西湖论剑2025cscs详解
Cobalt Strike流量主要是找beacon,主要以两种形式呈现
·一小段shellcode(几百个字节),通常叫做stager shellcode,这段代码下载整个的beacon。
·一个完全的beacon:一个可以反射性加载的PE文件
先来了解下cs流量的特征
cs流量特征:
1,基础特征:心跳包
2,请求特征:下发的指令,url路径,老版本固定的ua头
3,源码特征:checksum8 (92L 93L)
回到题目给的附件,我们来判断下给的流量包是否存在魔改
判断魔改
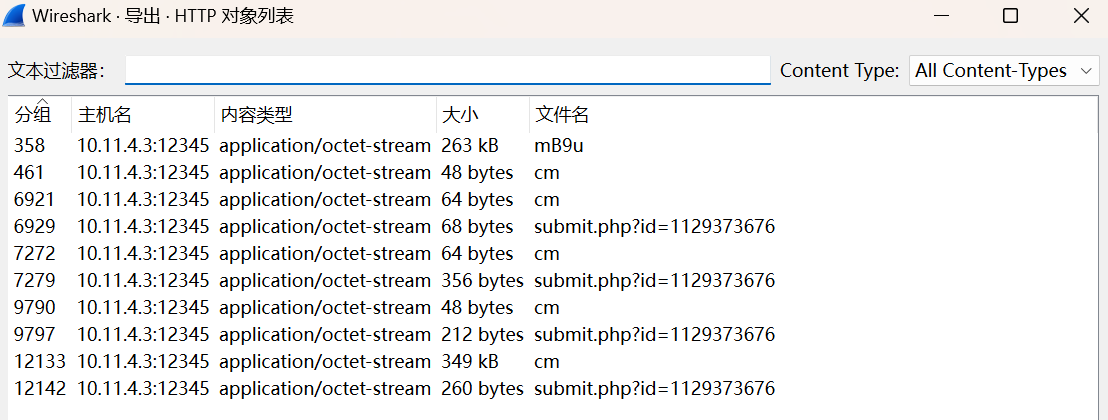
def checksum8(text): if len(text) < 4: return 0 text = text.replace("/", "") sum_value = 0 for char in text: sum_value += ord(char) return sum_value % 256 if __name__ == "__main__": print(checksum8("mB9u"))
输出为93,64位的后门,未魔改
解密心跳包
导出mB9u文件,后缀改为.vir,这是我们要的beacon,我们需要1768.py去分析,
1768.py是加密和解密beacon的配置文件
https://blog.didierstevens.com/2021/10/11/update-1768-py-version-0-0-8/
运行可以得到公钥等信息
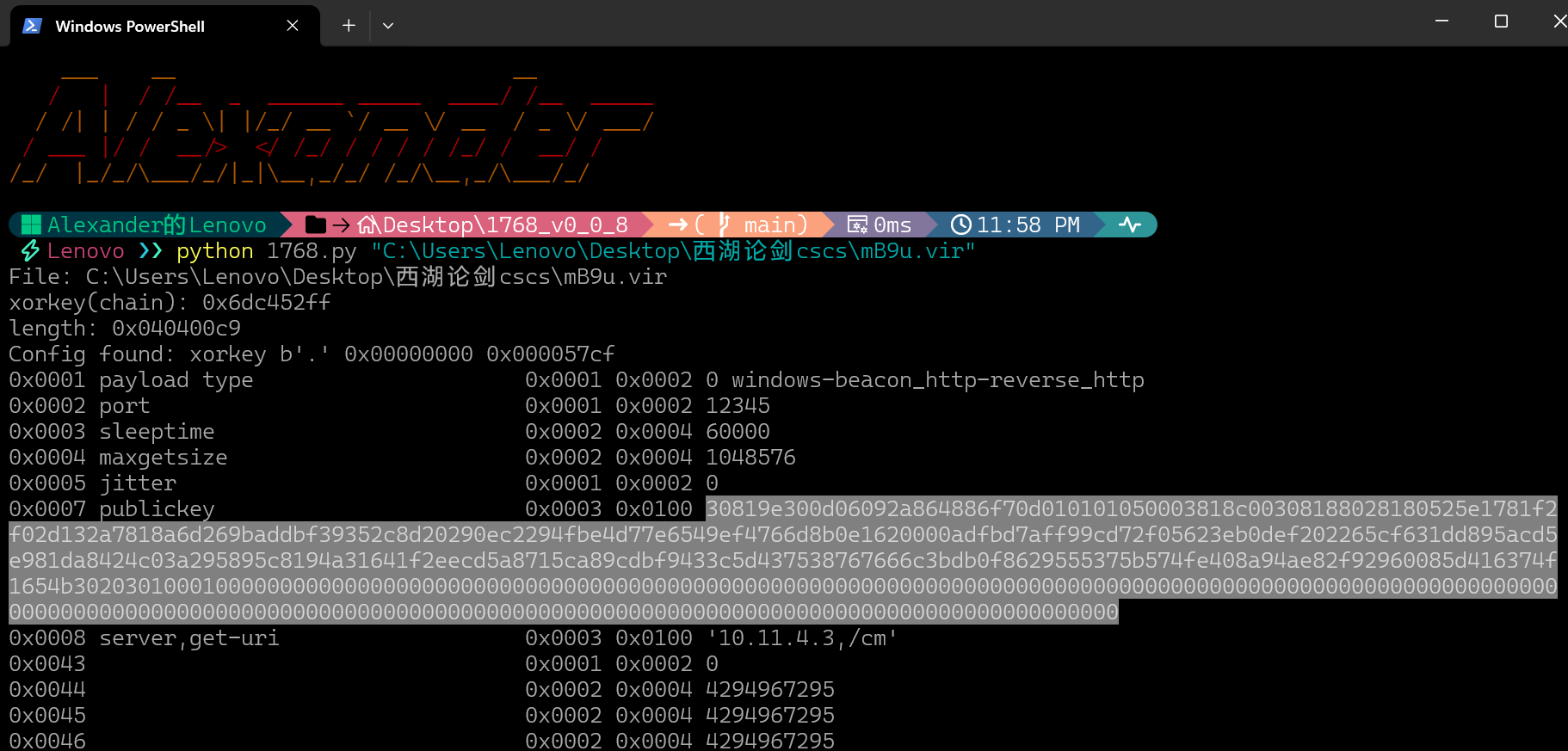
公钥数据
