Crypto
1.凯撒加密
YEI{CKRIUSK_ZU_2024_MKKQ_INGRRKTMK}
6位
SYC{WELCOME_TO_2024_GEEK_CHALLENGE}
2.RSA
原文:
from Crypto.Util.number import bytes_to_long, getPrime
from secret import flag
p = getPrime(128)
q = getPrime(128)
n = p*q
e = 65537
m = bytes_to_long(flag)
c = pow(m, e, n)
print(f"n = {n}")
print(f"p = {p}")
print(f"q = {q}")
print(f"c = {c}")'''
n = 33108009203593648507706487693709965711774665216872550007309537128959455938833
p = 192173332221883349384646293941837353967
q = 172282016556631997385463935089230918399
c = 5366332878961364744687912786162467698377615956518615197391990327680664213847
'''
经典的RSA,已知p,q,e,c
exp:
import gmpy2
import libnum
from Crypto.Util.number import *
n = 33108009203593648507706487693709965711774665216872550007309537128959455938833
p = 192173332221883349384646293941837353967
q = 172282016556631997385463935089230918399
c = 5366332878961364744687912786162467698377615956518615197391990327680664213847
e = 65537
n = p * q
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(libnum.n2s(int(m)))
#b'SYC{RSA_is_easy}'
3.不是套娃
实际上是个套娃题
第一层:

看一下txt
-..-/../-./..--.-/.---/../..--.-/--../../..--.-/.--/.-/..--.-/-.--/../..--.-/--../../..--.-/--/---/..--.-/-.--/../..--.-/-../..-/.-/..--.-/--../..
摩斯密码
解密有
XIN_JI_ZI_WA_YI_ZI_MO_YI_DUA_ZI
再根据标题key=lower(key)意思是大写转小写
xin_ji_zi_wa_yi_zi_mo_yi_dua_zi
第二层:
看到类似维吉尼亚的名称,猜测是维吉尼亚加密
key <- commanderKEY = uizrlbzii+ + + + + + + + + +
uizrlbzii Rsm o o o Bcynirv
+ + + + + + + + + +
uizrlbzii
+ + + + + + + + + +
uizrlbzii Rsm
+ + + + + + + + + +
uizrlbzii Rsm
+ + + + + + + + + +
uizrlbzii
+ + + + + + + + + +
uizrlbzii Rsm o o Yoxx-nhw o Bcynirv
+ + + + + + + + + +
刚开始还没看懂,然后不知不觉就捣鼓出来了
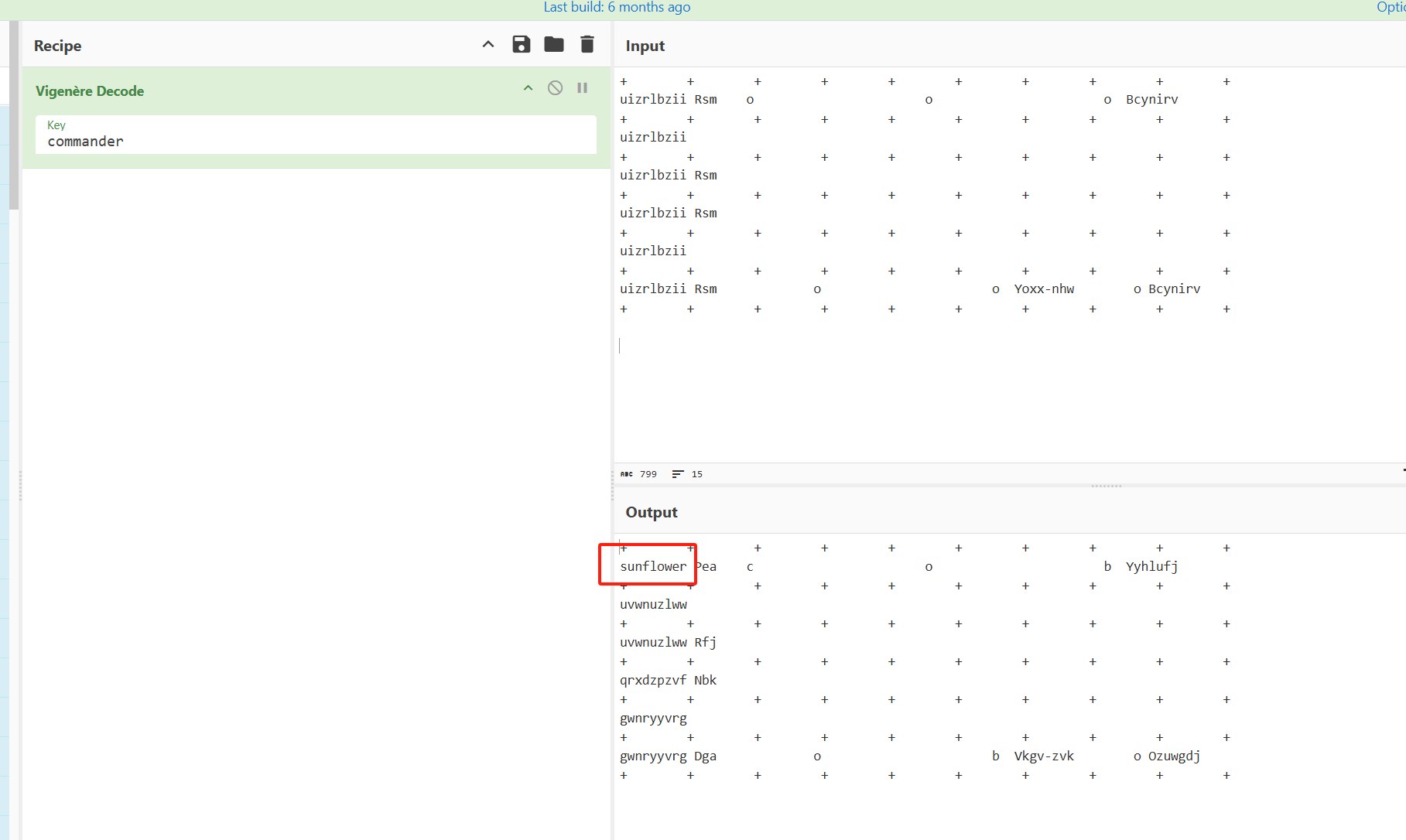
密码是
sunflower
第三层:

文档里给出了加密代码
a1fdbce928af7aae
疑似MD5,丢去解密
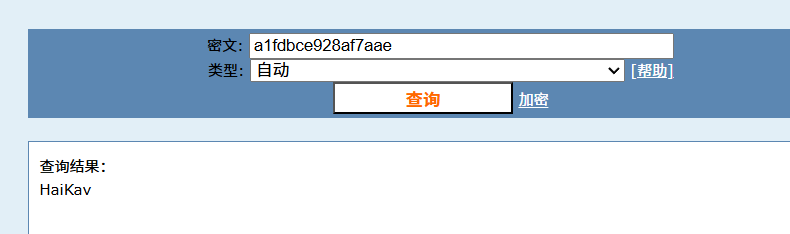
密码:
HaiKav
第四层

文档里:
NEFICPIC&CRTCTNEYO
你猜这是什么,根据标题,我猜是三个10进制=60进制?
好家伙,整了半天,是栅栏密码.......
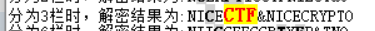
密码:
NICECTF&NICECRYPTO
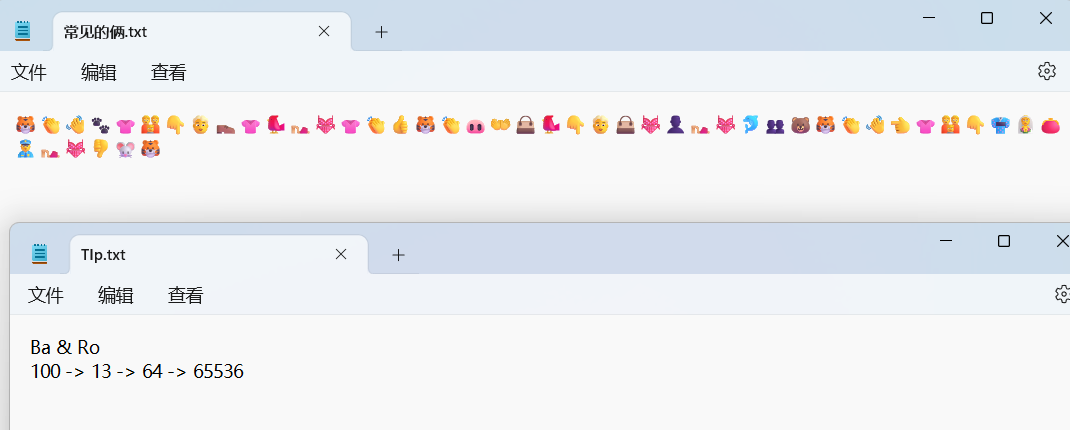
根据提示解密即可
解得:
原神,启动!
