[256];void rc4_init()
{char key[]="litctf!";unsigned int a3= strlen(key);for (int i = 0; i < 256; ++i) {v10[i]=i;v11[i]=key[i%a3];}int j=0;for (int i = 0; i < 256; ++i){j=(j+v10[i]+v11[i])%256;swap(v10[i],v10[j]);}
}void rc4_crypt(char* flag) {int i = 0, j = 0;int result;unsigned long len= strlen(flag);for (int k = 0; k < len; ++k) {i = (i + 1) % 256;j = (j+v10[i])%256;swap(v10[i], v10[j]);result = (v10[i]+v10[j])%256;flag[k]^=v10[result];}
}int main() {buf[0]=0x606EA290DC7CB2D5;buf[1]=0x3190B05971E41306;buf[2]=0xD71DC7B2;buf[3]=0x7F;rc4_init();rc4_crypt((char*) buf);printf("%s",buf);return 0;
}
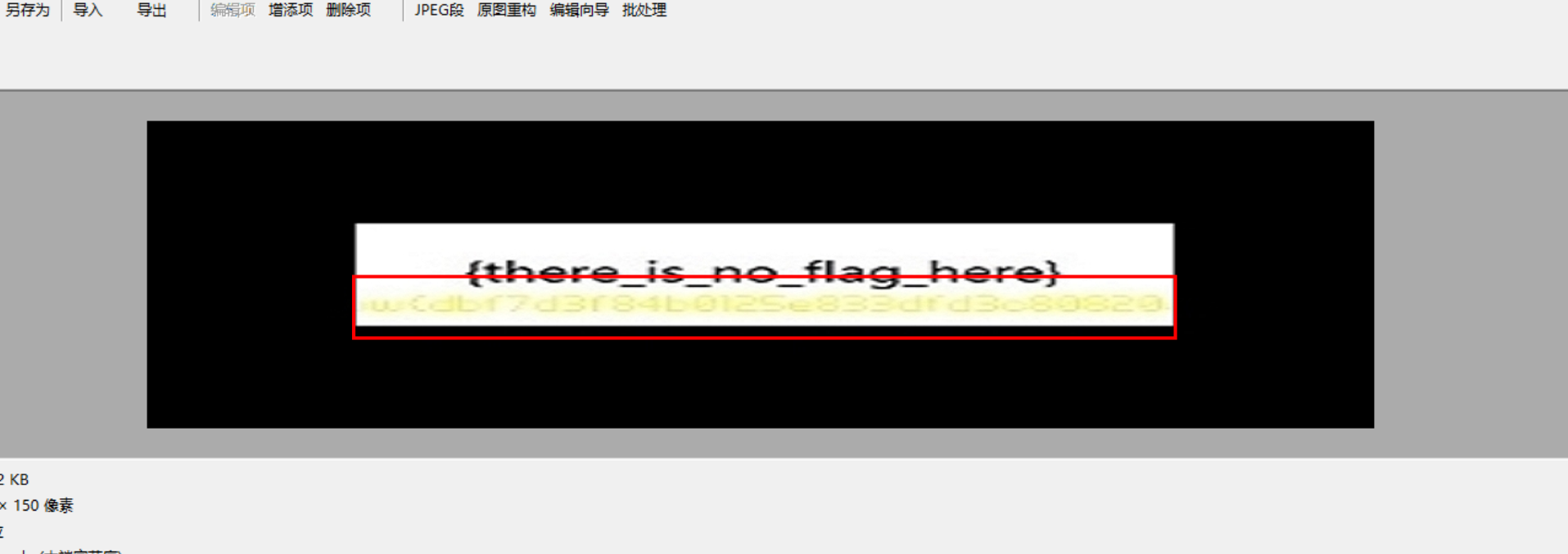
//LitCTF{rc4_love_nice 少个“}”,O.o?