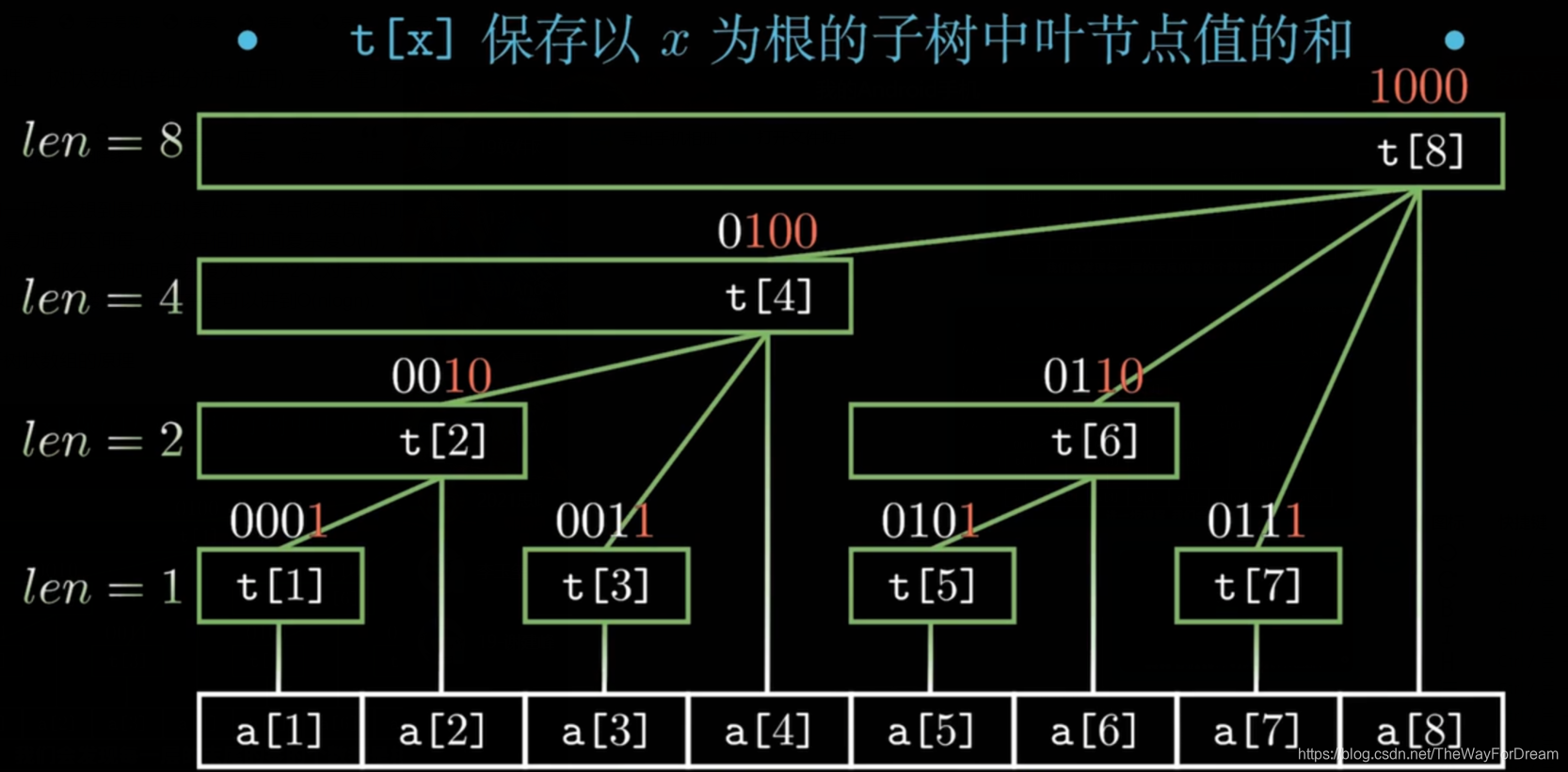
k8s安全框架概述
为了给K8S用户创建权限授权的功能。K8S的api-server对证书认证大概分为三部曲:- 鉴权: (Authentication)相当于进入小区的"出入证",以便于门口保安识别。这个"出入证"就是大家理解的证书。- 授权: (Authorization)相当于进入小区的单元楼要使用的"门禁卡"。这个"门禁卡",在K8S实现为kubeconfig文件或者token的方式。- 准入控制: 相当于识别门禁卡的设备。一旦识别后,就可以对K8S集群资源进行访问。
K8S的授权(Authorization)框架
- 角色【本质上就是对哪些资源授权,识别门禁卡的设备,体现的是: "我能干啥?"】类型:Role:用于控制局部资源的角色。ClusterRole:用于控制全局(集群)资源的角色。规则:apiGroups:资源所属的api组。resources:资源列表。verbs:可以对资源做哪些操作。比如:增删改查。- 主题【指定用户类型,相当于门禁卡,体现的是: "我是谁?"】- User用户,一般是给个人使用的。其体现形式为证书的"CN"字段,证书可以基于一个kubeconfig文件的形式存储。- ServiceAccount:服务账号,是K8S集群的sa资源,数据的数据以"Token"形式体现。而存储的token是基于secrets资源存储证书。- Group:组,一般是给一个组织使用的。其体现形式为证书的"O"字段,证书可以基于一个kubeconfig文件的形式存储。- 角色绑定 :【将"角色"和"主题"进行关联】就是将角色权限授权给主题。RoleBinding:将局部资源的角色权限绑定给一个主题。ClusterBinding:将控制全局(集群)资源的角色绑定给一个主题。
K8S内置集群角色
cluster-admin:超级管理员,有集群所有权限。admin:主要用于授权命名空间所有读写权限。edit:允许对大多数对象读写操作,不允许查看或者修改角色,角色绑定。view:允许对命名空间大多数对象只读权限,不允许查看角色,角色绑定和secret。
K8S四个集群角色
[root@master231 ~]# kubectl get clusterroles | grep -v system:
NAME CREATED AT
admin 2024-10-18T06:34:14Z
cluster-admin 2024-10-18T06:34:14Z
edit 2024-10-18T06:34:14Z
flannel 2024-10-18T07:20:43Z
kubeadm:get-nodes 2024-10-18T06:34:16Z