30819e300d06092a864886f70d010101050003818c00308188028180525e1781f2f02d132a7818a6d269baddbf39352c8d20290ec2294fbe4d77e6549ef4766d8b0e1620000adfbd7aff99cd72f05623eb0def202265cf631dd895acd5e981da8424c03a295895c8194a31641f2eecd5a8715ca89cdbf9433c5d437538767666c3bdb0f8629555375b574fe408a94ae82f92960085d416374f1654b30203010001
from hex to base64
MIGeMA0GCSqGSIb3DQEBAQUAA4GMADCBiAKBgFJeF4Hy8C0TKngYptJput2/OTUsjSApDsIpT75Nd+ZUnvR2bYsOFiAACt+9ev+ZzXLwViPrDe8gImXPYx3YlazV6YHahCTAOilYlcgZSjFkHy7s1ahxXKic2/lDPF1DdTh2dmbDvbD4YpVVN1tXT+QIqUroL5KWAIXUFjdPFlSzAgMBAAE=
ps:
import base64def hex_to_base64(hex_string):# 将十六进制字符串转换为字节数据byte_data = bytes.fromhex(hex_string)# 将字节数据编码为 Base64base64_data = base64.b64encode(byte_data)# 返回 Base64 字符串(解码为 UTF-8)return base64_data.decode('utf-8')# 示例用法
hex_input = ""
base64_output = hex_to_base64(hex_input)
print("Base64 输出:", base64_output)
这边建议使用厨子,因为后面会有超长的hex字节,会卡爆

获取私钥
本题流量是通信流量
通信流量是通过生成的 AES Key 和 HMAC Key 进行加密的