最后一层:
打开就是flag
SYC{H0W_P3RF3C+_YU0_AR3!}
4.共模攻击
原文:
from Crypto.Util.number import *
from secret import flag
p,q = [getPrime(1024) for _ in range(2)]
n = p*q
e = [getPrime(10) for _ in range(2)]m = bytes_to_long(flag)c = [pow(m, e[i], n) for i in range(2)]
print(f'n = {n}')
print(f'e1 = {e[0]}')
print(f'e2 = {e[1]}')
print(f'c1 = {c[0]}')
print(f'c2 = {c[1]}')
'''
n = 19742875423645690846073637620470497648804310111201409901059297083827103813674034450200432098143959078292346910591785265323563248781526393718834491458926162514713269984791730816121181307827624489725923763353393879316510062227511469438742429290073999388690825732236465647396755899136346150862848924231619666069528077790933176798057396704758072769660663756346237040909579775389576227450505746914753205890194457812893098491264392293949768193694560954874603451253079446652049592976605414438411872223250039782381259212718733455588477129910357095186014496957765297934289263536712574572533650393220492870445376144568199077767
e1 = 911
e2 = 967
c1 = 18676091924461946809127036439355116782539894105245796626898495935702348484076501694838877829307466429933623102626122909782775514926293363853121828819237500456062111805212209491398720528499589486241208820804465599279152640624618194425740368495072591471531868392274503936869225072123214869399971636428177516761675388589238329574042518038702529606188240859751459632643230538522947412931990009143731829484941397093509641320264169403755707495153433568106934850283614529793695266717330769019091782929139589939928210818515744604847453929432990185347112319971445630830477574679898503825626294542336195240055995445217249602983
c2 = 4229417863231092939788858229435938841085459330992709019823280977891432565586698228613770964563920779991584732527715378842621171338649745186081520176123907689669636473919678398014317024138622949923292787095400632018991311254591786179660603414693984024161009444842277220189315861986306573182865656366278782315864366857374874763243428496061153290565891942968876789905670073321426112497113145141539289020571684634406829272902118484670099097148727072718299512735637087933649345419433312872607209633402427461708181971718804026293074540519907755129917132236240606834816534369171888633588190859475764799895410284484045429152
'''
exp:
import gmpy2
import libnum
n = 19742875423645690846073637620470497648804310111201409901059297083827103813674034450200432098143959078292346910591785265323563248781526393718834491458926162514713269984791730816121181307827624489725923763353393879316510062227511469438742429290073999388690825732236465647396755899136346150862848924231619666069528077790933176798057396704758072769660663756346237040909579775389576227450505746914753205890194457812893098491264392293949768193694560954874603451253079446652049592976605414438411872223250039782381259212718733455588477129910357095186014496957765297934289263536712574572533650393220492870445376144568199077767
e1 = 911
e2 = 967
c1 = 18676091924461946809127036439355116782539894105245796626898495935702348484076501694838877829307466429933623102626122909782775514926293363853121828819237500456062111805212209491398720528499589486241208820804465599279152640624618194425740368495072591471531868392274503936869225072123214869399971636428177516761675388589238329574042518038702529606188240859751459632643230538522947412931990009143731829484941397093509641320264169403755707495153433568106934850283614529793695266717330769019091782929139589939928210818515744604847453929432990185347112319971445630830477574679898503825626294542336195240055995445217249602983
c2 = 4229417863231092939788858229435938841085459330992709019823280977891432565586698228613770964563920779991584732527715378842621171338649745186081520176123907689669636473919678398014317024138622949923292787095400632018991311254591786179660603414693984024161009444842277220189315861986306573182865656366278782315864366857374874763243428496061153290565891942968876789905670073321426112497113145141539289020571684634406829272902118484670099097148727072718299512735637087933649345419433312872607209633402427461708181971718804026293074540519907755129917132236240606834816534369171888633588190859475764799895410284484045429152
s,s1,s2=gmpy2.gcdext(e1,e2)
m=(pow(c1,s1,n)*pow(c2,s2,n))%n
print(libnum.n2s(int(m)).decode())
#SYC{U_can_really_attack}
5.XOR
原文:
from Crypto.Util.number import *
from pwn import xorkey = b'...'