view 其中,"flannel"是CNI组件安装时创建的集群角色,"kubeadm:get-nodes"是基于kubeadm方式安装时创建的集群角色。clusterrole查看,其中"system:"开头的为系统内部使用。而"kubeadm:get-nodes "是使用kubeadm方式部署集群才有的角色。 2024-10-18T06:34:14Z查看cluster-admin角色权限:
查看cluster-admin角色权限:[root@master231 ~]# kubectl get clusterroles cluster-admin -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:annotations:rbac.authorization.kubernetes.io/autoupdate: "true"creationTimestamp: "2024-10-18T06:34:14Z"labels:kubernetes.io/bootstrapping: rbac-defaultsname: cluster-adminresourceVersion: "87"uid: 03c5f390-f882-4c53-960f-affff416a023
rules:
- apiGroups:- '*'resources:- '*'verbs:- '*'
- nonResourceURLs:- '*'verbs:- '*'查看admin角色权限:
[root@master231 ~]# kubectl get clusterroles admin -o yaml
aggregationRule:clusterRoleSelectors:- matchLabels:rbac.authorization.k8s.io/aggregate-to-admin: "true"
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:annotations:rbac.authorization.kubernetes.io/autoupdate: "true"creationTimestamp: "2024-07-29T08:38:15Z"labels:kubernetes.io/bootstrapping: rbac-defaultsname: adminresourceVersion: "238108"uid: ee296dcf-08ba-4f8d-a1ee-c7b2ef1dff1d
rules:
- apiGroups:- ""resources:- pods/attach- pods/exec- pods/portforward- pods/proxy- secrets- services/proxyverbs:- get
.....