AES Key 和 HMAC Key是根据 TeamServer 端接收到第一个心跳包时用私钥去解密心跳包中公钥加密的 cookie根据解密出的协商公钥生成的
用cs-decrypt-metadata去解cookie发现根本解不开
我们用开源的rsatools去解私钥
https://github.com/RsaCtfTool/RsaCtfTool
帮我刚刚得到的公钥转换为标准格式并保存为key.pub
-----BEGIN PUBLIC KEY-----
MIGeMA0GCSqGSIb3DQEBAQUAA4GMADCBiAKBgFJeF4Hy8C0TKngYptJput2/OTUsjSApDsIpT75N
d+ZUnvR2bYsOFiAACt+9ev+ZzXLwViPrDe8gImXPYx3YlazV6YHahCTAOilYlcgZSjFkHy7s1ahx
XKic2/lDPF1DdTh2dmbDvbD4YpVVN1tXT+QIqUroL5KWAIXUFjdPFlSzAgMBAAE=
-----END PUBLIC KEY-----
终端命令
python RsaCtfTool.py --publickey ./key.pub --private

得到私钥
-----BEGIN RSA PRIVATE KEY-----
MIICWgIBAAKBgFJeF4Hy8C0TKngYptJput2/OTUsjSApDsIpT75Nd+ZUnvR2bYsO
FiAACt+9ev+ZzXLwViPrDe8gImXPYx3YlazV6YHahCTAOilYlcgZSjFkHy7s1ahx
XKic2/lDPF1DdTh2dmbDvbD4YpVVN1tXT+QIqUroL5KWAIXUFjdPFlSzAgMBAAEC
gYApWVrrvY2c0zZKu/VjQ/ivQUPy0b63GmVyS1Lg8frzAiAaESnE2Pl6bwsGbxTE
