数字破解
a、7位数字破解
hashcat64.exe -a 3 -m 0 --force 25c3e88f81b4853f2a8faacad4c871b6 ?d?d?d?d?d?d?d

b、7位小写字母破解
hashcat64.exe -a 3 -m 0 --force 7a47c6db227df60a6d67245d7d8063f3 ?l?l?l?l?l?l?l
c、1-8位数字破解
hashcat64.exe -a 3 -m 0 --force 4488cec2aea535179e085367d8a17d75 --increment --increment-min 1 --increment-max 8 ?d?d?d?d?d?d?d?d
d、1-8位小写字母+数字破解
hashcat64.exe -a 3 -m 0 --force ab65d749cba1656ca11dfa1cc2383102 --increment --increment-min 1 --increment-max 8 ?h?h?h?h?h?h?h?h
e、特定字符集:123456abcdf!@+-
hashcat64.exe -a 3 -1 123456abcdf!@+- 8b78ba5089b11326290bc15cf0b9a07d ?1?1?1?1?1
#这里的-1和?1是数字1,不是字母l
f、1-8为位符集:123456abcdf!@+-
hashcat64.exe -a 3 -1 123456abcdf!@+- 9054fa315ce16f7f0955b4af06d1aa1b --increment --increment-min 1 --increment-max 8 ?1?1?1?1?1?1?1?1
g、1-8位数字+大小写字母+可见特殊符号
hashcat64.exe -a 3 -1 ?d?u?l?s d37fc9ee39dd45a7717e3e3e9415f65d --increment --increment-min 1 --increment-max 8 ?1?1?1?1?1?1?1?1
或者:
hashcat64.exe -a 3 d37fc9ee39dd45a7717e3e3e9415f65d --increment --increment-min 1 --increment-max 8 ?a?a?a?a?a?a?a?a
字典破解
参数"-a 0"用于指定字典破解模式,参数"-o"用于输出结果到文件中:
hashcat64.exe -a 0 ede900ac1424436b55dc3c9f20cb97a8 password.txt -o result.txt
批量破解
hashcat64.exe -a 0 hash.txt password.txt -o result.txt

字典掩码
hashcat64.exe -a 6 9dc9d5ed5031367d42543763423c24ee password.txt ?l?l?l?l?l
MySQL

使用hashcat进行破解:
hashcat64.exe -a 3 -m 300 --force 6BB4837EB74329105EE4568DDA7DC67ED2CA2AD9 ?d?d?d?d?d?
Sha512
可以通过cat /etc/shadow获取:
hashcat64.exe -a 3 -m 1800 --force $6$mxuA5cdy$XZRk0CvnPFqOgVopqiPEFAFK72SogKVwwwp7gWaUOb7b6tVwfCpcSUsCEk64ktLLYmzyew/xd0O0hPG/yrm2X. ?l?l?l?l
不用整理用户名,使用--username:
hashcat64.exe -a 3 -m 1800 --force qiyou:$6$QDq75ki3$jsKm7qTDHz/xBob0kF1Lp170Cgg0i5Tslf3JW/sm9k9Q916mBTyilU3PoOsbRdxV8TAmzvdgNjrCuhfg3jKMY1 ?l?l?l?l?l --username
NT-Hash
hashcat64.exe -a 3 -m 1000 209C6174DA490CAEB422F3FA5A7AE634 ?l?l?l?l?l
LM-Hash
hashcat64.exe -a 3 -m 3000 F0D412BD764FFE81AAD3B435B51404EE ?l?l?l?l?l
MSSQL
hashcat64.exe -a 3 -m 132 --force 0x01008c8006c224f71f6bf0036f78d863c3c4ff53f8c3c48edafb ?l?l?l?l?l?d?d?d
WordP
hashcat64.exe -a 3 -m 400 --force $P$BYEYcHEj3vDhV1lwGBv6rpxurKOEWY/ ?d?d?d?d?d?d
DIscuz
hashcat64.exe -a 3 -m 2611 --force 14e1b600b1fd579f47433b88e8d85291: ?d?d?d?d?d?d
RAR密码
首先使用rar2john(获取rar文件hash值
http://openwall.info/wiki/_media/john/johntheripper-v1.8.0.12-jumbo-1-bleeding-e6214ceab-2018-02-07-win-x64.7zrar2john.exe 1.rar

之后进行破解:
hashcat64.exe -a 3 -m 13000 --force $rar5$16$639e9ce8344c680da12e8bdd4346a6a3$15$a2b056a21a9836d8d48c2844d171b73d$8$04a52d2224ad082e ?d?d?d?d?d?d

hashcat支持RAR3-hp和 RAR5,官方示例如下:
| -m 参数 | 类型 | 示例 hash |
|---|---|---|
| 12500 | RAR3-hp | $RAR3$045109af8ab5f297a*adbf6c5385d7a40373e8f77d7b89d317 |
| 13000 | RAR5 | $rar5$16$74575567518807622265582327032280$15$f8b4064de34ac02ecabfe |
ZIP密码
首先使用zip2john获取文件的hash值:
zip2john.exe 1.zip

之后使用hashcat进行破解:
hashcat64.exe -a 3 -m 13600 $zip2$*0*3*0*554bb43ff71cb0cac76326f292119dfd*ff23*5*24b28885ee*d4fe362bb1e91319ab53*$/zip2$ --force ?d?d?d?d?d?d

Office密码
获取office的hash值:
python office2john.py 11.docx

之后使用hashcat进行破解:
hashcat64.exe -a 3 -m 9600 $office$*2013*100000*256*16*e4a3eb62e8d3576f861f9eded75e0525*9eeb35f0849a7800d48113440b4bbb9c*577f8d8b2e1c5f60fed76e62327b38d28f25230f6c7dfd66588d9ca8097aabb9 --force ?d?d?d?d?d?d

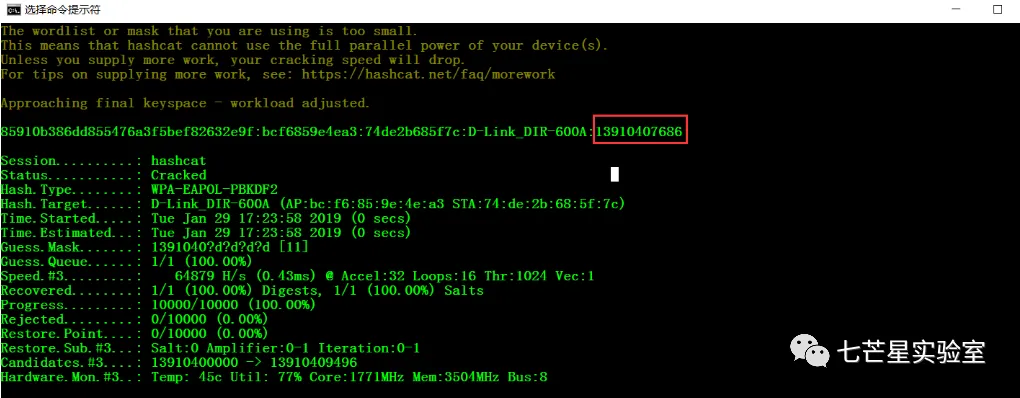
WIFI密码
首先把我们的握手包转化为hccapx格式,现在最新版的hashcat只支持hccapx格式了,以前的hccap格式已经不支持了,官方在线转换
https://hashcat.net/cap2hccapx/
hashcat64.exe -a 3 -m 2500 1.hccapx 1391040?d?d?d?d