这是您提供的基于用户授权的 K8S 案例的完整内容:
基于用户(User)授权案例
1. 安装证书管理工具 cfssl
1.1 下载 cfssl 软件包
下载地址:https://github.com/cloudflare/cfssl/releases
1.2 安装 cfssl 工具
[root@master231 ~]# apt -y install unzip rename
[root@master231 ~]# unzip oldboyedu-cfssl-v1.6.5.zip
[root@master231 ~]# ll cfssl*
-rw-r--r-- 1 root root 11890840 Jun 15 11:56 cfssl_1.6.5_linux_amd64
-rw-r--r-- 1 root root 8413336 Jun 15 11:56 cfssl-certinfo_1.6.5_linux_amd64
-rw-r--r-- 1 root root 6205592 Jun 15 11:56 cfssljson_1.6.5_linux_amd64
[root@master231 ~]#
[root@master231 ~]# rename 's/_1.6.5_linux_amd64//g' *_1.6.5_linux_amd64
[root@master231 ~]# ll cfssl*
-rw-r--r-- 1 root root 11890840 Jun 15 11:56 cfssl
-rw-r--r-- 1 root root 8413336 Jun 15 11:56 cfssl-certinfo
-rw-r--r-- 1 root root 6205592 Jun 15 11:56 cfssljson
[root@master231 ~]#
[root@master231 ~]# mv cfssl* /usr/local/bin/
[root@master231 ~]# chmod +x /usr/local/bin/cfssl*
[root@master231 ~]# ll /usr/local/bin/
total 25908
drwxr-xr-x 2 root root 4096 Aug 8 11:04 ./
drwxr-xr-x 10 root root 4096 Aug 10 2023 ../
-rwxr-xr-x 1 root root 11890840 Jun 15 11:56 cfssl*
-rwxr-xr-x 1 root root 8413336 Jun 15 11:56 cfssl-certinfo*
-rwxr-xr-x 1 root root 6205592 Jun 15 11:56 cfssljson*
1.3 验证 cfssl 工具是否安装成功
[root@master231 ~]# cfssl version
Version: 1.6.5
Runtime: go1.22.0
2. 编写证书请求
2.1 创建工作目录
[root@master231 user]# pwd
/oldboyedu/manifests/rbac/user
[root@master231 user]#
[root@master231 user]# ll
total 8
drwxr-xr-x 2 root root 4096 Aug 8 11:10 ./
drwxr-xr-x 3 root root 4096 Aug 8 11:10 ../
2.2 设置证书的有效期
[root@master231 user]# cat > ca-config.json <<EOF
{"signing": {"default": {"expiry": "87600h"},"profiles": {"kubernetes": {"usages": ["signing","key encipherment","server auth","client auth"],"expiry": "87600h"}}}
}
EOF
2.3 配置证书签发请求,注意 CN 字段是用户名
[root@master231 user]# cat > oldboyedu-csr.json <<EOF
{"CN": "oldboyedu","hosts": [],"key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","ST": "BeiJing","L": "BeiJing","O": "k8s","OU": "System"}]
}
EOF
3. 生成证书
3.1 使用 API Server 的 CA 证书进行签发
[root@master231 user]# ll
total 16
drwxr-xr-x 2 root root 4096 Aug 8 11:10 ./
drwxr-xr-x 3 root root 4096 Aug 8 11:10 ../
-rw-r--r-- 1 root root 292 Aug 8 11:10 ca-config.json
-rw-r--r-- 1 root root 222 Aug 8 11:10 oldboyedu-csr.json