I+3jeYuE1IdWOAeMnKPhY80fOSgws6vSri7CcxnMUEEn3AMw4YSwBIaBGkdLnfxf
pbS/kUUb/z7/A1SRtNq1n4hZYinnG2NpUuiO1WqwHqOGoQJBAJE14+VVt8ONGIZ1
qIf4cqAnAmtonPhyDNdYZQC0IlxNzyixo/lnlTc80b3jYUA4w8GGQQZea70op4RS
fIJV420CQQCRNePlVbfDjRiGdaiH+HKgJwJraJz4cgzXWGUAtCJcTc8osaP5Z5U3
PNG942FAOMPBhkEGXmu9KKeEUnyCVeSfAkB6vJQuKe+zaDVMoXKbyxIH8DEJXFkh
XjUgZ+SnXZqVbmclPFEe48Cp+cxGtkRjJhfAIZwgp/pk3lIJdDctay9ZAkAhlDeu
CcNj6hXYyg592tsO49ZwZhGedik4Bw3cOsuTUr7r5yBHBUgBLQRHh/QuOLIz50rU
ITOC24rZU4XNUfV7AkAipEfvmXf4RaJLlIoWZe/XkNXpGcsYIeaedUv29xqaNAbA
7HhEs3twu6+G0QP1YuAPNp28FNoe52XfJhVWTw1D
-----END RSA PRIVATE KEY-----
通过cookie得到HMACK key和AES key
工具地址
https://github.com/WBGlIl/CS_Decrypt
因为密码库M2Crypto非常老,我们要修改代码
'''
Beacon元数据
'''
import hashlib
import M2Crypto
import base64
import hexdumpPRIVATE_KEY = """
-----BEGIN RSA PRIVATE KEY-----
{}
-----END RSA PRIVATE KEY-----