flag = b'...'
assert len(key)==4enc = bytes_to_long(xor(flag,key))f1 = 4585958212176920650644941909171976689111990
f2 = 3062959364761961602614252587049328627114908
e1 = enc^f1
e2 = e1^f2
print(e2)"""
10706859949950921239354880312196039515724907
"""
两个xor,注意python只能异或数,Pwn的异或可以异或字符串
我给出的方法是爆破,范围再可打印的ASCII码
exp:
from Crypto.Util.number import *
from itertools import *
f1 = 4585958212176920650644941909171976689111990
f2 = 3062959364761961602614252587049328627114908
e2=10706859949950921239354880312196039515724907
e1=e2^f2
enc=e1^f1
#print(enc)
# #9529760761659260504037024859162256546622529
enc = b'mes)_c@3LHobXchblA'
for key in product(range(32, 127), repeat=4):key_bytes = bytes(key)try:flag = bytes([b ^ key_bytes[i % 4] for i, b in enumerate(enc)])if b'SYC{' in flag:print(flag)except IndexError:continue
#'SYC{a_part_0f_X0R}'#实际上下面这种方法可以快速求出key,感谢大佬的指点.
'''
from Crypto.Util.number import *
from pwn import xor
f1 = 4585958212176920650644941909171976689111990
f2 = 3062959364761961602614252587049328627114908
c=10706859949950921239354880312196039515724907
enc=long_to_bytes(c^f2^f1)
print(enc)
key=xor(b'SYC{',enc[:4])
print(key)
'''
6.dp
经典的dp泄露
原文:
from Crypto.Util.number import getPrime,bytes_to_longp,q = getPrime(512),getPrime(512)
n = p * q
e = 65537
d = pow(e,-1,(p-1) * (q-1))
dp = d % (p-1)
m = bytes_to_long(flag)
c = pow(m, e, n)print("c = ",c)
print("n = ",n)
print("e = ",e)
print("dp = ",dp)'''
c = 127916287434936224964530288403657504450134210781148845328357237956681373722556447001247137686758965891751380034827824922625307521221598031789165449134994998397717982461775225812413476283147124013667777578827293691666320739053915493782515447112364470583788127477537555786778672970196314874316507098162498135060
n = 157667866005866043809675592336288962106125998780791920007920833145068421861029354497045918471672956655205541928071253023208751202980457919399456984628429198438149779785543371372206661553180051432786094530268099696823142821724314197245158942206348670703497441629288741715352106143317909146546420870645633338871
e = 65537
dp = 2509050304161548479367108202753097217949816106531036020623500808413533337006939302155166063392071003278307018323129989037561756887882853296553118973548769
'''
exp:
import gmpy2 as gp
c = 127916287434936224964530288403657504450134210781148845328357237956681373722556447001247137686758965891751380034827824922625307521221598031789165449134994998397717982461775225812413476283147124013667777578827293691666320739053915493782515447112364470583788127477537555786778672970196314874316507098162498135060
n = 157667866005866043809675592336288962106125998780791920007920833145068421861029354497045918471672956655205541928071253023208751202980457919399456984628429198438149779785543371372206661553180051432786094530268099696823142821724314197245158942206348670703497441629288741715352106143317909146546420870645633338871
e = 65537
dp = 2509050304161548479367108202753097217949816106531036020623500808413533337006939302155166063392071003278307018323129989037561756887882853296553118973548769
for i in range(1,e):if(dp*e-1)%i == 0:if n%(((dp*e-1)//i)+1) == 0:p=((dp*e-1)//i)+1q=n//(((dp*e-1)//i)+1)phi=(q-1)*(p-1)d=gp.invert(e,phi)m=pow(c,d,n)
print(m)
print(bytes.fromhex(hex(m)[2:]))
#SYC{welcome_to_crypto}
7.ezRSA
题目描述:coppersmith
原文:
from Crypto.Util.number import *
from secret import flag
m = bytes_to_long(flag)
assert m.bit_length()<500
p = getPrime(512)
q = getPrime(512)
n = p*q
e = 3
c = pow(m, e, n)
bits = 150
m = (m >> bits) << bits
h = (2024*m-2023) % n
print('n =',n)
print('c =',c)
print('h =',h)'''
n = 98776098002891477120992675696155328927086322526307976337988006606436135336004472363084175941067711391936982491358233723506086793155908108571814951698009309071244571404116817767749308434991695075517682979438837852005396491907180020541510210086588426719828012276157990720969176680296088209573781988504138607511