[root@master231 user]# cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key -config=ca-config.json -profile=kubernetes oldboyedu-csr.json | cfssljson -bare oldboyedu
[root@master231 user]#
[root@master231 user]# ll
total 28
drwxr-xr-x 2 root root 4096 Aug 8 11:20 ./
drwxr-xr-x 3 root root 4096 Aug 8 11:10 ../
-rw-r--r-- 1 root root 292 Aug 8 11:10 ca-config.json
-rw-r--r-- 1 root root 1001 Aug 8 11:20 oldboyedu.csr
-rw-r--r-- 1 root root 222 Aug 8 11:10 oldboyedu-csr.json
-rw------- 1 root root 1679 Aug 8 11:20 oldboyedu-key.pem
-rw-r--r-- 1 root root 1281 Aug 8 11:20 oldboyedu.pem
3.2 查看证书的详细信息
[root@master231 user]# cfssl-certinfo -cert oldboyedu.pem
{"subject": {"common_name": "oldboyedu","country": "CN","organization": "k8s","organizational_unit": "System","locality": "BeiJing","province": "BeiJing","names": ["CN","BeiJing","BeiJing","k8s","System","oldboyedu"]},"issuer": {"common_name": "kubernetes","names": ["kubernetes"]},"serial_number": "676873962625811670734938715941963915094282023231","not_before": "2024-08-08T03:16:00Z","not_after": "2034-08-06T03:16:00Z","sigalg": "SHA256WithRSA","authority_key_id": "4D:0B:35:BD:C3:8D:0E:D8:02:B3:3B:8E:85:20:AB:5C:86:39:19:A8","subject_key_id": "72:E5:F0:4F:E7:B5:08:A8:C7:7F:F0:5F:66:AA:CA:C2:DE:C7:69:07","pem": "-----BEGIN CERTIFICATE-----\nMIIDhjCCAm6gAwIBAgIUdpAUBjadvjc58oMN+Kx10YHFMT8wDQYJKoZIhvcNAQEL\nBQAwFTETMBEGA1UEAxMKa3ViZXJuZXRlczAeFw0yNDA4MDgwMzE2MDBaFw0zNDA4\nMDYwMzE2MDBaMGQxCzAJBgNVBAYTAkNOMRAwDgYDVQQIEwdCZWlKaW5nMRAwDgYD\nVQQHEwdCZWlKaW5nMQwwCgYDVQQKEwNrOHMxDzANBgNVBAsTBlN5c3RlbTESMBAG\nA1UEAxMJb2xkYm95ZWR1MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA\nz6+am+12hVIq7IoE78oJAM7o8Nf2pU1Vwru5yfgzl0lxQOIeQaa6voSwJBzLN9sG\nlx9v08XxVGeZxW5H5bMwdIpfhKljFqzMT0HbIF5K2khRxPLIuxcx3Ki8ita2Fx05\nhxM6ekv4R61V8ytjjP1aH4JVuKd819xB74MQbqUN2hcoD4M093qw+u0GlWglsb6O\n7R1Q8G/JYhqbgtXCiz+QyHEl8DDQu/1KUN7cMmaVBw4zJw0/pwjlDCPx5StQUiF4\n5BLRPLBR3PTPMgPcPE8+NTm4X5hCIa/DBYgrIpqDa0bwd1wc9QHRncbh23f5XbB4\ngNjzNhXhcyQz3g+lpV8WDQIDAQABo38wfTAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0l\nBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMAwGA1UdEwEB/wQCMAAwHQYDVR0OBBYE\nFHLl8E/ntQiox3/wX2aqysLex2kHMB8GA1UdIwQYMBaAFE0LNb3DjQ7YArM7joUg\nq1yGORmoMA0GCSqGSIb3DQEBCwUAA4IBAQBYB7CuJDWExiZg91MGLUjg+DUwf22A\nDSGO36+hmX6CWDWiNufZY77ZGIjcToLu/+jRsqv/soEL56nPZF9kpr1w3ahsphh/\nBn+SevbQ1v+cjnhYn14oDFYLR6QiZXQwcJQ9SQuBtdMBvvkw5u86LJuK7MMNRGt5\nR+bVDaw4LZPq/RnO3fNXlJtuexkyhg9ALEMWpzjKqYzoLpc2ltcXSPrGsZZ9pejX\n1m64Y1b5SoGO2F9oRzfGHJWrSd34SICsu8Kw6p55ad2FV7ZZH1kaj+eQtIFwdkTM\n+dkUkF3ptHno0qpFFWqWwg0bGmCMed9vWptkseK42GSidddMP5x0ecRi\n-----END CERTIFICATE-----\n"