"""encode_data = ""
base64_key = ""pubkey = M2Crypto.RSA.load_key_string(PRIVATE_KEY.format(base64_key).encode())
ciphertext = pubkey.private_decrypt(base64.b64decode(encode_data), M2Crypto.RSA.pkcs1_padding)将上面的一部分代码替换成下面的
'''
Beacon元数据
'''
import hashlib
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_v1_5
import base64
import hexdumpPRIVATE_KEY = """-----BEGIN RSA PRIVATE KEY-----
{}
-----END RSA PRIVATE KEY-----"""encode_data = ""
base64_key = """private_key = RSA.import_key(PRIVATE_KEY.format(base64_key).encode())
cipher = PKCS1_v1_5.new(private_key)
ciphertext = cipher.decrypt(base64.b64decode(encode_data), 0)
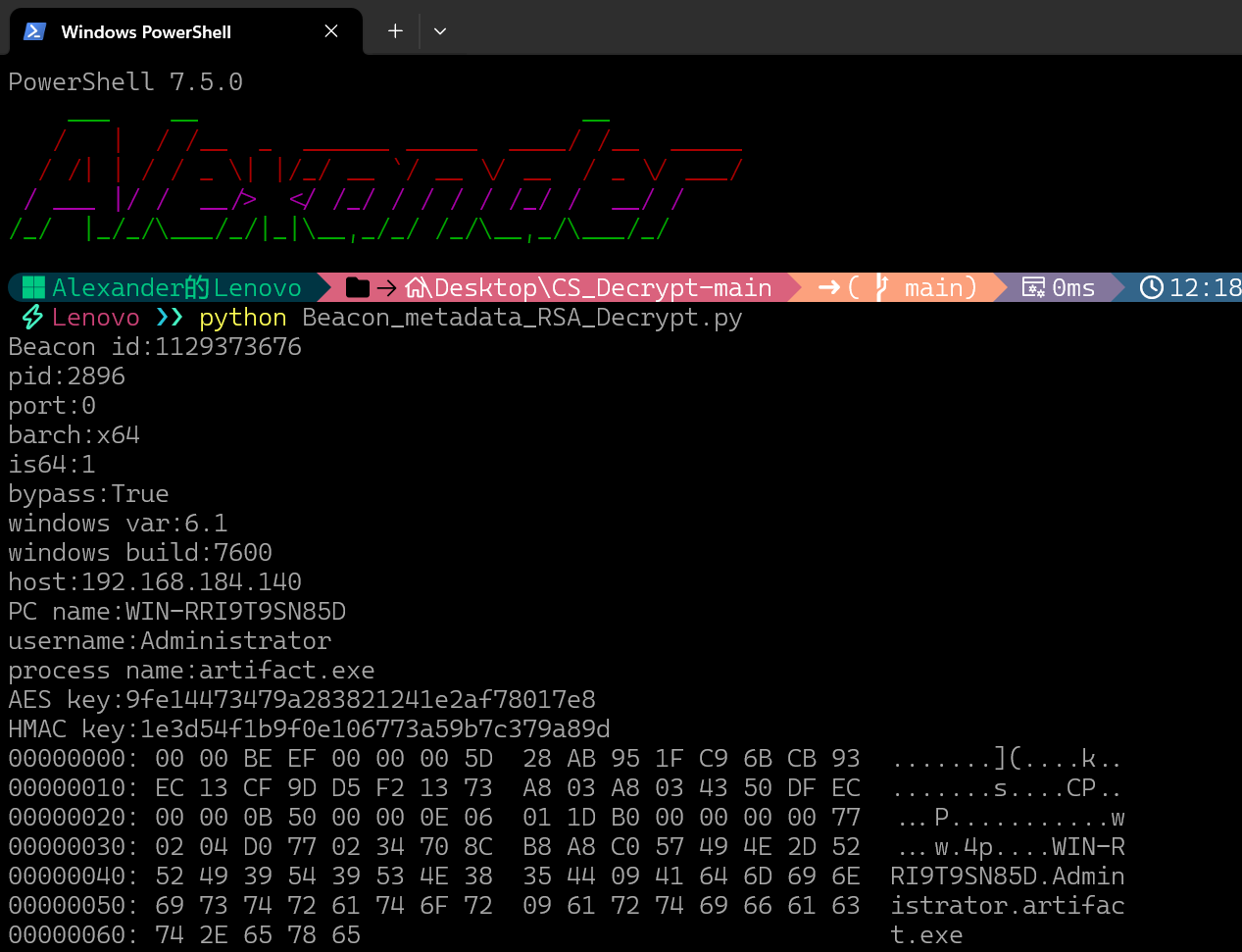
得到AES Key 和 HMAC Key
AES key:9fe14473479a283821241e2af78017e8
HMAC key:1e3d54f1b9f0e106773a59b7c379a89d
解密数据
用CS_Task_AES_Decrypt.py提取最大的包(开头349bytes的cm文件),解密出获得secret.pcapng流量包