c = 9379399412697943604731810117788765980709097637865795846842608472521416662350816995261599566999896411508374352899659705171307916591351157861393506101348972544843696221631571188094524310759046142743046919075577350821523746192424192386688583922197969461446371843309934880019670502610876840610213491163201385965
h = 111518648179416351438603824560360041496706848494616308866057817087295675324528913254309319829895222661760009533326673551072163865
'''
根据题目描述是coppersmith,所以为coppersmith攻击
Coppersmith 可以用于求多项式的小根,经常用于 RSA 攻击中“已知某些二进制位,求剩余位”这一类问题。
具体详情可以查看:大佬的文章
exp:
from Crypto.Util.number import *
def extended_euclidean(a, b):if a == 0:return b, 0, 1else:gcd, x, y = extended_euclidean(b % a, a)return gcd, y - (b // a) * x, x
def mod_inverse(a, m):gcd, x, _ = extended_euclidean(a, m)if gcd != 1:return None # 如果a和m不互质,则没有逆元else:return x % m# 给定的值
n = 98776098002891477120992675696155328927086322526307976337988006606436135336004472363084175941067711391936982491358233723506086793155908108571814951698009309071244571404116817767749308434991695075517682979438837852005396491907180020541510210086588426719828012276157990720969176680296088209573781988504138607511
h = 111518648179416351438603824560360041496706848494616308866057817087295675324528913254309319829895222661760009533326673551072163865
# 计算2024模n的逆元
inv_2024 = mod_inverse(2024, n)
# 计算m
high_m = (h + 2023) * inv_2024 % n
def phase2(high_m, n, c):R.<x> = PolynomialRing(Zmod(n), implementation='NTL')m = high_m + xM = m((m^3 - c).small_roots()[0])print(long_to_bytes(int(M)))c = 9379399412697943604731810117788765980709097637865795846842608472521416662350816995261599566999896411508374352899659705171307916591351157861393506101348972544843696221631571188094524310759046142743046919075577350821523746192424192386688583922197969461446371843309934880019670502610876840610213491163201385965
phase2(high_m, n, c)
#SYC{crypto_is_very_interesting_why_dont_you_join_us}
8.ecc
原文:
from Crypto.Util.number import *
from secret import flagp = getPrime(256)
a = getPrime(256)
b = getPrime(256)
E = EllipticCurve(GF(p),[a,b])
m = E.random_point()
G = E.random_point()
k = getPrime(256)
K = k * G
r = getPrime(256)
c1 = m + r * K
c2 = r * Gcipher_left = bytes_to_long(flag[:len(flag)//2]) * m[0]
cipher_right = bytes_to_long(flag[len(flag)//2:]) * m[1]print(f"p = {p}")
print(f"a = {a}")
print(f"b = {b}")
print(f"k = {k}")
print(f"E = {E}")
print(f"c1 = {c1}")
print(f"c2 = {c2}")
print(f"cipher_left = {cipher_left}")
print(f"cipher_right = {cipher_right}")
'''
p = 93202687891394085633786409619308940289806301885603002539703165565954917915237
a = 93822086754590882682502837744000915992590989006575416134628106376590825652793
b = 80546187587527518012258369984400999843218609481640396827119274116524742672463
k = 58946963503925758614502522844777257459612909354227999110879446485128547020161
E = Elliptic Curve defined by y^2 = x^3 + 619398863196797048716428124691975702784687120972413594924940810635907737556*x + 80546187587527518012258369984400999843218609481640396827119274116524742672463 over Finite Field of size 93202687891394085633786409619308940289806301885603002539703165565954917915237
c1 = (40485287784577105052142632380297282223290388901294496494726004092953216846111 : 81688798450940847410572480357702533480504451191937977779652402489509511335169 : 1)
c2 = (51588540344302003527882762117190244240363885481651104291377049503085003152858 : 77333747801859674540077067783932976850711668089918703995609977466893496793359 : 1)
cipher_left = 34210996654599605871773958201517275601830496965429751344560373676881990711573
cipher_right = 62166121351090454316858010748966403510891793374784456622783974987056684617905
'''
椭圆曲线加密,直接丢给GPT
复现不出来了,擦