}
4. 生成 kubeconfig 授权文件
4.1 编写生成 kubeconfig 文件的脚本
[root@master231 user]# cat > kubeconfig.sh <<'EOF'
# 配置集群
kubectl config set-cluster oldboyedu-linux92 \--certificate-authority=/etc/kubernetes/pki/ca.crt \--embed-certs=true \--server=https://10.0.0.231:6443 \--kubeconfig=oldboyedu-linux92.kubeconfig# 设置客户端认证
kubectl config set-credentials linux92 \--client-key=oldboyedu-key.pem \--client-certificate=oldboyedu.pem \--embed-certs=true \--kubeconfig=oldboyedu-linux92.kubeconfig# 设置上下文
kubectl config set-context xixi \--cluster=oldboyedu-linux92 \--user=linux92 \--kubeconfig=oldboyedu-linux92.kubeconfig# 设置当前默认上下文
kubectl config use-context xixi --kubeconfig=oldboyedu-linux92.kubeconfig
EOF
4.2 生成 kubeconfig 文件
[root@master231 user]# bash kubeconfig.sh
Cluster "oldboyedu-linux92" set.
User "linux92" set.
Context "xixi" modified.
Switched to context "xixi".
4.3 验证权限
[root@master231 user]# kubectl get pods --kubeconfig=oldboyedu-linux92.kubeconfig
Error from server (Forbidden): pods is forbidden: User "oldboyedu" cannot list resource "pods" in API group "" in the namespace "default"
温馨提示:此步骤发现
oldboyedu用户没有访问权限,因为尚未授权。
5. 创建 RBAC 授权策略
5.1 创建 RBAC 配置文件
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:namespace: defaultname: oldboyedu-custom-role
rules:- apiGroups: ["","apps"]resources: ["pods","deployments"]verbs: ["get", "list"]- apiGroups: ["","apps"]resources: ["daemonsets"]verbs: ["get", "list","delete"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:name: oldboyedu-linux-rbacnamespace: default
subjects:- kind: Username: oldboyeduapiGroup: rbac.authorization.k8s.io
roleRef:kind: Rolename: oldboyedu-custom-roleapiGroup: rbac.authorization.k8s.io
5.2 应用 RBAC 授权
[root@master231 user]# kubectl apply -f rbac.yaml
role.rbac.authorization.k8s.io/oldboyedu-custom-role created
rolebinding.rbac.authorization.k8s.io/oldboyedu-linux-rbac created
5.3 测试验证
[root@master231 user]# kubectl get pods --kubeconfig=oldboyedu-linux92.kubeconfig
NAME READY STATUS RESTARTS AGE
deploy-stress-7c98946b97-5slrj 1/1 Running 0 20h
deploy-stress-7c98946b97-8sgnm 1/1 Running 0 20h
...