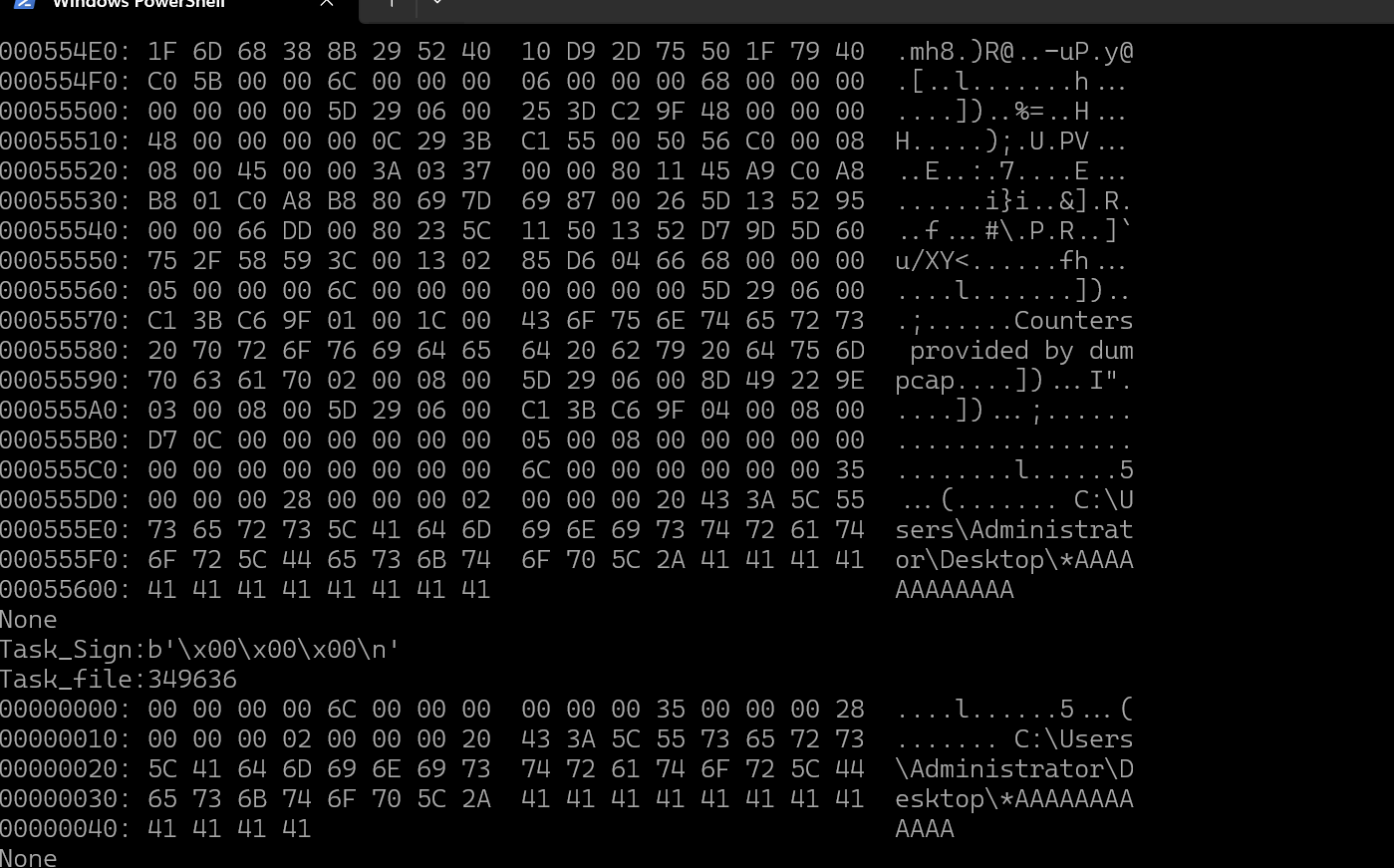
将保存的data.bin改为1.pcapng,发现wireshark是打不开的
恢复流量包
第一种就是手动删去多余的部分
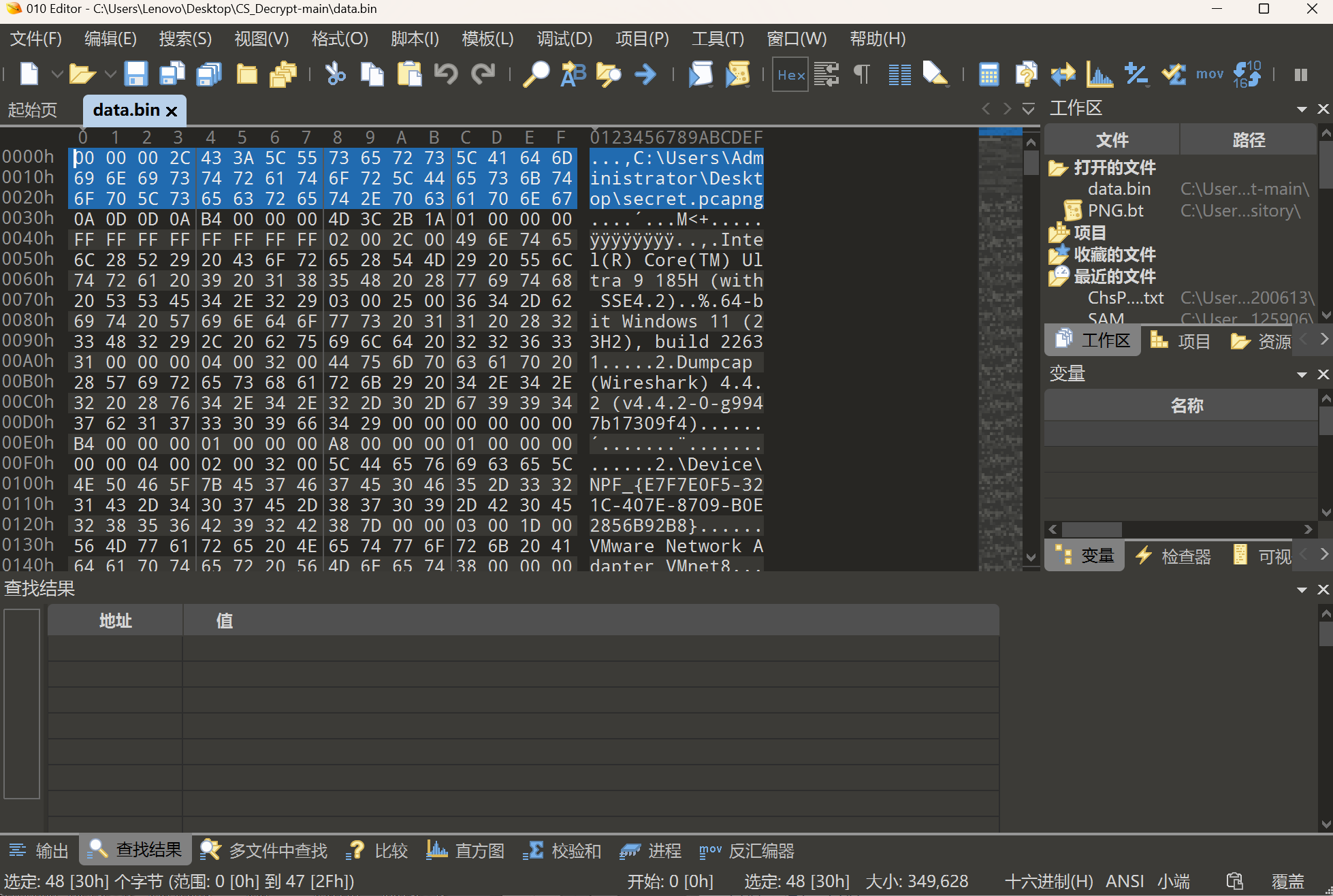
比较麻烦,直接工具修了
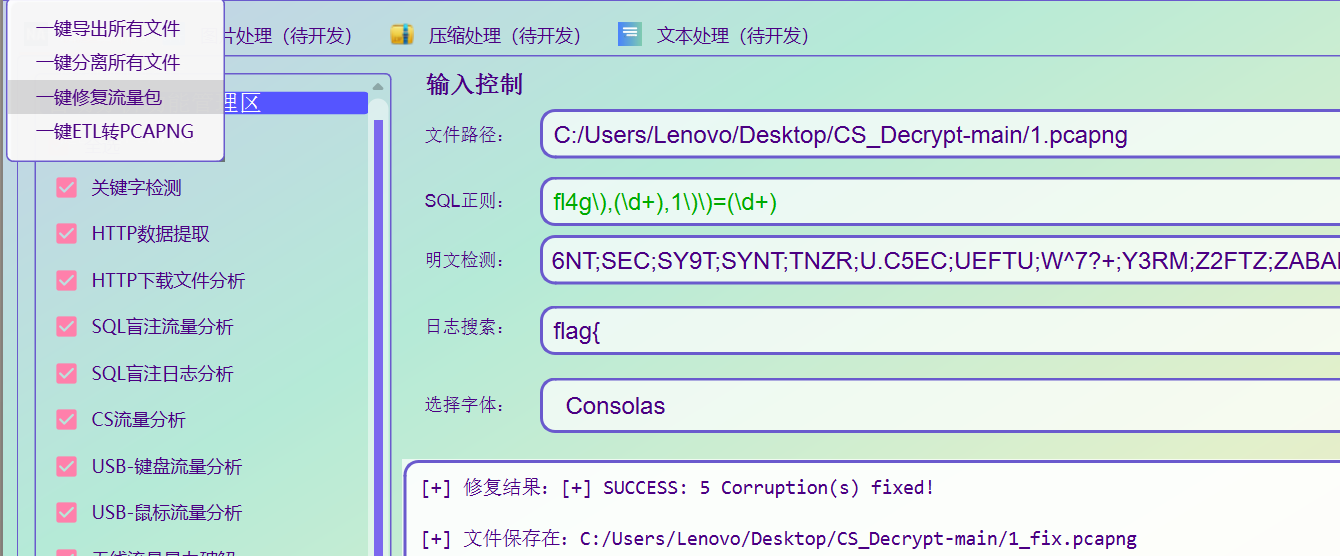
成功打开流量包
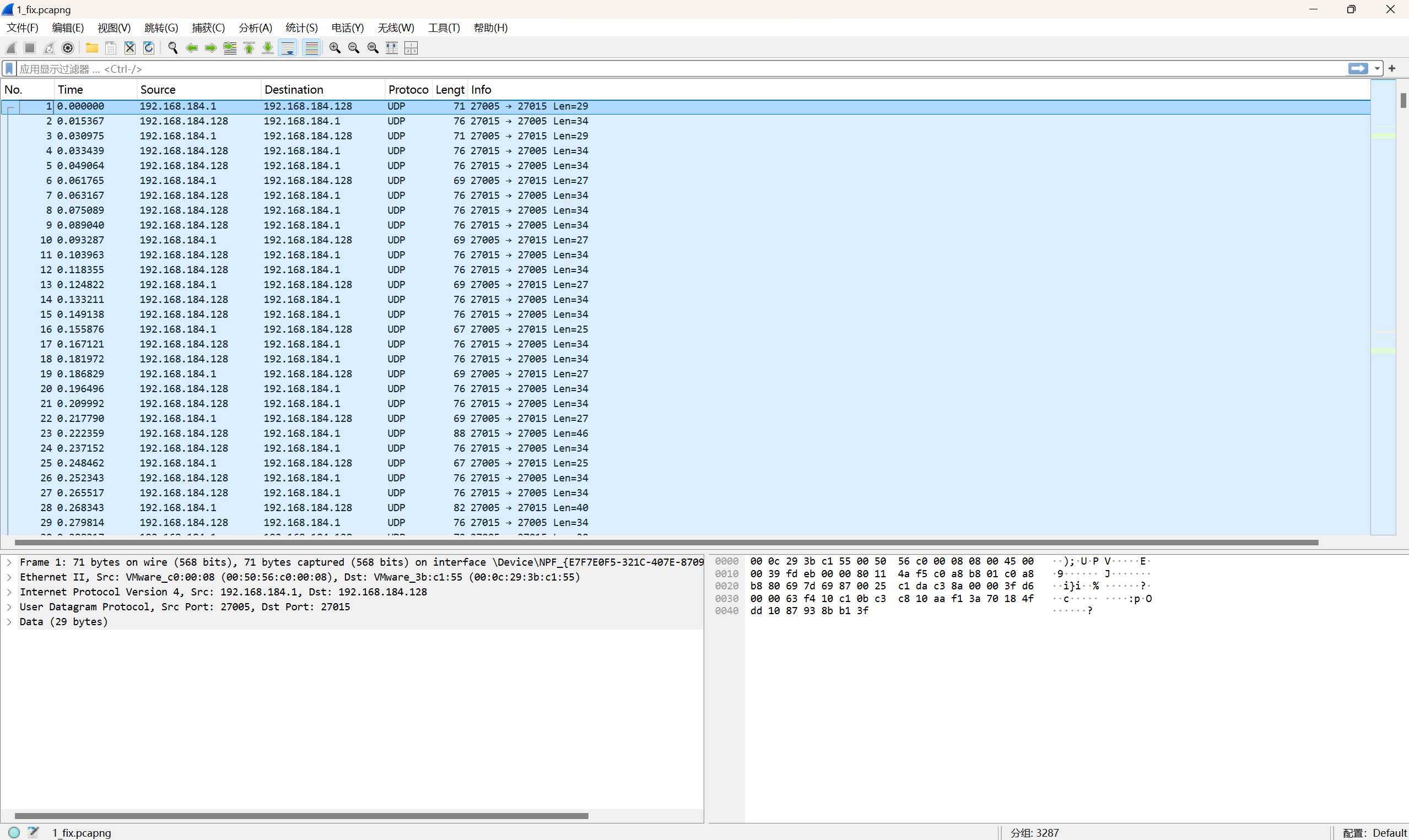
cs1.6流量
L3HCTF的原题
https://www.anquanke.com/post/id/261339
引用其中的C代码,并作修改
extern "C"
{ int _LongSwap(int l) { unsigned int res = __builtin_bswap32(*(unsigned int *)&l); return *(int *)&(res); } const unsigned char mungify_table[] = { 0x7A, 0x64, 0x05, 0xF1, 0x1B, 0x9B, 0xA0, 0xB5, 0xCA, 0xED, 0x61, 0x0D, 0x4A, 0xDF, 0x8E, 0xC7}; const unsigned char mungify_table2[] = { 0x05, 0x61, 0x7A, 0xED, 0x1B, 0xCA, 0x0D, 0x9B, 0x4A, 0xF1, 0x64, 0xC7, 0xB5, 0x8E, 0xDF, 0xA0}; unsigned char mungify_table3[] = { 0x20, 0x07, 0x13, 0x61, 0x03, 0x45, 0x17, 0x72, 0x0A, 0x2D, 0x48, 0x0C, 0x4A, 0x12, 0xA9, 