温馨提示:
- Role 角色只能针对某个命名空间的资源进行授权。
- 未授权的资源是无法访问的。
以下是您提供的基于 Group 类型授权的 K8S 案例:
验证 "~/.kube/config" 文件基于 Group 类型授权
1. 导入 kubeconfig 的证书文件
[root@master231 ~]# cat /root/.kube/config | grep client-certificate-data | awk '{print $2}' | base64 -d > /tmp/admin.kubeconfig
2. 查看证书的详细信息
[root@master231 ~]# cfssl-certinfo -cert /tmp/admin.kubeconfig
{"subject": {"common_name": "kubernetes-admin","organization": "system:masters","names": ["system:masters","kubernetes-admin"]},"issuer": {"common_name": "kubernetes","names": ["kubernetes"]},"serial_number": "6158114966617684857","not_before": "2024-07-29T08:38:06Z","not_after": "2025-07-29T08:38:07Z","sigalg": "SHA256WithRSA","authority_key_id": "4D:0B:35:BD:C3:8D:0E:D8:02:B3:3B:8E:85:20:AB:5C:86:39:19:A8","subject_key_id": "","pem": "-----BEGIN CERTIFICATE-----\nMIIDITCCAgmgAwIBAgIIVXYE719De3kwDQYJKoZIhvcNAQELBQAwFTETMBEGA1UE\nAxMKa3ViZXJuZXRlczAeFw0yNDA3MjkwODM4MDZaFw0yNTA3MjkwODM4MDdaMDQx\nFzAVBgNVBAoTDnN5c3RlbTptYXN0ZXJzMRkwFwYDVQQDExBrdWJlcm5ldGVzLWFk\nbWluMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAztFMSsqHJ4Hp97e1\n7C7+eCahwUPEZItZEbxD67Kkw52FE9z0m2xUOb274lhhd6gT9BtkN1EyoRL1DkyL\nq3Cjoe6vIykyJN5J+s1qaEuQNwRW9XlGMHsVinBZC1MaEN7rXSvQkgJg24YFxG2Q\nuRR0PXWa1B9b4Et6+y/luH/EFrw45qc+V/5jCmyBwKE4cLkWID3eBMHUeeCsme3Q\nLwLI+Up33PMbuOFlIUAVMJE75m34blh7XiiP/9QN0dETO4L//DsTBLaVzr2EpBxR\nsIDBKwfa+GPXkrXFqfPpqUea0Yi2i3BJoy0YYNLG1HtyBPmd0SuDU6db5nWUILIS\ndKeNqwIDAQABo1YwVDAOBgNVHQ8BAf8EBAMCBaAwEwYDVR0lBAwwCgYIKwYBBQUH\nAwIwDAYDVR0TAQH/BAIwADAfBgNVHSMEGDAWgBRNCzW9w40O2AKzO46FIKtchjkZ\nqDANBgkqhkiG9w0BAQsFAAOCAQEADBeUDYPSDq6GGYYzKp2jfqo8Y8cBsYCzR6ma\nfX76wo7gnz6+Eg1Zbm2riWEg6+TvQbuYWCClqoh/D8OICMpxQdsvnCP6aLEfED9r\nbt7Mw4gBuahkenwGFsg5tNyJd8/4tfYm1JK/qxvDXxd3UL5g7J5WhcHPSFVgazup\nla12arNsyG6SM677j8ZvYCxPOylJoZWuTEdVdTp+hz30+YGMxy7g4g77z3uT5MZ/\nJXMmBMDoyyTsBIYa6wDVp0K9nJ7NnB2g9sahtEcrZLXahqashfO+zhQumQBtuNLT\ns4egimsdreON/fe8SvoE86Dmda8RfXkN/oRKc+23eEanpLVufA==\n-----END CERTIFICATE-----\n"
}
注意观察:证书中的
organization字段表示用户属于system:masters组,这意味着该用户是管理员角色的一部分。
3. 查看集群角色绑定
[root@master231 ~]# kubectl get clusterrolebindings cluster-admin -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:annotations:rbac.authorization.kubernetes.io/autoupdate: "true"creationTimestamp: "2024-07-29T08:38:15Z"labels:kubernetes.io/bootstrapping: rbac-defaultsname: cluster-adminresourceVersion: "148"uid: 30712701-af0d-447b-9777-440276aec8f3
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.iokind: Groupname: system:masters
这里我们可以看到,
cluster-admin角色是绑定给了system:masters组,这也是管理员组,说明管理员用户是通过Group类型进行授权的。
加载 kubeconfig 配置文件的四种方法
1. 基于 --kubeconfig 选项指定 kubeconfig 文件
[root@worker232 ~]# kubectl get pods --kubeconfig=/root/oldboyedu-linux92.kubeconfig
NAME READY STATUS RESTARTS AGE
deploy-stress-7c98946b97-8sgnm 1/1 Running 0 20h
deploy-stress-7c98946b97-gnj8s 1/1 Running 0 18m
...
2. 将 kubeconfig 文件存放到家目录中,以便于调用
[root@worker232 ~]# ll ~/.kube/
total 12
drwxr-x--- 3 root root 4096 Aug 8 12:27 ./
drwx------ 8 root root 4096 Aug 8 12:27 ../
drwxr-x--- 4 root root 4096 Aug 8 12:27 cache/
[root@worker232 ~]# cp oldboyedu-linux92.kubeconfig ~/.kube/config
[root@worker232 ~]# ll ~/.kube/
total 20
drwxr-x--- 3 root root 4096 Aug 8 12:28 ./
drwx------ 8 root root 4096 Aug 8 12:27 ../
drwxr-x--- 4 root root 4096 Aug 8 12:27 cache/
-rw------- 1 root root 5764 Aug 8 12:28 config
[root@worker232 ~]# kubectl get pods
NAME READY STATUS RESTARTS AGE
deploy-stress-7c98946b97-8sgnm 1/1 Running 0 20h
deploy-stress-7c98946b97-gnj8s 1/1 Running 0 19m
...
3. 声明 KUBECONFIG 变量
[root@worker232 ~]# export KUBECONFIG=/root/oldboyedu-linux92.kubeconfig
[root@worker232 ~]# kubectl get pods
NAME READY STATUS RESTARTS AGE
deploy-stress-7c98946b97-8sgnm 1/1 Running 0 20h
deploy-stress-7c98946b97-gnj8s 1/1 Running 0 23m
...
4. 使用别名
[root@worker233 ~]# vim ~/.bashrc
...
alias kubectl='kubectl --kubeconfig=/root/oldboyedu-linux92.kubeconfig'
...
[root@worker233 ~]# source ~/.bashrc
[root@worker232 ~]# kubectl get pods
NAME READY STATUS RESTARTS AGE
deploy-stress-7c98946b97-8sgnm 1/1 Running 0 20h
deploy-stress-7c98946b97-gnj8s 1/1 Running 0 28m
...
这是您提供的完整的基于用户组(Group)授权和服务账户(ServiceAccount)管理的案例。以下是详细内容:
基于用户组 (Group) 授权案例
1. RBAC 基于组的方式认证
用户组的好处是无需单独为某个用户创建权限,而是统一为该组授权,所有的用户都作为组的一部分访问资源。
温馨提示:
- (1) API Server 会优先校验用户名(CN 字段),若用户名没有权限,则会进一步校验用户组(O 字段)的权限。
- CN:表示用户的名称,例如 "hanwentong" 或 "kangzhengyang"。
- O:表示用户组的名称,例如 "linux92" 组。
- (2) 用户和用户组是通过证书中的字段提取的,而不是在集群中创建的。
RBAC 基于组的认证流程:
- CN:代表用户
- O:代表用户组
2. 将 hanwentong 用户添加到 linux92 组
2.1 编写证书请求
[root@master231 group]# cat > ca-config.json <<EOF
{"signing": {"default": {"expiry": "87600h"},"profiles": {"kubernetes": {"usages": ["signing","key encipherment","server auth","client auth"],"expiry": "87600h"}}}
}
EOF[root@master231 group]# cat > hanwentong-csr.json <<EOF
{"CN": "hanwentong","hosts": [],"key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","ST": "BeiJing","L": "BeiJing","O": "linux92","OU": "System"}]
}
EOF
2.2 使用 Kubernetes CA 签发客户端证书
[root@master231 group]# cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key -config=ca-config.json -profile=kubernetes hanwentong-csr.json | cfssljson -bare linux92
3. 生成 kubeconfig 授权文件
3.1 编写生成 kubeconfig 文件的脚本
[root@master231 group]# cat > kubeconfig.sh <<'EOF'
kubectl config set-cluster linux92-cluster \--certificate-authority=/etc/kubernetes/pki/ca.crt \--embed-certs=true \--server=https://10.0.0.231:6443 \--kubeconfig=oldboyedu-linux92-groups.kubeconfig# 设置客户端认证
kubectl config set-credentials hanwentong \--client-key=linux92-key.pem \--client-certificate=linux92.pem \--embed-certs=true \--kubeconfig=oldboyedu-linux92-groups.kubeconfig# 设置上下文