0xB5}; void COM_UnMunge2(unsigned char *data, int len, int seq) { int i; int mungelen; int c; int *pc; unsigned char *p; int j; mungelen = len & ~3; mungelen /= 4; for (i = 0; i < mungelen; i++) { pc = (int *)&data[i * 4]; c = *pc; c ^= seq; p = (unsigned char *)&c; for (j = 0; j < 4; j++) { *p++ ^= (0xa5 | (j << j) | j | mungify_table2[(i + j) & 0x0f]); } c = _LongSwap(c); c ^= ~seq; *pc = c; } }
}改为1.cpp
下面需要用到msys2这个工具
也可以直接在虚拟机里编译,因为之前写逆向的题下了所以我就用mingw64直接编译了
这里注意的是windows系统中使用的是.dll文件,而不能加载.so文件
g++ -shared -o 1.dll 1.cpp
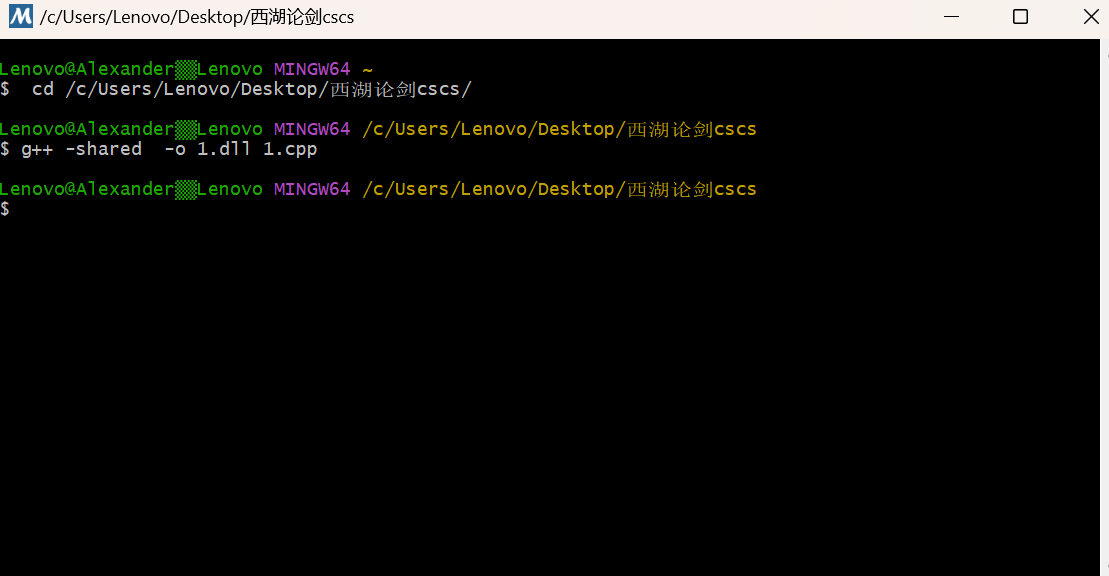
得到.dll文件
直接解密流量包就行了
# -*- coding: UTF-8 -*-
from scapy.all import *
from ctypes import *
import structlib=CDLL('')
COM_UnMunge=lib.COM_UnMunge2pcaps = rdpcap("")f=open('res','wb')