kubectl config set-context haha \--cluster=linux92-cluster \--user=hanwentong \--kubeconfig=oldboyedu-linux92-groups.kubeconfig# 设置当前默认使用的上下文
kubectl config use-context haha --kubeconfig=oldboyedu-linux92-groups.kubeconfig
EOF
3.2 生成 kubeconfig 文件
[root@master231 group]# bash kubeconfig.sh
4. 访问测试
[root@worker232 ~]# kubectl get pods --kubeconfig=oldboyedu-linux92-groups.kubeconfig -n kube-system
Error from server (Forbidden): pods is forbidden: User "hanwentong" cannot list resource "pods" in API group "" in the namespace "kube-system"
5. 创建 RBAC 授权策略
[root@master231 group]# cat rbac.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:namespace: kube-systemname: oldboyedu-custom-role-reader
rules:- apiGroups: ["","apps"]resources: ["pods","nodes","services","deployments"]verbs: ["get", "watch", "list"]---apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:name: oldboyedu-group-rolebindingnamespace: kube-system
subjects:- kind: Groupname: linux92apiGroup: rbac.authorization.k8s.io
roleRef:kind: Rolename: oldboyedu-custom-role-readerapiGroup: rbac.authorization.k8s.io
[root@master231 group]# kubectl apply -f rbac.yaml
role.rbac.authorization.k8s.io/oldboyedu-custom-role-reader created
rolebinding.rbac.authorization.k8s.io/oldboyedu-group-rolebinding created
6. 再次访问测试
[root@worker232 ~]# kubectl get pods --kubeconfig=oldboyedu-linux92-groups.kubeconfig -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-6d8c4cb4d-2l5jw 1/1 Running 2 (2d ago) 9d
coredns-6d8c4cb4d-qs4pd 1/1 Running 2 (2d ago) 9d
etcd-master231 1/1 Running 2 (2d ago) 9d
kube-apiserver-master231 1/1 Running 1 (2d ago) 2d20h
...
[root@worker232 ~]# kubectl get pods --kubeconfig=oldboyedu-linux92-groups.kubeconfig -n default
Error from server (Forbidden): pods is forbidden: User "hanwentong" cannot list resource "pods" in API group "" in the namespace "default": RBAC: role.rbac.authorization.k8s.io "oldboyedu-custom-role-reader" not found
7. 将 "zbr" 用户重复步骤 1-6
记得修改相应的字段,如用户名、证书等。
响应式管理 ServiceAccount
1. 创建 ServiceAccount
[root@master231 sa]# kubectl create sa oldboyedu
serviceaccount/oldboyedu created
[root@master231 sa]#
2. 查看 ServiceAccount
[root@master231 sa]# kubectl get sa
NAME SECRETS AGE
default 1 9d
oldboyedu 1 3s
3. 删除 ServiceAccount
[root@master231 sa]# kubectl delete sa oldboyedu
serviceaccount "oldboyedu" deleted
[root@master231 sa]#
[root@master231 sa]# kubectl get sa
NAME SECRETS AGE
default 1 9d
声明式管理 ServiceAccount
1. 创建 ServiceAccount
[root@master231 sa]# cat 01-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:name: oldboyedunamespace: default
[root@master231 sa]# kubectl apply -f 01-sa.yaml
serviceaccount/oldboyedu created
[root@master231 sa]#
[root@master231 sa]# kubectl get -f 01-sa.yaml
NAME SECRETS AGE
oldboyedu 1 9s
2. 删除 ServiceAccount
[root@master231 sa]# kubectl delete -f 01-sa.yaml
serviceaccount "oldboyedu" deleted
[root@master231 sa]#