for mpacket in pcaps.filter(lambda x:UDP in x and x[UDP].sport==27015):# mpacket.show()udp=mpacket[UDP]data=bytes(udp.payload)[8:]seq=bytes(udp.payload)[:4]ack=bytes(udp.payload)[4:8]c=create_string_buffer(data)COM_UnMunge(c,len(data),seq[0])print(mpacket.time,mpacket[IP].src,'->',mpacket[IP].dst)decode_bytes=bytes(c)if len(decode_bytes)>10:if struct.unpack('<L', seq)[0] & (1<<30):if len(decode_bytes)>10+struct.unpack('<h', decode_bytes[7:9])[0]+1:print('find extra data block:')print(decode_bytes[10+struct.unpack('<h', decode_bytes[7:9])[0]:])decode_bytes=decode_bytes[10:10+struct.unpack('<h', decode_bytes[7:9])[0]]f.write(decode_bytes)print(f'finally decode data:{decode_bytes}\nlength:{len(decode_bytes)}')
f.close
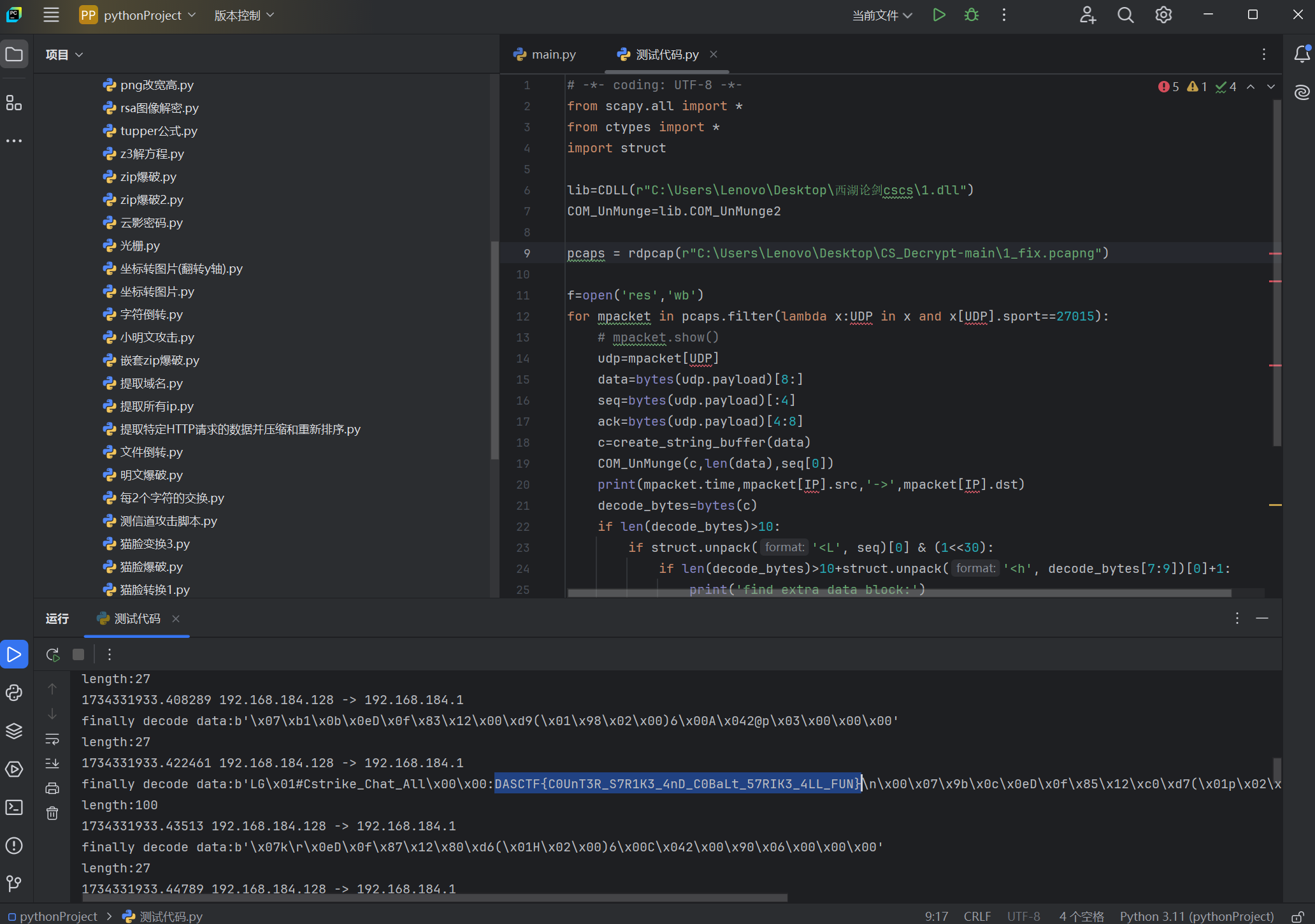
DASCTF{C0UnT3R_S7R1K3_4nD_C0BaLt_57RIK3_4LL_FUN}



![分享[清华大学DeepSeek教程全家桶]下载地址](https://img2024.cnblogs.com/blog/44814/202502/44814-20250226000155121-2043354056.png)